Attackers are continually taking advantage of Microsoft products, and this month’s vulnerabilities and subsequent patch updates reflect that reality. One particular zero-day vulnerability, CVE-2021-40444, involves MSHTML and allows an attacker to create nefarious documents to gain access to a user’s computer remotely. Other critically scored vulnerabilities affecting Microsoft products include Windows WLAN AutoConfig Service, Azure Services and Windows Scripting Engine. Attackers are becoming more persistent and educated, and vendors may not provide updates for all Critical vulnerabilities — making it more vital than ever for organizations to review their prioritization protocols and lean in on their security posture to protect themselves from a breach.
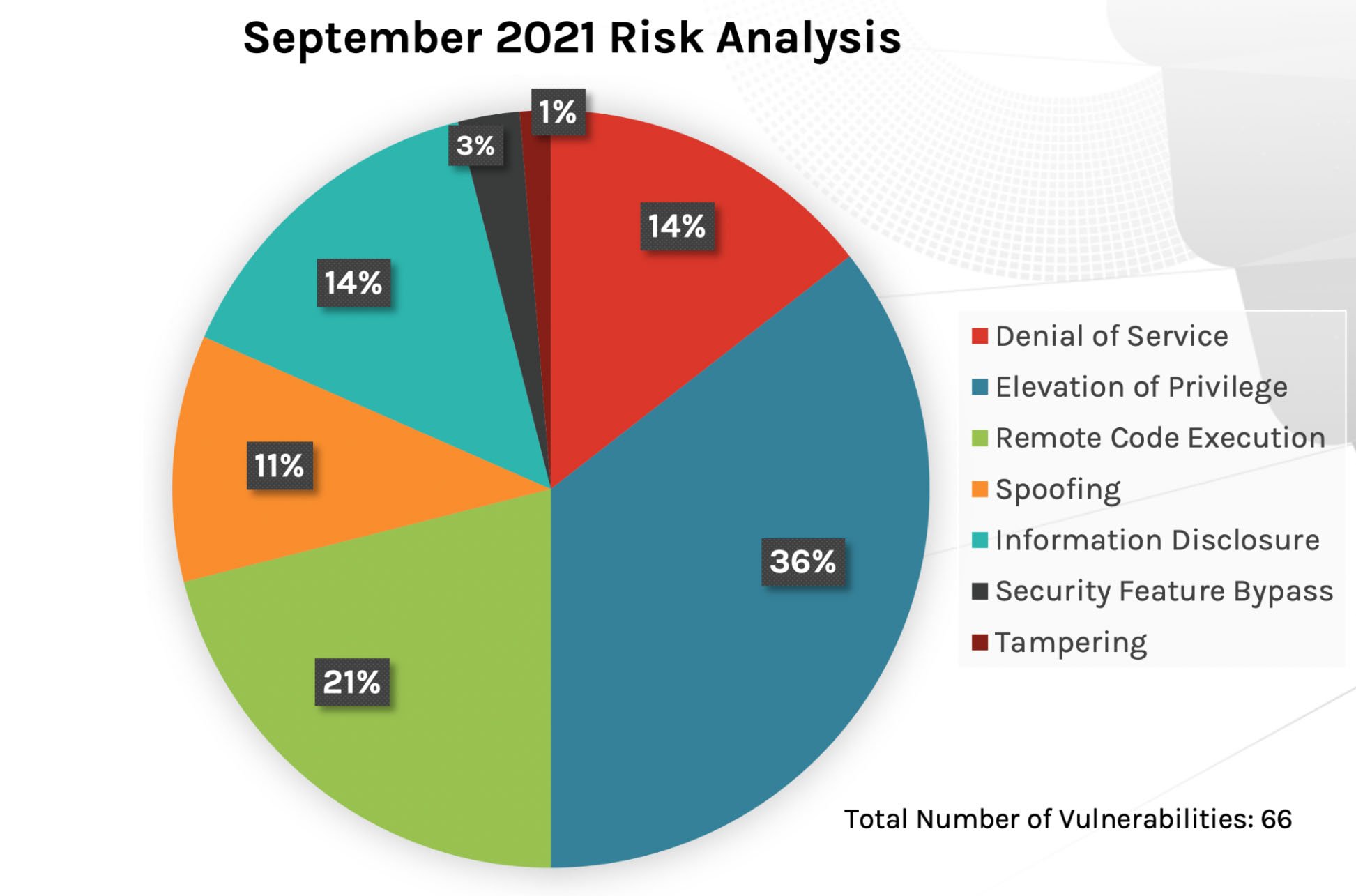 Figure 1. Breakdown of September 2021 Patch Tuesday attack impact
Figure 1. Breakdown of September 2021 Patch Tuesday attack impact
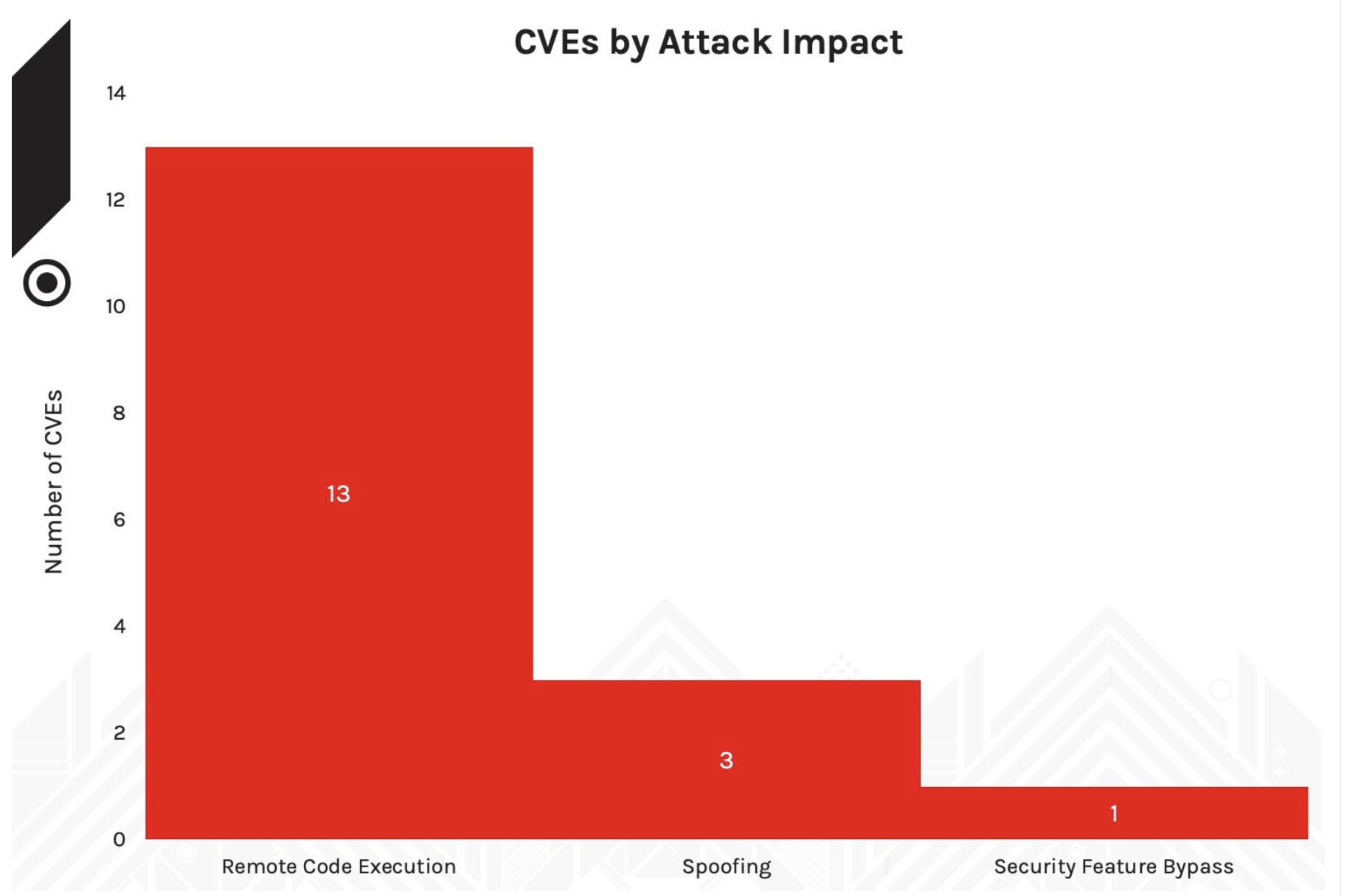 Figure 2. Attack impact for Critical CVEs, February-May 2021
Of the Microsoft product families that received updates this month (see Figure 3), it appears that the same products are receiving a similar number of patches as in July and August 2021: Windows, Extended Security Update program (ESU) and Microsoft Office products. Therefore, if your organization heavily uses one of these Microsoft product areas, you might want to examine your patching policies and prioritize those that pose more risk.
