Microsoft has released 117 security patches for its April Patch Tuesday rollout. Of the 117 CVEs addressed, two are ranked as Important zero-days, including CVE-2022-24521, which is under active exploitation. This zero-day was discovered by CrowdStrike Intelligence and affects the Windows Common Log File System. Additionally, this month featured 10 critical vulnerability patches, bringing the total number of updates to nearly double what was offered in March 2022.
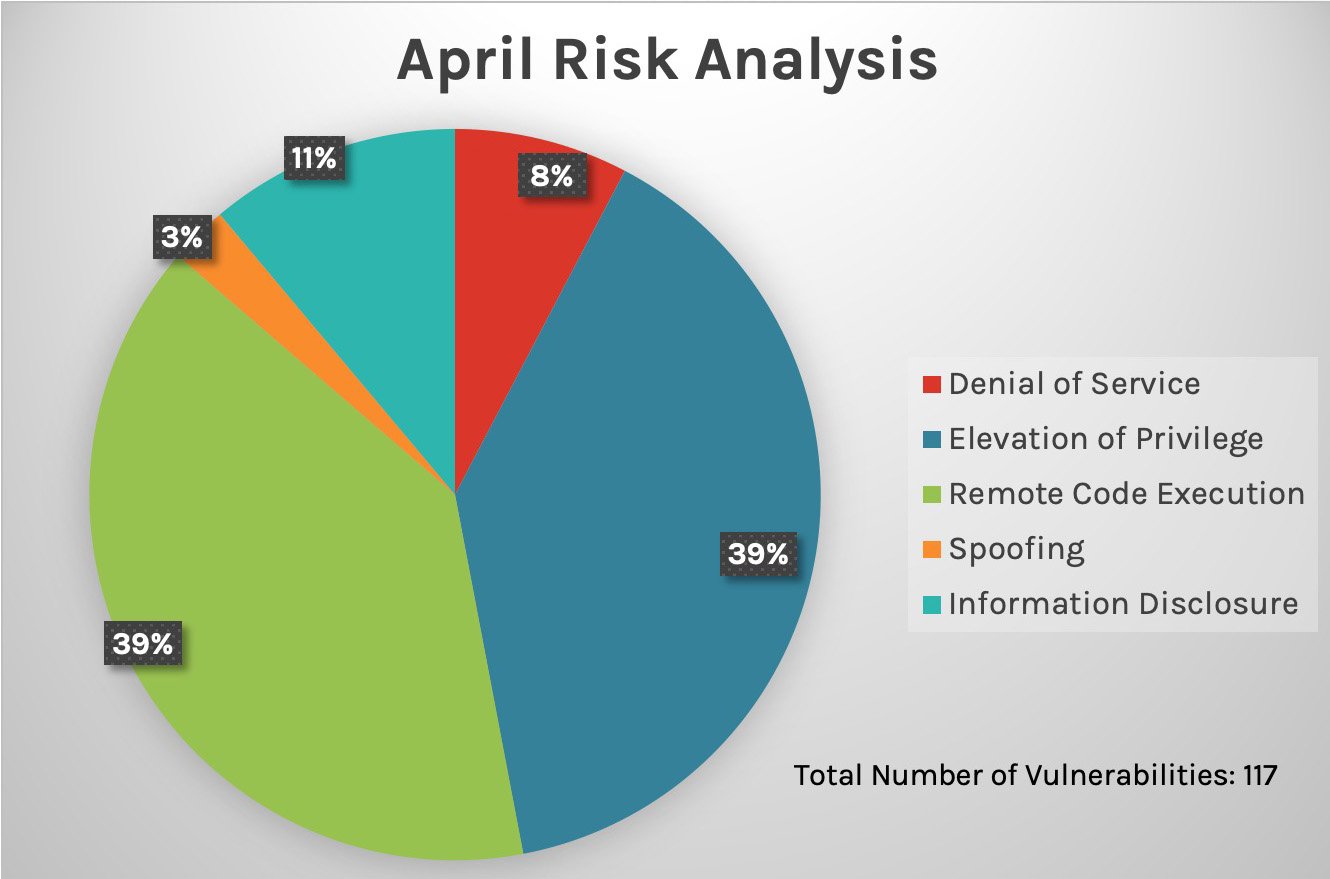 Figure 1. Breakdown of April 2022 Patch Tuesday attack types
The affected product families, however, are much different than last month. For April 2022, Developer tools saw a significant increase in vulnerabilities patched. Microsoft Office has taken second place in receiving the most patches, with Windows and Extended Security Updates following close behind.
