Last month, teams participating in a global hacking contest, Pwn2Own, succeeded in exploiting several Microsoft products on the first day of the competition. These Windows products, which include Microsoft Teams, Windows 10 and Microsoft Exchange Server (which has also seen noteworthy exploitation as of late — see here), all now have active and publicly known vulnerabilities. Unfortunately, in this Patch Tuesday update, Microsoft chose not to patch all of the vulnerabilities that this contest exploited. It’s also worth mentioning that Microsoft provided updates for only 55 vulnerabilities this month — the lowest number of patches on a Patch Tuesday to date this year.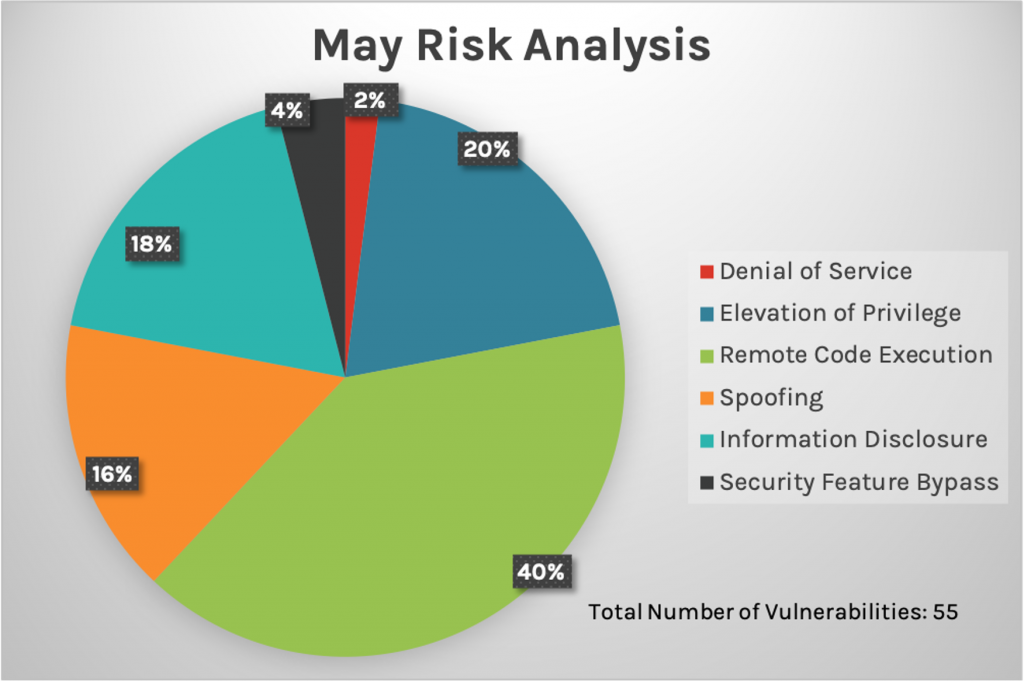
We also see updates in the wireless and Bluetooth stacks. None of these vulnerabilities is rated as Critical, but they could allow spoofing or information disclosure.
Additional Resources
The most significant updates we did receive from Microsoft cover only a couple of Microsoft Exchange Server vulnerabilities (exploited during the Pwn2Own contest) and only four Critical vulnerabilities, as well as a newly released wormable vulnerability in the HTTP network stack.
The CrowdStrike Falcon® Spotlight™ analyst team reviews these updates in this month’s blog, as well as vulnerabilities in the wireless and Bluetooth stacks, Microsoft Office Suite, Visual Studio and Visual Studio Code Editors. IT staff should observe that while Microsoft shared no reports of any vulnerabilities exploited in the wild this month, it’s vitally important for IT staff to prioritize these critical and wormable vulnerabilities.
Let’s get started.
New Patches for 55 Vulnerabilities
This month’s Patch Tuesday updates include fixes for 55 vulnerabilities.
