Microsoft has released 84 security patches for its July 2022 Patch Tuesday rollout. Four vulnerabilities are rated Critical in severity and the rest are classified as Important, with one (CVE-2022-22047) under active exploitation. In this blog, the CrowdStrike Falcon® Spotlight™ team offers an analysis of this month’s vulnerabilities, as well as insights into the vulnerabilities and patches affecting Microsoft products in the first half of this year. We highlight the CVEs in this month’s update that are most severe and recommend how to prioritize patching.
July 2022 Risk Analysis
The top three attack types — elevation of privilege, remote code execution (RCE) and information disclosure — continue to dominate, with denial of service following at almost 6%.
 Figure 1. Breakdown of July 2022 Patch Tuesday attack types
Figure 1. Breakdown of July 2022 Patch Tuesday attack typesMicrosoft Windows received the most patches this month, with Extended Security Updates (ESUs) following close behind. There are also patches for 33 Azure vulnerabilities this month and a couple for Microsoft Office products.
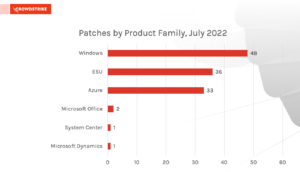 Figure 2. Breakdown of July 2022 Patch Tuesday affected product families
Figure 2. Breakdown of July 2022 Patch Tuesday affected product familiesZero-Day CSRSS Vulnerability Under Active Exploitation
CVE-2022-22047 is listed as being under active attack, but there’s no information from Microsoft on where, or how widely, the vulnerability is being exploited. This vulnerability allows an attacker to execute code as SYSTEM, provided they can execute other code on the target. Bugs of this type are typically paired with a code execution bug, usually a specially crafted Office or Adobe document, to take over a system. These attacks often rely on macros, which are now disabled by default.
| Rank | CVSS Score | CVE | Description |
| Important | 7.8 | CVE-2022-22047 | Windows CSRSS Elevation of Privilege |
CrowdStrike recommends that you monitor your environment to see if it is affected by this vulnerability and apply the fix offered. For CrowdStrike customers using Falcon Spotlight, this CVE is ranked as Critical.
Critical Vulnerabilities in Network File System and RPC
Four vulnerabilities ranked as Critical received patches this month. Affected products are Remote Procedure Call (RPC), Windows Network File System (NFS) and Windows Graphics Component. Let’s review a couple of these vulnerabilities and how they could affect an organization’s environment.
CVE-2022-22038: This vulnerability could allow a remote, unauthenticated attacker to exploit code on an affected system. While not specified in the bulletin, the assumption is that, with elevated privileges, code execution would occur. By combining these attributes, you may end up with a potentially wormable bug. Microsoft rates the attack complexity as high since an attacker would need to make “multiple exploitation attempts” to take advantage of this vulnerability, but again, unless you are actively blocking RPC activity, you may not see these attempts. If the exploit complexity were rated low, which some would argue it should be since the attempts could likely be scripted, the CVSS would be 9.8. CrowdStrike recommends that you test and deploy this patch quickly.
CVE-2022-22029: This is the third month in a row with a Critical-rated NFS vulnerability, and while this one has a lower CVSS than the previously listed vulnerabilities, it could still allow a remote, unauthenticated attacker to execute their code on an affected system with no user interaction. Microsoft notes multiple exploit attempts may be required to do this, but unless you are specifically auditing for this, you may not notice. If you’re running NFS, make sure you don’t ignore this patch.
| Rank | CVSS Score | CVE | Description |
| Critical | 8.8 | CVE-2022-30221 | Windows Graphics Component Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2022-22038 | Remote Procedure Call Runtime Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2022-22029 | Windows Network File System Remote Code Execution Vulnerability |
| Critical | 7.5 | CVE-2022-22039 | Windows Network File System Remote Code Execution Vulnerability |
Important Azure Site Recovery Service Vulnerabilities
Based on the total count of Azure vulnerabilities addressed this month, this set of CVEs should be prioritized. Azure Site Recovery is primarily a cloud-based service, but there are some on-premises components. An automatic update for these vulnerabilities is very unlikely to happen. Microsoft recommends upgrading to version 9.49 to remediate these vulnerabilities. Instructions can be found in this article. It’s incredibly unusual to see so many CVEs addressed in a single month for a single component.