Figure 2. Attack impact for Critical CVEs, February-May 2021
Of the Microsoft product families that received updates this month (see Figure 3), it appears that the same products are receiving a similar number of patches as in July and August 2021: Windows, Extended Security Update program (ESU) and Microsoft Office products. Therefore, if your organization heavily uses one of these Microsoft product areas, you might want to examine your patching policies and prioritize those that pose more risk.
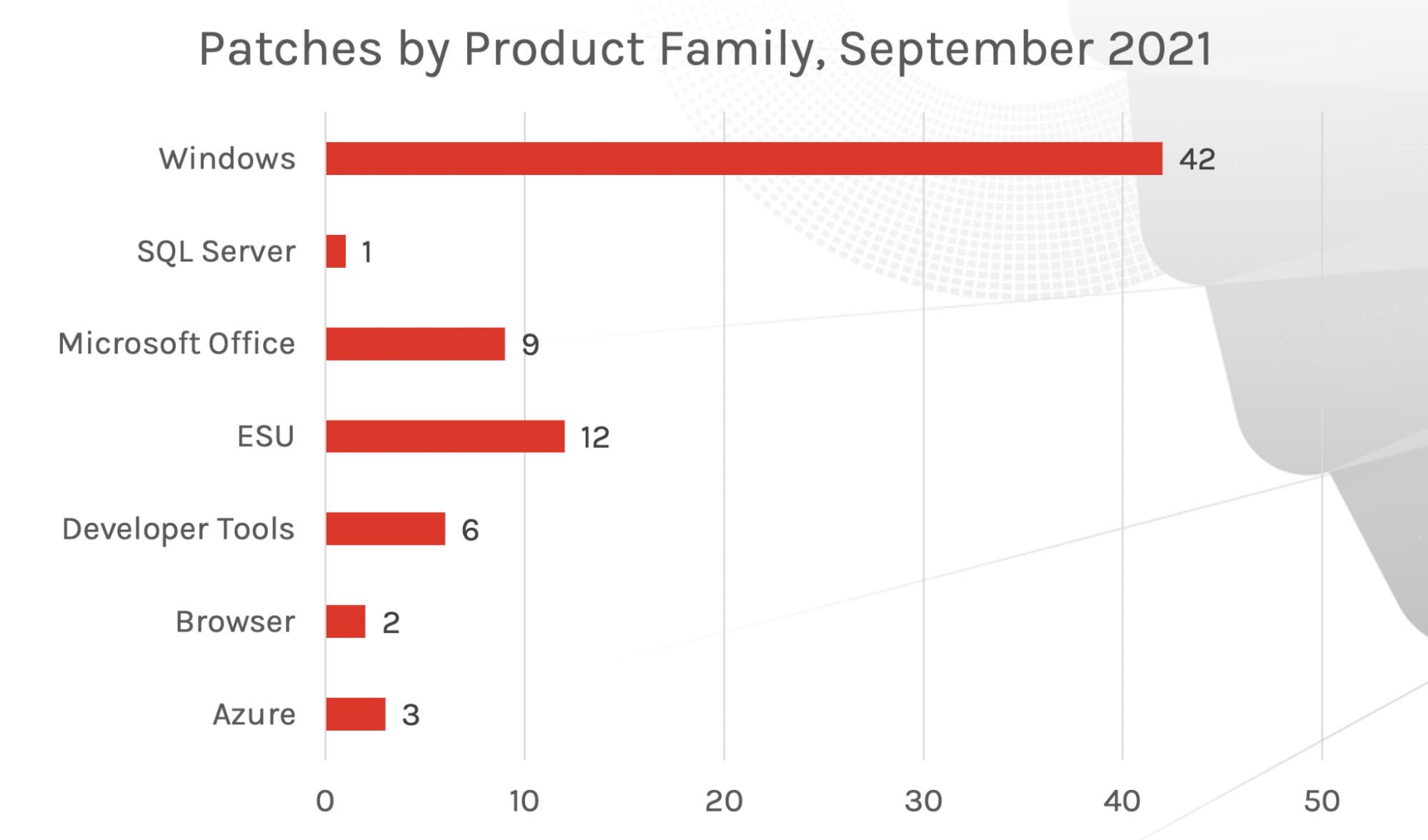 Figure 3. Patches by product family, September 2021
Figure 3. Patches by product family, September 2021
Critical Vulnerabilities To Prioritize
This month, there are three Critical vulnerabilities that organizations should consider prioritizing: CVE-2021-38647, affecting Azure services; CVE-2021-36965 within the Windows WLAN AutoConfig Service; and CVE-2021-26435, affecting Windows Scripting Engine. While there are other Critical-scored vulnerabilities and patches, these three have the highest CVSS scores and CrowdStrike recommends patching them quickly. Of the other Critical vulnerabilities to consider, CVE-2021-30632 — affecting Google Chrome — should be one to monitor. As discussed in CrowdStrike’s deep dive analysis into the patches offered by Microsoft in the first half of 2021, Chromium-based Edge products continue to see exploitation.
Other critical vulnerabilities to consider:
Additional Resources
New Patches for 66 Vulnerabilities
This month’s Patch Tuesday updates include fixes for 66 vulnerabilities. Not surprisingly, remote code execution and elevation of privilege are still favored attack vectors for threat actors. For the first part of 2021, remote code execution and spoofing led the way in the number of vulnerabilities (as shown in Figure 2), but in the last couple of months, privilege elevation has been a rising attack vector — read the August 2021 Patch Tuesday update for more details. Figure 1. Breakdown of September 2021 Patch Tuesday attack impact
Figure 1. Breakdown of September 2021 Patch Tuesday attack impact Figure 2. Attack impact for Critical CVEs, February-May 2021
Figure 2. Attack impact for Critical CVEs, February-May 2021 Figure 3. Patches by product family, September 2021
Figure 3. Patches by product family, September 2021In-the-Wild Exploit for CVE-2021-40444
