- A novel technique that reduces the overhead in extracting sensitive data from Chromium browser’s memory was recently found by researchers from CyberArk Labs
- Existing access to the targeted system is required before leveraging the technique
- Successful use of the technique can lead to multifactor authentication (MFA) bypass by extracting valid authentication tokens from the web browser’s memory
- CrowdStrike has built defensive capability in the CrowdStrike Falcon®® sensor against this technique
- The Falcon platform helps identify, prevent and detect memory-based vulnerabilities and protect customers from modern identity-based attacks
Recent research from CyberArk Labs presents a new technique for extracting sensitive data from the Chromium browser’s memory. However, existing access to the targeted system is required before leveraging the technique to extract the sensitive data. The technique could enable identity-based attacks involving authentication bypass using Oauth cookies that have already passed an MFA challenge.
CrowdStrike built defensive capabilities to protect CrowdStrike customers from similar post-compromise attacks leveraging this novel technique for extracting valid authentication tokens from the Chromium browser’s memory.
The Falcon sensor helps identify, prevent and detect memory-based vulnerabilities, while the Falcon platform enables customers to stay safe from identity-based attacks, enforcing Zero Trust on the endpoint, the identity and the data.
According to the CrowdStrike Falcon® OverWatch™ threat hunting team, 80% of breaches are now identity-driven. Stopping the adversary in real time and preventing attacks from progressing requires a unified approach to security that delivers native identity protection capabilities, halts adversaries and stops breaches.
About the Research and the Technique
The research and proof of concept (POC) demonstrate how sensitive information is extracted by a non-elevated process running on the local machine and performs direct access to Chrome’s memory using OpenProcess + ReadProcessMemory APIs.
While existing access to the targeted system is required before leveraging the technique, the extracted sensitive data could be used in subsequent identity-based attacks that can bypass MFA using Oauth cookies or enable lateral movement using extracted credentials.
The presented technique takes a novel approach in reducing the overhead involved in extracting valid Oauth tokens from web browser memory by reading the Chromium browser's memory and monitoring for specific login URLs. A snapshot is taken of specific memory buffer regions, both before and after login and authentication. This significantly reduces the amount of memory that needs to be dumped and scanned. Additionally, the technique reduces the amount of time necessary to extract the token and increases the window of opportunity for an attacker before the token expires.
