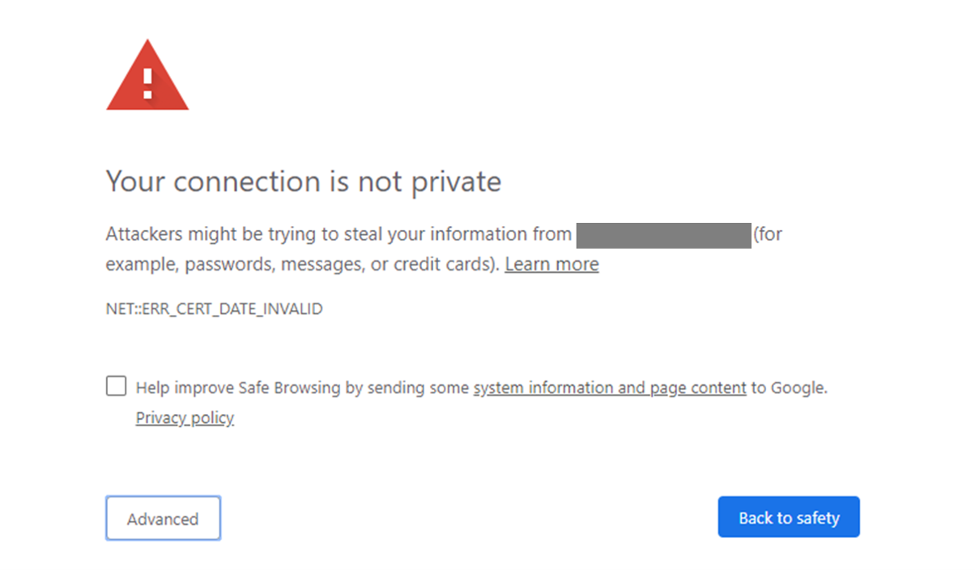
SSL certificates grant authentication to your websites or domains and are critical for ensuring proper encryption of internet traffic and verified server identity. Without these certificates, end users will have no way of knowing if the website they are currently browsing is what it claims to be.
A change in policy in 2020 by Apple, Google and Mozilla mandated that SSL certificates operate for a period of no longer than 398 days, after which they expire. If not renewed on time, expired SSL certificates leave your organization exposed to a range of both cyber and business risks.
The shorter certificate validity period facilitates algorithm upgrades, and faster certificate and key replacements, especially during malicious cyberattacks. The less time required to deploy changes and updates, the lower the security risk. The purpose of digital certificates, like TLS/SSL certificates, is to verify the identity of the website or website owner and encrypt the connection between client (browser) and server (website). A longer certificate lifespan means long expiration of validation, which fuels the exposure to security lapses due to obsolete encryption protocols.
There is no lack of tools that are supposed to help IT and security teams manage these certificates and renew them on time. Nevertheless, domains with expired certificates are prevalent and becoming increasingly common due to recent updates to certificates expiration periods.
What Are the Risks?
Your Website Could Be Less Secure
Once an SSL certificate expires, other clients (users with browsers) cannot verify your website authenticity. In addition, it may not comply with the latest security standards, leading to vulnerability in encryption mechanisms down the line.
Customers’ Trust and Revenue Are at Stake
SSL certificates are a cornerstone in building a trust-based relationship between your business and customers. You want to provide a safe and secure environment for your website users, ensuring their comfort when they provide personal data, such as home address or credit card info. The padlock on the top left corner of the browser is a fundamental component in the chain of trust.
Once your SSL certificate expires, the browser will immediately flag your website and warn any visitor wanting to access your website. This will dramatically reduce the traffic to your website.
In addition, expired SSLs can lead to service outages that in turn damage both your reputation, customer trust and revenue stream. An Azure 2014 outage was due to an expired SSL certificate, while 2020 witnessed several high-profile cases of online services disruption caused by expired SSL certificates: For example, GitHub’s CDN SSL certificate expired and led to several malfunctions of its site, leaving millions of its users confused, and Spotify’s SSL certificate expired and resulted in a major downtime in its music streaming services and many disappointed users.
Man-in-the-Middle (MITM) Attack
A man-in-the-middle attack is a type of cyberattack where the attacker secretly relays — and possibly alters — the correspondence between two parties who believe that they are directly communicating with each other. One example of a man-in-the-middle attack is active eavesdropping, where the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker.
