Twenty years ago, Microsoft introduced the concept of Patch Tuesday to “reduce the burden on IT administrators by adding a level of increased predictability and manageability.” The goal of Patch Tuesday was to provide needed structure around what was largely an ad hoc process.
By consolidating the majority of security updates and required patches into a planned release cycle, IT departments and system administrators could better plan and allocate resources to eliminate some of the chaos that followed a patch release. To this day, Patch Tuesday persists. Microsoft still releases security updates on the second Tuesday of every month.
But while the schedule has remained constant — with exceptions for occasional emergency fixes — the world has changed since October 2003. To support remote work, organizations raced into the digital age by rapidly moving to the cloud and eliminating traditional security perimeters. The number of endpoints, connected devices, applications and cloud estates that need to be managed has skyrocketed, creating a broader surface for vulnerabilities to manifest.
The Microsoft product ecosystem has also grown dramatically, covering a range of technology, software, applications, cloud offerings and more. This has resulted in a larger number of vulnerabilities spanning the technology stack and an expansion of enterprise risk. The burden of dealing with this massive growth in vulnerabilities — and cyberattacks targeting them — is too often shifted from the vendor to the customer. This is why for many security and IT teams, Patch Tuesday is no longer a beacon of hope in the chaos of patching. It has become emblematic of the nightmare they face each month as they race to prioritize patches, understand the downstream impact and act before an adversary can exploit the vulnerabilities putting them at risk.
20 Years Later: Microsoft’s Vulnerability Problem Has Grown
The ubiquity of Microsoft products and volume of Microsoft vulnerabilities have created a massive attack surface. This shouldn't be a surprise given the popularity of Microsoft’s operating system and office software. One survey found “Microsoft Windows is the most widely used computer (desktop, tablet and console) operating system (OS) in the world.”
Adversaries constantly seek weak points in potential victims’ environments. And as we’ve seen with the growth of Patch Tuesday over the years, Microsoft vulnerabilities provide a broad landscape for adversaries to target.
Since Patch Tuesday began, Microsoft has issued more than 10,900 patches, most of them in just the last few years. Since 2016, Microsoft has patched 124 unique zero-day vulnerabilities, 1,200+ unique vulnerabilities classified as Critical and 5,300+ rated as Important in severity. More than 630 exploits exist for Critical and Important vulnerabilities. In 2023 alone, Microsoft has already issued patches for more than 800 vulnerabilities.
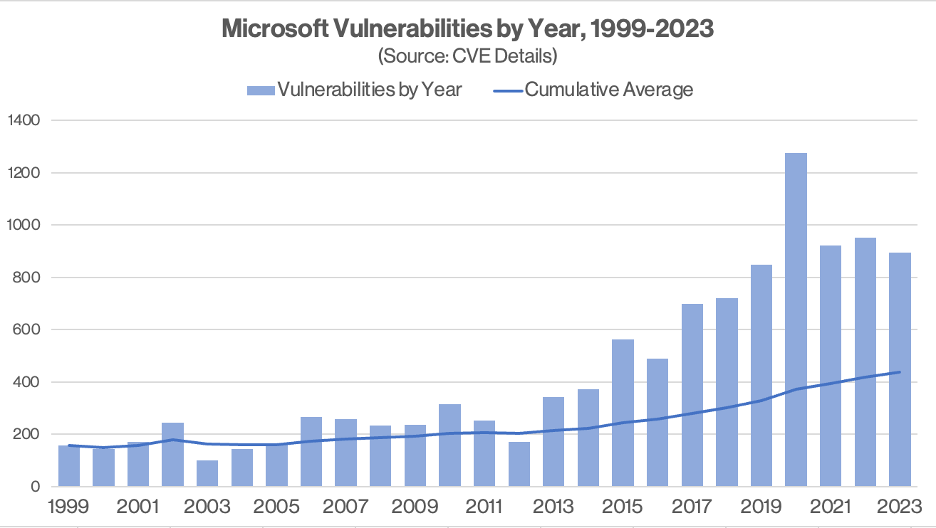 This data can be found at CVE Details.