Review of Critical Vulnerabilities
If a server is using HTTP Protocol Stack (http.sys) to process packets, CVE-2021-31166 could allow an unauthenticated attacker to send a specially crafted packet to compromise the host, leading to remote code execution on the server. This vulnerability is rated a 9.8 CVSS score and designated Critical by Microsoft, as it can be used as a worm to spread to other servers in the network. Patches for Windows 10 and Windows Server have rolled out. We also see a highly rated CVSS 9.9 vulnerability: CVE-2021-28476. This Hyper-V remote code execution vulnerability could allow a guest virtual machine to force the Hyper-V host's kernel to read from an arbitrary, potentially invalid address. This could lead to a compromise of the host’s Hyper-V security. Patches have rolled out for Windows 7 and all newer operating systems. Two additional Critical vulnerabilities were also identified, both of which received updates for all supported platforms dating back to Windows 7 and Windows Server 2008.| Rank | CVSS Score | CVE | Description |
| Critical | 9.9 | CVE-2021-28476 | Hyper-V Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2021-31166 | HTTP Protocol Stack Remote Code Execution Vulnerability |
| Critical | 7.8 | CVE-2021-31194 | OLE Automation Remote Code Execution Vulnerability |
| Critical | 7.5 | CVE-2021-26419 | IE Scripting Engine Memory Corruption Vulnerability |
Vulnerabilities for Microsoft Office Suite
Several applications in Microsoft Office Suite — Word, Excel, SharePoint and Access — received updates this month, but none of the CVEs is rated Severe. The impact ranges from information disclosure to remote code execution. IT staff should consider where they should remediate these important, but not immediately critical, vulnerabilities in their prioritization plan.| Rank | CVSS Score | CVE | Description |
| Important | 8.8 | CVE-2021-31181 | Microsoft SharePoint Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2021-28474 | Microsoft SharePoint Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2021-28455 | Microsoft Jet Red Database Engine and Access Connectivity Engine Remote Code Execution Vulnerability |
| Important | 7.8 | CVE-2021-31175 | Microsoft Office Remote Code Execution Vulnerability |
| Important | 7.8 | CVE-2021-31176 | Microsoft Office Remote Code Execution Vulnerability |
| Important | 7.8 | CVE-2021-31177 | Microsoft Office Remote Code Execution Vulnerability |
| Important | 7.8 | CVE-2021-31179 | Microsoft Office Remote Code Execution Vulnerability |
| Important | 7.8 | CVE-2021-31180 | Microsoft Office Graphics Remote Code Execution Vulnerability |
| Important | 7.6 | CVE-2021-28478 | Microsoft SharePoint Spoofing Vulnerability |
| Important | 7.1 | CVE-2021-31172 | Microsoft SharePoint Spoofing Vulnerability |
| Important | 5.5 | CVE-2021-31174 | Microsoft Excel Information Disclosure Vulnerability |
| Important | 5.5 | CVE-2021-31178 | Microsoft Office Information Disclosure Vulnerability |
| Important | 5.3 | CVE-2021-31173 | Microsoft SharePoint Information Disclosure Vulnerability |
| Important | 4.6 | CVE-2021-26418 | Microsoft SharePoint Spoofing Vulnerability |
| Important | 4.1 | CVE-2021-31171 | Microsoft SharePoint Information Disclosure Vulnerability |
| Rank | CVSS Score | CVE | Description |
| Important | 7.1 | CVE-2021-31182 | Microsoft Bluetooth Driver Spoofing Vulnerability |
| Important | 6.5 | CVE-2020-24588 | Windows Wireless Networking Spoofing Vulnerability |
| Important | 6.5 | CVE-2020-24587 | Windows Wireless Networking Information Disclosure Vulnerability |
| Important | 6.5 | CVE-2020-26144 | Windows Wireless Networking Spoofing Vulnerability |
Patching Is Essential for Microsoft Products
While Microsoft released a relatively low number of patches compared to prior months and to the number potentially expected due to the above-referenced Pwn2Own contest, the updates ranked as Critical should be reviewed with care. The vulnerabilities CVE-2021-31166 and CVE-2021-28476 are both worthy of significant concern, and IT staff should prioritize these CVEs due to their high CVSS scores, especially with CVE-2021-31166’s ability to be used as a worm to spread throughout the network. Analysts should review their prioritization and patching programs carefully, especially when it comes to products that are widely used throughout the organization such as some of those detailed above, to strengthen their organization’s security posture.
Learn More
Watch this video on Falcon Spotlight™ vulnerability management to see how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- For more information on CVEs you should know about, read Falcon Complete Stops Microsoft Exchange Server Zero-Day Exploits, Vulnerability Roundup: 10 Critical CVEs of 2020, and our Patch Tuesday blogs for February 2021, March 2021 and April 2021.
- Learn how Falcon Spotlight™ can help you discover and manage vulnerabilities in your environments.
- See how Falcon Complete™ stops Microsoft Exchange Server zero-day exploits.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Learn about the recent Baron Samedit vulnerability and CrowdStrike’s custom dashboard.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)
![Endpoint Protection and Threat Intelligence: The Way Forward [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/GK-Blog_Images-1)








































