- Cybercriminals more frequently target small and medium-sized businesses (SMBs) than large companies, often due to SMBs’ lack of security resources
- SMBs in the not-for-profit and transportation sectors face more high- and critical-severity attacks than those in other industries
- Industry-leading cybersecurity solutions for SMBs are essential to stop advanced attacks
Small and medium-sized businesses (SMBs) are more frequent targets of cybercrime than larger companies, industry research shows, and the trend is putting enormous financial pressure on small businesses. Some SMBs feel this pressure more strongly than others: CrowdStrike’s data shows sectors including not-for-profit and transportation are more frequently targeted with high- and critical-severity attacks than other industries.
SMBs — defined in this post as organizations with 250 or fewer employees — must contend with a unique set of challenges in defending against cybercrime. A 2021 Harvard Business Review article discussed strategies SMBs must employ and the obstacles they face:
Small, or non-existent, security teams are tasked with defending the business from the full range of cyber threats — from sophisticated, novel, and targeted campaigns to very fast moving smash-and-grab attacks — while managing an increasingly distributed workforce and complex digital infrastructure. The challenge extends beyond adequate resources — the threats these organizations face are too fast or too stealthy for humans to contend with and the number of new avenues for hackers to gain entry is growing at a rate too rapid for security teams to monitor.
The FBI joined CNBC’s Small Business Playbook event toward the end of 2022 to discuss the dramatic rise in cyberattacks on SMBs. As large companies have continued to invest in strengthening their security posture, officials explained, attackers evolved their tactics to pursue softer targets — a trend that increasingly puts SMBs in the crosshairs.
Small businesses often have less money to spend on building their defenses or responding to ransomware, malware and extortion attacks. It would seem this lack of resources would make SMBs unappealing targets for criminals seeking financial gain; however, attackers are still taking aim. Instead of targeting a large enterprise for one big payout, they’re finding success in hitting several small businesses to accumulate massive profits. SMBs were victims in the majority of cyberattacks the FBI’s Internet Crime Complaint Center (IC3) investigated in 2021, which in total led to $6.9 billion USD in losses.
Some adversaries don’t target SMBs for the funds they have, but because they are weak links in the supply chain that can be exploited to access larger organizations. Compromising an SMB’s systems may enable an attacker to infiltrate a more valuable business, a tactic seen in the 2013 Target breach. The adversary stole credentials from a third-party SMB vendor that provided HVAC services; as a result, they were able to breach Target and compromise 70 million credit and debit card accounts.
SMBs are low-hanging fruit for cybercriminals; however, not all SMBs are targeted to the same degree. There are some organizations at greater risk for a higher volume of attack attempts, more severe attacks, or both. This is clear in CrowdStrike platform telemetry from Sept. 8 to Dec. 7, 2022.
CrowdStrike Data Reveals the Most Frequently Targeted SMB Sectors
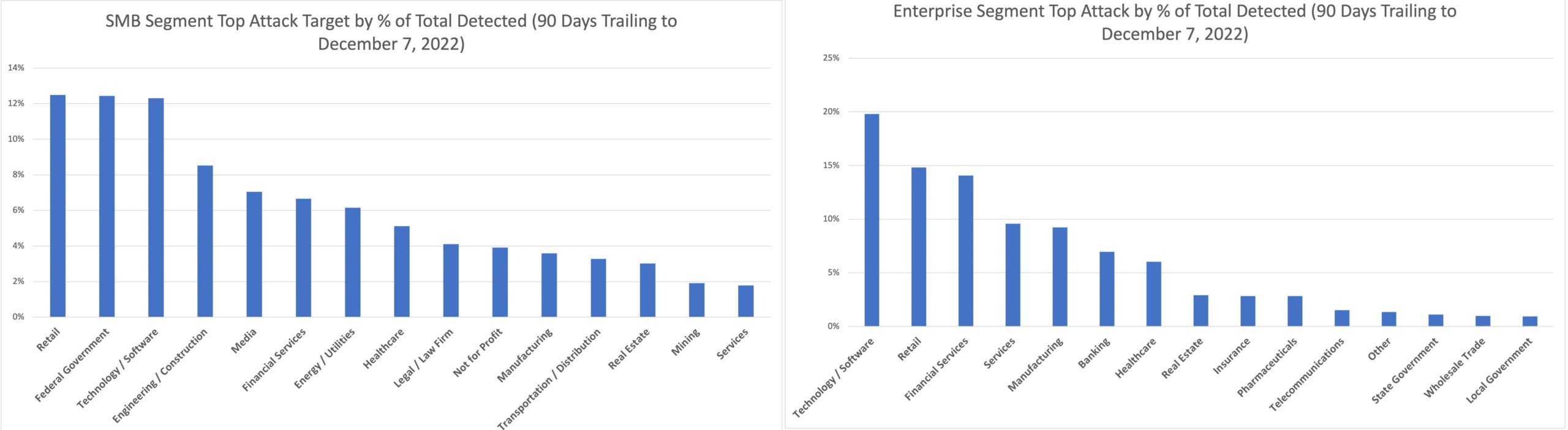 Figure 1. Percentage of total attacks for segment distributed across the top 15 SMB and enterprise segments, Sept. 8-Dec. 7, 2022 (click to enlarge) (Source: CrowdStrike platform telemetry)
Figure 1. Percentage of total attacks for segment distributed across the top 15 SMB and enterprise segments, Sept. 8-Dec. 7, 2022 (click to enlarge) (Source: CrowdStrike platform telemetry)The distribution of cyberattacks varies across industries when accounting for organization size. Media and engineering/construction are frequently hit among SMB targets, for example, while financial services and manufacturing are more often targeted among enterprise victims during the same time period.
