Phishing is the weapon of choice for many adversaries. And it’s easy to understand why: Users fall victim to attacks in under 60 seconds on average, novice cybercriminals can launch effective phishing campaigns thanks to off-the-shelf phishing kits and generative AI, and above all, it works — 71% of organizations reported at least one successful attack in 2023.
To defend against rampant phishing attacks, organizations require robust systems to detect, investigate and respond to phishing threats. This is where CrowdStrike Falcon® Next-Gen SIEM and CrowdStrike Falcon® Fusion SOAR can deliver tremendous value, allowing you to quickly stop threats from one unified platform.
This blog shares how Falcon Next-Gen SIEM helps stop phishing attacks and why we’re offering 10GB/day of free email data ingestion to jumpstart your next-gen SIEM journey.
Detect Phishing Attacks with Falcon Next-Gen SIEM
Falcon Next-Gen SIEM empowers you to detect phishing fast by consolidating your endpoint data and third-party data on the AI-native CrowdStrike Falcon® cybersecurity platform. With a robust ecosystem of data connectors and parsers, Falcon Next-Gen SIEM simplifies the ingestion of third-party data so you can quickly detect and stop attacks.
Legacy SIEMs burden security teams with complex and unwieldy lists of correlation rules, often developed years or decades ago. These rules create a flood of false positives, forcing specialized detection engineers to waste time tuning and maintaining them. Overwhelmed, many organizations turn to managed security service providers (MSSPs) with mixed results.
Falcon Next-Gen SIEM cuts through the pitfalls of outdated correlation rules. It delivers laser-accurate detection for both Falcon telemetry — including endpoint, cloud and identity data — and third-party logs. Crafted by CrowdStrike experts with industry-leading adversary research, our out-of-the-box correlation rules