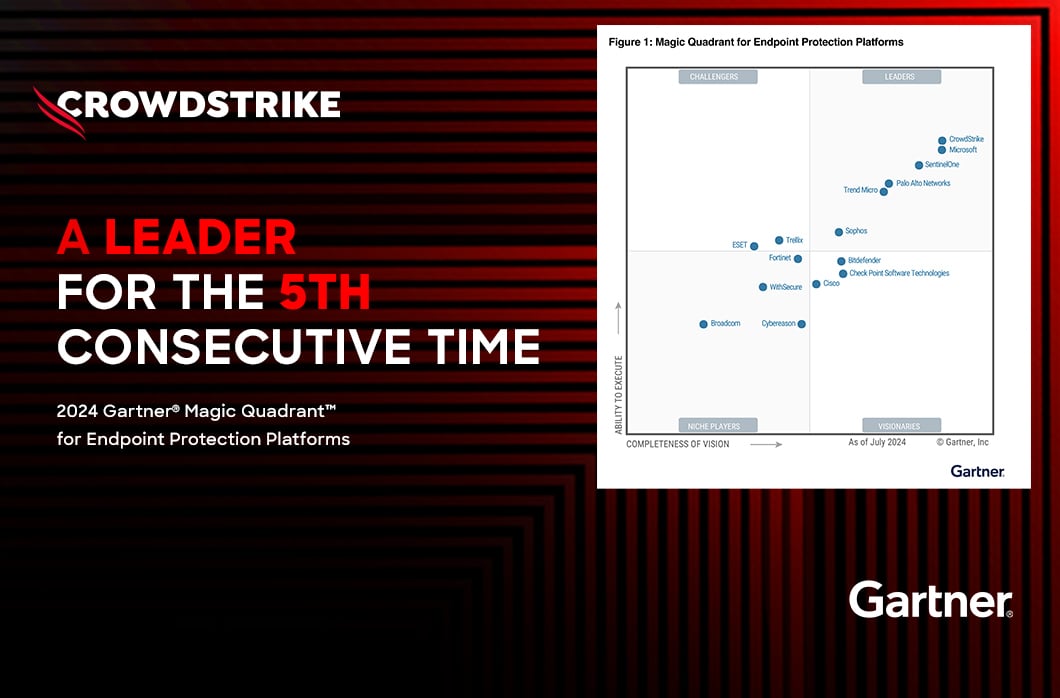
Protecting Users from Malicious Sites with Falcon for Mobile

Introduction
Today, mobile devices are ubiquitous within enterprise environments. But with their proliferation, it provides adversaries with yet another attack surface with which they can target users and cause a breach.
From phishing attacks to malicious apps, mobile users tend to let their guard down and potentially click on obfuscated links to malicious sites. Falcon for Mobile protects users by preventing connections to malicious sites on both iOS and Android devices. Some examples of sources for these malicious connections are texts, emails, apps, or even QR codes.
Falcon for mobile can block navigating to malicious sites and notifying the user why it was blocked, educating the user and reducing the risk in the future.
Security administrators can also view reports within the Falcon Console to identify individuals within the organization that may require additional phishing training.