More significant differences emerge when comparing SMB silos most frequently hit by high- and critical-severity attacks, which are more sophisticated, more dangerous and more difficult to defend against. While common attacks mostly revolve around garden-variety malware such as botnets, trojans and backdoors, critical-severity attacks usually involve detected hands-on-keyboard adversary activity and the use of sophisticated malware and vulnerabilities.
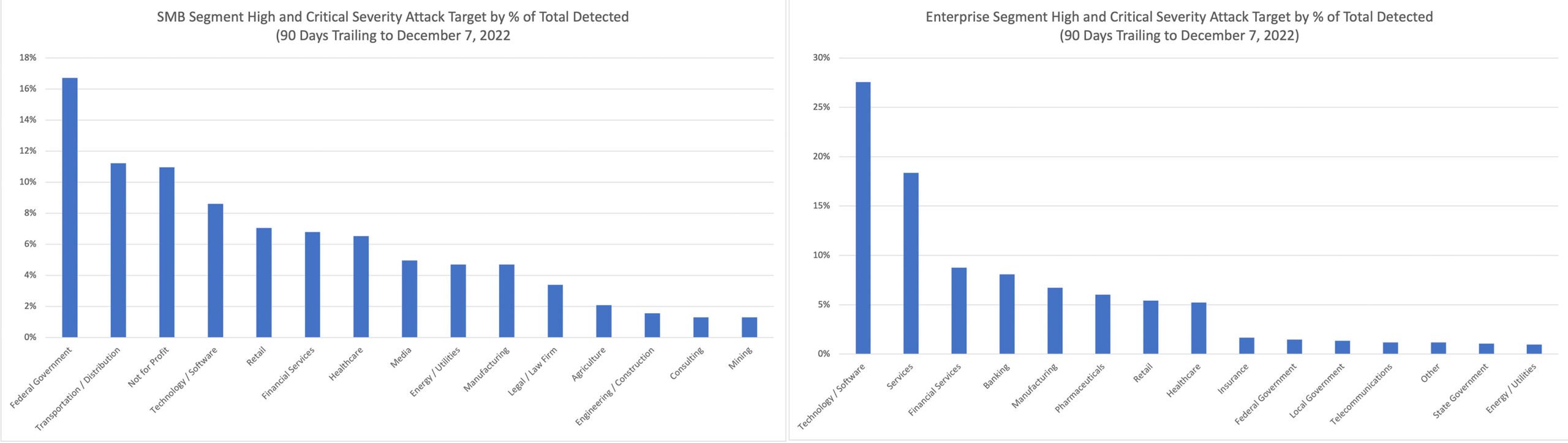 Figure 2. Percentage of total high and critical-severity attacks distributed across top 15 SMB and enterprise segments, Sept. 8-Dec. 7, 2022 (Click to enlarge) (Source: CrowdStrike platform telemetry)
Figure 2. Percentage of total high and critical-severity attacks distributed across top 15 SMB and enterprise segments, Sept. 8-Dec. 7, 2022 (Click to enlarge) (Source: CrowdStrike platform telemetry)When it comes to high- and critical-severity attacks targeting SMBs, federal government, transportation and not-for-profit organizations are the most common victims. While federal government organizations were also among the most frequently targeted entities overall, the transportation and not-for-profit industries were on the lower end for attack frequency. SMBs in these verticals are expected to offer services to larger organizations, acting as consultants or partners in providing specific services usually outsourced to them by larger entities. This role, combined with budget constraints and cybersecurity skills shortage, makes SMBs in these industries prime targets for supply chain attacks.
Why Not-for-Profits Are Targeted with High-Severity Cybercrime
In terms of total attacks detected, the SMB not-for-profit vertical barely squeezes into the top 10 targeted industries. But when it comes to sophisticated adversaries unleashing critical-severity attacks, SMB not-for-profit is the third biggest target — just barely topped by second-place transportation/distribution.
Why would cybercriminals target small and medium-sized not-for-profit organizations with high-severity attacks? We don’t typically think of not-for-profits, especially smaller ones, as rich targets, but there are multiple reasons why they are hit so hard:
- Not-for-profit organizations are often reluctant to take on continuing operating costs in order to direct as much money as possible to their cause, while also avoiding budget-related penalties. Some states have laws that prohibit spending on overhead expenses, such as Oregon’s 70% cap. As a result, they often run older versions of software and operating systems — increasing their vulnerability — while forgoing the expenses of trained IT security staff and cybersecurity software.
