The term “social distancing” has swept across the world. It is an incredibly important response measure during a pandemic. The term is not new; just over 100 years ago, cities across the U.S. introduced measures to limit public gatherings due to the outbreak of the Spanish flu. A century later, we’re dealing with COVID-19, and the global benefits of social distancing are clear to see: It remains one of the best ways we can fight the new coronavirus and prevent transmission.
Social distancing in the time of COVID-19 means most of us are nearly always at home — and we’re online more than we have ever been. Unfortunately, one of the things we have to deal with when we’re online in this current environment is the significant increase in COVID-19-themed scams and financially motivated criminals who are preying on people’s fears and need for information during this global pandemic.
While social distancing is one of the most important ways we can slow the spread of COVID-19 in the physical world, in the digital one, we need a different approach. It begins with the right cybersecurity technologies. Think of these technologies as highly effective masks that filter out digital pathogens and as highly scalable tests that can flag malicious behavior on IT infrastructure so you can more easily contain it.
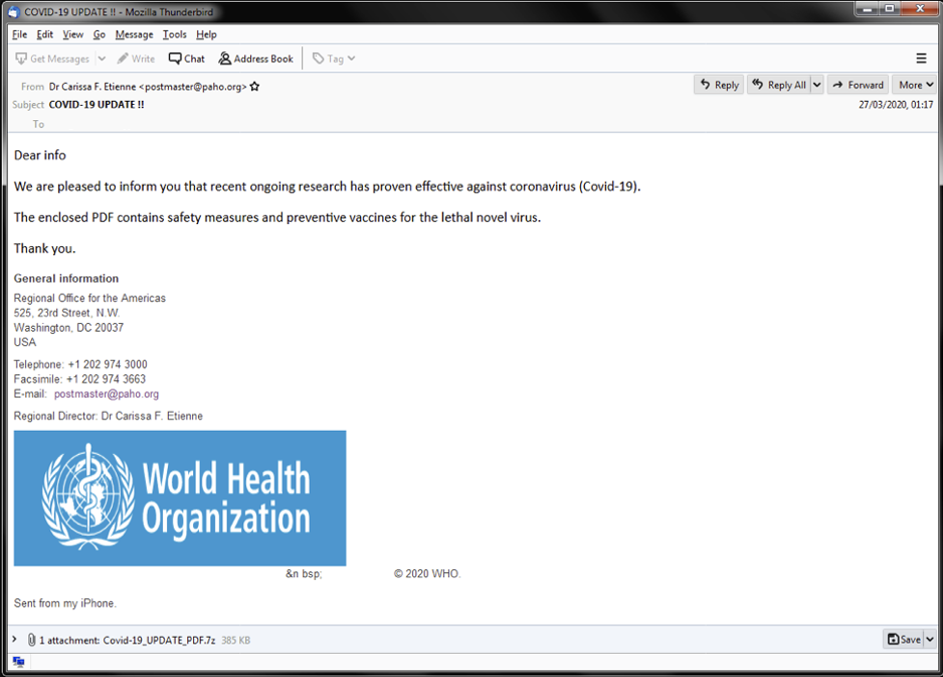 Figure 1. COVID-19-themed phishing email purportedly from World Health Organization; WHO did not send this e-mail
Without the right measures in place, people who fall victim to one of these digital scams could unintentionally cause their personal — or worse, their employers’ — business data to be encrypted and held for ransom. The impact of ransomware on a struggling business could be devastating during the current global economic downturn.
Over the last 12 months, CrowdStrike® experts have observed an increase in incidents of ransomware, a maturation in the tactics used, and growing ransom demands from eCrime actors (escalating from an average of $600K in 2018 to over $15M in 2019). One of the disturbing trends that we believe is here to stay is what we call “big game hunting” (BGH) — the shift toward large ransom payouts characterized by low-volume, high-return criminal targeting. With the potential to cause financial ruin during the current global pandemic, financially motivated cyberattackers see COVID-19 as the perfect business opportunity.
One of the challenges in dealing with ransomware is that conventional signature-based endpoint protection has proven to be woefully inadequate. Organizations continue to be impacted by ransomware because their incumbent technology failed. In response, point solution technology evolved to include additional measures such as whitelisting, indicators of compromise (IOCs) or machine learning to add a degree of improvement over signature-based detection. However, they each have their own limitations.
For example, in the case of fileless and zero-day ransomware, all of those countermeasures would prove unreliable in detecting or preventing attacks. Furthermore, relying on IOCs, which by definition can only be detected after a compromise has occurred, typically ends up alerting IT to the attack after it’s too late to make a difference — in most instances, by the time firm IOCs present themselves, the ransomware has already encrypted its target data.
Over the last 18 months, CrowdStrike has seen a rapid increase in criminal actors following BGH methods to target vulnerable companies. BGH eCrime actors target networks, utilize advanced techniques to circumvent security tools and, when the time is right, deploy ransomware to the network. In some cases, BGH actors were on a network for up to three months before the ransomware attack was launched. This ability to lay low and stay quiet is extremely important to understand, especially because now some organizations may be taking a higher risk when it comes to protecting their employees while working from home.