Video
Protecting Mobile Users
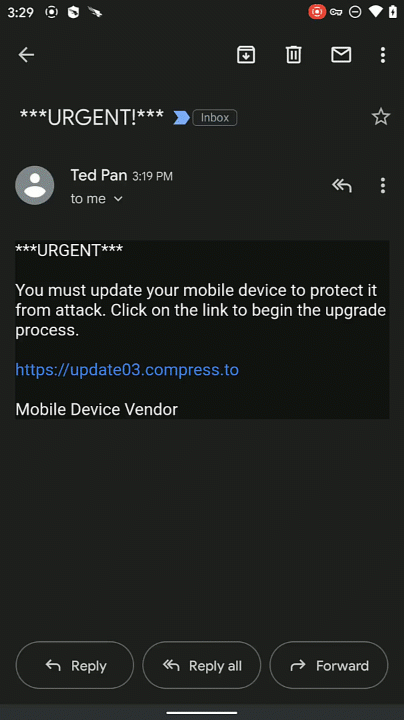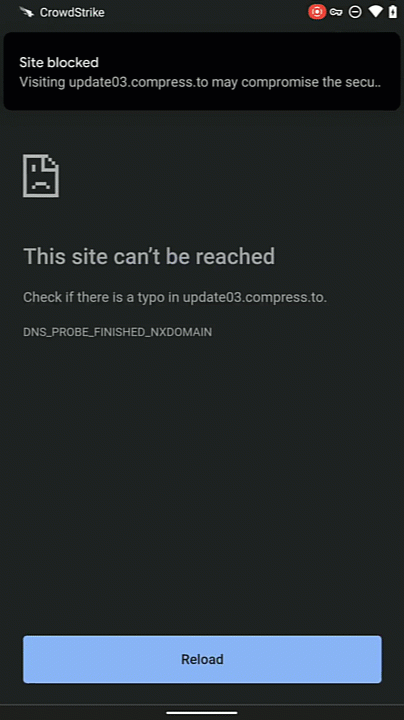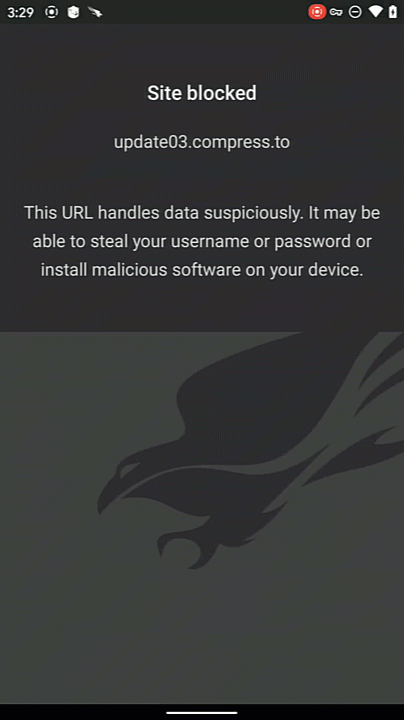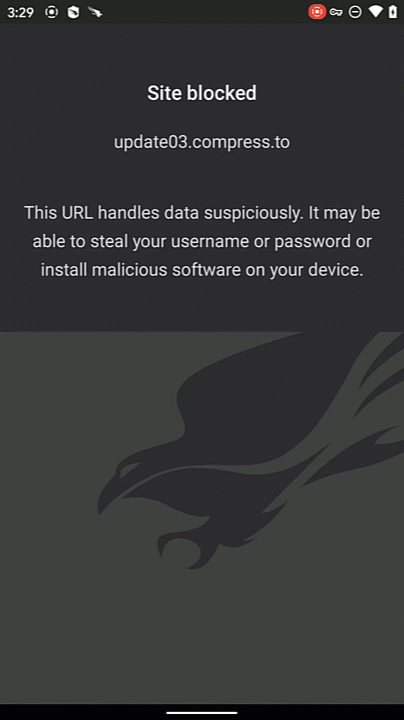
When the device attempts to connect to a phishing site, we see that it cannot be reached. The user is protected from the malicious site that could be attempting to harvest their credentials or install malicious software.
Falcon for Mobile also provides a notification as to why the site was blocked. The user can expand the notification to see additional details.
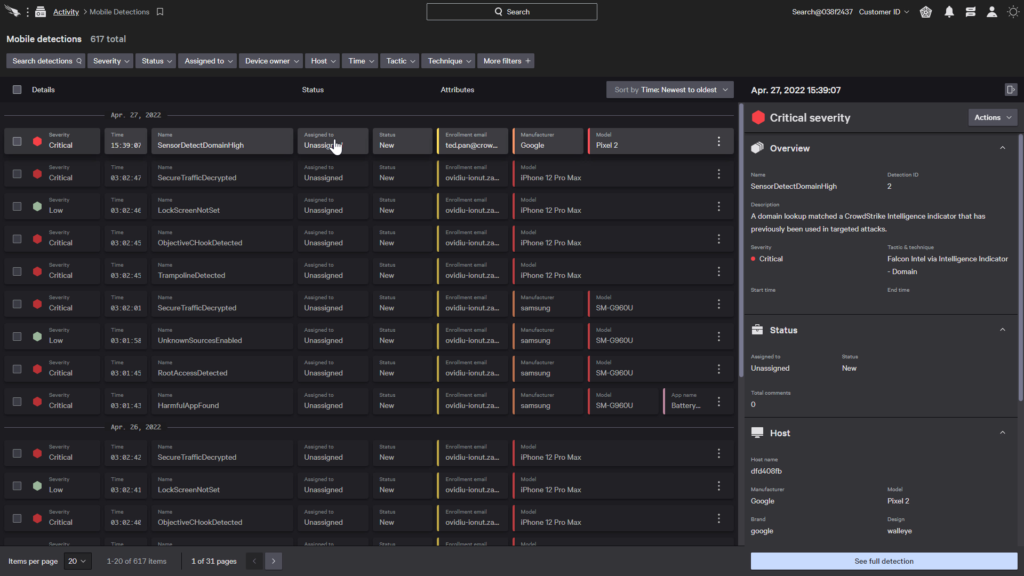
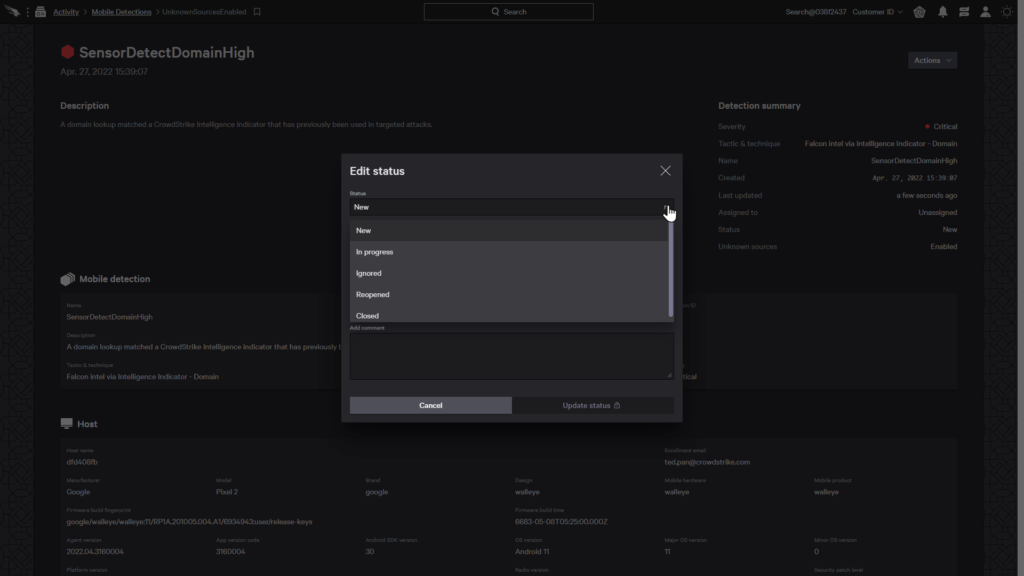
The mobile detection screen in the CrowdStrike Falcon Console is structured in a way that provides an easy way to view mobile threats identified within the environment.
Each line shows a high level overview of a detection, presenting information such as the threat name, mobile user, and device impacted.