align with MITRE ATT&CK®, helping you detect attack techniques across the cyber kill chain. Your team can easily customize rules with a unified language for search, parsing and dashboards.
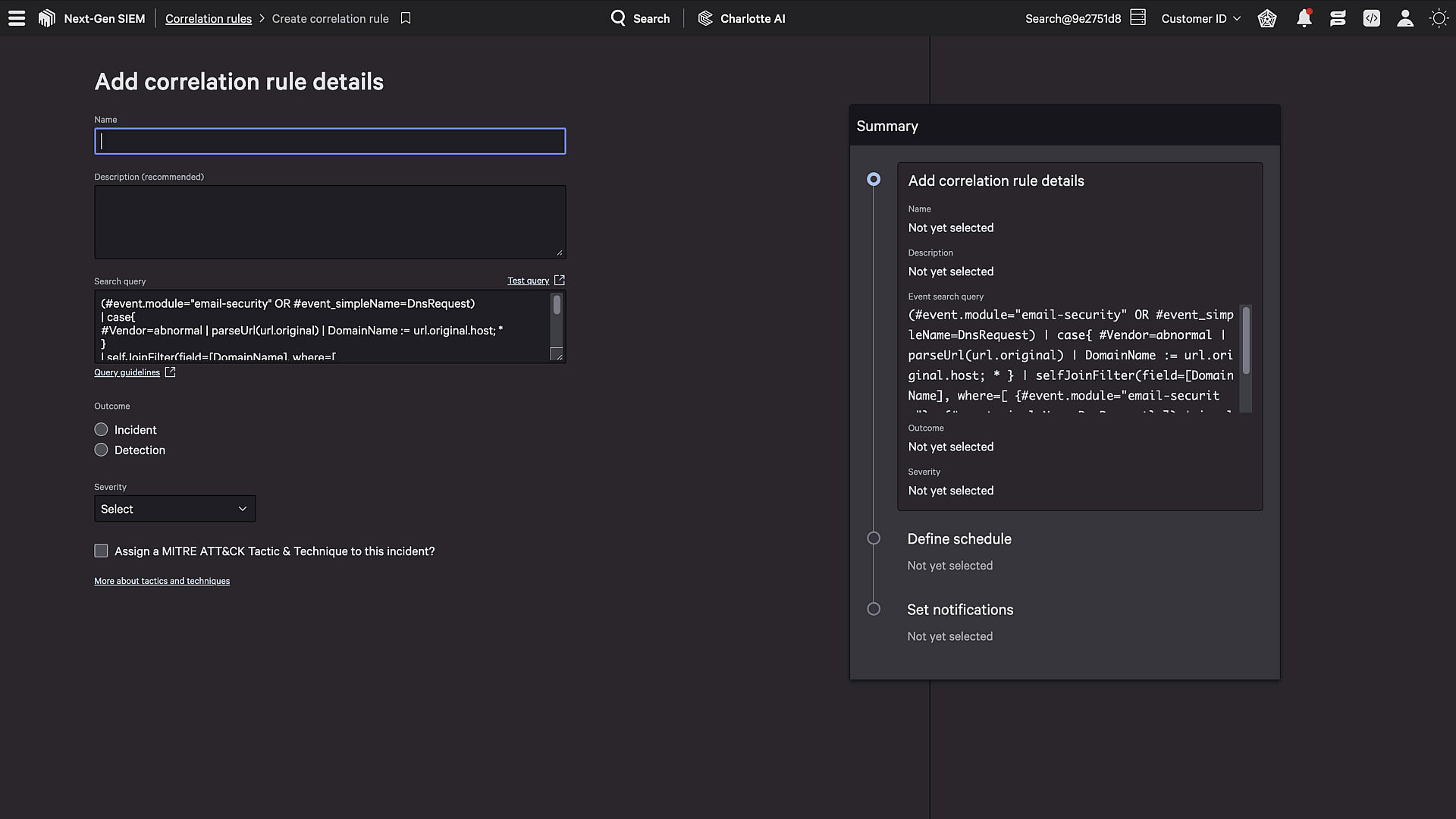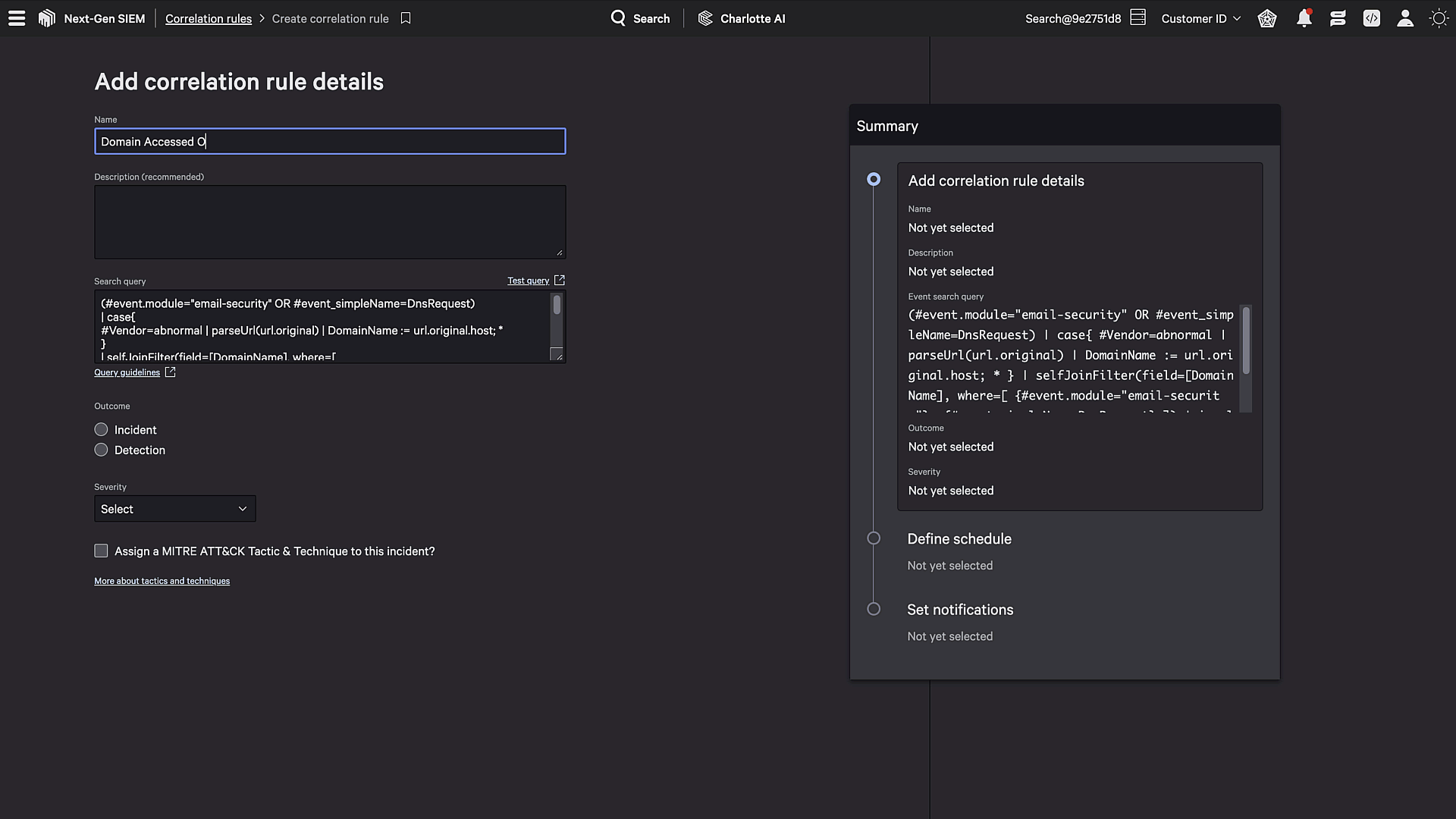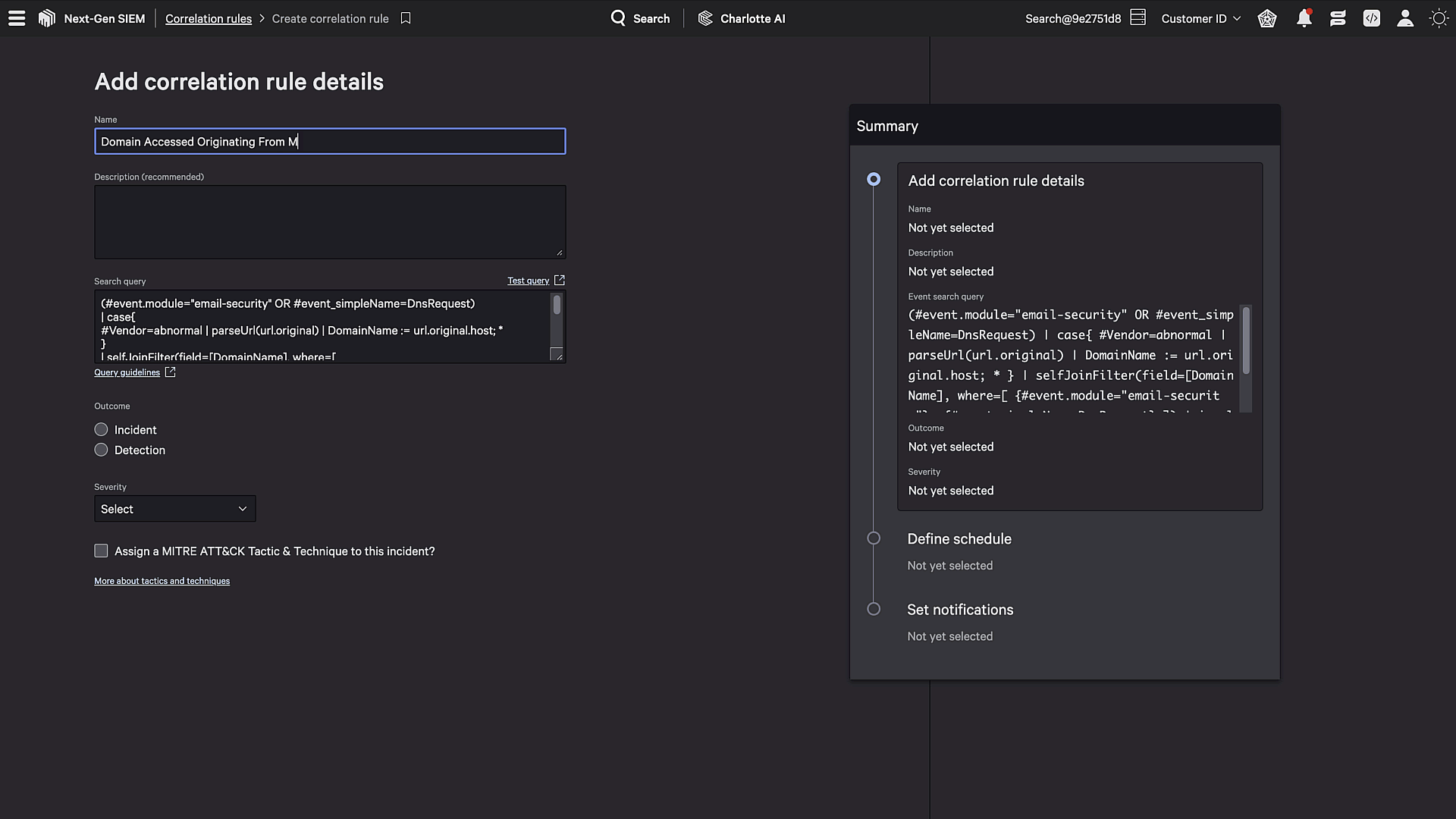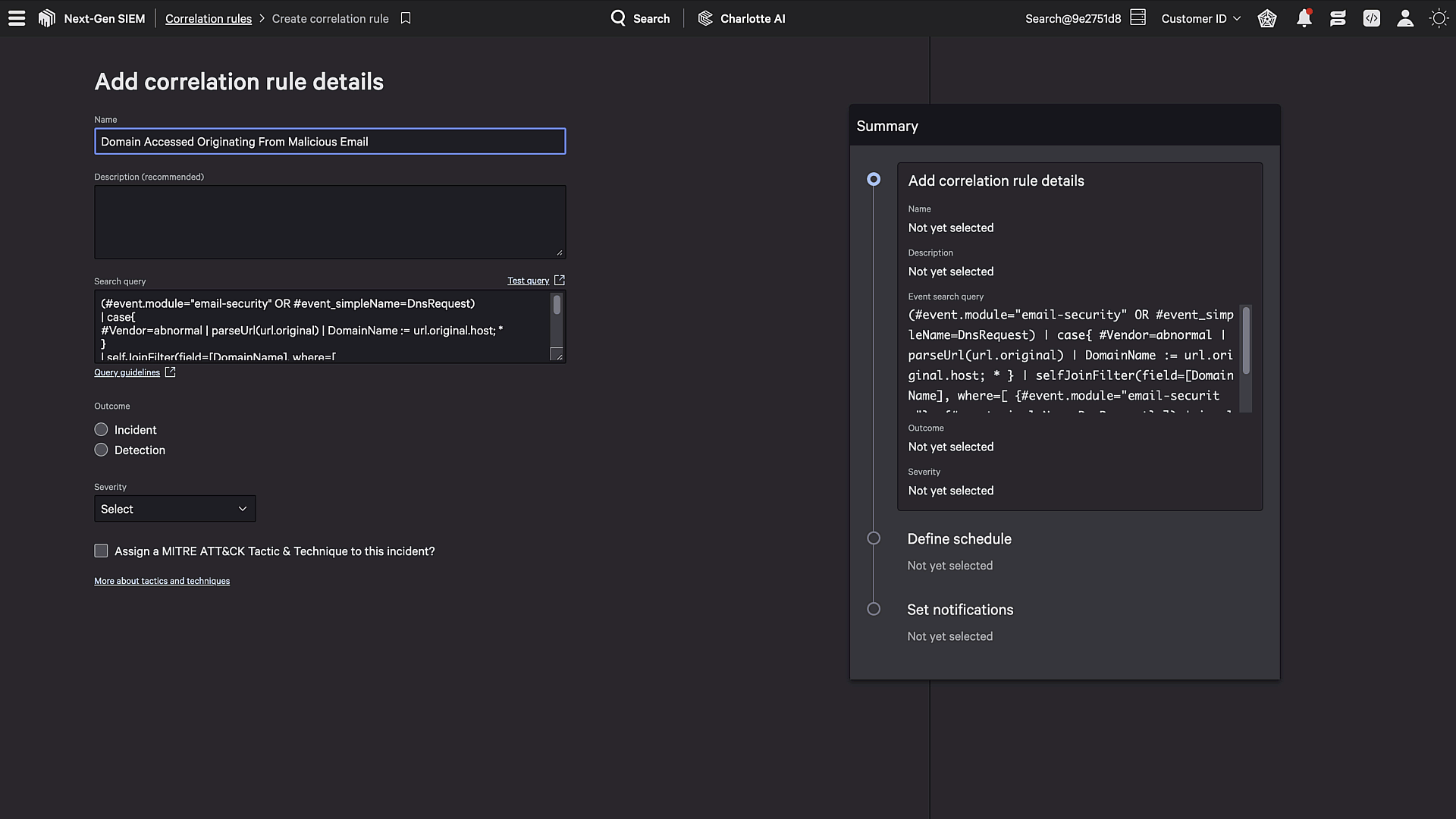
Figure 2. Falcon Next-Gen SIEM correlation rules are flexible and use the same common language used across all third-party data.
Monitor Threats with Live Dashboards
Next, it’s helpful to discuss how live dashboards can help you identify top threats and analyze trends to improve your security posture.
