As organizations increasingly rely on connected devices to drive efficiency and innovation, the Extended Internet of Things (XIoT) — covering industrial control systems (ICS), operational technology (OT), Internet of Things (IoT), and Internet of Medical Things (IoMT) — has rapidly expanded. This greater connectivity often drives increased vulnerability as critical assets are exposed to sophisticated threats.
XIoT assets are typically foundational to how organizations in manufacturing, healthcare, utilities, and other critical sectors operate. Their mission-critical nature makes XIoT assets prime targets for attackers seeking maximum disruption, financial payoff, and the theft of sensitive data and intellectual property.
BERSERK BEAR, a Russia-based adversary first detected in 2003, has a specific focus on targeting XIoT assets and is one of many adversaries increasingly targeting them. This adversary uses phishing, stolen credentials, and vulnerability exploitation as their primary tactics and techniques. Many security teams lack the real-time visibility and vulnerability prioritization to stop adversaries like BERSERK BEAR, leaving them exposed to widespread disruption across their organization.
CrowdStrike recently introduced new innovations in CrowdStrike Falcon® for XIoT to make it easier for organizations to strengthen security across their XIoT environments. Here, we take a closer look.
Understanding Falcon for XIoT
CrowdStrike Falcon for XIoT delivers modern security for complex ecosystems comprising ICS, OT, IoT, and IoMT devices. Built on the AI-native CrowdStrike Falcon® cybersecurity platform, Falcon for XIoT integrates comprehensive asset visibility, adversary-driven threat intelligence, and rapid vulnerability prioritization into a single solution. It’s designed to address the challenges faced by teams managing mission-critical operations across key industries reliant on XIoT devices.
CrowdStrike understands the urgency of securing connected devices, which is why Falcon for XIoT provides complete asset and vulnerability visibility in as little as 10 minutes,1 without hardware or extensive network configuration changes. This rapid deployment ensures organizations quickly bridge security gaps, significantly reducing exposure to potential threats and enhancing their ability to proactively manage risks.
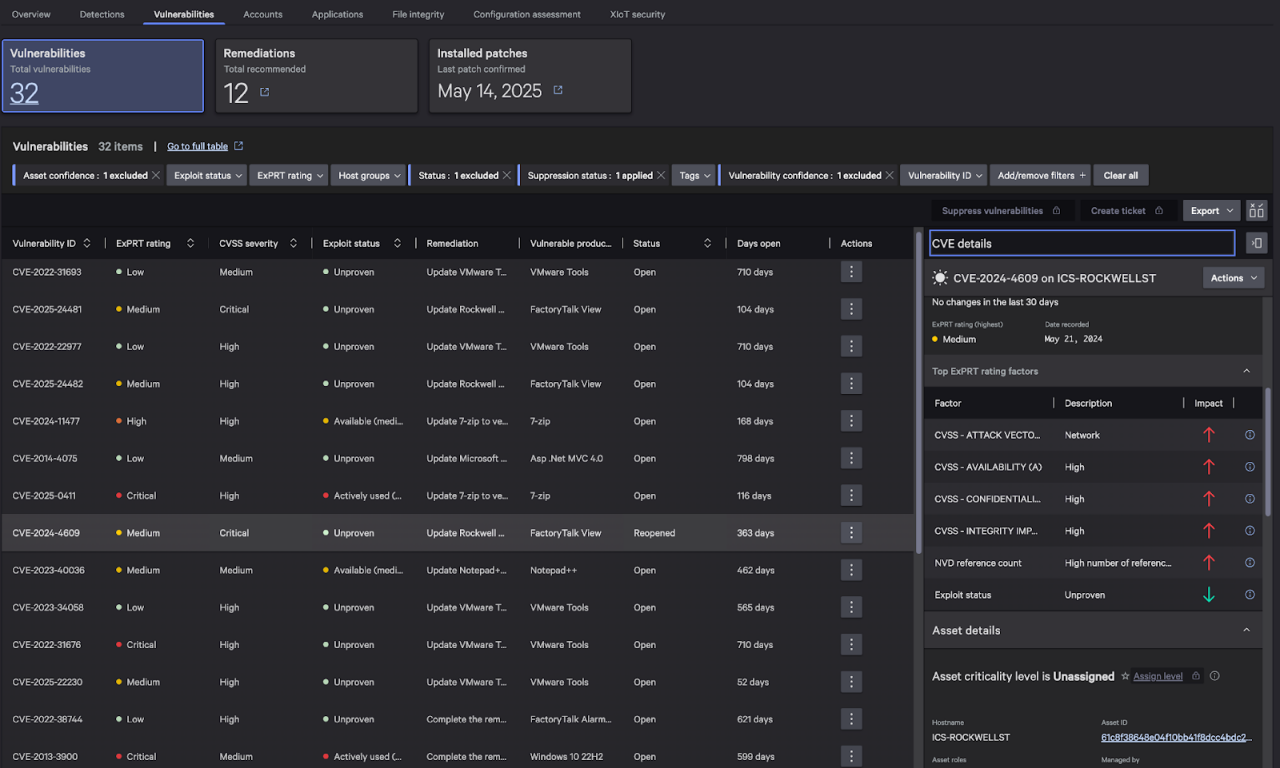
Enhanced Risk Prioritization with ExPRT.AI
CrowdStrike has enhanced ExPRT.AI, our Expert Prediction Rating AI model, with XIoT-specific asset and adversary context to improve its effectiveness in XIoT environments.
Detecting, prioritizing, and patching vulnerabilities is complicated in XIoT environments. Organizations have historically struggled with lengthy manual processes and generic vulnerability scoring systems, which often fail to provide clear guidance on which risks to address first. CrowdStrike’s ExPRT.AI transforms this approach by enabling security teams to prioritize vulnerabilities up to 200% faster2 than solely relying on CVSS through real-time, adversary-driven intelligence tailored for XIoT. It adjusts prioritization based on real-world XIoT-specific asset and adversary intelligence, giving security teams the insights they need to respond effectively to XIoT vulnerabilities.
With ExPRT.AI, organizations receive precise insights into the XIoT vulnerabilities most likely to be exploited by adversaries. This allows them to streamline remediation efforts while enhancing protection against the most pressing threats.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)