An info pane on the right provides additional details about the threat, such as a description of the threat or additional host information.
The full details show related threat data such as the domain that was blocked as well as a timeline of activities related to this detection.
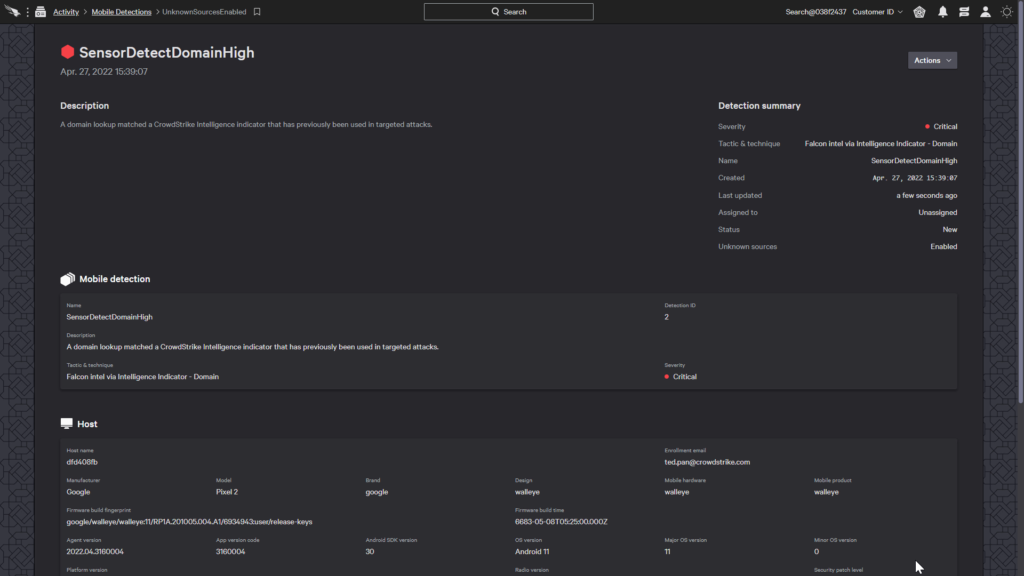
An analyst can adjust the case with options such as setting its status, assigning it to another analyst, adding a tag, or adding a comment.
After they’re done, the status will be updated and tracked to ensure resolution of the case.
Conclusion
So as we can see, Falcon for Mobile provides powerful protection that prevents users from unknowingly navigating to malicious sites and accidentally sharing data or credentials .
With phishing attacks being such a common vector for mobile attacks, blocking malicious network connections with Falcon for Mobile helps protect organizations from a breach.