What is phishing training?
How often do you receive an email that you know is a scam? Maybe it’s the misspelled words or irregular formatting that gives it away, or the attention-grabbing subject line that gives you pause. Chances are, as a cybersecurity or IT professional, you can spot a phishing email with no trouble at all. But can your employees?
As cybercrime of all kinds, and phishing, in particular, reaches new heights in 2023, it’s important for every person in your organization to be able to identify a phishing attack and play an active role in keeping the business and your customers safe.
Phishing attack awareness training is an education program that teaches people:
- What phishing attacks are and how they work
- How to spot phishing emails and other attack methods
- Steps a person can take to avoid becoming a victim of a phishing attack
- How to report a suspected phishing attack
Learn More
What is phishing?
Phishing is an email scam that impersonates a reputable person or organization with the intent to steal usernames and passwords or other sensitive information, such as data. Although email is the most common type of phishing attack, depending on the type of phishing scam, the attack may occur via a text message (“smishing”) or even a voice message (“vishing”).
Why do you need phishing training?
As phishing incidents increase and more activity takes place online, it’s absolutely critical for organizations to take steps to protect the company and its digital assets. Unfortunately, people can be one of your biggest vulnerabilities, unwittingly launching malware or ransomware attacks simply by clicking a malicious link or downloading a corrupted file.
The most recent Internet Crime Report from the FBI’s Internet Crime Complaint Center (IC3) published in March 2022 reveals a 280% increase in phishing scams since the COVID-19 pandemic began in early 2020. This significant jump indicates cybercriminals’ ongoing intention to exploit people as a way to gain access to corporate systems and advance their attack plans.
While many companies leverage technology such as antivirus solutions and endpoint detection and response (EDR) to help limit risk, these tools are not foolproof. Further, as cybercriminals become more advanced, some tools, especially free or budget solutions, can become less effective at flagging suspicious messages. That means it’s up to your employees to help your company win the fight against phishing.
Is phishing training effective?
As with any corporate training or IT program, the answer depends. The quality of the program, the individual’s willingness to learn and the company’s culture will all influence how effective a phishing training program can be over both the short- and long-term.
Since many IT organizations lack in-depth cybersecurity expertise, it can be very helpful to engage a trusted partner to assess the organization’s level of awareness, identify gaps in knowledge and develop the skills and processes to ensure all employees are ready, willing and able to combat phishing and other cyber risks.
Steps to Implement Phishing Awareness Training
Phishing awareness should be a core component within every company’s overall cybersecurity training program. Here we outline the steps companies should take when implementing a phishing awareness training.
1. Plan Employee Education Materials
As a first step, the IT team should conduct intensive research or partner with a reputable cybersecurity vendor or expert to understand the unique risks the company faces. As part of this process, the team should review any past incidents the company may have experienced, as well as the business’s existing tools, policies and procedures that can help prevent future attacks.
From there, the organization should develop a customized training program, as well as supplemental tools, such as quizzes and simulations, to help employees strengthen their security awareness, adopt best practices, and observe company policies.
What Education Materials Should Cover
While every organization’s situation is unique and most require a customized training program, the phishing curriculum should cover the following topics:
- The typical phishing attack pattern
- Commonly used techniques by cybercriminals
- Typical characteristics of phishing messages
- The intent of attackers and typical outcomes of successful events
- What not to do if a recipient suspects an email may be part of a phishing campaign
- How to properly report phishing campaigns to both the IT team and authorities
Learn More
