Simplifying API Security with Salt’s Falcon Foundry App for CrowdStrike Falcon

Roy Bar Yosef Technical Product Manager, Salt Security
Introduction
Deploying API security at scale is often a slow, manual, and error-prone process. Security teams must contend with OS-specific dependencies, disconnected consoles, and fragile scripts — all while trying to protect APIs that are increasingly targeted by attackers. These operational hurdles delay protection and leave critical assets exposed.
To address this, Salt Security partnered with CrowdStrike to build a native FalconFoundry App within the Falcon platform. This integration allows users to deploy and manage the Salt Sensor and Salt’s API traffic collector directly from the Falcon console using the built-in Real-Time Response (RTR) capabilities. The result is a streamlined, fully embedded experience: deployment in one click, consistent sensor management, and complete visibility across your infrastructure — all without leaving the Falcon console.
You can find the Salt app template in Foundry > App Templates.
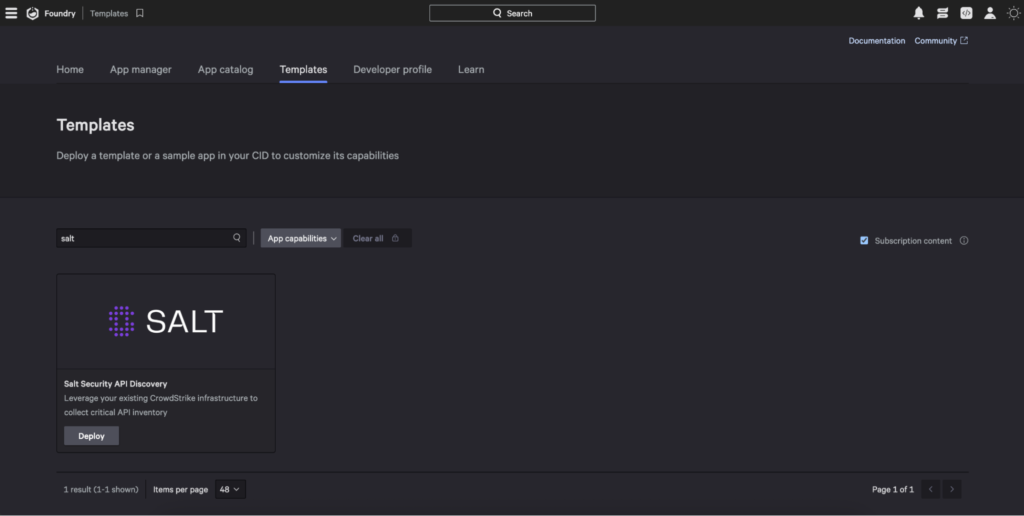
Salt Foundry App visible in the Falcon console
Built for Simplicity: How the Integration Works
The Salt Falcon Foundry App redefines how API security is deployed and managed in modern environments. By embedding sensor installation and lifecycle control directly into the Falcon console, it removes the operational overhead and fragmentation typically associated with deploying and managing API security at scale. This integration delivers immediate value through automated deployment, centralized oversight, and seamless alignment with existing endpoint security workflows.
- Zero-Friction Deployment – Sensors are deployed to Linux hosts with a single click. The app automatically detects system architecture and OS, fetches the correct package, injects tokens, and executes installation — no scripting or manual steps required.
- Unified Visibility and Control – Users can monitor deployment jobs, view audit logs, and check host coverage directly in the Falcon Console. Salt alerts and threat detections can also be forwarded into CrowdStrike’s Falcon Next-Gen SIEM for broader threat correlation.
- Faster Time to Protection – Installation and onboarding that used to take hours now takes minutes. Built-in SOAR workflows handle new host onboarding and sensor removal automatically, ensuring consistent coverage with minimal effort.
Technical Architecture: How We Built It
The Salt Foundry App is built on top of CrowdStrike’s Falcon Foundry framework — a modular development platform that allows third-party vendors to embed powerful integrations directly inside the Falcon console. This framework provides three primary capabilities: a secure, embeddable UI container, the foundry-fn-go FDK (Functions Development Kit), and the goFalcon SDK (Software Development Kit) for defining backend workflows, endpoints, and job orchestration. The UI layer handles user interactions and visual deployment flows, while the backend SDK logic processes sensor installation commands, status tracking, and data exchange with Salt’s backend APIs. Together, these components offer a complete framework for interactive, secure, and auditable deployment experiences embedded within the CrowdStrike ecosystem.
