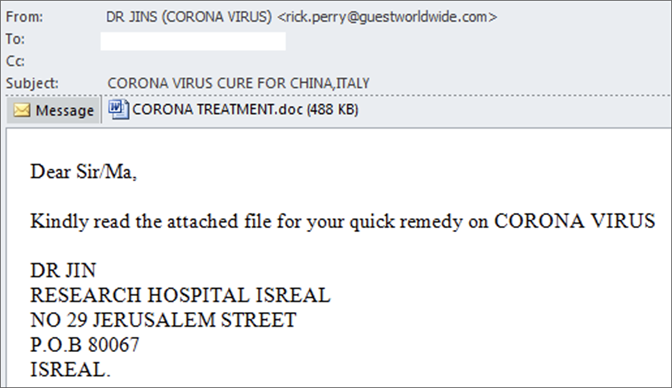
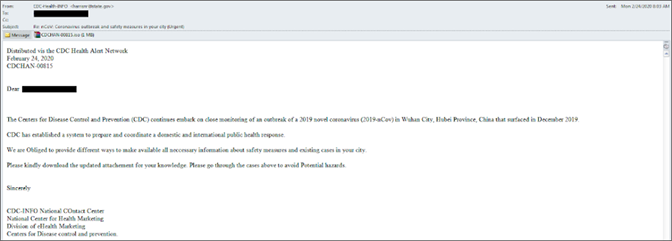
Spear phishing is a targeted attack on a specific person or organization, whereas general phishing campaigns are sent to a large volume of people.
What is Phishing?
Everyone with an inbox is familiar with phishing attacks. A modern phishing attack is likely to look like a legitimate email from a well-known business or a bank, and it will only be deemed malicious by an alert user who mouses over the sender address to see if it is correct before clicking a link or downloading an attachment.
Phishing attacks are a numbers game: Instead of targeting one individual, they target many people in the hope of catching a few.
Attacks are not personalized, and a key identifier of a phishing email is that it does not use the recipient’s name. Phishing attacks are conducted not only by email but also by text, phone and messaging apps.
What is Spear Phishing?
While phishing attacks target anyone who might click, spear phishing attacks try to fool people who work at particular businesses or in particular industries in order to gain access to the real target: the business itself.
Spear phishing attacks are at least as personalized as a typical corporate marketing campaign. For example, a spear phishing attack may initially target mid-level managers who work at financial companies in a specific geographical region and whose job title includes the word “finance.”
A great deal of research may occur before a spear phishing attack is launched, but the effort is worthwhile to an attacker because the payoff could be significant. That payoff isn’t necessarily monetary — spear phishing attacks are frequently sponsored by nation-states.
To execute a spear phishing attack, attackers may use a blend of email spoofing, dynamic URLs and drive-by downloads to bypass security controls. Advanced spear phishing attacks may exploit zero-day vulnerabilities in browsers, applications or plug-ins. The spear phishing attack may be an early stage in a multi-stage advanced persistent threat (APT) attack that will execute binary downloads, outbound malware communications and data exfiltration in future stages.
Expert Tip
One example of bait is an email that looks like a message from Human Resources asking the employee to log in to the HR portal to update password information. When the employee clicks on the link provided in the email, the resulting webpage looks like the HR portal but is actually a mock-up. When the employee attempts to log in to the fake page, their login credentials are captured by the criminals behind the attack. Those credentials will then be used by the attacker to access the network.
How to Protect Yourself From Both Phishing and Spear Phishing
Below are a few simple tips that can go a long way in protecting against phishing scams:
- Ensure that remote services, VPNs and multifactor authentication (MFA) solutions are fully patched, properly configured and integrated.
- Offer security awareness training to educate employees on the various types of phishing attacks.
- Conduct phishing simulations within your company so that employees can practice what they learned from security awareness training.
- Know how to validate URLs before clicking on links
- Use an anti-spam filter: Anti-spam filters use pre-defined blacklists created by expert security researchers to automatically move phishing emails to your junk folder, to protect against human error
- Use anti-virus software: Anti-malware tools scan devices to prevent, detect and remove malware that enter the system through phishing
- Use an up-to-date browser and software: Regardless of your system or browser, make sure you are always using the latest version.
- Never reply to spam: Responding to phishing emails lets cybercriminals know that your address is active.