CrowdStrike Teams with the MITRE Engenuity Center for Threat-Informed Defense to Develop ATT&CK Defense for IaaS
November 17, 2022
Liviu Arsene - Joel Spurlock - Sergey Kozlov - Manoj Ahuje Endpoint Security & XDR
- CrowdStrike is a Research Partner in the MITRE Engenuity Center for Threat-Informed Defense and also a Research Participant in the Center’s Defending IaaS with ATT&CK® research project
- This project’s goal was to develop effective methods and strategies for defending against adversaries attacking infrastructure as a service (IaaS) across the cloud, containers and Linux
- Researchers identified and reviewed 510 techniques used by adversaries to attack IaaS, and the project resulted in the release of ATT&CK tool updates, a collection of 277 unique techniques in STIX format and a new methodology and process for defending IaaS with ATT&CK
As a Research Partner with the MITRE Engenuity Center for Threat-Informed Defense, CrowdStrike was also a Research Participant in the Center’s recently completed project: Defending IaaS (Infrastructure as a Service) with ATT&CK. CrowdStrike researchers worked alongside fellow Research Participants and with the Center’s team to identify and review hundreds of techniques used by adversaries for IaaS environment attacks, including insider threat and pre-attack.
The CrowdStrike Falcon® platform leads the industry in cloud security. Our researchers bring extensive firsthand experience and expertise in breach prevention, making the participation of CrowdStrike analysts and researchers a valuable project resource. In addition, CrowdStrike is a longtime supporter of the MITRE ATT&CK framework, engaging in partnerships with MITRE that have yielded multiple advancements for the Center in 2022 including February’s Insider Threat Knowledge Base and October’s Cloud Analytics project.
The Center has announced that the IaaS project was completed successfully, resulting in the release of ATT&CK tool updates, a collection of 277 unique techniques in STIX format and a new methodology and process specific to defending IaaS with ATT&CK.
The Need for Defending IaaS Matrix
IaaS is a cloud computing model that allows users to utilize a third-party cloud service provider’s virtualized compute resources. These can include compute, network and storage in addition to the layered monitoring, administrative and security services offered by the IaaS provider. This model reduces the need for physical on-premises servers and allows clients to move their application workloads to the cloud, which can quickly scale up or down capacity as needed. However, it adds complexity to the security posture. The cloud service provider is responsible for managing the IaaS cloud infrastructure, but the client is responsible for installing, configuring, managing and securing any software, applications, operating systems and middleware that has been installed on the infrastructure.
The goal of this project was to aid security teams in defending against adversarial attacks targeting IaaS environments.
The Enterprise ATT&CK matrix applicable to an organization’s IaaS currently must be broken down further to platform-specific matrices. Organizations must focus on each matrix that is applicable to their technology stack in order to defend against the adversaries that are targeting all of the available attack surfaces.
Organizations using IaaS must understand that adversaries can use any number of malicious techniques to compromise their environment, whether it is in the cloud management layer, the container or the hosted infrastructure layer. It’s not sufficient to solely focus on one matrix, even if it might seem to be the most obvious attack vector. For example, attacks originating inside the container can escape the container, move laterally to other valuable locations, then attack cloud management layers in the same kill chain. An example of container escape in the wild is cr8escape, which CrowdStrike discovered earlier this year.
For protectors, it’s necessary to have a combined view of relevant tactics, techniques and procedures (TTPs) that attackers can use against their IaaS infrastructure. This knowledge is required to formulate a uniform strategy, security evaluation, gap analysis and detection coverage to be able to beat the attackers on multiple fronts — easier said than done when adversaries are continually coming up with new TTPs and the existing ATT&CK framework is not optimized for IaaS environments.
To solve this challenge, CrowdStrike worked with the Center and other research participants to add and combine relevant TTPs specifically applicable to IaaS infrastructure. The goal was to develop an ATT&CK matrix that makes it easy for organizations to understand the full range of techniques and defend against attacks made against that environment.