| Rank | CVSS Score | CVE |
| Important | 8.3 | CVE-2022-33674 |
| Important | 7.8 | CVE-2022-33675 |
| Important | 7.2 | CVE-2022-33677 |
| Important | 7.2 | CVE-2022-33676 |
| Important | 7.2 | CVE-2022-33678 |
| Important | 6.5 | CVE-2022-30181 |
| Important | 6.5 | CVE-2022-33641 |
| Important | 6.5 | CVE-2022-33643 |
| Important | 6.5 | CVE-2022-33655 |
| Important | 6.5 | CVE-2022-33656 |
| Important | 6.5 | CVE-2022-33657 |
| Important | 6.5 | CVE-2022-33661 |
| Important | 6.5 | CVE-2022-33662 |
| Important | 6.5 | CVE-2022-33663 |
| Important | 6.5 | CVE-2022-33665 |
| Important | 6.5 | CVE-2022-33666 |
| Important | 6.5 | CVE-2022-33667 |
| Important | 6.5 | CVE-2022-33672 |
| Important | 6.5 | CVE-2022-33673 |
| Important | 4.9 | CVE-2022-33642 |
| Important | 4.9 | CVE-2022-33650 |
| Important | 4.9 | CVE-2022-33651 |
| Important | 4.9 | CVE-2022-33653 |
| Important | 4.9 | CVE-2022-33654 |
| Important | 4.9 | CVE-2022-33659 |
| Important | 4.9 | CVE-2022-33660 |
| Important | 4.9 | CVE-2022-33664 |
| Important | 4.9 | CVE-2022-33668 |
| Important | 4.9 | CVE-2022-33669 |
| Important | 4.9 | CVE-2022-33671 |
| Important | 4.4 | CVE-2022-33652 |
| Important | 4.4 | CVE-2022-33658 |
Falcon Spotlight provides the visibility SecOps teams need to quickly identify which vulnerabilities are prevalent in your organization’s environment. Since Falcon Spotlight is completely integrated within the CrowdStrike Falcon® platform, IT staff are able to take swift action by isolating potentially compromised hosts from exploited vulnerabilities. Additionally, the Falcon platform mitigates the risk from vulnerabilities that cannot be patched rapidly by detecting and automatically preventing exploitation attempts and post-exploitation activity.
Managing Vulnerabilities Is Ultimately about the Long Game
As evident in these monthly patch rollouts, no product is safe from vulnerabilities. Attackers will use any weakness to gain access, exploit flaws and move laterally to take advantage of your organization. While prioritization and patching are vital for immediately addressing critical issues, what makes a vulnerability management program successful is planning for the long term.
When your organization is planning for the long term, reviewing everything within your environment is important. Patching should not be done in a vacuum — it requires open communication with other parts of your cybersecurity organization and cross-collaboration with IT hygiene, threat intelligence and compliance teams to fully understand which areas of risk your organization might be exposed to and the types of threats or attackers are more likely to take advantage.
Organizations rely on full-suite platforms that offer comprehensive solutions to do this in a timely manner. Your staff should be able to make accurate and actionable recommendations based on any kind of suspicious activity surrounding the assets and entities in your environment while having access to relevant contextual data to provide the insight needed to make appropriate decisions to protect your environment. CrowdStrike stands resolutely behind this. When we say “We stop breaches,” we offer a holistic approach to creating a defensible security posture — and we do it in a way that is relevant, timely and accessible to all who are responsible for keeping your defenses strong. Beyond Falcon Spotlight, we suggest you try our Falcon platform to see how CrowdStrike can enable your team for success.
Learn More
This video on Falcon Spotlight™ vulnerability management shows how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- Learn more about vulnerabilities that can affect your environment at Fal.Con 2022, the cybersecurity industry’s most anticipated annual event. Register now and meet us in Las Vegas, Sept. 19-21!
- See how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- Read how CrowdStrike Asset Graph works in conjunction with Falcon Discover to offer you advanced insights on how suspicious activity is related to other assets within your environment.
- Learn how Falcon Identity Protection products can stop workforce identity threats faster.
- Download the CrowdStrike 2022 Global Threat Report to learn who and what is affecting your environment.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself with a free trial of Falcon Prevent™.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)
![Endpoint Protection and Threat Intelligence: The Way Forward [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/GK-Blog_Images-1)








