In essence, an attacker could hijack an authenticated user's browser session, get access to restricted information, and most significantly, bypass MFA without knowing any of the victim’s credentials.
For more detailed technical information on the research and POC, check out the research here.
CrowdStrike Falcon® vs. the Memory-Based Data Extraction Technique
Recent research presented by CyberArk Labs to CrowdStrike shows the benefits of cooperation and collaboration in advancing the state of cybersecurity, ultimately helping to build better defense-in-depth capabilities to protect organizations from novel threats, tactics and techniques. Based on the details provided by the research and POC, we were able to build comprehensive Falcon capabilities to protect customers from the newly found technique and other similar ones.
After carefully analyzing the technique presented in the POC, we found there is a vast array of legitimate processes opening a handle to a browser process and using the same open handle access rights to read its memory. See Figure 1 for a snapshot.
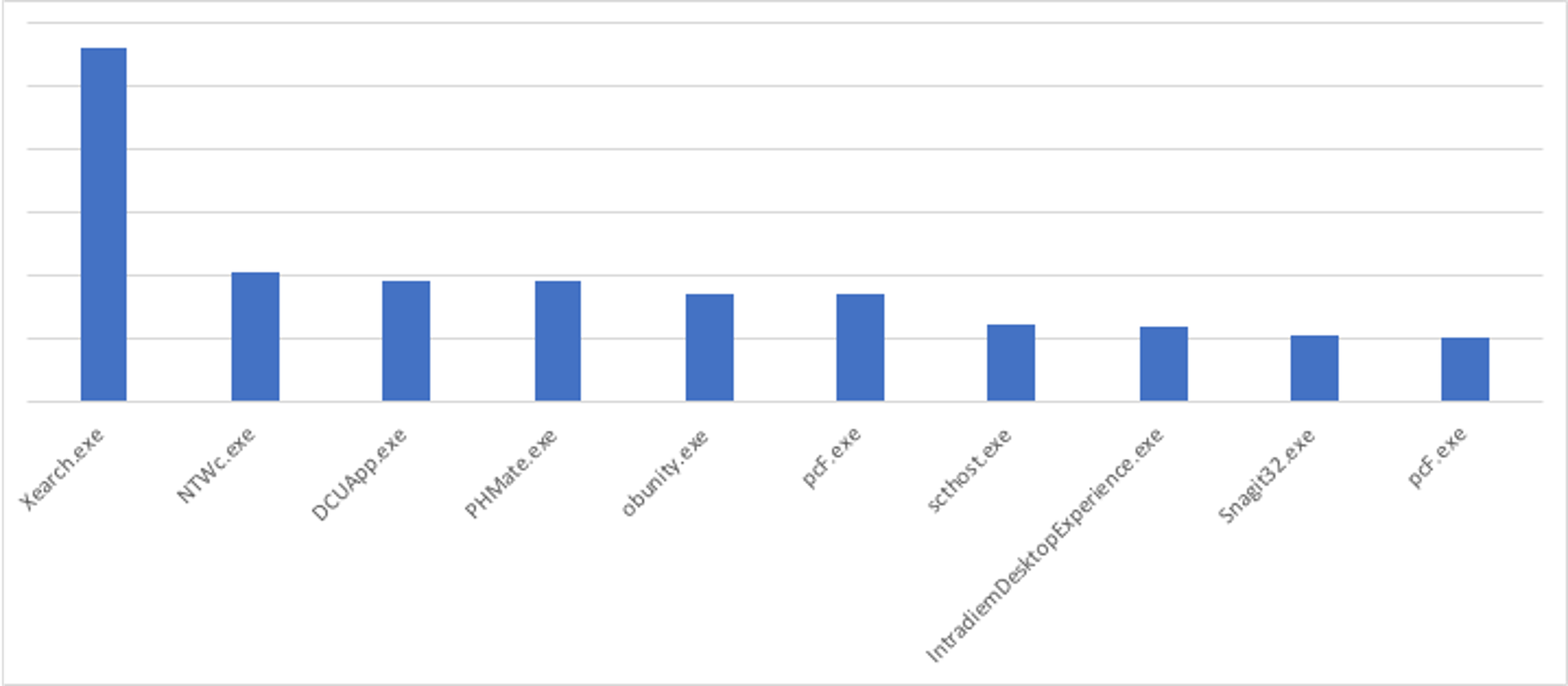 Figure 1. Top 10 legitimate processes that use the same method for opening a process and accessing memory data, according to CrowdStrike telemetry (Click to enlarge)
Figure 1. Top 10 legitimate processes that use the same method for opening a process and accessing memory data, according to CrowdStrike telemetry (Click to enlarge)This can present a big challenge to threat hunters as it can be like searching for the proverbial needle in a haystack when looking for malicious processes exhibiting the same behavior. However, there are some subtle differences in how the POC operates that can help us discern between benign and malicious processes.
From a defense perspective, it's important to look at the Chrome browser as a credential store, just like Local Security Authority Subsystem Service (LSASS) that’s responsible for enforcing security policy on the machine in terms of handling user authentication, password changes and authentication tokens. Identifying processes that attempt to inject or tamper with LSASS to either create a minidump or attach a debugger can potentially reveal malicious behavior.
The defense of browser credential theft requires similar thinking, both in terms of detection and prevention strategy, as well as a robust identity-based defense.
When CrowdStrike’s machine learning and behavior-based indicators of attack (IOAs) determine a process is malicious, Falcon will automatically prevent this process from accessing the browser’s memory using this technique.
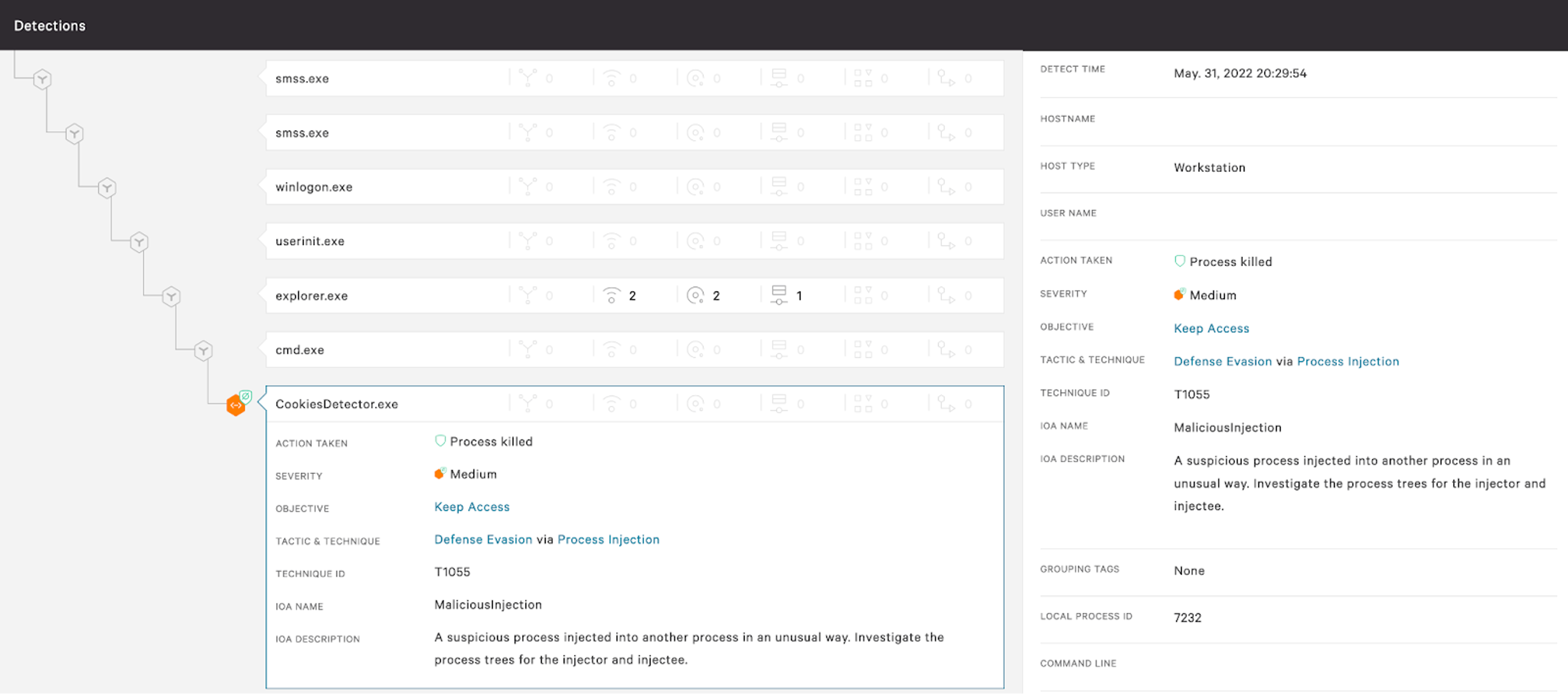 Figure 2. CrowdStrike Falcon® detection and prevention of the POC attempting to inject the chrome.exe process (Click to enlarge)