Falcon Next-Gen SIEM’s dashboard capability allows you to create custom dashboards from queries, providing at-a-glance data visualization for quick decision-making. You can view aggregated data from various email sources based on common fields and use interactions to drill down into vendor-specific data and fields.
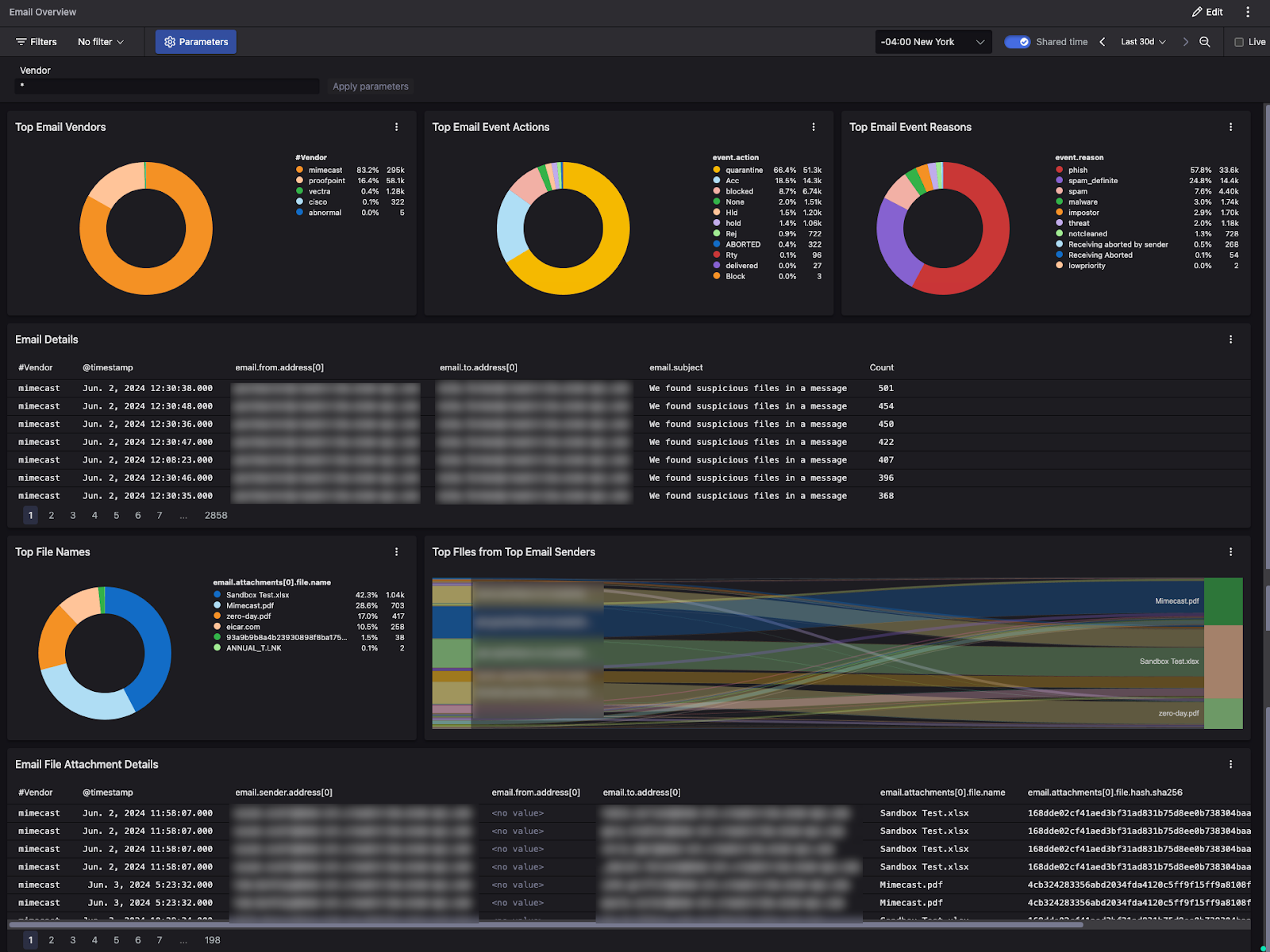
Figure 4. Aggregate and visualize your data with the intuitive dashboard builder in Falcon Next-Gen SIEM.
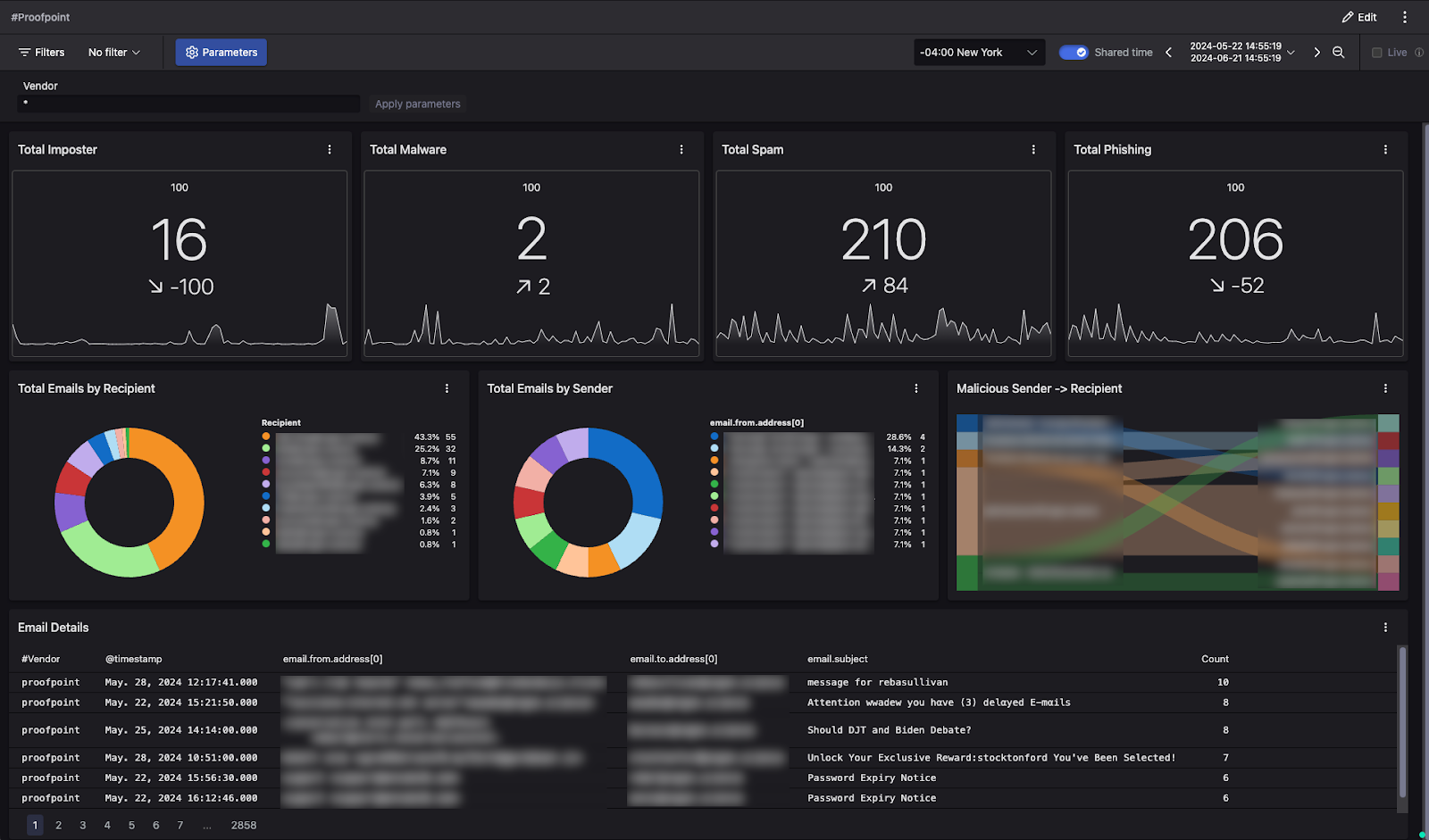
Figure 5. Leverage dashboard interactions to zoom in to different views of your data, including vendor-specific fields.
