The popularity of legitimate cryptomining is being challenged by the rise of cryptojacking — its criminal cousin. The earning potential of a successful cryptojacking attack has made it an attractive pursuit for bad actors — an article in ZDNet even names 2018 as the “year of malicious cryptocurrency mining attacks,” referring to it as
the “new ransomware.” This is because, while cryptojacking and ransomware are both for financial profit, cryptojacking is not overtly disruptive — providing long-term earning potential for the attacker. Cryptojacking occurs when an attacker uses malware to hijack an endpoint’s processing
power and uses it to mine cryptocurrency on the attacker’s behalf. The endpoints are used to perform the computations necessary to update cryptocurrencies' blockchains, creating
new
tokens and generating fees in the process. These are deposited into wallets owned by the attacker, while the costs of “mining” — electricity and processing power — are incurred
by the unwitting victim.
Show Me Where the Monero Is
Unlike ransomware, which typically demands payment in Bitcoin, cryptojackers prefer Monero, a secure and private currency system that is both easier to mine and almost impossible to trace. In addition, while Bitcoin mining requires specialized, expensive hardware, Monero can be mined using any desktop, laptop or server, making individual systems more lucrative targets. Monero also provides anonymity and privacy, protecting attackers from the prying eyes of law enforcement. Clearly, attackers are profiting from this scheme with some attacks reportedly
earning as much as $3.6 million.
Stolen Resources and Lost Productivity
The damage caused by cryptojacking extends far beyond overworked CPUs. Lost processing power can impact business operations —
slowing system performance and often resulting in system downtime and application crashes. These clandestine disruptions can cost organizations dearly, and not only in lost productivity: When attackers use an organization’s high-performance servers for mining, it saps their ability to be strong business-value assets. Organizations could see a spike in operating costs as their resources are redirected to the cryptominer’s efforts. More recently, nation-state-sponsored fileless attack tactics are being brought into the cryptojacking paradigm with devastating effectiveness. Earlier this year, the WannaMine Monero miner was found propagating throughout networks via the EternalBlue exploit seen in WannaCry and NotPetya attacks. A detailed CrowdStrike® blog noted how WannaMine used “living off the land” techniques, such as Windows Management Instrumentation (WMI) permanent event subscriptions as a persistence mechanism. Its fileless nature and use of legitimate system software, such as WMI and PowerShell, make it difficult, if not impossible, for organizations to block it without some form of next-generation antivirus solution. Although cryptojacking may not bring operations grinding to a halt, if an organization is susceptible to cryptojacking, they are susceptible to a breach. A cryptojacker that has successfully slipped past an organization’s defenses in the past has an open invitation to return, if security gaps aren’t closed.
Challenges for Security Teams
Security teams that have limited resources and visibility have a difficult time addressing cryptojacking because, to be successful, they must do the following:
- Identify an event and understand the attack vector. The increased use of legitimate tools and fileless attacks makes this difficult.
- Stop an active breach and remediate systems quickly. When an incident occurs, security teams must stop the incident, then remediate the systems as quickly as possible. This often involves manual investigation and reimaging of machines, which are resource-draining tasks.
- Learn from an attack and close security gaps. After the incident, security teams must understand what happened, why it happened, and ensure that it doesn’t happen again.
Tips for Protecting Against Cryptojacking
Cryptojacking is a menace to an organization’s productivity and security. To address this risk, organizations need to:
- Practice strong security hygiene. IT hygiene is foundational to security. Regularly patching vulnerable applications and operating systems, and protecting privileged user accounts, are essential practices for optimal security posture.
- Deploy a true next-generation endpoint protection platform (EPP). Organizations must be prepared to prevent and detect all threats, including known and unknown malware, as well as identifying in-memory attacks. This requires a solution that includes next-gen AV protection, as well as endpoint detection and response (EDR), to prevent attacks and gain full visibility throughout the environment.
According to Gartner, effectively defending against threats to your endpoints means deploying a solution that has NGAV and EDR capabilities. The CrowdStrike Falcon® platform is a true next-gen EPP solution that is designed to detect stealthy behavioral indicators of attack (IOAs), regardless of whether the malware writes itself to disk or executes in-memory only.
How to Respond in Real Time
The CrowdStrike Falcon® platform enables teams to see, investigate and respond to a security incident within minutes. By recording all endpoint telemetry data, security teams have complete visibility into their environments and receive events in real time, so they can begin their investigation.
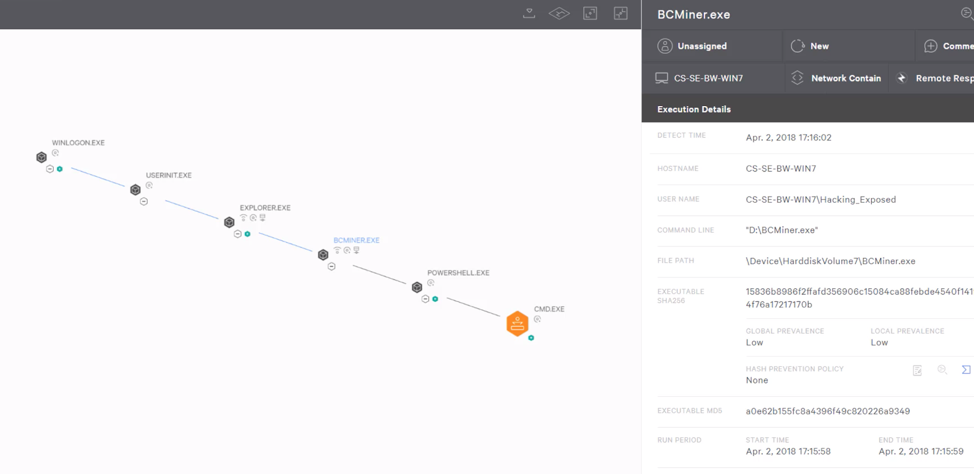 Figure 1. Detection of Malicious Powershell Script
Figure 1. Detection of Malicious Powershell ScriptEven with attacks such as WannaMine, which attempt to use legitimate tools (like WMI) to avoid detection, malicious behavior is immediately detected by CrowdStrike’s behavioral IOAs. In the detection shown in Figure 1, a malicious Powershell script has been identified and prevented from executing. Falcon gives security teams granular visibility into the processes executed, while Falcon Insight™ offers a real-time response feature that can be used to immediately contain and remotely remediate the endpoint. In addition, though most security teams opt to reimage machines when an incident occurs, it isn’t needed with Falcon Insight. Instead, real-time response opens a reverse shell with easy-to-use commands that make reimaging unnecessary. Some examples of these commands include the ability to stop a process and remotely remove the file from an endpoint, as shown in Figure 2.
