Microsoft has released security updates for 58 vulnerabilities, including five zero-days, three of which are being actively exploited. One of the zero-days (CVE-2023-36025) is a Windows SmartScreen Security Feature Bypass Vulnerability, the second (CVE-2023-36033) is a privilege escalation vulnerability in the Windows DWM Core Library, and the third (CVE-2023-36036) is another privilege escalation vulnerability affecting the Windows Cloud Files Mini Filter Driver. Three of the 58 vulnerabilities addressed today are rated as Critical, and the remaining 55 are rated as Important.
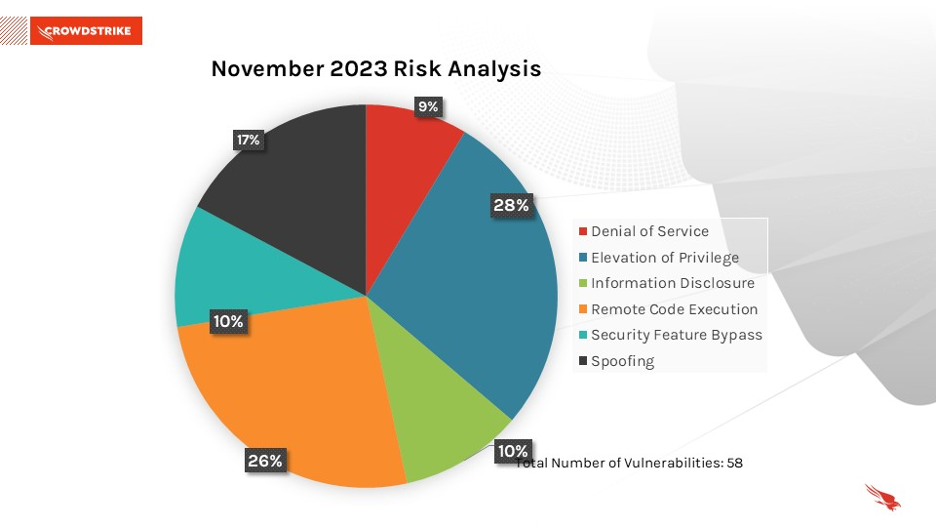
November 2023 Risk Analysis
This month’s leading risk type is elevation of privilege (28%), followed by remote code execution (26%) and spoofing (17%).
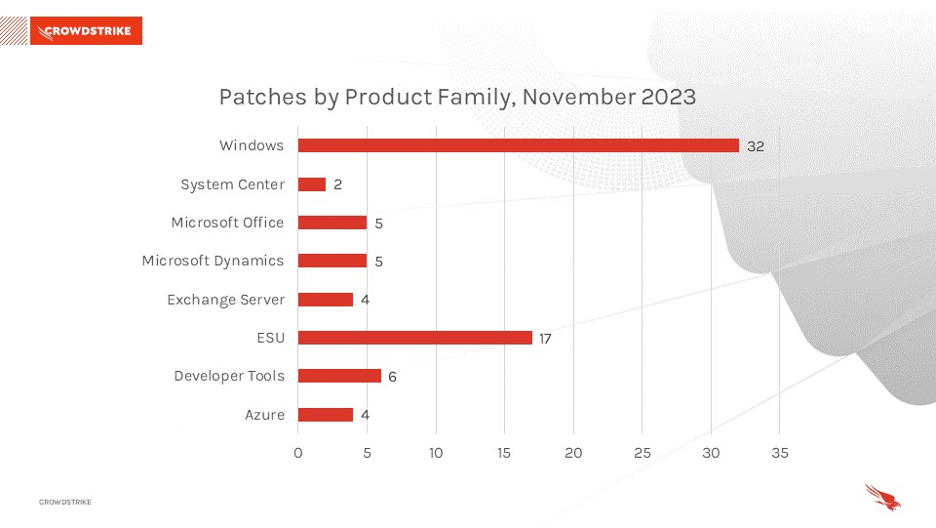
The Microsoft Windows product family received the most patches this month (32), followed by Extended Support Updates (17).