Investigate and Respond with Falcon Fusion SOAR
Workflow automation offers numerous benefits, including reduced mean time to respond (MTTR), enhanced team efficiency and cost savings.
Phishing is an ideal starting point for workflow automation due to the repetition in phishing investigations and the need for consistent responses and swift action. With Falcon Fusion SOAR, the no-code orchestration, automation and response capability built into the Falcon platform, you can quickly reap the benefits of automation, empowering your team to respond more effectively to phishing threats.
With more than 125 pre-built actions and the ability to execute actions directly on the endpoint with CrowdStrike Falcon® Insight XDR, Falcon Fusion SOAR lets you orchestrate incident response across your SOC. You can easily build workflows to automatically investigate the contents of suspicious emails or reset compromised credentials, allowing your team to save valuable time and focus on higher priorities. Workflows can run on-demand or trigger automatically based on a detection or a predefined schedule.
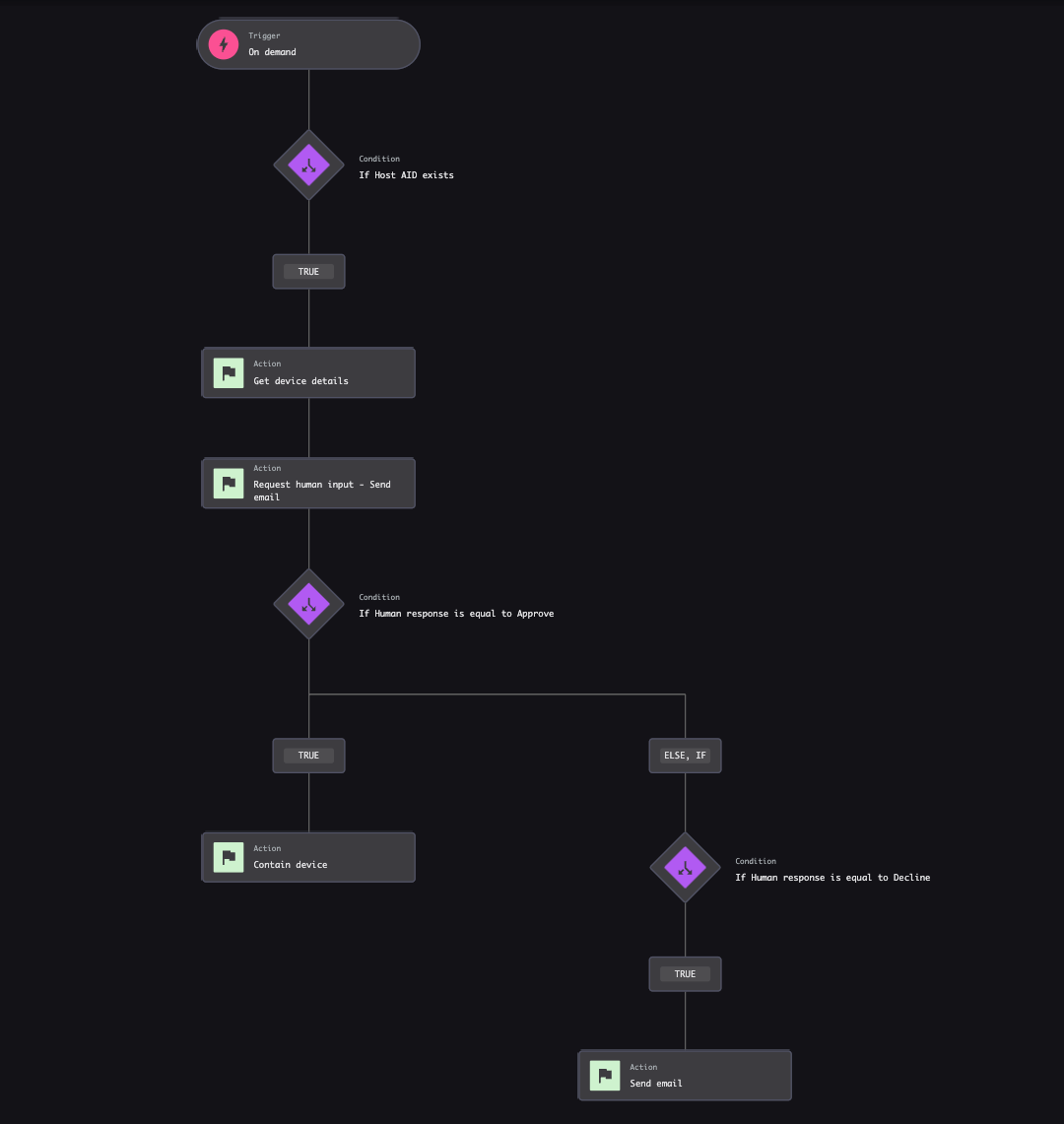
Figure 6. Falcon Fusion SOAR lets you quickly build workflows by choosing the trigger, defining the conditions and configuring actions.