Figure 1 shows the scope of an IaaS platform, where defenders need to take into account their cloud, container and Linux platforms. It allows removal of unnecessary techniques like T1546.002, which is part of the traditional Linux ATT&CK matrix and irrelevant to cloud infrastructure. Remember, simplification is part of making this approach as straightforward as possible so weeding out the irrelevant TTPs is important.
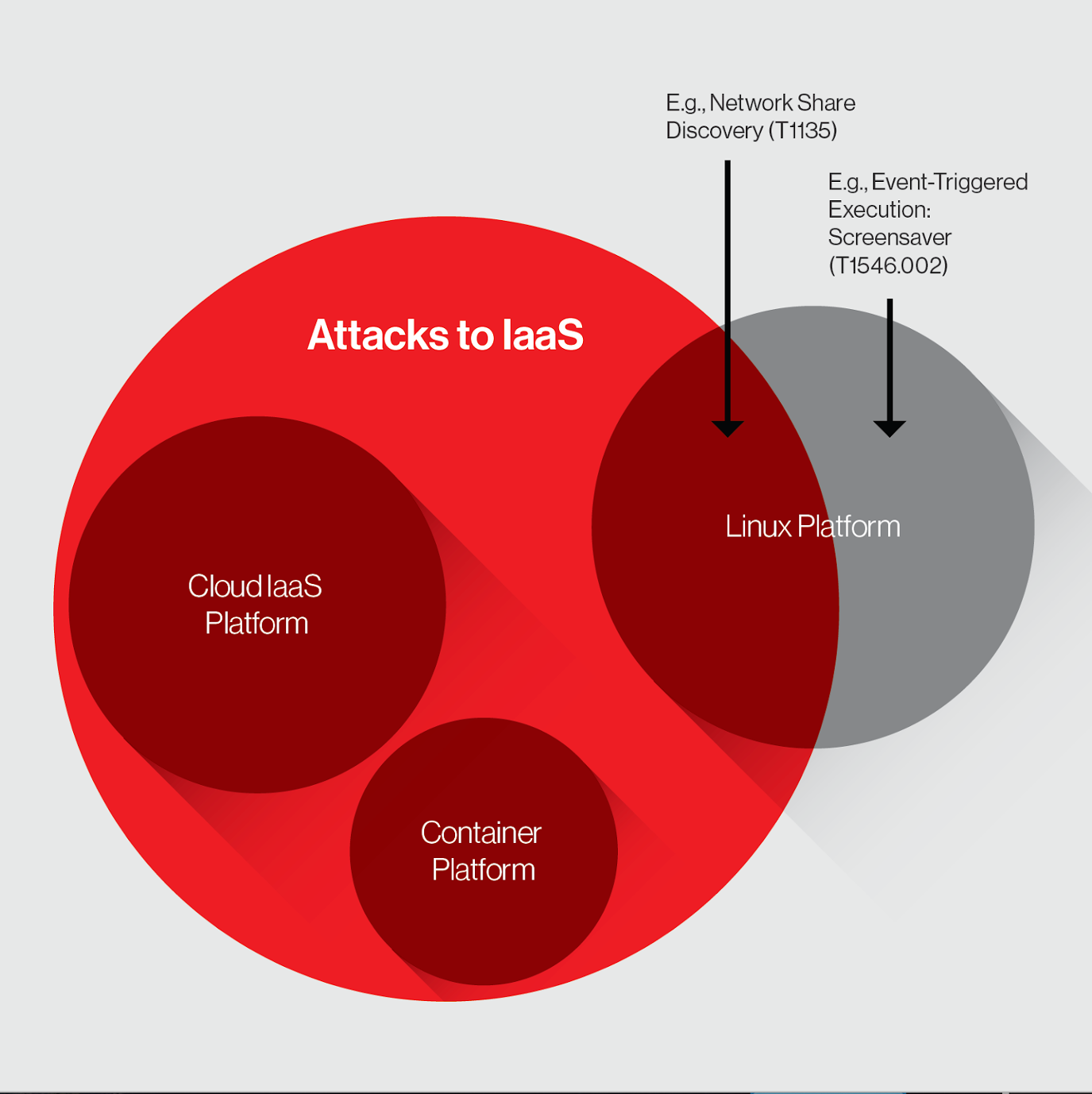
Figure 1. Scope of defending the IaaS matrix across the platforms to eliminate irrelevant techniques
Methodology and Use of Defending IaaS Matrix
CrowdStrike researchers — along with the Center and other Research Participants — identified and reviewed 510 techniques used by adversaries to attack the IaaS environment. The distribution of techniques was as follows:
- Linux: 280
- Cloud (IaaS): 67
- Containers: 36
- Insider Threat: 50
- PRE (-ATT&CK): 77
The team then eliminated 137 techniques, narrowing the list to a subset of relevant techniques. Participants used three key focus areas during their evaluations — physical, environmental and operational — to determine whether a technique is relevant to the IaaS environment.
