At Fal.Con 2025, CrowdStrike introduced Threat AI, an agentic threat intelligence system of autonomous agents that reason across data, hunt for threats, and take action. As part of our vision for the agentic SOC, these AI-powered agents automate complex intelligence workflows so defenders can keep up with AI-powered adversaries while staying in control of every decision.
This vision takes a concrete step forward with the first two agents, both available to customers of CrowdStrike Falcon® Adversary Intelligence Premium. The Malware Analysis Agent automates a critical analyst workflow by turning malicious files into actionable intelligence and adaptive defenses, while the Hunt Agent translates CrowdStrike’s deep adversary knowledge into always-on, hypothesis-driven threat hunts with verified leads.
This blog focuses on the Malware Analysis Agent and how it revolutionizes malware investigations.
Malware Analysis in the MITRE ATT&CK Evaluation
The same core technologies that power the Malware Analysis Agent played a central role in CrowdStrike’s performance in the 2025 MITRE ATT&CK® Enterprise Evaluations, where CrowdStrike achieved 100% detection and 100% protection with zero false positives. These results, in the industry's most demanding and comprehensive cross-domain security assessment to date, reflect how the CrowdStrike Falcon® platform and CrowdStrike threat intelligence worked together to uncover and stop advanced adversary tradecraft.
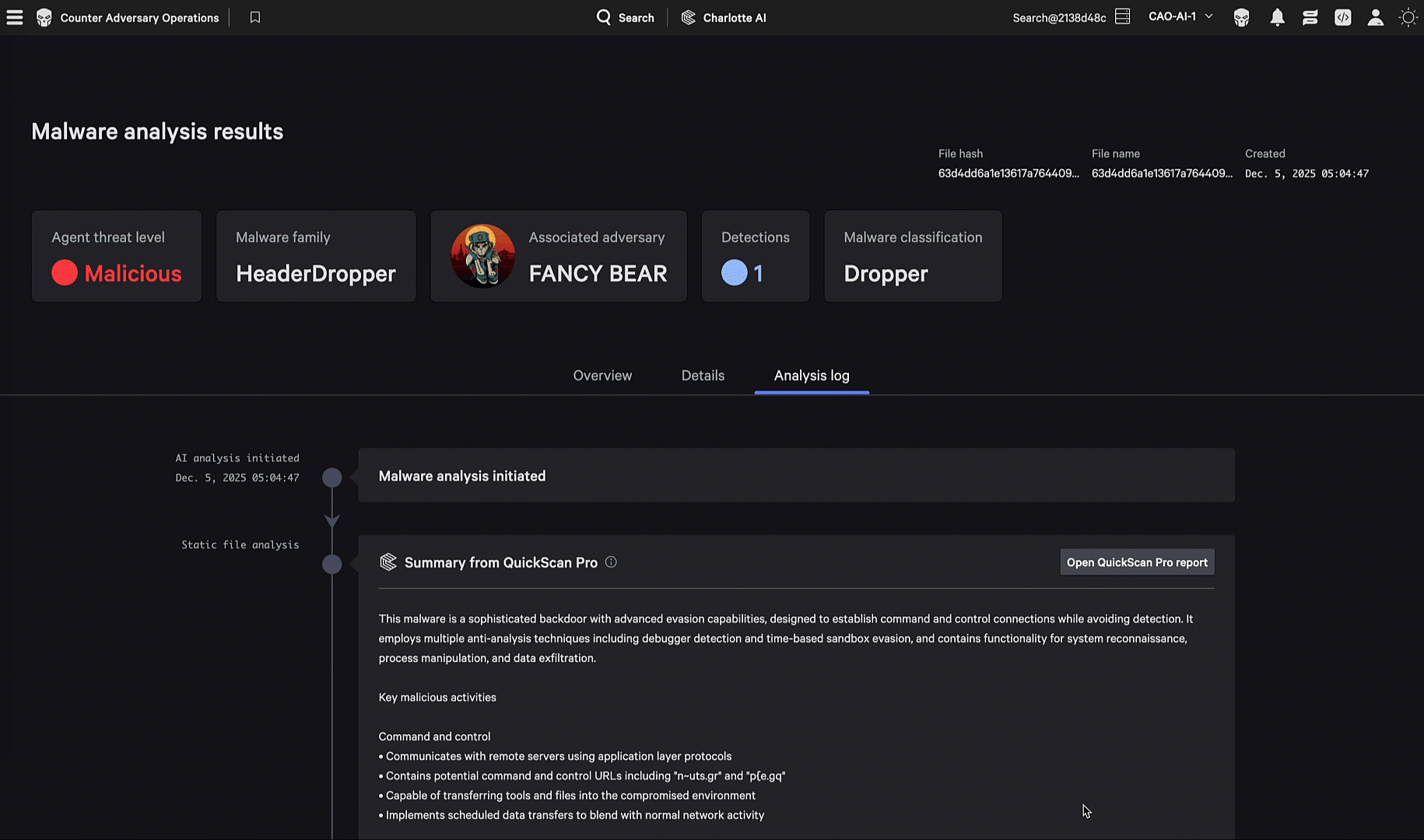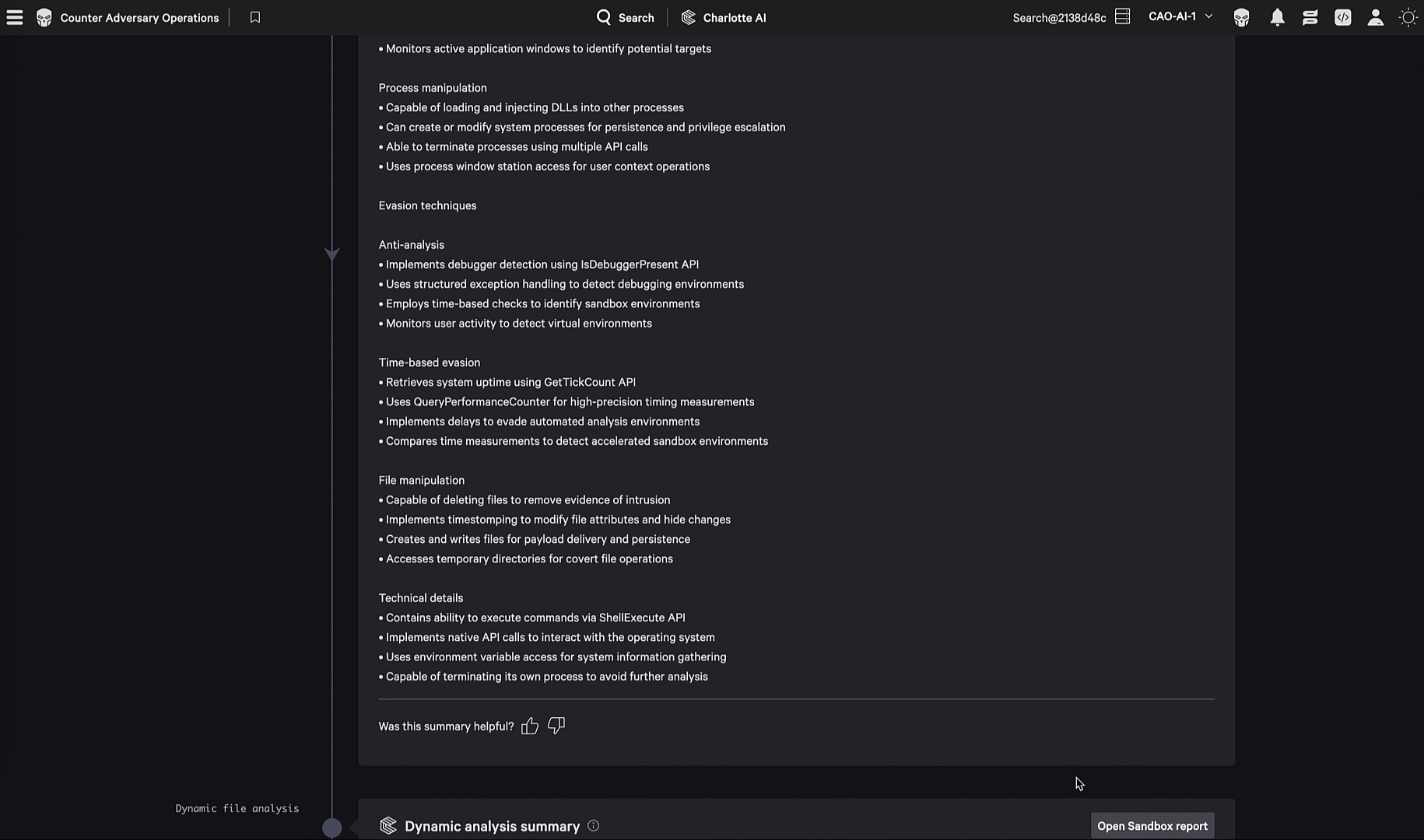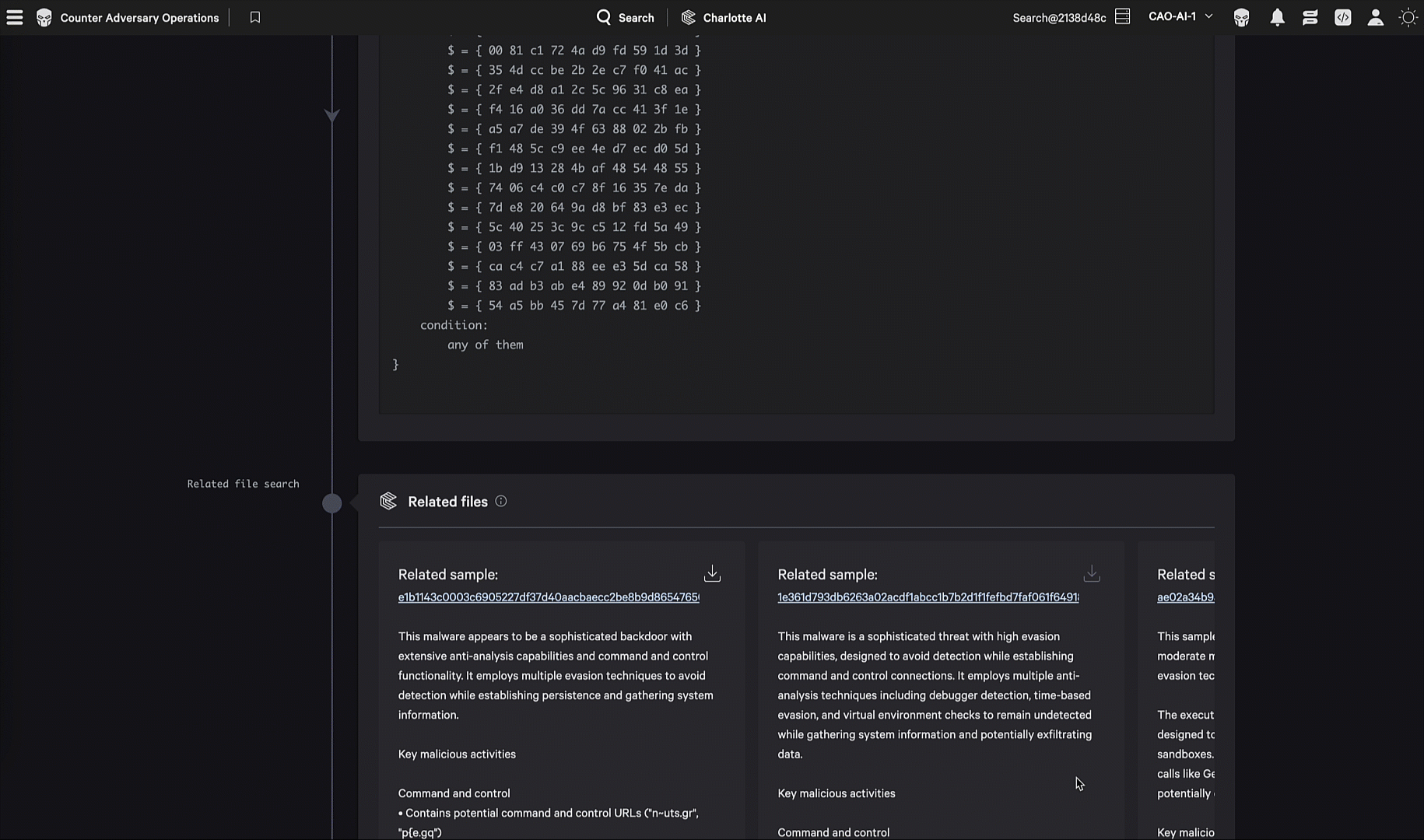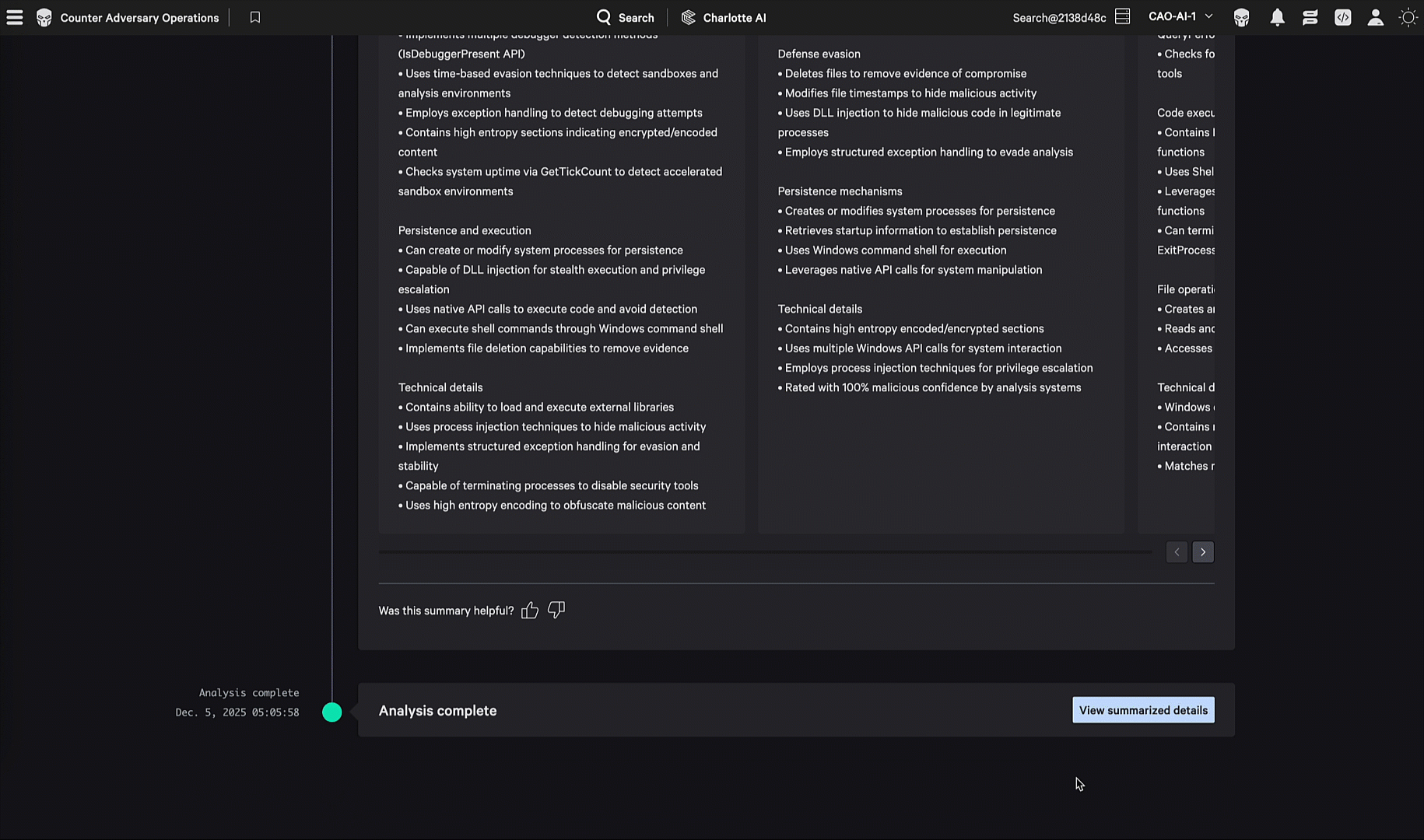
In one evaluation scenario, the adversary embedded encoded shellcode within their malware so it could evade security products, then reflectively loaded and executed that shellcode at runtime. CrowdStrike’s static and dynamic analysis capabilities quickly investigated files of interest and delivered precise intelligence that was automatically converted into detections and protections through CrowdStrike Falcon® Fusion