CVE-2021-40444 is a remote code execution vulnerability in MSHTML, which is used to process webpage data in many settings, including Microsoft Office documents. The vulnerability was disclosed the week of September 6, 2021, and was reportedly discovered in the wild by researchers. Microsoft released workarounds to disable ActiveX and document preview, but within a couple of days of using the malicious samples, researchers were able to thwart these workarounds and gain remote code execution. This vulnerability does not involve any memory corruption, making the exploit chain relatively stable to the current mitigations. The exploits have already started popping up on GitHub and forums. Because of the exploit’s stability and the wide availability even before the patch, this could be the next Equation Editor CVE-2017-11882, which to date is still the top exploit we see in the wild for Microsoft Office, even four years after getting patched. Updates have been released as part of the Patch Tuesday as far back as Windows 7 and Windows Server 2008. Although Microsoft rated this as Important, CrowdStrike analysts recommend that you patch this CVE as quickly as possible. This situation is escalating to a shelfware exploit.
| Rank | CVSS Score | CVE | Description |
| Important | 8.8 | CVE-2021-40444 | Microsoft MSHTML Remote Code Execution Vulnerability |
Critical Vulnerabilities To Prioritize
This month, there are three Critical vulnerabilities that organizations should consider prioritizing: CVE-2021-38647, affecting Azure services; CVE-2021-36965 within the Windows WLAN AutoConfig Service; and CVE-2021-26435, affecting Windows Scripting Engine. While there are other Critical-scored vulnerabilities and patches, these three have the highest CVSS scores and CrowdStrike recommends patching them quickly. Of the other Critical vulnerabilities to consider, CVE-2021-30632 — affecting Google Chrome — should be one to monitor. As discussed in CrowdStrike’s deep dive analysis into the patches offered by Microsoft in the first half of 2021, Chromium-based Edge products continue to see exploitation.
- CVE-2021-38647. Microsoft disclosed CVE-2021-38647, a remote code execution vulnerability in Open Management Infrastructure (OMI), which powers some Azure services. A patch for this vulnerability was offered in August 2021 in the open-source codebase. It could potentially affect millions of endpoints, but customers don’t need to install any patches unless they self-host OMI. All Azure services have been mitigated.