Foundry SDK (Go)
The Salt Foundry App uses the CrowdStrike Foundry FDK for Go to create robust RESTful APIs for orchestrating deployment workflows like sensor installation. Each route (e.g., /upsert-job) is registered using Foundry’s multiplexer and handled by a domain-specific Go struct that encapsulates the input, logic, and response.
The sensor installation workflow is driven by the InstallSaltSensorAction struct. This struct receives parameters like saltUrl, saltToken, and saltSensorUrl from the workflow input schema and validates them before triggering the RTR script execution. Here’s how it works:
func (action InstallSaltSensorAction) validate() []fdk.APIError {
var errs []fdk.APIError
if action.SaltToken == "" {
errs = append(errs, NewValidationError(InvalidActionConfig,
"invalid Salt Token"))
}
if action.SaltUrl == "" {
errs = append(errs, NewValidationError(InvalidActionConfig,
"invalid Salt Url"))
}
if action.SaltToken != "" && action.SaltUrl != "" {
body := "{}"
action.SaltUrl = strings.TrimSpace(action.SaltUrl)
req, err := http.NewRequest("POST",
action.SaltUrl+"/api/v1/http/exchange", strings.NewReader(body))
if err != nil {
errs = append(errs,
NewValidationError(InvalidActionConfig, "failed to create request to
SaltUrl"))
} else {
req.Header.Set("Authorization", "Bearer
"+action.SaltToken)
}
}
return errs
}
Falcon Foundry App UI Design
The Salt Falcon Foundry App’s user interface was built using a modern web stack with modular JavaScript and TailwindCSS for consistent, responsive design. The app frontend includes a clean, branded layout that matches the CrowdStrike design system, enabling seamless user experience within the Falcon console.
From the UI, users can:
- Select target host groups for sensor installation.
- View job progress and audit logs from within the same window.
- Trigger install/uninstall jobs with a single action.
The UI is rendered inside a secure web container provided by Falcon Foundry and communicates with backend functions via pre-defined RESTful endpoints. It was optimized for responsiveness and accessibility, ensuring operators can manage deployments from any environment without learning new tools.
The main elements include:
- Installation Wizard Panel – step-by-step deployment interface with real-time validation.
- Job Execution View – status updates for each host, color-coded by result.
- Audit Summary Section – logs key RTR interactions and error reasons.
Styling is handled through a structured CSS framework and the HTML is dynamically populated based on runtime variables fetched from CrowdStrike’s APIs. This allows rapid UI adjustments and data binding without requiring deep logic embedded in the front-end layer.
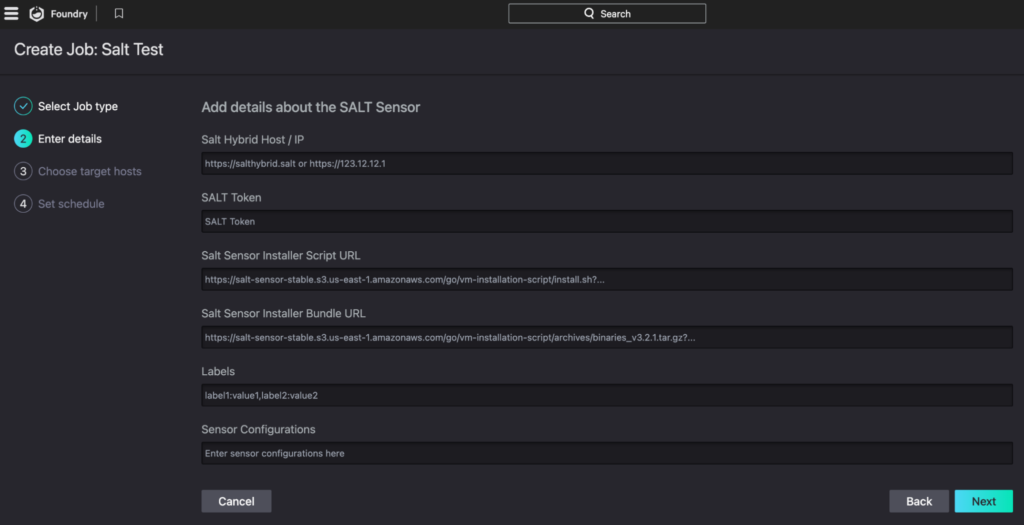
Workflow Automation
To streamline deployment, the Salt Falcon Foundry App packages a suite of workflow templates that handle the complete lifecycle of the Salt Sensor. These workflows are included with the app and automatically triggered through predefined conditions or user actions. Each workflow definition is YAML-based and leverages Falcon’s Real Time Response (RTR) engine to automate execution of custom code directly on the endpoints while maintaining full auditability. The included workflows are:
- Install Salt Sensor: Queries Linux devices based on predefined group conditions, installs the Salt Sensor using RTR, logs activity, and applies labeling for traceability.