Adversaries have also moved past the traditional methods used to spread ransomware. In 2019, enterprise-scale ransomware operations were the most lucrative enterprise for eCrime adversaries. Ransom demands soared into the millions, and already in 2020, there have been significant ransomware attacks around the world. In the first three months of 2020 alone, the volume of hands-on-keyboard intrusions reached 57% of the levels set for all of 2019. With half of this activity attributed to eCrime, this trend will continue — especially during the COVID-19 crisis.
Figure 1. COVID-19-themed phishing email purportedly from World Health Organization; WHO did not send this e-mail
Without the right measures in place, people who fall victim to one of these digital scams could unintentionally cause their personal — or worse, their employers’ — business data to be encrypted and held for ransom. The impact of ransomware on a struggling business could be devastating during the current global economic downturn.
Over the last 12 months, CrowdStrike® experts have observed an increase in incidents of ransomware, a maturation in the tactics used, and growing ransom demands from eCrime actors (escalating from an average of $600K in 2018 to over $15M in 2019). One of the disturbing trends that we believe is here to stay is what we call “big game hunting” (BGH) — the shift toward large ransom payouts characterized by low-volume, high-return criminal targeting. With the potential to cause financial ruin during the current global pandemic, financially motivated cyberattackers see COVID-19 as the perfect business opportunity.
One of the challenges in dealing with ransomware is that conventional signature-based endpoint protection has proven to be woefully inadequate. Organizations continue to be impacted by ransomware because their incumbent technology failed. In response, point solution technology evolved to include additional measures such as whitelisting, indicators of compromise (IOCs) or machine learning to add a degree of improvement over signature-based detection. However, they each have their own limitations.
For example, in the case of fileless and zero-day ransomware, all of those countermeasures would prove unreliable in detecting or preventing attacks. Furthermore, relying on IOCs, which by definition can only be detected after a compromise has occurred, typically ends up alerting IT to the attack after it’s too late to make a difference — in most instances, by the time firm IOCs present themselves, the ransomware has already encrypted its target data.
Over the last 18 months, CrowdStrike has seen a rapid increase in criminal actors following BGH methods to target vulnerable companies. BGH eCrime actors target networks, utilize advanced techniques to circumvent security tools and, when the time is right, deploy ransomware to the network. In some cases, BGH actors were on a network for up to three months before the ransomware attack was launched. This ability to lay low and stay quiet is extremely important to understand, especially because now some organizations may be taking a higher risk when it comes to protecting their employees while working from home.
Adversaries have also moved past the traditional methods used to spread ransomware. In 2019, enterprise-scale ransomware operations were the most lucrative enterprise for eCrime adversaries. Ransom demands soared into the millions, and already in 2020, there have been significant ransomware attacks around the world. In the first three months of 2020 alone, the volume of hands-on-keyboard intrusions reached 57% of the levels set for all of 2019. With half of this activity attributed to eCrime, this trend will continue — especially during the COVID-19 crisis.
 Figure 1. COVID-19-themed phishing email purportedly from World Health Organization; WHO did not send this e-mail
Figure 1. COVID-19-themed phishing email purportedly from World Health Organization; WHO did not send this e-mailMultiple Methods of Defense
To combat the escalating level of ransomware threat sophistication, CrowdStrike uniquely combines multiple methods into a powerful and integrated approach that protects endpoints more effectively. Specifically, the CrowdStrike Falcon® next-generation endpoint protection platform uses an array of complementary prevention and detection methods to defend against the menace of ransomware:- Blocking of known ransomware to weed out common threats with minimum effort
- Exploit blocking to stop the execution and spread of ransomware via unpatched vulnerabilities
- Machine learning to detect previously unknown or zero-day ransomware
- Indicators of attack (IOAs) to identify and block additional unknown ransomware in the early stages of an attack, before it can fully execute and inflict damage — and to protect against new categories of ransomware that do not use files to encrypt victim systems
- Falcon OverWatchTM, a dedicated team of elite, trained threat hunters, alerting you and detecting even the most sophisticated criminal actors
Employing the Power of IOAs
Among these methods, IOAs are critically important in dealing with ransomware because they are fundamentally different from other methods and represent a unique proactive capability. With IOAs, Falcon looks for early warning signs that an attack may be underway before adversaries actually accomplish their objectives. Those signs can include code execution, attempts at being stealthy and lateral movement, to name a few. IOAs are concerned with the execution of these steps, their sequence and their dependency, recognizing them as indicators that reveal the true intentions and goals of the attacker. IOAs focus on these signs rather than on the specific tools malware attackers use to accomplish their objectives, since those can change very quickly, as illustrated by the recent surge of ransomware variants. This approach is particularly potent against fileless attacks, which are starting to be used by more attackers in place of traditional malware. In the case of fileless ransomware, malicious code is either introduced in a native scripting language or is written straight into memory by legitimate tools such as PowerShell without being written to disk. This is another example where in most cases, signature-based methods will not protect the end user. In contrast, IOAs detect the sequences of events that ransomware must