This data can be found at CVE Details.These numbers may seem high, but they actually conceal the scale of the problem. If we extrapolate the 1,200+ unique critical vulnerabilities Microsoft has issued patches for since 2016 to account for the same vulnerabilities impacting multiple Microsoft products, the number of total critical vulnerabilities jumps to almost 21,000+. While most Microsoft patches will address multiple affected Microsoft products with a single install, there are always exception cases and specific patching processes may vary.
The massive growth of Microsoft’s vulnerability problem has more than offset efficiencies gained through tinkering with the patching process. For many security and IT teams, Patch Tuesday has become more of a burden. They need to scramble to figure out which vulnerabilities to prioritize, which put them most at risk, which could have downstream impact on IT and which could make or break the business. It often seems that just as the team is figuring what to prioritize, another batch of vulnerabilities drops.
This has a huge impact in terms of time, cost, resources and risk. According to the Infosec Institute, the average time it takes to patch a vulnerability can be anywhere from 60 to 150 days. Some security and IT teams take “at least 38 days to issue a patch.” The pace of patching is no match for the speed of the modern adversary and its ability to exploit vulnerabilities.
If a vulnerability isn’t patched fast enough and a breach occurs, the victim is often blamed for falling short of security practices and failing to patch. This ignores the fact that the sheer scale of Microsoft vulnerabilities has once again shifted the burden back to the customer — a burden that grows as adversaries continue to weaponize vulnerabilities.
Microsoft Vulnerabilities: The Attack Surface of the Modern Adversary
Microsoft product vulnerabilities have become the de facto attack surface of the modern adversary. It shouldn’t be surprising that adversaries are weaponizing this growing problem.
According to research published by the Cybersecurity and Infrastructure Security Agency (CISA), four of the 12 Top Routinely Exploited Vulnerabilities are in Microsoft products. CISA also noted Microsoft topped the list of exploited CVEs used in ransomware attacks. More than 40% of the vulnerabilities exploited to deploy ransomware are associated with Microsoft products.
Not only are adversaries exploiting existing flaws, they’re also ushering in a new era of “vulnerability rediscovery.” The CrowdStrike 2023 Global Threat Report found adversaries are modifying or reapplying the same exploit to target other, similarly vulnerable products. They’re also circumventing earlier patches.
As an example of this activity, the report highlights “... the proxy mechanisms exploited to compromise Microsoft Exchange during ProxyLogon and ProxyShell campaigns in 2021 were targeted again in Q4 2022, this time using an authenticated variation called ProxyNotShell (CVE-2022-41040 and CVE-2022- 41082). ProxyNotShell mitigations were subsequently bypassed when ransomware-affiliated actors used an alternative exploitation vector that abused CVE-2022-41080 to accomplish the same objectives.”
Modern adversaries are faster, smarter and more ruthless than ever, while the volume of vulnerabilities and the process of testing and patching can slow down teams trying to protect their organizations from attacks.
Patch Tuesday was supposed to give security and IT teams an advantage against the adversary, but the sheer volume of Microsoft vulnerabilities over the last several years has had the reverse effect. Patching systems, changing configurations and similar actions impact the tools and workflows of business. These changes can have a material impact on productivity. This is compounded by the risk of not patching. The speed at which adversaries are exploiting vulnerabilities continues to increase.
While Patch Tuesday itself is not the problem, it has become emblematic of the broader vulnerability issue that plagues the industry. Until companies like Microsoft start making more secure products by design and alleviate the burden of patching, organizations must understand the risks they face and take proactive steps to discover and prioritize the vulnerabilities that can cause the most damage.
When it comes to protection, it’s worth asking: Who do you trust? Can you trust the vendor selling security when it’s also responsible for such a high volume of critical vulnerabilities?
Additional Resources
- Download the CrowdStrike 2023 Global Threat Report and CrowdStrike 2023 Threat Hunting Report to learn how the threat landscape has shifted in the past year and understand the adversary behavior driving these shifts.
- See how Falcon Spotlight can help you discover and manage vulnerabilities and prioritize patches in your environments.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself with a free trial of CrowdStrike Falcon® Prevent next-generation antivirus.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)


















