- New Asset Install Salt Sensor: Automatically triggered when a new managed asset is detected. It introduces a short delay for system readiness, then validates platform and group criteria before proceeding with installation and logging.
- Remove Salt Sensor: Targets existing Linux devices tagged with Salt Sensor, validates conditions, executes the uninstallation process, updates audit logs, and removes the associated device tags.
By packaging these workflows with the application, Salt ensures seamless, consistent, and observable deployment operations across diverse environments.
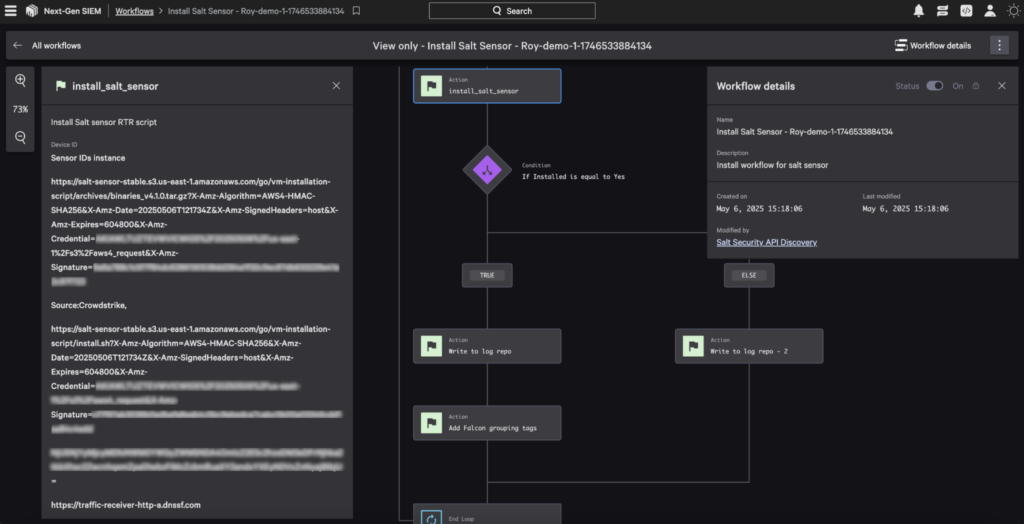
Visual representation of the “Install Salt Sensor” SOAR workflow as seen in Falcon’s workflow editor.
Falcon Agent & Real Time Response
The Salt Falcon Foundry App leverages CrowdStrike’s Real Time Response (RTR) capability to remotely install and manage the Salt Sensor on Linux endpoints already running the Falcon Agent. Instead of introducing new agents, the app executes pre-packaged shell scripts via RTR, using contextual information and deployment parameters defined in Foundry workflows.
The workflow invokes an action (rtr_scripts.install_salt_sensor) that runs the Salt Sensor installation script with parameters such as the Salt token, URLs, labels, and configuration. These values are defined in the job request body and schema:
// input_schema.json
{
"properties": {
"saltToken": { "type": "string" },
"saltSensorUrl": { "type": "string" },
...