An estimated 50-70% of ransomware attacks target small- and medium-sized businesses, likely because adversaries believe smaller organizations do not have robust security measures in place to defend the business and its data.
To minimize this risk, businesses, especially SMBs, need to develop an employee cybersecurity training program that will educate their people about common security risks, promote responsible online behavior and outline steps to take when they believe an attack may be in progress.
Read: How to create an employee cybersecurity awareness training program
Using Real-World Examples to Improve Outcomes
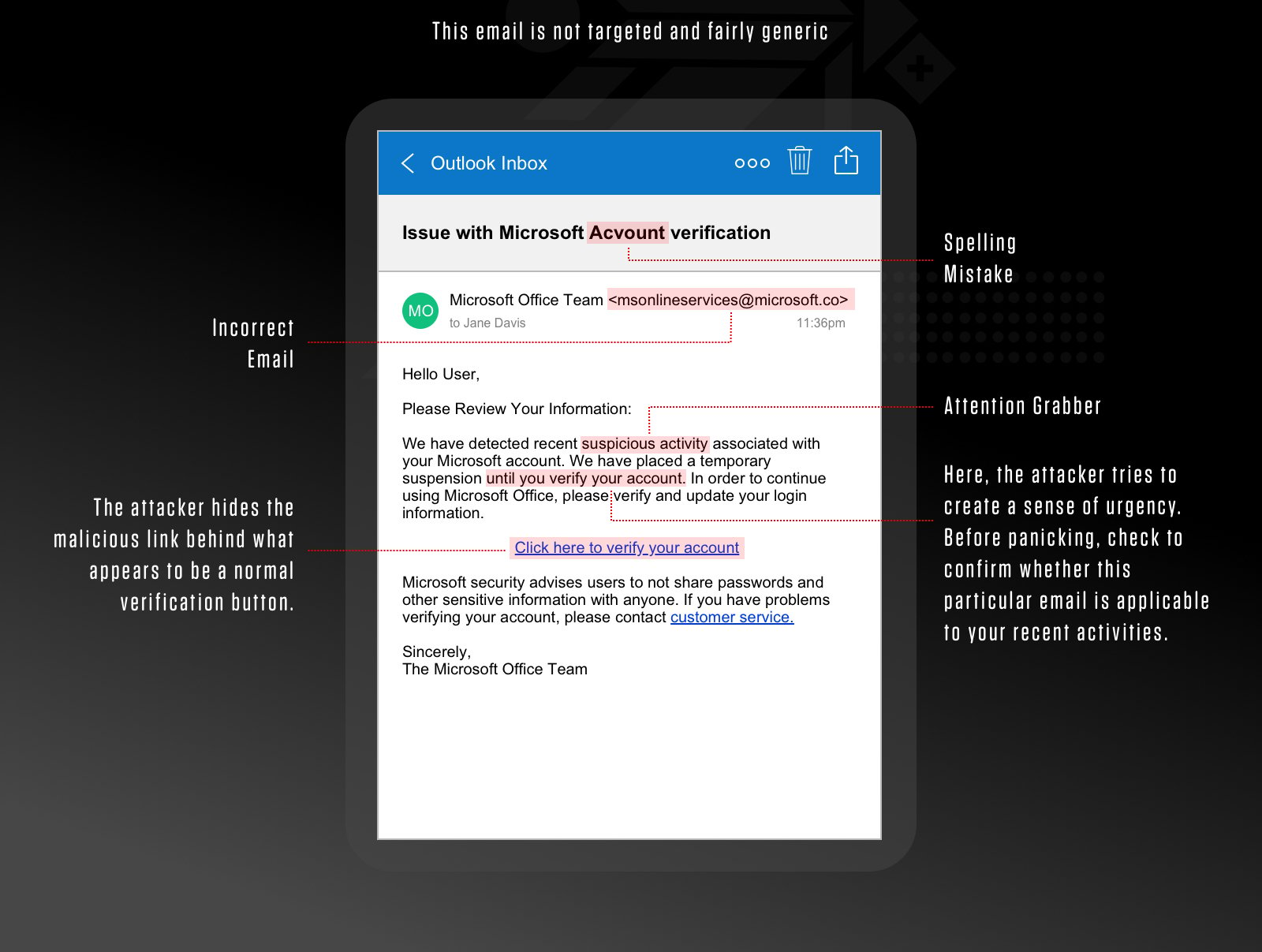
With the proper training and awareness, most basic phishing attacks can be easy to recognize. As part of the training course, it is helpful to use a variety of known phishing emails such as the one included below to help people spot common characteristics and identify the scam.
Phishing checklist
It might be a phishing email if the sender:
- Asks for sensitive information
- Uses a different domain
- Contains links that don’t match the domain
- Includes unsolicited attachments
- Is not personalized
- Uses poor spelling and grammar
- Tries to panic the recipient
2. Assign Phishing Attack Training Quiz
Once the training is complete, it’s important to assess participants’ knowledge and awareness about the topic and their ability to spot phishing emails and messages.
CrowdStrike has developed a Phishing Awareness Quiz, which features a variety of real-world phishing examples and asks employees to identify risky messages, as well as the steps they should take in the event they receive such a message. Incorporating this Phishing Awareness Quiz or one like it can help the IT team confirm the effectiveness of their training materials and identify areas where they may need further instruction.
3. Deploy Simulated Phishing Campaigns
Every training program should also include regular, unannounced simulated phishing tests to reinforce the curriculum, identify persistent weak spots and keep cybersecurity top of mind for people.
These tests could come in the form of emails, SMS messages or voicemails sent and monitored by the IT team. Individuals who click a link, download a file or respond to a message could be redirected to relevant training resources to help them improve their cybersecurity awareness and skills. The team can also use the results of such exercises to refine training materials or create custom courses on key topics.
4. Teach Employees How to Report Phishing Attacks
Every phishing awareness training program should also teach people the steps they should take to safely manage suspected phishing emails. This includes:
- Not opening, replying to or interacting with suspicious emails
- Immediately reporting the suspected phishing event to the IT team
- Informing teammates and colleagues to be on the lookout for similar messages
Expert Tip
To make the internet a safer place for everyone, corporate IT groups should also report phishing to the relevant authorities: phishing-report@us-cert.gov.
5. Evaluate Results and Test Regularly
Because phishing is an evolving and persistent threat, organizations should conduct regular refresher courses, as well as customized programs to teach people about new phishing campaigns, techniques and characteristics.
The IT team should also conduct regular tests and simulations to ensure employees remain vigilant in the fight against phishing. Results of these tests can be used to refine the training program and provide intensive instruction to individuals or teams who may be at higher risk of compromise.
Provide Readily Available Phishing Resources
It may also be helpful – and reassuring! – to let people know what additional steps the IT team is taking to limit the risk of phishing and other cyberattacks. This can include a wide variety of security tools, services, policies and procedures that are designed to limit their exposure to phishing attacks in the first place. These may include:
- Antivirus software that can prevent, detect and remove malware that enters the system through phishing.
- Antispam filters which use predefined blocklists created by expert security researchers to automatically move phishing emails to the user’s junk folder.
- Regular browser and software updates to provide stronger defenses against phishing scams, as new and innovative attacks are launched each day.
- Multifactor authentication (MFA), which requires a second level of verification, like an access code sent to your phone, before gaining access to a sensitive account.