Figure 1. Breakdown of April 2022 Patch Tuesday attack types
The affected product families, however, are much different than last month. For April 2022, Developer tools saw a significant increase in vulnerabilities patched. Microsoft Office has taken second place in receiving the most patches, with Windows and Extended Security Updates following close behind.
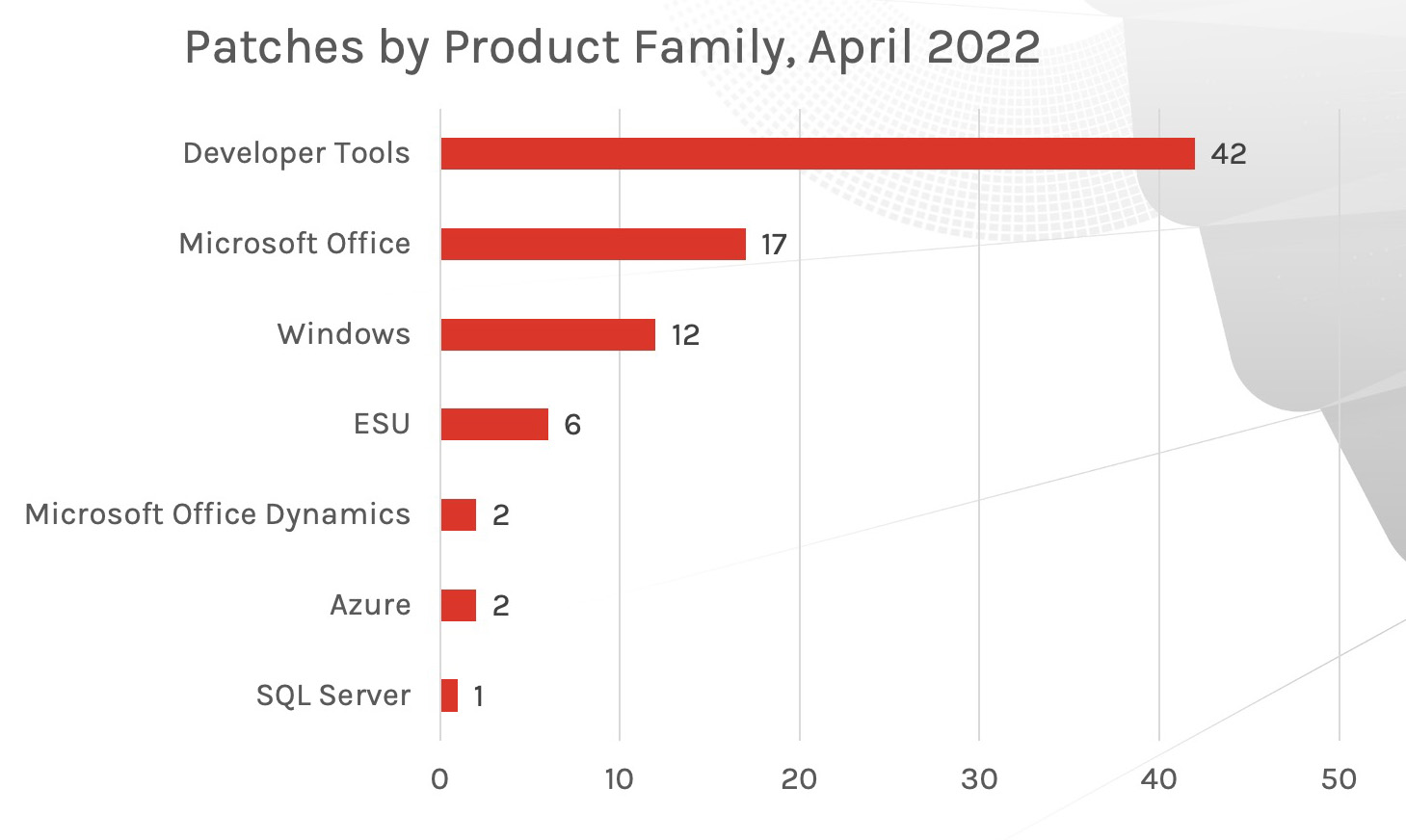 Figure 2. Breakdown of April 2022 Patch Tuesday affected product families
Figure 2. Breakdown of April 2022 Patch Tuesday affected product families
Two Zero-Day Vulnerabilities, One Under Active Attack
The two zero-day vulnerabilities patched this month received CVSS scores between 7 and 7.8 — a rank of Important. Nonetheless, these vulnerabilities are relevant to any organization using the affected products. CrowdStrike Falcon® Spotlight™ ExPRT.AI provides valuable data and insights for a more accurate understanding of how these zero-day vulnerabilities could affect your environment.CVE-2022-24521: Windows Common Log File System Driver elevation of privilege vulnerability. Although given a CVSS score of 7.8, Microsoft has seen active exploitation with a low attack complexity. Now that Microsoft has issued a patch, adversaries may be analyzing the details of this vulnerability to learn how to better exploit it.