Physical criteria are used to determine if the collection will include techniques based on physical characteristics of the system. Techniques in this section exclude attacks that target the underlying physical technology. Examples of these components include physical servers, firmware, hypervisor and some elements of networking.
Environmental criteria are used to define exceptional aspects or characteristics that are specific to the environment. This section intends to address nuances of adversary behavior that may vary, depending on the environment’s technology deployment or operations. For example, techniques that do not align with common best practices in IaaS — automated provisioning, scaling and data recovery — are excluded.
Operational criteria are used to determine if the collection will include techniques based on functional characteristics such as how the system is intended to operate.
Mature organizations can consume STIX bundles, though for many organizations ramping up in cloud security, it’s necessary to have an easier way to consume the Defending IaaS Matrix.
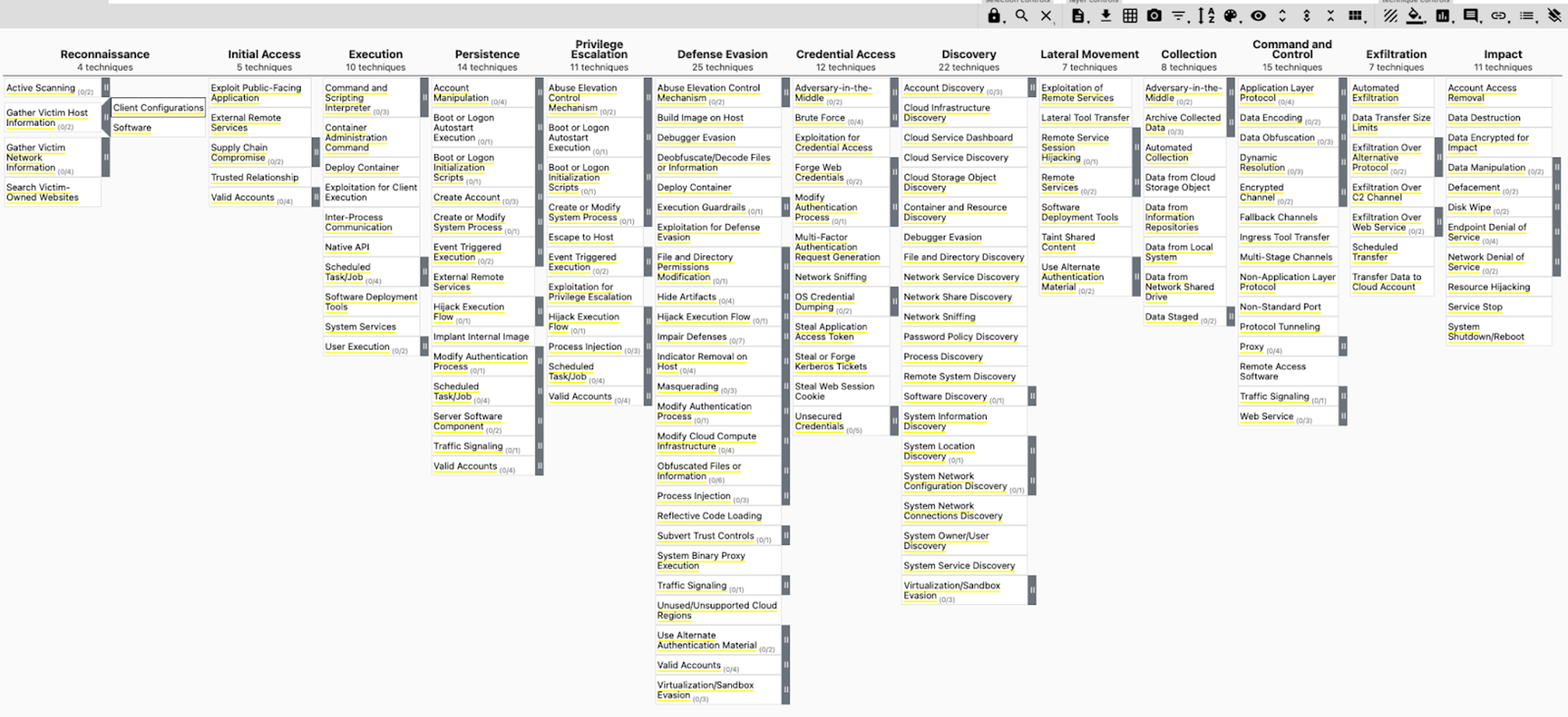
With the feedback from CrowdStrike and other participants, MITRE hosted an instance of ATT&CK Navigator for the Defending IaaS Matrix. Figure 2 shows the initial layer “DIWA” present alongside Enterprise, Mobile and ICS layers. Once “DIWA” is selected, the Defending IaaS Matrix opens as a layer as shown in Figure 3. Here, with the help of ATT&CK Navigator, the layer can be further customized to the organization’s technology stack and needs in order to focus on the most important aspects of defending against adversaries.
Figure 2. MITRE ATT&CK Navigator layer DIWA — Defending IaaS with ATT&CK
Tools to Help with Adoption of MITRE ATT&CK Framework
To address increasing requirements and community interest, MITRE has released multiple tools to expand the adoption of the ATT&CK framework. With continuous feedback from CrowdStrike, other research participants and community members, MITRE released a new version of the following tools, delivering numerous improvements, features and ways to track adversary kill chains.
