Which Way Did She Go? Speeding Up Lateral Movement Investigations

One of the biggest challenges facing security investigators is creating a full picture of a threat, piecing together disparate pieces of information that may occur across a range of time and hosts. At CrowdStrike, we’re excited to deliver new lateral movement visibility, continuing our efforts to lighten the load on investigators and shrink the time to understand and respond to emerging threats.
While attacks may begin with the compromise of a single host, it’s rare that adversaries conducting the most harmful campaigns limit themselves to that initial compromise. We observe lateral movement attempts in nearly all attacks from sophisticated adversaries. Attackers begin on the initial foothold host, often of comparatively low value, and move to additional hosts in the network attempting to extend reach and locate higher-value targets. While there’s some impact from the compromise of any host, organizations can often withstand a contained compromise of a single low-value target. It’s the subsequent broader and higher-value compromises that are frequently the most critical.
As defenders, we face the challenging task of determining if and how the attacker moved laterally to other hosts. We must infer links between activity on seemingly disjointed hosts. Further, we must do this amid a substantial backdrop of system and network activity. It’s common for an enterprise to perform millions of benign operations on remote hosts per day that resemble malicious movement. As we’re currently battling adversaries that break out within hours or even minutes, any additional time it takes us to make connections between hosts and filter through benign noise can result in a significantly expanded attack scope and impact.
A Synchronized View of Lateral Movement
It’s an ongoing mission of ours to improve the information available to help quickly identify and understand how an attacker is attempting to spread across a network. Our latest work in this area has enabled us to infer connections between hosts, alert on particularly suspicious cases and provide additional context about the lateral movement.
It’s challenging to derive meaningful context about activities involving multiple hosts by exclusively taking an individual host-level or network-level approach. At an individual host level, we may know there was suspicious process activity but do not know how it relates to other hosts. At a network level, we may have a better understanding of relationships but lack detailed information for discerning suspicious process or system activity. The CrowdStrike Falcon®® detection engine instead takes input from and correlates across these levels. We analyze host activity observed by one CrowdStrike Falcon® agent alongside the relationships and activities of other hosts on the network as tracked in our distributed graph database, CrowdStrike Threat Graph®.
When suspicious activity has been observed on one host, we increase our attention on that host as well as on the interactions it has with other hosts on the network. In order to locate suspicious hosts, we leverage CrowdScore™. CrowdScore implicates a host in an incident based on an aggregation of behavior observed on a host. Incidents are scored and prioritized according to likelihood of maliciousness. Highlighting the lateral movement on hosts experiencing incidents helps investigators sift through benign environmental noise from ongoing remote activity, and focus their attention on those movements that are more likely to be malicious.
Movement in the Context of Incidents
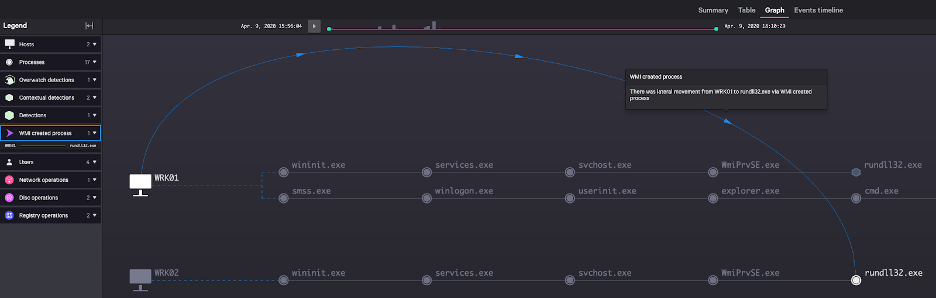
Figure 1: Lateral movement from host WRK01 to WRK02 using WMI process creation
Consider a technique regularly seen in the wild from nation-state actors, propagating ransomware, and attack frameworks. Having compromised an initial host, dumped credentials, and performed reconnaissance, the attacker seeks to move to other hosts in the network. The attacker creates a process on a remote host using Windows Management Instrumentation (WMI), functionality built into Windows and commonly used by attackers for lateral movement. For example, the NotPetya ransomware has been known to use derivations of the following WMI command:
wmic.exe /node:<target> /user:<username> /password:<password> process call create C:\Windows\System32\rundll32.exe C:\ProgramData\perfc.dat\<NotPetya args>
This command launches rundll32.exe and executes a malicious DLL named perfc.dat on a target host. Figure 1 shows this remote execution from source host WRK01 to target host WRK02. Falcon’s detection engine correlates the process creation observed on WRK02 with the credential dumping, reconnaissance and WMI behaviors observed in the incident on WRK01. The lateral movement is highlighted in the incident and graphically depicted by the edge from WRK01 to rundll32.exe on WRK02. When replaying the attack, the incident workbench will display this lateral movement in temporal relation to other process activity occurring on the impacted hosts.