- With cybersecurity underfunded, staff training in best practices often suffers as well, leaving the organization more vulnerable to tactics such as phishing attacks.
- Not-for-profits can be treasure troves of valuable data such as donor credit card information. Some also operate online storefronts to sell merchandise and take donations, which leaves customer data at risk.
- Although they tend to spend less on operating expenses than commercial companies, not-for-profits are still part of the supply chain and can be exploited as the “weakest link” by attackers searching for a foothold to attack a larger organization.
- Because they are often centered around causes, not-for-profits and charities can be targeted by hackers with a political agenda, as seen in cyberattacks reported this year that disrupted the operations of European charities assisting Ukrainian refugees.
Given this context — possession of personal and financial data, supply chain access, outdated/underpowered defenses and involvement in causes that might make them a visible target — it’s not difficult to see why SMBs in the not-for-profit sector are more often hit by severe cyberattacks. CrowdStrike provides pro bono security software and services, including free access to the industry-leading CrowdStrike Falcon® platform, to protect not-for-profits, human rights organizations, journalists, think tanks and those fighting to protect digital freedoms and privacy— so they can focus on what matters most.
Recommendations and Predictions
The FBI advises all SMBs to significantly improve their security hygiene to protect themselves from becoming a cyberattack statistic. This includes adopting best practices such as strong password policies, multi-factor authentication, backups and applying security patches — but these are only some basic cybersecurity recommendations that should be implemented. SMBs should also train and test their employees to be aware of the security threats and social engineering attacks they face at work.
This CrowdStrike blog, written to mark Cybersecurity Awareness Month in October 2022, expands on ways that SMBs can protect themselves. This includes updating legacy tech, performing regular backups and investing in stronger cybersecurity protection.
Investing in modern endpoint protection technologies can do more than just help achieve cyber insurance initiatives — it can help SMBs achieve real-time, end-to-end visibility across their infrastructure, improve threat detection and resolution, enhance efficiency and improve outcomes. Having the right systems in place to detect and prevent any signs of intrusion as early as possible helps reduce any potential costs associated with the fallout of a breach.
Answering SMB Cybersecurity Shortfalls with CrowdStrike
The impact of an attack on a small business can be catastrophic: In 2021, the average cost of a data breach for a small business was pegged at $2.98 million USD. Ignoring cybersecurity is clearly not an option.
The answer is for SMBs to augment their existing IT security teams with the most advanced protection platform on the market, CrowdStrike Falcon. Employing an arsenal of state-of-the-art technologies such as artificial intelligence and machine learning, indicators of attack (IOAs) and behavioral blocking, CrowdStrike Falcon Go — our next-generation antivirus and device control exclusively for SMBs — defends against the full range of cyberattacks, including malware, ransomware and threats that spread using removable USB devices — while significantly reducing the false positives that waste valuable IT resources to investigate. Whether employees work from home or together in the office, CrowdStrike’s cloud-based solution keeps them secure from any location, on any network, without getting in the way of productivity with sluggish scans or on-premises equipment.
SMBs shouldn’t have to sacrifice or compromise on cybersecurity solutions because of a lack of resources, technology or security experts. Turning to managed cybersecurity services, such as CrowdStrike Falcon® Complete, small businesses can get a team of security experts dedicated to protecting their business, with 24/7 cybersecurity monitoring, response and remediation. With dedicated cybersecurity experts extending existing teams and leveraging a platform that provides full visibility across any infrastructure, small companies can immediately benefit from a mature security program without the difficulty, burden and costs of building one internally.
Proof of the effectiveness of the Falcon platform in protecting SMBs can be seen in the results of a recent survey conducted by TechValidate. You can read the full results here, but highlights include:
- Over 70% of SMB respondents chose CrowdStrike because it is a “proven security leader recognized by major analysts” and delivers “best-in-class protection by independent testing.”
- 73% of respondents said CrowdStrike improved the efficiency of their security operations
- 70% of respondents reported faster IT and security performance
In short, employing CrowdStrike Falcon Go eliminates friction caused by difficult-to-manage legacy security solutions, enables SMBs to protect and secure all their devices wherever they are, and allows them to monitor and govern USB accessories that could put their network at risk.
Additional Resources
- Explore the CrowdStrike small business bundles.
- Learn how the powerful CrowdStrike Falcon® platform provides comprehensive protection across your organization, workers and data, wherever they are located.
- Test CrowdStrike next-gen AV for yourself with a free trial of Falcon Prevent™.
- CrowdStrike’s Small Business Cybersecurity Survival Guide to learn how to identify threats and stop them — even with limited resources.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)













