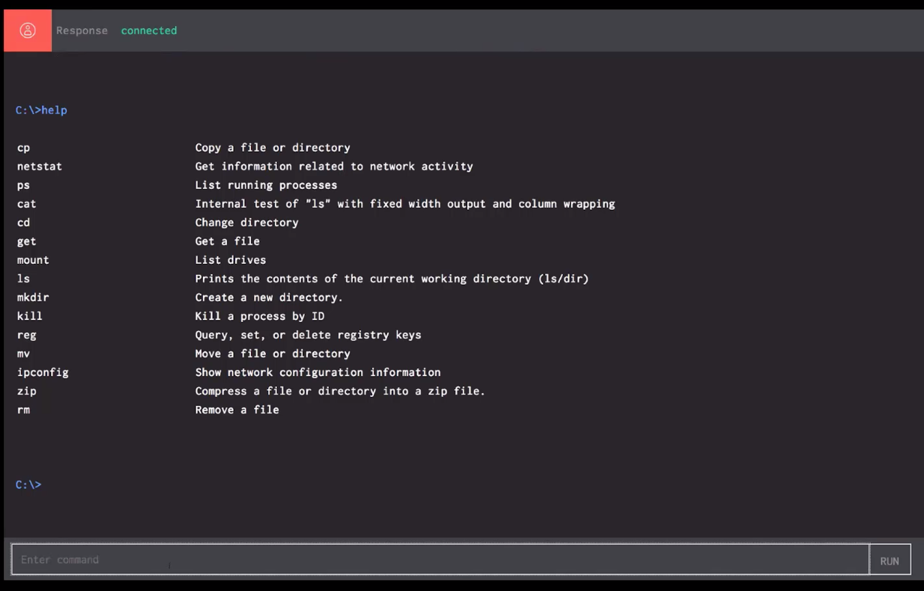 Figure 2: Real Time Response Shell
Figure 2: Real Time Response ShellFalcon also enables teams to pivot quickly and search across an environment for the malicious executable to determine if other systems have been impacted.
Those systems can then be remediated and the hash of the malware can be added to the blacklist to prevent further issues.
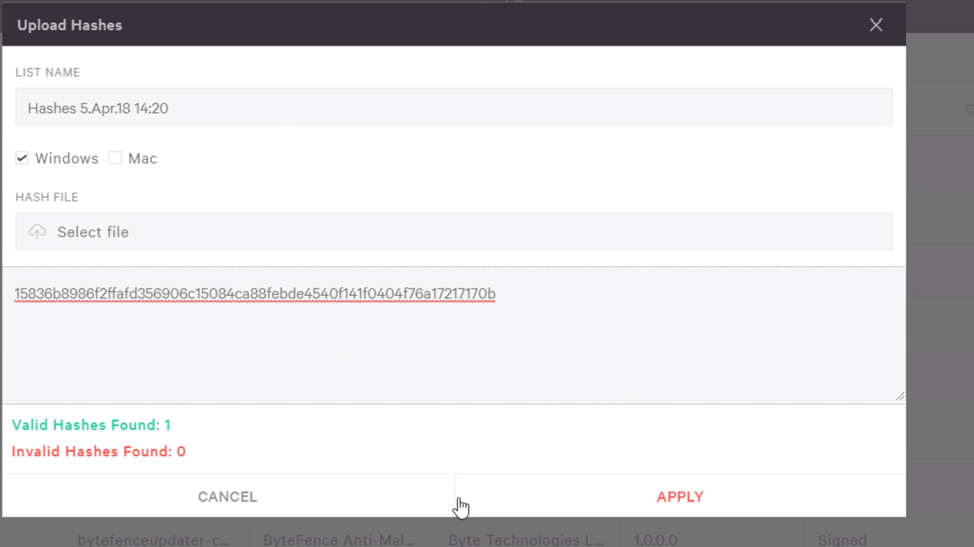 Figure 3: Blacklisting the Malicious File in the Falcon UI
Figure 3: Blacklisting the Malicious File in the Falcon UIConclusion
Cryptojacking is a threat to organizations because it hijacks valuable resources and is extremely difficult to detect. Even when found, it can require painstaking efforts to remove it and ensure an organization is secure. The Falcon comprehensive endpoint protection platform quickly detects and stops cryptojacking attempts before any resources-draining activity can begin.
Additional Resources
- Learn more about comprehensive endpoint protection with the CrowdStrike Falcon® platform by visiting the product page.
- Get an in-depth understanding of true “next-gen” endpoint detection and response (EDR) capabilities in this white paper: “EDR — Automatic Protection Against Advanced Threats.”
- Get tips for upgrading your legacy AV in our AV replacement guide: “What You Need to Know Before Replacing Your Current Antivirus Solution.”
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)


















