"sensorConfig": { "type": "string" }
},
"required": [
"saltToken",
"saltUrl",
"saltSensorUrl",
"saltArtifactUrl"
]
}
The actual script executed via RTR is Salt Security’s unified installation script, designed to handle a wide variety of Linux distributions and environments. Upon execution, the script dynamically detects the operating system and distribution type and installs required dependencies. It then fetches the correct Salt Sensor binary using the provided saltArtifactUrl, tailored to the system’s OS and architecture, ensuring compatibility. Labels and optional runtime configurations (like sensorConfig) are appended before executing the installation, enabling fine-grained telemetry and control.
# script.sh (combined excerpt)
...
define_distro() {
log "Detecting distribution..."
parse_os_release
case "$DISTRO_NAME" in
*Ubuntu*) DISTRO="ubuntu" ;;
*Red?Hat*) DISTRO="redhat" ;;
*Amazon?Linux*) DISTRO="fedora" ;;
*SUSE*) DISTRO="suse" ;;
*) error_exit "Unsupported distribution: $DISTRO_NAME" ;;
}
...
perform_installation() {
log "Starting the salt-sensor installation process..."
...
perform_installation "$saltSensorUrl" "$saltToken" "$saltUrl" "$saltArtifactUrl" "$labels"
...
log "Installation completed successfully."
...
}
Debugging and Logging
The Salt Falcon Foundry App builds on CrowdStrike’s Scalable RTR sample app, leveraging its native audit and logging mechanisms. This provides a consistent structure for capturing all RTR executions, including job metadata, script responses, and failure messages.
To extend this foundation, Salt integrates custom logging actions that persist key runtime signals to a dedicated audit collection. These include device-level success flags, installation output, group context, and timestamps—enabling detailed post-execution analysis. Each job lifecycle is tracked via functions.job_history.update_job_history, while write_to_log_repo actions ensure contextual data is recorded at both success and failure points.
RTR Audit Log – shows script execution output and install status:
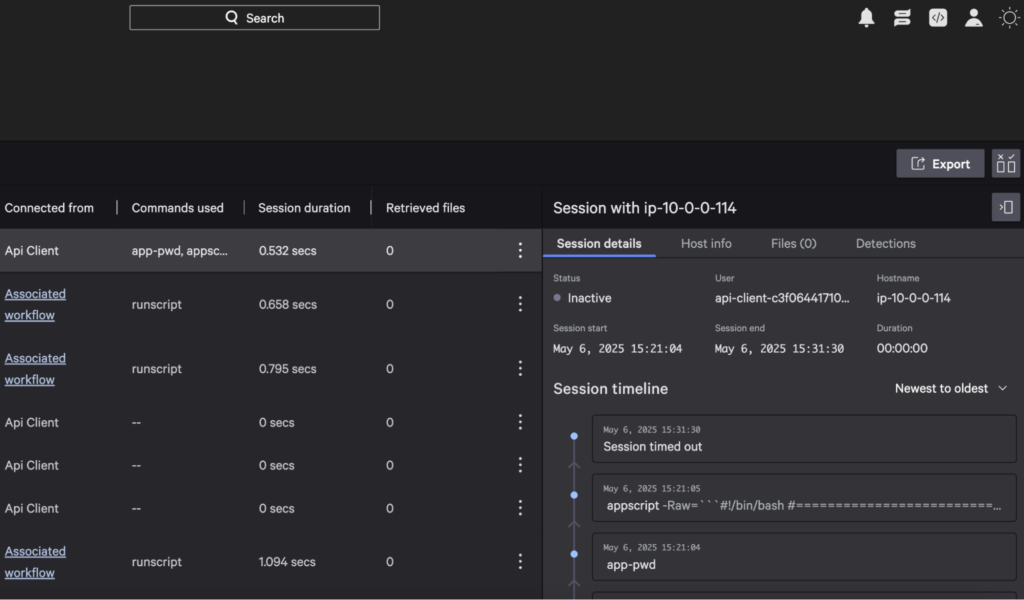
Falcon Foundry Job Audit Log – captures job status transitions
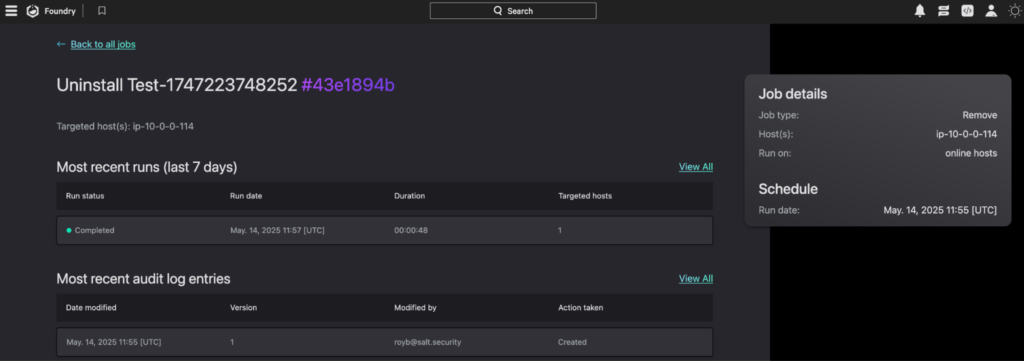
Salt Dashboard Integration
The final piece that completes the integration experience is the dedicated Salt Dashboard tile for the CrowdStrike Falcon Foundry App. This tile was purpose-built within Salt’s console to make it easy for customers to finish the deployment journey with just a few clicks.
This dashboard tile provides:
- Clear integration instructions tailored to the customer’s selected deployment environment, including required tokens, URLs, and command examples.
- Copy-paste simplicity to execute final setup steps, minimizing the risk of misconfiguration.
- Contextual visibility into sensor deployment status across hosts that were onboarded via CrowdStrike’s Falcon console.
- Consistent branding and user experience, making the deployment feel like a native extension of the Salt platform.