ATT&CK Workbench
ATT&CK Workbench is the self-hosted tool that allows adding, customizing and exporting the collection of techniques. Workbench can ingest a collection as a STIX bundle from a provider like MITRE. The tool allows the creation of a collection tailored to the organization’s needs from scratch or the modification of existing collections as needed to match an organization’s technology stack.
ATT&CK Flow
The ATT&CK Flow tool can be used to build a graphical representation of attacker behavior and sequence of events. This can help an organization analyze an attack in detail and create its own representation of malicious behavior used by adversaries. Doing so supports incident response work and allows for a deep dive into a malicious campaign.
CrowdStrike’s Ongoing Commitment to MITRE and Cybersecurity Leadership
CrowdStrike continues to deepen its commitment to the industry through our work with MITRE Engenuity. The market-leading Falcon platform achieved the highest detection coverage in the first-ever closed-book MITRE ATT&CK Evaluations for Security Service Providers, achieving 99% detection coverage by conclusively reporting 75 of the 76 adversary techniques.
CrowdStrike also recently became a Research Partner in the MITRE Engenuity Center for Threat-Informed Defense, deepening our commitment in working with ecosystem partners to advance cybersecurity research in the public interest.
Additional Resources
- Learn how you can stop cloud breaches with CrowdStrike unified cloud security for multi-cloud and hybrid environments — all in one lightweight platform.
- For an in-depth examination of how attackers target the cloud, download “Protectors of the Cloud: Combating the Rise in Threats to Cloud Environments.”
- Read about adversaries tracked by CrowdStrike in 2021 in the 2022 CrowdStrike Global Threat Report and in the 2022 Falcon OverWatch™ Threat Hunting Report.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.