Figure 2. CrowdStrike Falcon® detection and prevention of the POC attempting to inject the chrome.exe process (Click to enlarge)As seen in Figure 2, the Falcon platform can immediately detect and prevent the POC from progressing by identifying any suspicious injection techniques on chrome.exe. The process is promptly killed, triggering an alert in the Falcon console.
Running the CyberArk POC through the MITRE ATT&CK® framework mapping reveals tactics and techniques commonly associated with identity-based attacks. The CrowdStrike Falcon® platform provides defenders with actionable information on a given technique so that they can immediately take mitigation actions by identifying and blocking the use of stolen credentials and enforcing MFA. By successfully identifying and blocking these chokepoint techniques, defenders can disrupt the adversary and shut down the identity-based attack.
| Tactic | Description |
| Execution | Native API: T1539 |
| Credential Access | Steal Web Session Cookie: T1111 Multi-Factor Authentication Interception: T1106 |
CrowdStrike Platform Protects from Modern Identity-Based Attacks
Many breaches are now identity-driven. Credential theft, credential hopping, stealing browser cookies for bypassing MFA or credential theft using various tools are just some of the tactics and techniques used in modern identity-based attacks.
With recent examples of identity-based attacks involving sophisticated adversaries stealing Chrome browser cookies from a user that had already passed an MFA challenge, organizations need a unified approach to security that also enforces Zero Trust.
CrowdStrike’s identity protection capabilities recently shut down MITRE ATT&CK adversaries during the latest adversary emulation, stopping the test before it could even start. Coupled with the Falcon sensor’s comprehensive IOAs and machine learning capabilities, as well as Falcon’s unified cloud-native automated orchestration and threat intelligence, the Falcon platform can equip defenders with the right data at the right time to stop breaches.
Additional Resources
- Learn more about CrowdStrike’s Zero Trust solution.
- Learn how CrowdStrike Falcon® Identity Protection reduces costs and risks across the enterprise by protecting workforce identities.
- Read the blogs “CrowdStrike Partners with MITRE CTID, Reveals Real-world Insider Threat Techniques” and “Falcon Platform Identity Protection Shuts Down MITRE ATT&CK Adversaries.”
- Learn how the powerful CrowdStrike Falcon®® platform provides comprehensive protection across your organization, workers and data, wherever they are located.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and see for yourself how true next-gen AV performs against today’s most sophisticated threats.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)













