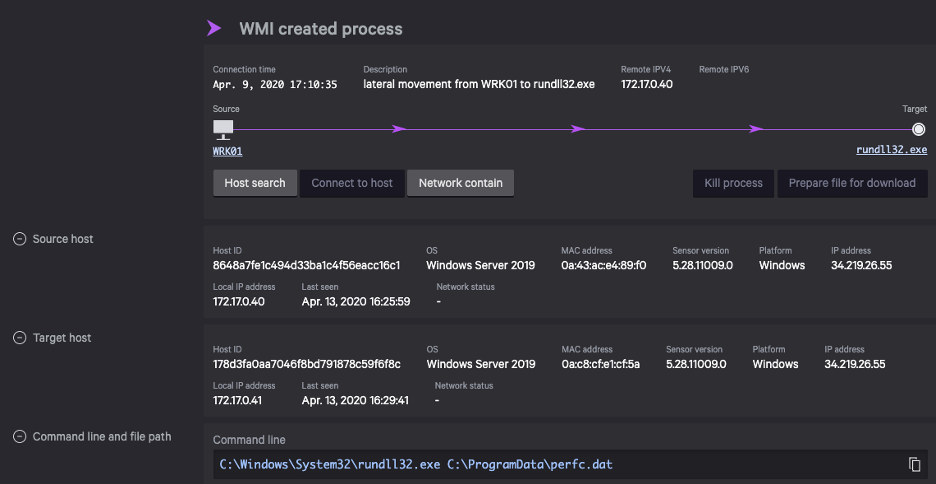
Figure 2: Lateral movement details for rundll32.exe remote execution
The details pane for the lateral movement edge (Figure 2) contains more information about the remote execution. The initially compromised source host and the target of the movement are shown along with information about those hosts such as their IP addresses. We can also see the command line used to launch rundll32.exe and load perfc.dat.
In addition to visually alerting on suspicious movements in incidents, we’ve added a button to allow you to quickly drill down for deeper investigation. A new “Lateral movement event search” button (Figure 3) takes you to the “Investigate” window where you can explore the full event details and broader set of lateral movement events originating from the source host of the incident.
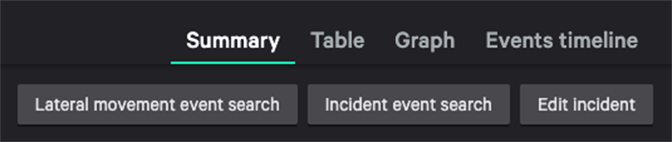
Figure 3: Lateral movement event search button reveals full set of events and event details
Available in CrowdScore Incident Workbench
These enhancements are immediately available for all Falcon platform customers. They will appear on incidents when relevant and can be filtered by the Lateral Movement Tag. Also be on the lookout for future additions as we continue to develop capabilities to speed up lateral movement investigation both at the aggregate level that we highlight in incidents as well as the details that we provide in event data.
Additional Resources
- Learn more about CrowdScore by watching an on-demand webinar, “CrowdScore: Get in the Driver’s Seat.”
- Read a blog on how CrowdScore alleviates alert fatigue: “Noise is the Problem — CrowdScore is the Solution.”
- Learn more about the CrowdStrike Falcon® platform by visiting the product webpage.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and learn how true next-gen AV performs against today’s most sophisticated threats.