Falcon Fusion SOAR provides out-of-the-box playbook templates to simplify workflow automation. Predefined templates can be easily customized to align to your organization’s security policies and technologies.
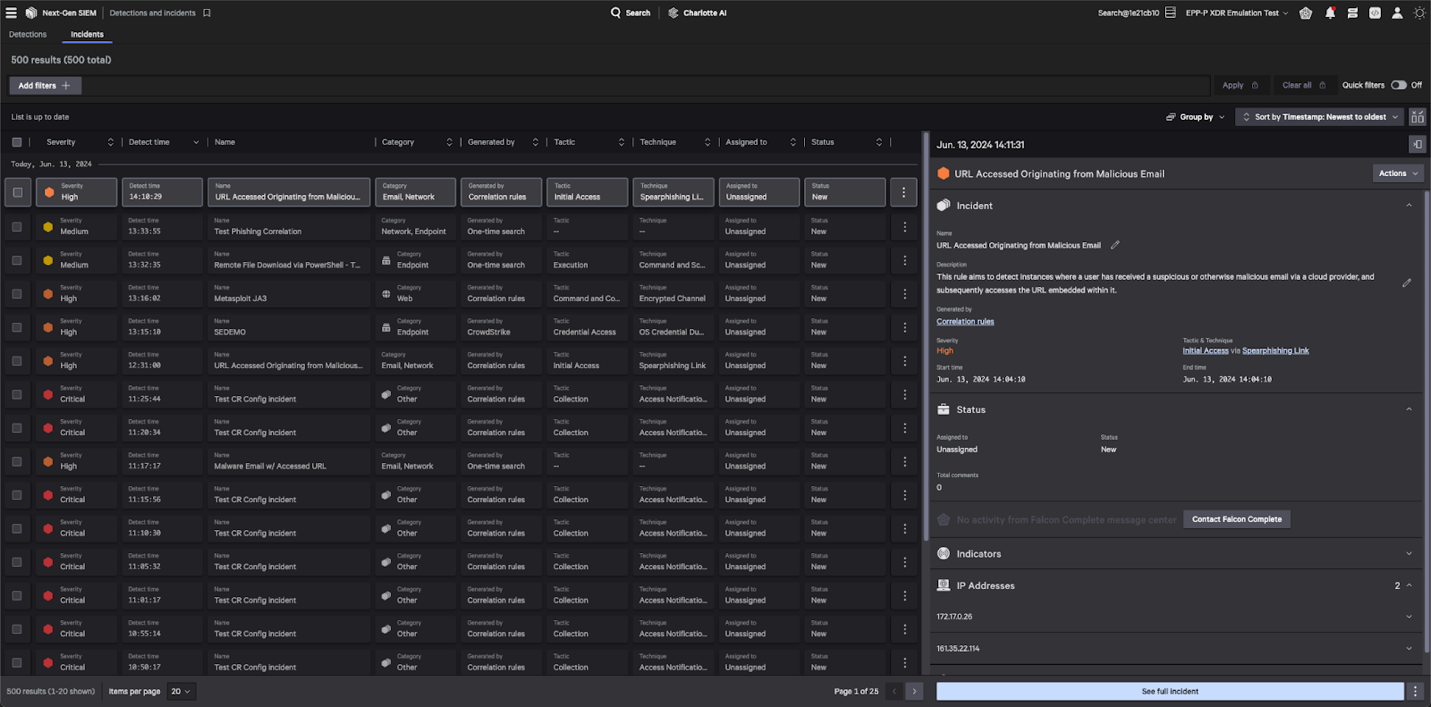
The Incident Workbench enhances incident visualization and team collaboration. It illustrates the relationships and connections between entities, providing a clear view of the attack’s progression. Clicking on the graph reveals detailed information on each entity, including sender details, malicious URLs, indicators of compromise and relevant threat actors.

Figure 7. The Incident Workbench enhances investigation with incident visualization and expedites response with on-demand workflow automation.
A prebuilt SOAR dashboard helps you monitor team performance, executed workflows, related detections and MTTR trends. By continuously measuring your phishing KPIs, you can make ongoing improvements to your detection and response capabilities, shifting from a reactive to a proactive security approach.