SOAR, without analyst involvement. CrowdStrike Falcon® Adversary Intelligence’s integrated static analysis capabilities triages files, extracts configurations, identifies code relationships, and correlates samples to known malware families, while dynamic sandbox detonations provide rich behavioral intelligence by observing real execution.
Together, these capabilities transform suspicious files into actionable intelligence and detections within seconds, enabling rapid triage, adversary attribution, and automated defense aligned to adversary TTPs. The Malware Analysis Agent brings these capabilities together in a single agent, enabling defenders to detect malware at machine speed.
AI-Powered Malware Analysis at Speed and Scale
Traditional Malware Analysis Is Slow and Difficult
When a suspicious file appears, security analysts must answer critical questions: Is it malicious? What does it do? How do we stop it? Does it indicate a broader campaign or targeted activity? Getting these answers often takes hours of manual work, multiple tools, and expertise many organizations lack.
Typical file investigations start with a detection through endpoint detection and response (EDR), email attachment, or an incident response investigation. Most teams begin with a hash lookup using an IOC feed or access an open source malware repository to determine verdict and priority. If it is a unique sample, or only limited context is available, they may send it through a malware analysis sandbox and then to a reverse engineer, if they have one. The analyst would spend hours picking through decompiled code, searching derivative artifacts across databases and feeds, accessing memory dumps, attributing to a malware family or adversary, hunting for related samples, and building a remediation plan.
This isn’t scalable. Dynamic malware analysis alone takes about 15 minutes or more. Multiply that across hundreds of files from dozens of daily detections, and it’s at least a day of waiting on the analysis of artifacts that may not even be malicious. In this situation, scaling malware analysis across the detection stack to generate environment-specific intelligence is practically impossible, and many detection artifacts are never analyzed because of ingestion cost and time.
The Malware Analysis Agent Reduces SOC Time and Effort
The Malware Analysis Agent uses AI to orchestrate CrowdStrike's malware analysis tools, which embed finished intelligence to help detect and understand novel threats and respond within minutes.
Analysts have three options for providing data to the Malware Analysis Agent:
- Manually load files into the agent within the Falcon platform
- Programmatically integrate the agent with third-party detection tools and different EDR-centric workflows with Falcon Fusion SOAR or via API
- Configure prevention policies to automatically upload suspicious files from sensors to the cloud for analysis
Every step of the agent’s analysis is logged so analysts have full transparency into what was done and why.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)