- CVE-2021-36965. CVE-2021-36965 is a Critical remote code execution vulnerability in Windows WLAN AutoConfig Service. This service manages the configuration of connection to wireless APs automatically. No user interaction is required to exploit this — and in light of the ubiquity of wireless-capable devices, this vulnerability could result in a very large gap that customers should consider patching immediately. Patches have rolled out for platforms from Windows 7 and Windows Server 2008 up to more recent versions.
- CVE-2021-26435. Another critical vulnerability released for September 2021 Patch Tuesday is CVE-2021-26435, a memory corruption vulnerability in the Windows Scripting Engine. Using this vulnerability, an attacker can trick a user into browsing a controlled website or open a malicious document. Microsoft has released patches for platforms as old as Windows 7 and Windows Server 2008.
| Rank | CVSS Score | CVE | Description |
| Critical | 9.8 | CVE-2021-38647 | Open Management Infrastructure Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2021-36965 | Windows WLAN AutoConfig Service Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2021-26435 | Windows Scripting Engine Memory Corruption Vulnerability |
- CVE-2021-30632. Microsoft released a patch for CVE-2021-30632, a Google Chrome CVE that was reported to be exploited in the wild. Patches were released for Chromium-based Microsoft Edge as Google offered a patch for this vulnerability this Monday. Customers who use this product will not need to install a patch, and Edge will be automatically updated if configured.
- CVE-2021-36967. CVE-2021-36967 is an elevation of privilege vulnerability in Windows WLAN AutoConfig Service. Unlike CVE-2021-36965 discussed above, this vulnerability does require user interaction and is therefore rated Important with a CVSS score of 8. Keep in mind that this vulnerability is only applicable to Windows 10 and Server 2016 and newer.
- CVE-2021-36968. Microsoft also disclosed CVE-2021-36968, which had been previously disclosed but not exploited in the wild. It's an elevation of privilege vulnerability in Windows DNS. Microsoft has labeled that exploitation is Less Likely for this vulnerability. Patches for this particular CVE are available only for Windows 7 and Windows Server 2008.
- CVE-2021-36955. Another vulnerability to consider prioritizing is CVE-2021-36955, a Windows Common Log File System Driver elevation of privilege vulnerability. It has been classified as Exploitation More Likely — no user interaction is required, and it’s a low attack complexity bot that does not require network access. This mix of factors makes this vulnerability potentially attractive to attackers and should be considered relevant in the patching process.
| Rank | CVSS Score | CVE | Description |
| Important | 7.8 | CVE-2021-30632 | Chromium: Out of bounds write in V8 |
| Important | 8 | CVE-2021-36967 | Windows WLAN AutoConfig Service Elevation of Privilege Vulnerability |
| Important | 7.8 | CVE-2021-36968 | Windows DNS Elevation of Privilege Vulnerability |
| Important | 7.8 | CVE-2021-36955 | Windows Common Log File System Driver Elevation of Privilege |
Review Patching Protocols — Because Exploited Vulnerabilities Are Holding Steady
This year has been an ongoing challenge with Microsoft products — many vulnerabilities have seen in-the-wild exploitation with no patch issued from Microsoft to protect the organizations using these products. As with the PrintNightmare situation, attackers have been taking full advantage of a range of vulnerabilities related to various Microsoft products, and there is no sign that activity is slowing down. More than 20 Microsoft vulnerabilities in 2021 have been exploited, meaning that prompt patching is a vitally important activity. When a vendor does not provide a patch or share knowledge on how to mitigate, then an organization must lean on its other security processes to stay secure and avoid breaches. Bottom line: Patch, mitigate and secure.Learn More
Watch this video on Falcon Spotlight™ vulnerability management to see how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- Learn more on how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- See how Falcon Complete stops Microsoft exchange server zero-day exploits.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Read last month’s Patch Tuesday for more information on critical vulnerabilities your organization should prioritize.
- Learn about the recent Baron Samedit vulnerability and CrowdStrike’s custom dashboard.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)


















