The POODLE Attack
POODLE attacks are actually a vulnerability of SSL version 3.0 protocol, defined as “Padding Oracle On Downgraded Legacy Encryption,” aka POODLE vulnerability. SSL 3.0 vulnerability stems from the way blocks of data are encrypted under a specific type of algorithm within the SSL protocol. The POODLE attack takes advantage of the protocol version negotiation feature built into SSL/TLS to force the use of SSL v3.0 and then leverages this new vulnerability to decrypt select content within the SSL session. The decryption is done byte by byte and will generate a large number of connections between the client and server. In simpler words, the POODLE attack is a type of MITM attack that allows sensitive data such as user information to be exposed to malicious attackers. This alarming situation happens when using the SSL v3.0 for communicating encrypted transactions back and forth through the website server to the user’s browser.
But don’t worry, executing POODLE attacks are not that simple — for one to happen, an attacker must first perform a MITM attack from start to end, then hope the server uses the SSL v3.0 or persuades the server to use it by performing connection dropouts. This then indicates if the user is able to use the same TLS protocol, forcing the server to try and use the previous version (SSL v3). If both the MITM attack and the forces protocol succeed, they would then be vulnerable to the POODLE attack, which an attacker can take advantage of and come after the information communicated between the parties.
The BEAST Attack
BEAST (Browser Exploit Against SSL/TLS) attacks exploit a vulnerability in the Transport-Layer Security (TLS) 1.0 and older SSL protocols, using the cipher block chaining (CBC) mode of encryption. It allows attackers to capture and decrypt HTTPS client-server sessions and obtain authentication tokens. It does so by combining a MITM, along with a record-splitting and chosen boundary attack. The theoretical vulnerability for the BEAST attack was described by Phillip Rogaway as early as 2002. A proof of concept for the attack was demonstrated in 2011 by security researchers Thai Duong and Juliano Rizzo. The BEAST attack has some similarities to protocol downgrade attacks, such as POODLE, in that it also uses a MITM approach and exploits vulnerabilities in CBC. The exploit was fixed in TLS 1.1 and later, but at the time of discovery, there was no browser support for TLS 1.1 and newer TLS versions.
The CRIME Attack
CRIME (Compression Ratio Info-leak Made Easy) is a security vulnerability that allows an attacker to perform session hijacking on an authenticated web session. This is done by compression, which can leak the content of secret web cookies. CRIME was assigned CVE-2012-4929. CRIME was developed by two security researchers, Juliano Rizzo and Thai Duong. It decrypts the session cookies from the hypertext transfer protocol secure (HTTPS) connections by means of brute force. CRIME attack induces a vulnerable web browser into percolating a cookie authentication, created when a user starts an HTTPS session with a website. The obtained cookie can be used by hackers to log in to the victim’s account on the site.
Is It So Difficult to Renew SSL Certificates on Time?
In theory, no. There are plenty of accessible certificate management tools that solve this problem. But the rising number of headlines relating to cyber incidents resulting from expired SSL certificates is suggesting that it may not be that simple.
IT and security teams at large-scale organizations must keep track of hundreds, if not thousands, of websites and domains and make sure their certificates are renewed on time.
The problem? Teams are often unaware of all websites and domains that belong to their organization and its subsidiaries. Some of these sites and domains might have been created without their knowledge, while others may have been forgotten or abandoned.
Even when using the most convenient automated tool, you can only track the SSL certificates for websites and domains you are aware of.
How Can CrowdStrike Help?
The CrowdStrike Falcon® Surface external attack surface management module automatically creates an organization’s internet-facing asset inventory and analyzes assets for a wide range of security issues including SSL certificates about to expire or recently expired, and abandoned subdomains that are susceptible to hostile takeover.
The solution alerts you when SSL certificates are about to expire, either in your organizations or subsidiaries, so your team can remediate the issue in real time.
Visit the product webpage to learn more about how Falcon Surface provides a comprehensive analysis of your external attack surface to discover all of your internet-facing assets including domains and expired SSL certificates.
Additional Resources
- Want to learn more about Falcon Surface? Join our CrowdCast to hear about five key considerations before investing in an EASM solution.
- Visit the Falcon Surface product webpage.
- Download the Falcon Surface data sheet.
- See for yourself how the industry-leading CrowdStrike Falcon platform protects against modern threats. Start your 15-day free trial today.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)