At AWS re:Inforce 2024, CrowdStrike is announcing expanded AWS support to provide breach protection, enhanced visibility and faster response across your cloud environment. Let’s explore three cutting-edge CrowdStrike Falcon® Cloud Security and CrowdStrike Falcon® Next-Gen SIEM features that are changing the way organizations manage security risks.
Safeguard Serverless Architectures
As serverless computing continues to gain traction, security must evolve to address new challenges. Falcon Cloud Security now supports vulnerability scanning of AWS Lambda functions the moment they are created in the cloud, providing crucial security information for AWS Lambda, a leading serverless computing solution. This feature plays a pivotal role in mitigating risks associated with the execution of Lambda functions, which may include vulnerabilities due to injection flaws, inadequate error handling or the insecure use of third-party libraries.
Falcon Cloud Security empowers organizations to control which code runs in their environments. Customers can allow or deny the execution of functions based on assessed risk factors. This selective enforcement ensures only authorized and verified functions are executed, thereby protecting the serverless environment from potential exploits and reducing the surface area for attacks. This adds to our existing cloud security posture management (CSPM) scanning for AWS Lambda misconfigurations.
Accelerate Investigation and Response Time
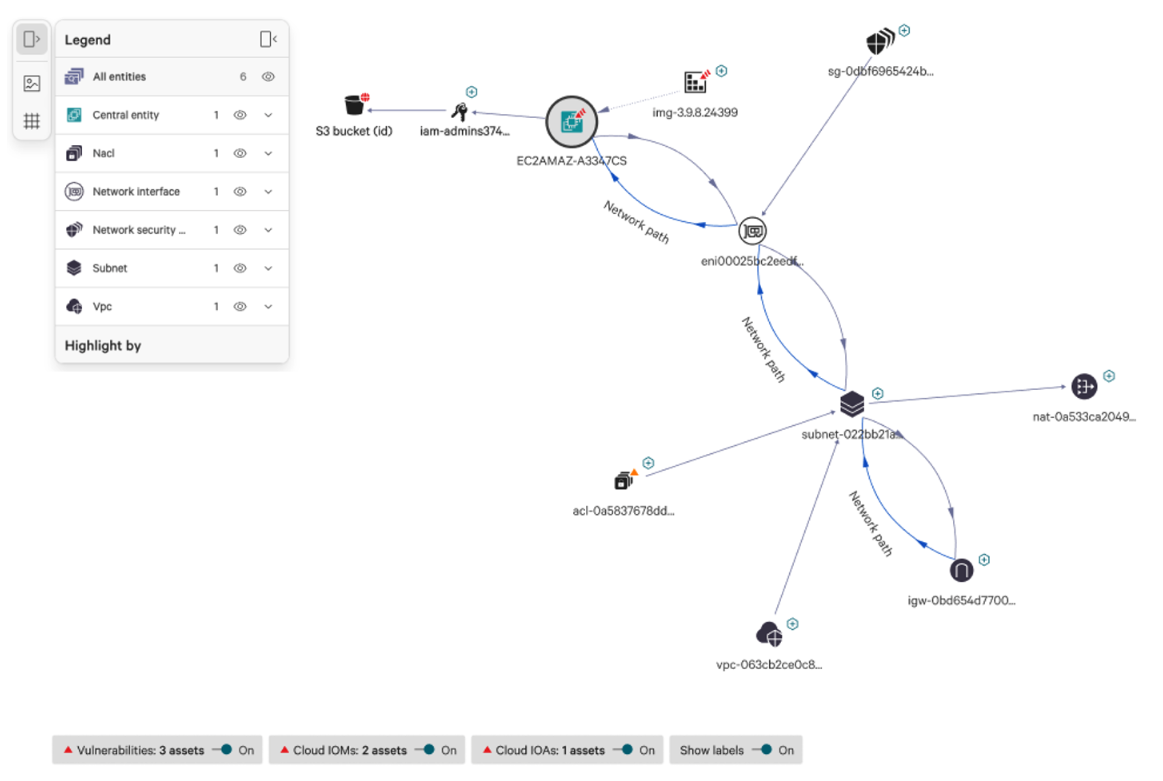
The fastest recorded breakout time in 2023 is just over 2 minutes, as noted in the CrowdStrike 2024 Global Threat Report. Organizations are in a race with adversaries, tirelessly working to close every gap that could be an entry point. This race starts with complete endpoint-to-cloud visibility of the adversary’s attack path, which is the route between an internet-exposed asset (source) and a critical asset (destination). Adversaries can exploit weaknesses in assets along the attack path to move deeper into a target environment and achieve their objectives.