By surfacing the Falcon Foundry App contextually inside the Salt Dashboard, we ensure that users have everything they need to complete the integration in one centralized view — eliminating guesswork and accelerating time to protection.

Business Impact
The Salt Falcon Foundry App provides tangible business benefits that drive value for joint Crowdstrike and Salt customers. First and foremost, it significantly accelerates deployment time, reducing the process from hours to just minutes. The automation and centralized management capabilities eliminate many of the manual steps traditionally associated with security tool rollouts, minimizing configuration errors and streamlining operations. By consolidating management into a single platform, it also reduces the complexity and overhead typically placed on security teams. As a result, organizations benefit from enhanced threat protection, broader security coverage, and more efficient use of resources — all while lowering operational costs.
Strategic Impact
This integration between Salt and CrowdStrike delivers strategic value for both customers and the broader security ecosystem. For existing Falcon users, it offers an effortless path to extend their protection coverage to APIs, one of the most vulnerable parts of the modern application stack. By simplifying adoption and deployment, the integration increases the likelihood that customers will embrace Salt’s API security platform, accelerating time to value and boosting overall satisfaction. Furthermore, being part of the CrowdStrike Falcon Foundry low-code application platform strengthens Salt’s visibility in the market and reinforces its position as a leader in API security. This partnership reflects the growing demand for unified security strategies and highlights the critical role of APIs in the enterprise attack surface.
What’s Next
Looking ahead, we are focused on deepening the integration and expanding the value it delivers to customers. Areas of exploration include enhanced threat intelligence sharing between Salt and CrowdStrike to enable more comprehensive threat detection and response. We are also working on advanced policy management features that will give security teams greater control and flexibility over their API protection strategies. Another exciting development is real-time adaptation, where the Salt Sensor will dynamically adjust based on threat patterns and behavioral changes in the environment. These future enhancements aim to make the joint Salt + CrowdStrike solution even more intelligent, responsive, and aligned with evolving enterprise security needs.
Final Thoughts
API security is foundational to modern enterprise protection. By embedding Salt into the Falcon platform, we’ve created a unified solution that enhances deployment, visibility, and protection.
Security teams get faster, more effective coverage for their most exposed assets: their APIs.
Want to see it in action?
Reach out to your Salt Security representative for a demo of the Salt Falcon Foundry App.