CVE-2022-26904: Windows User Profile Service elevation of privilege vulnerability. This publicly known zero-day flaw impacts the Windows User Profile Service and has a CVSS severity score of 7.0. In addition to having a proof-of-concept (POC) code available, there’s a Metasploit module. This vulnerability allows an attacker to gain code execution at SYSTEM level on affected systems. Microsoft has not seen this exploited in the wild.
| Rank | CVSS Score | CVE | Description |
| Important | 7.8 | CVE-2022-24521 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| Important | 7.0 | CVE-2022-26904 | Windows User Profile Service Elevation of Privilege Vulnerability |
April 2022 Risk Analysis
The top three attack types — remote code execution, elevation of privilege and information disclosure — continue to dominate, with denial of service following at almost 8% (up from 5% in March). Figure 1. Breakdown of April 2022 Patch Tuesday attack types
Figure 1. Breakdown of April 2022 Patch Tuesday attack types Figure 2. Breakdown of April 2022 Patch Tuesday affected product families
Figure 2. Breakdown of April 2022 Patch Tuesday affected product familiesCritical Vulnerabilities in LDAP, Hyper-V and SMB
Ten vulnerabilities ranked as Critical received patches this month across a number of Microsoft products, most notably in Windows Network File System (NFS) and Remote Procedure Call (RPC) runtime.CVE-2022-26809: Remote Procedure Call (RPC) runtime remote code execution vulnerability. This flaw is rated CVSS 9.8, and is described as “exploitation more likely” by Microsoft. It could allow an attacker to execute code with high privileges on an affected system. Since no user interaction is required, these factors combine to make this wormable, at least between target hosts where RPC can be reached. However, the static port used (TCP port 135) is typically blocked at the network perimeter. This vulnerability could be used for lateral movement by an attacker. We recommend that your team test and deploy this patch quickly as possible.
CVE-2022-24491 and CVE-2022-24497: Windows Network File System remote code execution vulnerabilities. These two NFS vulnerabilities also have a 9.8 CVSS score and are listed as “exploitation more likely.” On systems where the NFS role is enabled, a remote attacker could execute their code on an affected system with high privileges and without user interaction. Again, that adds up to a wormable bug — at least between NFS servers. Similar to RPC, this is often blocked at the network perimeter. Microsoft offers some guidance on how the RPC port multiplexer (port 2049) “is firewall-friendly and simplifies deployment of NFS.” Check your installations and roll out these patches rapidly.
| Rank | CVSS Score | CVE | Description |
| Critical | 8.1 | CVE-2022-26919 | Windows LDAP Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2022-23259 | Microsoft Dynamics 365 (on-premises) Remote Code Execution Vulnerability |
| Critical | 7.8 | CVE-2022-22008 | Windows Hyper-V Remote Code Execution Vulnerability |
| Critical | 7.8 | CVE-2022-24537 | Windows Hyper-V Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2022-23257 | Windows Hyper-V Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2022-24491 | Windows Network File System Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2022-24497 | Windows Network File System Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2022-26809 | Remote Procedure Call Runtime Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2022-24541 | Windows Server Service Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2022-24500 | Windows SMB Remote Code Execution Vulnerability |
18 Windows DNS Server Remote Code Execution Vulnerabilities
Eighteen RCE vulnerabilities affecting Windows DNS Server received patches this month. All are ranked as Important, with two vulnerabilities that warrant additional attention.CVE-2022-26815: This vulnerability is the most severe of the 18 DNS Server CVEs patched this month. This flaw is also very similar to one (CVE-2022-21984) patched in February, which raises the question whether or not this month’s patch for CVE-2022-26815 is the result of a failed or incomplete patch. Important to note for patching teams:
- Dynamic updates must be enabled for a server to be affected
- CVSS details lists a level of privileges to exploit
To exploit this vulnerability, the attacker or targeted user would need specific elevated privileges. As is best practice, regular validation and audits of administrative groups should be conducted.