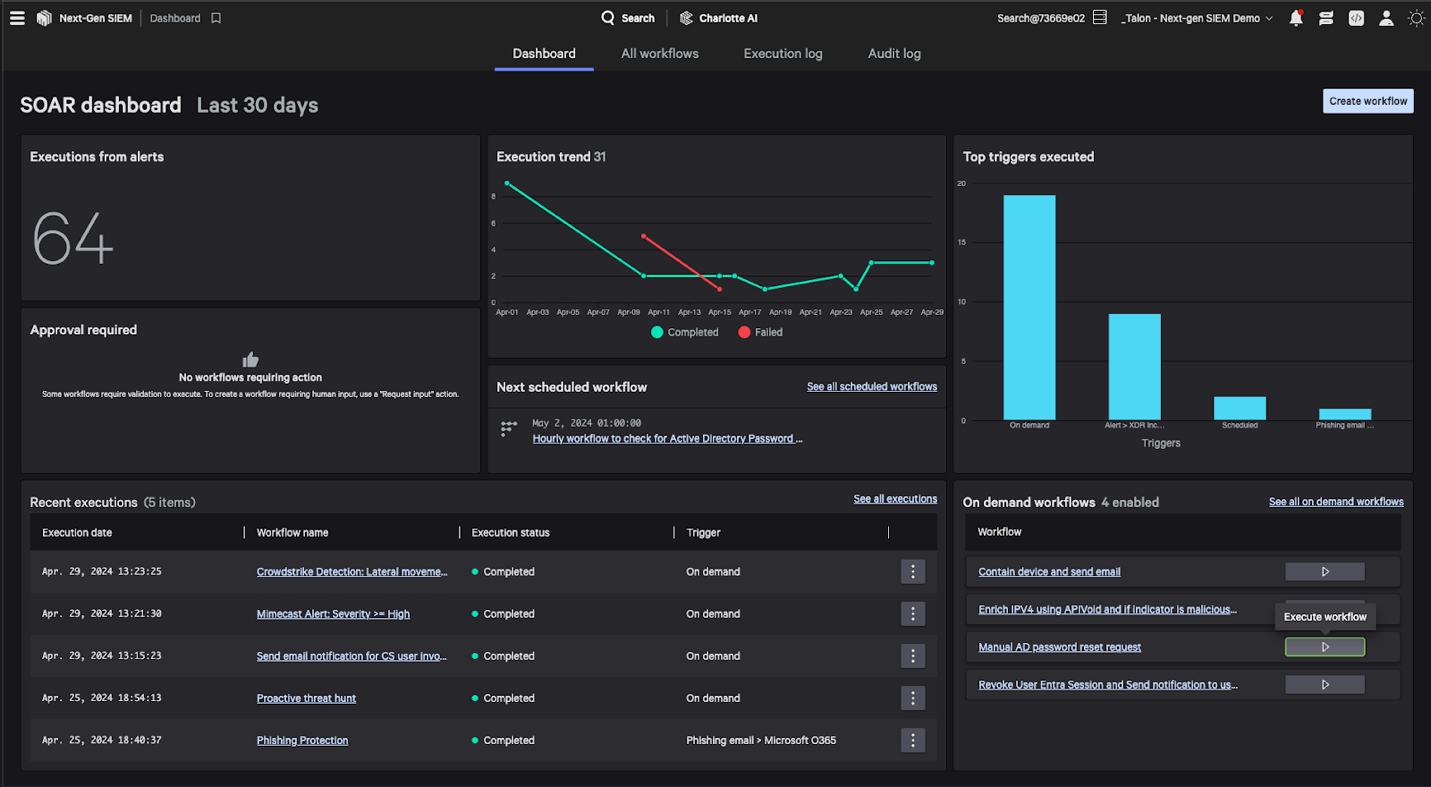
Figure 8. Continuously measure and monitor SOAR KPIs to improve your security posture with the new metrics dashboard in Falcon Fusion SOAR.
Get Started with 10GB of Free Email Data Ingestion
Phishing attacks remain a persistent threat to organizations. The Falcon platform seamlessly integrates data, AI, workflow automation and threat intelligence on a unified platform for full visibility and protection against cyberthreats, including phishing attacks.
Email data can be a rich source of information for uncovering malicious activity. Starting today, Falcon Insight XDR customers get 10GB per day of free email data ingestion to kickstart their SOC transformation and realize the power of combining Falcon platform data with third-party data to detect phishing schemes, accelerate investigations and meet compliance requirements.
Contact your sales representative or technical account manager to learn more about this offering.
Additional Resources
- Read this technical blog to start ingesting email data into Falcon Next-Gen SIEM.
- Learn about key benefits of next-gen SIEM in the Falcon Next-Gen SIEM data sheet.
- Sign up to attend our Next-Gen SIEM Showcase.
- Read the Complete Guide to Next-Gen SIEM to learn how to modernize your SOC.
- Want to learn more about Falcon Fusion SOAR? Read the data sheet or visit the product page.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)
![Endpoint Protection and Threat Intelligence: The Way Forward [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/GK-Blog_Images-1)