Actively Exploited Zero-Day Vulnerability Enables Windows SmartScreen Security Feature Bypass
Windows SmartScreen has received a patch for CVE-2023-36025. According to Microsoft, by exploiting this vulnerability, “The attacker would be able to bypass Windows Defender SmartScreen checks and their associated prompts.” This vulnerability requires user interaction — the user would have to click on a specially crafted internet shortcut (.URL) or a hyperlink pointing to an internet shortcut file in order to be compromised by the attacker.
| Severity | CVSS Score | CVE | Description |
| Important | 8.8 | CVE-2023-36025 | Windows SmartScreen Security Feature Bypass |
Table 1. Zero-day in Windows SmartScreen Security Feature
Actively Exploited Zero-Day Vulnerability Affects Windows DWM (Desktop Window Manager) Core Library
CVE-2023-36033 is a publicly disclosed vulnerability affecting the Windows DWM Core Library. This vulnerability could allow an attacker to gain SYSTEM privileges.
| Rank | CVSS Score | CVE | Description |
| Important | 7.8 | CVE-2023-36033 | Windows DWM Core Library Elevation of Privilege Vulnerability |
Table 2. Zero-day in Windows DWM Core Library
Actively Exploited Zero-Day Affects Windows Cloud Files Mini Filter Driver
CVE-2023-36036 is another vulnerability affecting the Windows Cloud Files Mini Filter Driver being exploited in the wild. Successful exploitation of this flaw could allow an attacker to gain SYSTEM privileges.
| Severity | CVSS Score | CVE | Description |
| Important | 7.8 | CVE-2023-36036 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
Table 3. Zero-day affecting Windows Cloud Files Mini Filter Driver
Critical Vulnerabilities
CVE-2023-36397, a remote code execution vulnerability rated as Critical, affects Windows Pragmatic General Multicast. To successfully exploit this vulnerability, an attacker would have to send a specifically crafted malicious MSMQ packet to a MSMQ server, leading to remote code execution. This Windows component needs to be enabled for a system to be vulnerable. Microsoft recommends checking if the Message Queuing service is running and TCP port 1801 is listening on the machine; if the service is running and not in use, consider disabling.
CVE-2023-36400, a privilege escalation vulnerability rated as Critical, affects Windows HMAC Key Derivation. If exploited, this could allow an attacker to gain SYSTEM privileges. According to Microsoft, “A successful attack could be performed from a low privilege Hyper-V guest. The attacker could then traverse the guest's security boundary to execute code on the Hyper-V host execution environment.”
CVE-2023-36052 is a Critical vulnerability affecting Azure CLI commands. An attacker could recover plaintext passwords and usernames from log files created by the affected CLI commands and published by Azure DevOps and/or GitHub Actions in public repositories. Customers using the affected CLI commands must update their Azure CLI version to 2.53.1 or above to be protected against the risks of this vulnerability, Microsoft says. This also applies to customers with log files created using these commands through Azure DevOps and/or GitHub Actions.
| Rank | CVSS Score | CVE | Description |
| Critical | 9.8 | CVE-2023-36397 | Azure Arc-enabled Kubernetes cluster Connect Elevation of Privilege Vulnerability |
| Critical | 8.8 | CVE-2023-36400 | Microsoft Office Remote Code Execution Vulnerability |
| Critical | 8.6 | CVE-2023-36052 | Azure CLI REST Command Information Disclosure Vulnerability |
Table 4. Critical vulnerabilities in Windows and Azure
Not All Relevant Vulnerabilities Have Patches: Consider Mitigation Strategies
As we have learned with other notable vulnerabilities, such as Log4j and ProxyNotShell, not every highly exploitable vulnerability can be easily patched. It’s critically important to develop a response plan for how to defend your environments when no patching protocol exists.
Regular review of your patching strategy should still be a part of your program, but you should also look more holistically at your organization's methods for cybersecurity and improve your overall security posture.
Learn More
Learn more about how CrowdStrike Falcon® Spotlight can help you quickly and easily discover and prioritize vulnerabilities here.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- For more information on which products are in Microsoft’s Extended Security Updates program, refer to the vendor guidance here.
- Download the CrowdStrike 2023 Global Threat Report and CrowdStrike 2023 Threat Hunting Report to learn how the threat landscape has shifted in the past year and understand the adversary behavior driving these shifts.
- See how CrowdStrike Falcon® Spotlight vulnerability management can help you discover and manage vulnerabilities and prioritize patches in your environments.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself with a free trial of CrowdStrike Falcon® Prevent next-generation antivirus.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)
![Endpoint Protection and Threat Intelligence: The Way Forward [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/GK-Blog_Images-1)