| Rank | CVSS Score | CVE | Description |
| Important | 8.8 | CVE-2022-26815 | Windows DNS Server Information Disclosure Vulnerability |
| Important | 7.5 | CVE-2022-26814 | Windows DNS Server Information Disclosure Vulnerability |
| Important | 7.5 | CVE-2022-26817 | Windows DNS Server Information Disclosure Vulnerability |
| Important | 7.5 | CVE-2022-26818 | Windows DNS Server Information Disclosure Vulnerability |
| Important | 7.5 | CVE-2022-26829 | Windows DNS Server Information Disclosure Vulnerability |
| Important | 7.2 | CVE-2022-24536 | Windows DNS Server Information Disclosure Vulnerability |
| Important | 7.2 | CVE-2022-26811 | Windows DNS Server Information Disclosure Vulnerability |
| Important | 7.2 | CVE-2022-26813 | Windows DNS Server Information Disclosure Vulnerability |
| Important | 7.2 | CVE-2022-26823 | Windows DNS Server Information Disclosure Vulnerability |
| Important | 7.2 | CVE-2022-26824 | Windows DNS Server Information Disclosure Vulnerability |
| Important | 7.2 | CVE-2022-26825 | Windows DNS Server Information Disclosure Vulnerability |
| Important | 7.2 | CVE-2022-26826 | Windows DNS Server Information Disclosure Vulnerability |
| Important | 6.7 | CVE-2022-26812 | Windows DNS Server Information Disclosure Vulnerability |
| Important | 6.6 | CVE-2022-26819 | Windows DNS Server Information Disclosure Vulnerability |
| Important | 6.6 | CVE-2022-26820 | Windows DNS Server Information Disclosure Vulnerability |
| Important | 6.6 | CVE-2022-26821 | Windows DNS Server Information Disclosure Vulnerability |
| Important | 6.6 | CVE-2022-26822 | Windows DNS Server Information Disclosure Vulnerability |
| Important | 4.9 | CVE-2022-26816 | Windows DNS Server Information Disclosure Vulnerability |
RCE Is Still a Popular Attack Type, So Consider Prioritizing Patches Accordingly
This month’s Patch Tuesday contains 47 patches for RCE bugs. In addition to those already mentioned is yet another RDP client flaw (CVE-2022-24533) that would allow code execution if a user connected to a malicious RDP server. If that sounds familiar, it’s because there was a similar bug last month, with a number of related CVEs going further back. There are a few open-and-own vulnerabilities in Office components, most notably Excel, that have also received patches this month. The chance of people applying patches to Excel before April 15 appears low, but there is risk of exploitation if patching isn’t applied. Another vulnerability to consider is CVE-2022-26788 (another CVE this month discovered by CrowdStrike, this one in conjunction with VMware), which is a PowerShell privilege elevation CVE. It’s ranked as Important with a CVSS of 7.8.CrowdStrike recommends continually reviewing your patching strategy, as vigilance can make a dramatic difference in keeping your environments protected.
Learn More
Watch this video on Falcon Spotlight™ vulnerability management to see how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- See how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- Learn how Falcon Identity Protection products can stop workforce identity threats faster.
- Download the CrowdStrike 2022 Global Threat Report to learn who and what is affecting your environment.
- Learn about the latest trending threat in Linux and how you can find it.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself with a free trial of Falcon Prevent™.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)
![Endpoint Protection and Threat Intelligence: The Way Forward [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/GK-Blog_Images-1)








































