The discovery by security researchers in March 2018 of a PDF sample that contains exploits for two zero-day vulnerabilities has confirmed that exploiting PDF readers is still considered a viable attack vector by, presumably, more advanced threat actors.1,2 With CrowdStrike® Falcon Sandbox™ we strive to enable our customers, in a completely automated and generic fashion, to analyze all types of attacks, including sophisticated ones using zero-day PDF reader exploits. This is why CrowdStrike has added new capabilities to Falcon Sandbox that allow for more thorough analyses of PDF files, particularly ones that contain exploits targeting Adobe’s Acrobat Reader. Due to its widespread usage, Reader has often been the target of exploit attempts. These additions to Falcon Sandbox include improvements to its detection capabilities for LPE (local privilege escalation) exploits, which are crucial for bypassing Acrobat Reader’s sandbox protections. To illustrate these improvements, the following section walks you through a recent Falcon Sandbox analysis of the sample mentioned in the opening paragraph.
Fully Automated Falcon Sandbox Analysis of a Malicious PDF Containing Zero-Day Exploits
As previously mentioned, in March 2018 researchers discovered a PDF sample that contains two zero-day exploits targeting Acrobat Reader and Acrobat, and older Windows versions, respectively (CVE-2018-4990 and CVE-2018-8120). CVE-2018-4990 is an out-of-bounds read vulnerability in Acrobat Reader while CVE-2018-8120 is an EoP (elevation of privilege) vulnerability in Win32k caused by a null pointer dereference, which is used to bypass the Acrobat Reader sandbox.  The sample appears to still have been in development at the time of its discovery and hadn’t been fully weaponized yet, only dropping a POC (proof of concept) malware file to disk after successful exploitation. Several excellent articles, in addition to the two referenced above, have been published that describe these two vulnerabilities and their exploitation in detail.3,4,5 This blog will focus on how Falcon Sandbox enables its users to analyze the malicious PDF sample in an automated fashion. The original in-the-wild PDF file (SHA256: 4b672deae5c1231ea20ea70b0bf091164ef0b939e2cf4d142d31916a169e8e01) turned out to be unreliable when attempting to successfully exploit multiple vulnerable Acrobat Reader versions. Keeping in mind that for demonstration purposes our goal is to trigger as much malicious behavior as we can, so we can extract as many IOCs (indicators of compromise) as possible, we made slight improvements to the PDF’s exploit code that make it more stable and ensure successful exploitation. The report discussed below stems from a recent Falcon Sandbox analysis of the improved PDF sample (SHA256: c319913bd07365503ee5925ac93b20967f5531b49f392b99d7e3619ae4d06477). The Falcon Sandbox environment used for analysis had the following OS and Acrobat Reader versions installed:
The sample appears to still have been in development at the time of its discovery and hadn’t been fully weaponized yet, only dropping a POC (proof of concept) malware file to disk after successful exploitation. Several excellent articles, in addition to the two referenced above, have been published that describe these two vulnerabilities and their exploitation in detail.3,4,5 This blog will focus on how Falcon Sandbox enables its users to analyze the malicious PDF sample in an automated fashion. The original in-the-wild PDF file (SHA256: 4b672deae5c1231ea20ea70b0bf091164ef0b939e2cf4d142d31916a169e8e01) turned out to be unreliable when attempting to successfully exploit multiple vulnerable Acrobat Reader versions. Keeping in mind that for demonstration purposes our goal is to trigger as much malicious behavior as we can, so we can extract as many IOCs (indicators of compromise) as possible, we made slight improvements to the PDF’s exploit code that make it more stable and ensure successful exploitation. The report discussed below stems from a recent Falcon Sandbox analysis of the improved PDF sample (SHA256: c319913bd07365503ee5925ac93b20967f5531b49f392b99d7e3619ae4d06477). The Falcon Sandbox environment used for analysis had the following OS and Acrobat Reader versions installed:
- Windows 7 32-bit SP1 Build 7601
- Adobe Acrobat Reader DC Continuous Release 2018.009.20044
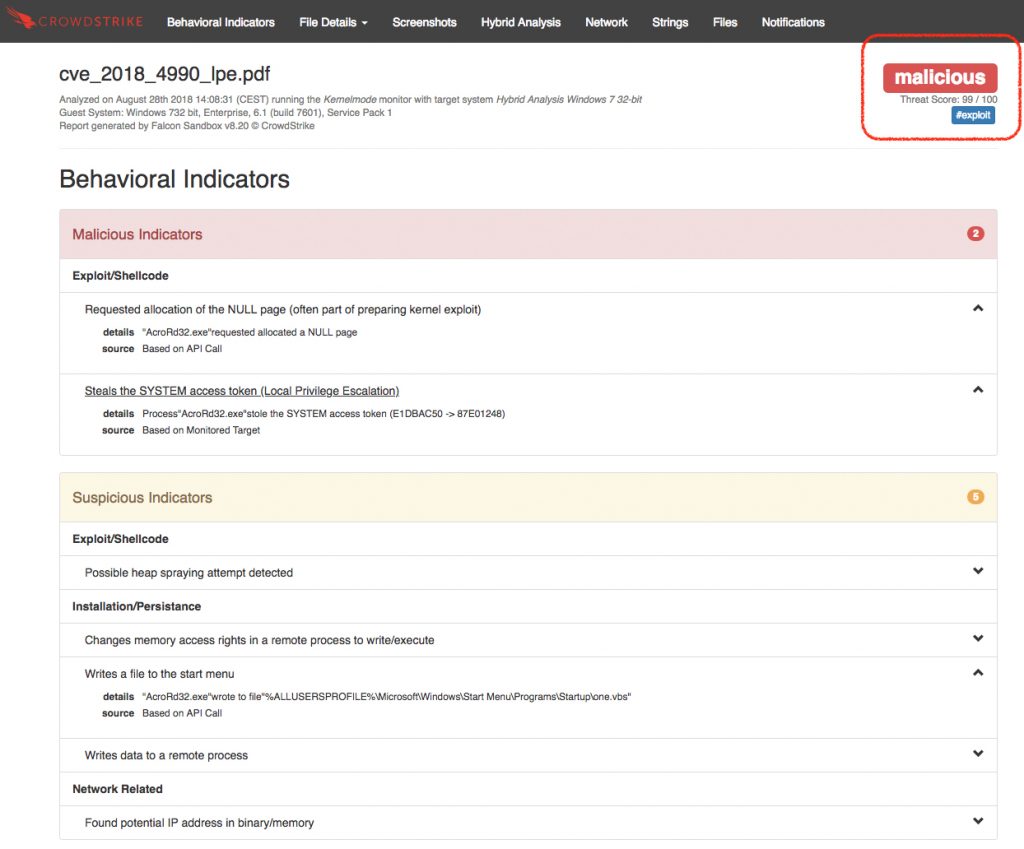 Looking at the report, we see right away that the sample has been identified as malicious with a Threat Score of 99/100, i.e., with very high confidence. Furthermore, the #exploit label has been assigned, meaning that Falcon Sandbox detected that the PDF contains exploits. If we look further down at the Behavioral Indicators section, we see under Malicious Indicators the following:
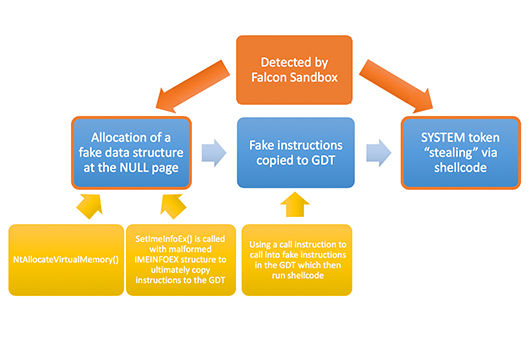
Looking at the report, we see right away that the sample has been identified as malicious with a Threat Score of 99/100, i.e., with very high confidence. Furthermore, the #exploit label has been assigned, meaning that Falcon Sandbox detected that the PDF contains exploits. If we look further down at the Behavioral Indicators section, we see under Malicious Indicators the following: 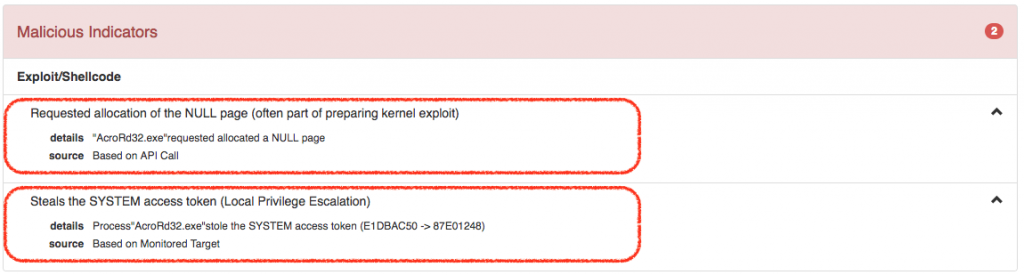 Falcon Sandbox detected that the AcroRd32 process “stole” the process token from the SYSTEM process, a technique often used in kernel exploits for elevating privileges. Here, it is used to escape the Acrobat Reader sandbox. In addition, NULL page memory allocation has been detected, which is used in this exploit to allocate a fake data structure at the NULL page which is later used by the exploit to copy malicious instructions to the GDT (Global Descriptor Table). These instructions ultimately result in the execution of shellcode that does the “token stealing” that results in the EoP (Elevation of Privilege) mentioned above. Under Suspicious Indicators we see the following:
Falcon Sandbox detected that the AcroRd32 process “stole” the process token from the SYSTEM process, a technique often used in kernel exploits for elevating privileges. Here, it is used to escape the Acrobat Reader sandbox. In addition, NULL page memory allocation has been detected, which is used in this exploit to allocate a fake data structure at the NULL page which is later used by the exploit to copy malicious instructions to the GDT (Global Descriptor Table). These instructions ultimately result in the execution of shellcode that does the “token stealing” that results in the EoP (Elevation of Privilege) mentioned above. Under Suspicious Indicators we see the following: 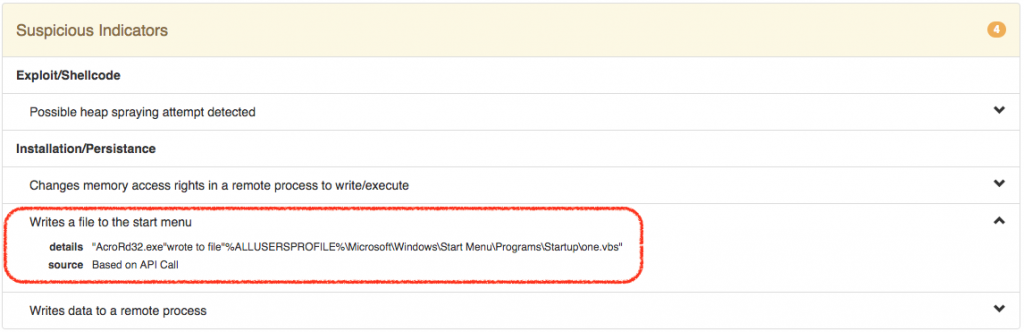 AcroRd32 writes a file called one.vbs to the Startup folder. This file, which constitutes the POC malware mentioned earlier, has been extracted by Falcon Sandbox and is available for further analysis.
AcroRd32 writes a file called one.vbs to the Startup folder. This file, which constitutes the POC malware mentioned earlier, has been extracted by Falcon Sandbox and is available for further analysis. 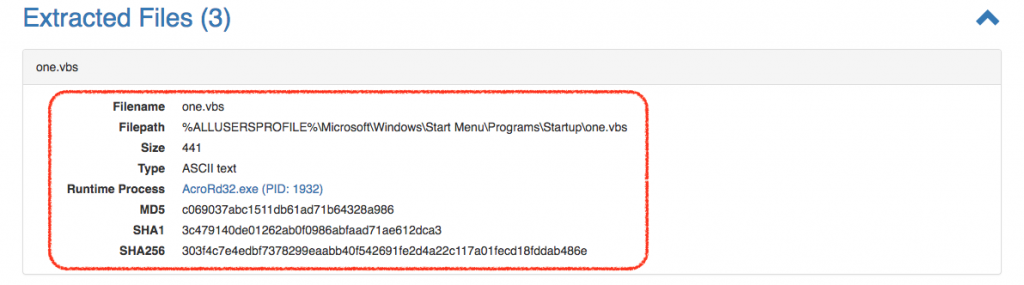 Had this been a fully weaponized PDF file, we would see further activity such as connections to C2 (command and control) infrastructure, which would also be picked up by Falcon Sandbox and shown in the report.
Had this been a fully weaponized PDF file, we would see further activity such as connections to C2 (command and control) infrastructure, which would also be picked up by Falcon Sandbox and shown in the report.
Conclusion
Falcon Sandbox equips its users with the capability to detect advanced attacks that employ zero-day exploits, and as illustrated above, is able to provide detailed indicators of exploitation techniques that are used in the attack in a completely automated fashion. With Falcon Sandbox as part of the CrowdStrike Falcon® platform, it has access to its vast resources and expertise, and we are able to provide our customers with new and improved sandbox features on a regular basis. This further facilitates and automates the analysis of all types of attacks.
Samples
Original in-the-wild PDF file: SHA256: 4b672deae5c1231ea20ea70b0bf091164ef0b939e2cf4d142d31916a169e8e01 Modified PDF sample used for Falcon Sandbox analysis: SHA256: c319913bd07365503ee5925ac93b20967f5531b49f392b99d7e3619ae4d06477
Footnotes
1.welivesecurity by ESET: A tale of two zero-days. https://www.welivesecurity.com/2018/05/15/tale-two-zero-days 2. Microsoft Secure: Taking apart a double zero-day sample discovered in joint hunt with ESET. https://cloudblogs.microsoft.com/microsoftsecure/2018/07/02/taking-apart-a-double-zero-day-sample-discovered-in-joint-hunt-with-eset/
3. 360 Research: CVE-2018-4990 Adobe Reader 代码执行漏洞利用分析. https://ti.360.net/blog/articles/analysis-of-cve-2018-4990 4. Source Incite: Adobe, Me and an Arbitrary Free; Analyzing the CVE-2018-4990 Zero-Day Exploit. https://srcincite.io/blog/2018/05/21/adobe-me-and-a-double-free.html 5. 小刀志: Analysis of a Win32k Null Pointer Dereference by Matching the May Patch. https://xiaodaozhi.com/exploit/156.html
Learn More:
Download the Falcon Sandbox data sheet. Visit the Falcon Sandbox product web page. Read the Falcon Sandbox FAQ. Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)