In case you missed it, we released attack path analysis support for these AWS resources: Amazon S3, AWS Identity and Access Management (IAM), Amazon Relational Database Services and container images a few months back. Now, we are excited to announce the release of additional AWS services to be included in CrowdStrike® Asset Graph. These services include: Amazon Athena, Amazon Redshift, Amazon Elastic Container Registry (ECR), Amazon Elastic File System (EFS), Amazon Elastic Block Store (EBS) Volume, Amazon Machine Image (AMI), Amazon ElastiCache and Amazon DynamoDB.
Automatically stitching together the complete trajectory of an adversary will accelerate investigation and response time for security teams, ultimately enhancing overall security posture and more effectively protecting critical assets.
CrowdStrike Falcon Cloud Security for AWS
Falcon Cloud Security integrates with over 50 AWS services to deliver effective protection at every stage of the cloud journey, combining multi-account deployment automation, sensor-based runtime protection, agentless API attack and misconfiguration detection, and pre-runtime scanning of containers, Lambda functions and IaC templates.
CrowdStrike uses real-time IOAs, threat intelligence, evolving adversary tradecraft and enriched telemetry from vectors such as endpoint, cloud, identity and more. This enhances threat detection and facilitates automated protection, remediation and elite threat hunting, aligned closely with understanding AWS assets, enforcing strict access control and authentication measures, and ensuring meticulous monitoring and management of cloud resources.
You can try Falcon Cloud Security through a Cloud Security Health Check, during which you’ll engage in a one-on-one session with a cloud security expert, evaluate your current cloud environment, and identify misconfigurations, vulnerabilities and potential cloud threats.
Falcon Next-Gen SIEM Connectors for AWS
The effectiveness of a security operations team hinges on its ability to have a comprehensive view of all activities across their environments. Our Falcon Next-Gen SIEM Connectors for AWS offer effortless ingestion of a plethora of logs generated by AWS services including AWS CloudTrail, Amazon S3, Amazon GuardDuty, Amazon CloudWatch, AWS Config, AWS Security Hub, AWS Network Firewall and AWS WAF.
This integration ensures SecOps teams have full visibility, which is critical for threat detection, investigation, response and compliance. By leveraging the Falcon Next-Gen SIEM data connectors and parsers, organizations can seamlessly collect and process logs, thereby enhancing their ability to quickly identify and mitigate threats while avoiding complex data onboarding processes.
Falcon Next-Gen SIEM unifies data, AI, automation and intelligence in one AI-native platform to stop breaches. It extends CrowdStrike’s industry-leading detection and response and expert services to all data, including AWS logs, for complete visibility and protection. Your team can detect and respond to cloud-based threats in record time with real-time alerts, live dashboards and blazing-fast search. Native workflow automation lets you streamline analysis of cloud incidents and say goodbye to tedious tasks.
Your analysts can investigate cloud-based threats from the same console they use to manage cloud workload security and CSPM. CrowdStrike consolidates multiple security tools, including next-gen SIEM and cloud security, on one platform to cut complexity and costs. Watch a 3-minute demo of Falcon Next-Gen SIEM to see it in action.
Additional Resources
- Learn more about Falcon Cloud Security for AWS.
- To learn what other industry analysts are saying about CrowdStrike, visit the Industry Recognition webpage.
- Take a free Cloud Security Health Check to visualize misconfigurations and other vulnerabilities in minutes.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)