undertake in order to complete its mission. This renders moot malware methods such as hiding through leveraging "known good" system binaries, packing and binary obfuscation. In addition, IOAs provide a reliable way to prevent ransomware from deleting backups. This gives users the ability to restore encrypted files, even if file encryption began before the ransomware was stopped. All of this makes IOAs a major breakthrough for ransomware prevention. Instead of trying to fight the futile battle of detecting malware based on the ever-changing contents and characteristics of a ransomware program, IOAs monitor, detect and stop the effects of what ransomware is attempting to achieve before any damage is done. Using this approach, one IOA can cover many variants and versions of multiple ransomware families, including new ones as they are released in the wild. A real-world example of the success of this approach is the global WannaCry ransomware attack that hit multiple countries on Friday, May 12, 2017. CrowdStrike Falcon® proactively protected against this ransomware attack without the need for any updates on endpoints.CrowdStrike's Three-Pronged Approach
CrowdStrike employs its combination of protection methods within a layered and integrated three-pronged approach that combines next-generation antivirus with endpoint detection and response (EDR) and managed threat hunting.Next-Generation Antivirus
CrowdStrike Falcon® PreventTM offers the most proven and advanced next-generation prevention capabilities to protect against known and unknown malware, and even attacks that do not use malware. A variety of techniques are combined within AI-powered machine learning, and importantly, rather than attempting to detect known malware iterations, Falcon Prevent leverages the power of IOAs to stop ransomware before it can execute and inflict damage — without the need for bloated signatures and the heavy updates that come with them, which are especially problematic for remote workers today.Built-in EDR
Unlike signature-based prevention approaches, next-gen antivirus provides multiple protections against attacks such as ransomware. Simultaneously, EDR acts like a surveillance camera recording what takes place on the endpoint. Any time an endpoint completes an action, whether it is running an application, connecting to a network, visiting a website or writing a file, the Falcon platform’s built-in EDR capabilities provide enough data to create a complete picture with the fidelity necessary to find IOAs. The collected activity information is then fed into the CrowdStrike Threat Graph® data model to analyze and correlate it with trillionsof events across CrowdStrike’s entire customer base, spotting anomalies and detecting IOA patterns to determine if an attack is underway.Integrated Managed Hunting
Ransomware delivery techniques today go beyond “spray and pray” phishing campaigns. More and more attackers are taking advantage of unsecured external services and vulnerable public-facing applications to obtain hands-on-keyboard access to deploy specific ransomware payloads, and ensure that their execution techniques will evade legacy security solutions and result in maximum impact. BGH ransomware preparation activities typically employ “living off the land” (LOTL) techniques, with operators often painstakingly preparing the environment, deleting backups and clearing logs well before ransomware binaries are deployed. Without the human “eyes on glass” provided by threat hunting, you can miss a crucial opportunity to thwart ransomware operators before they have the opportunity to begin encrypting files. An example of this is from October 2019, when the CrowdStrike Falcon® OverWatch managed threat hunting team identified an eCrime intrusion against a customer’s network and observed malicious activity reflective of an early-stage, hands-on ransomware attack. The initial intrusion vector was likely a password-spraying attack against Remote Desktop Protocol (RDP) and Server Message Block (SMB) services exposed to the internet, enabling the attacker to interactively log on to the system, drop tools and execute custom scripts, including ransomware to encrypt machines within the organization. The adversary's use of LOTL techniques reinforces the importance of having humans continuously hunting across a network in order to enable rapid response to quickly developing threat activity. After deployment of the CrowdStrike Falcon® agent, the EDR information gathered is used by the Falcon OverWatch team to proactively sift through endpoint data to find new hidden attacks that may not immediately trigger automated alerts. The holistic nature of these elements working together provides the ultimate power behind CrowdStrike's capabilities.Staying Safe and Secure
Keeping your organization safe and all of your employees productive is especially important right now. This means keeping the organization safe from cyber threats, but it also means ensuring security technologies do not impact employee productivity. Over the coming months, we will be releasing more blogs and videos on how you can use the CrowdStrike Falcon® platform to keep your organization and your users safe from cyberattack. Read a blog from our CrowdStrike OverWatch team offering a detailed look at increasing intrusions against the healthcare sector. If there is anything that CrowdStrike can do to help your organization stay secure in this time of need, please don’t hesitate to reach out to us.Additional Resources
- For more information on how the CrowdStrike Falcon® platform defends against ransomware and other modern attacks, read the white paper “Ransomware, a Growing Enterprise Threat.”
- Learn more about the CrowdStrike Falcon® platform.
- Visit the Falcon Complete™ webpage for information on no-touch managed endpoint protection.
- Visit our COVID-19 and Cybersecurity Resource Center to learn more about securing remote workers.
- CrowdStrike has announced two new programs to help secure remote workers during the COVID-19 crisis.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent to see how true next-gen AV performs against today’s most sophisticated threats.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)
![Endpoint Protection and Threat Intelligence: The Way Forward [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/GK-Blog_Images-1)









































