It is Time to Replace Your Existing AV
Introduction
This document will cover the simple steps of replacing your traditional antivirus (AV) vendor with CrowdStrike.
Video
Step-by-step
Falcon’s versatility as an AV, EDR or Intelligence product makes it a perfect solution to install with other security technologies. For example, if you have an existing AV solution in place and would like to add Falcon Insight or Falcon Intel, it can easily be installed to provided those important layers.
However, it is not recommended to install CrowdStrike Falcon in prevention or blocking mode simultaneous with other AV solutions also in blocking mode.
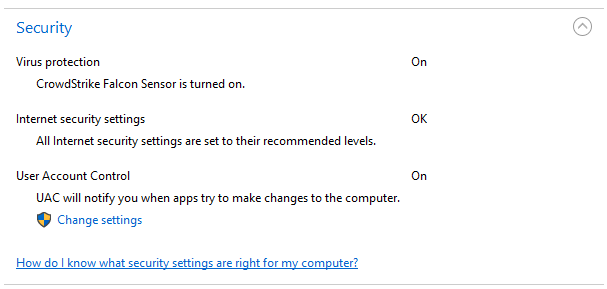
If you are adding a Falcon solution to your existing security product it is recommended that you install Falcon in DETECT ONLY policy (default policy). For more information on policies see the article on the tech center here regarding policy configuration. Below is an example of a policy with preventions disabled. This policy can safely be installed alongside another AV solutions. However reliance on traditional AV solutions should be temporary. Next we’ll illustrate the removal of the old solution and implementing a blocking policy in Flacon.
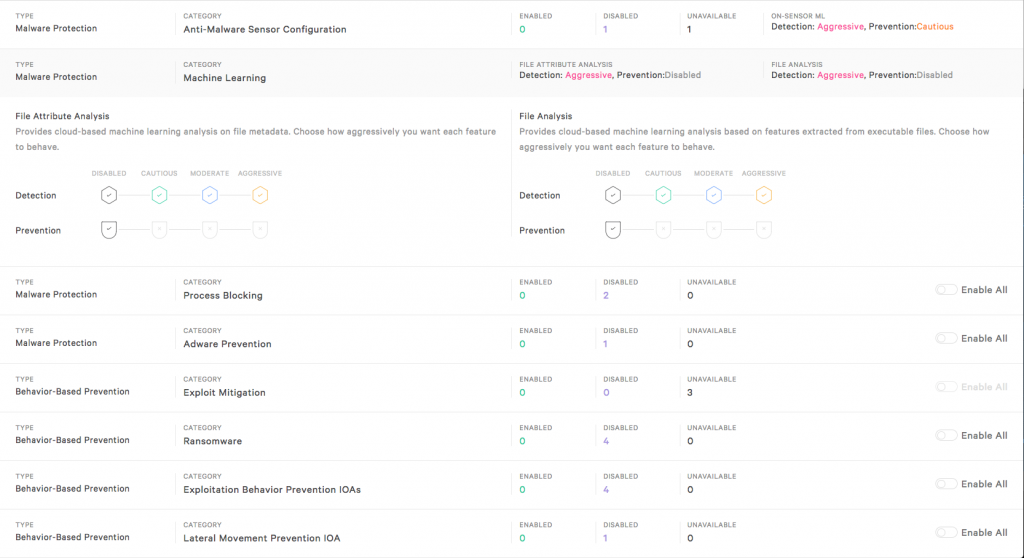
Sample policy in detect mode only
For an organization wide removal, Group Policy, SCCM, or other utilities will be used to remove the old application from the production environment. To remove other AV vendors from an individual host, utilize the “Add/Remove Programs” feature in the Windows Control Panel and uninstall the application.
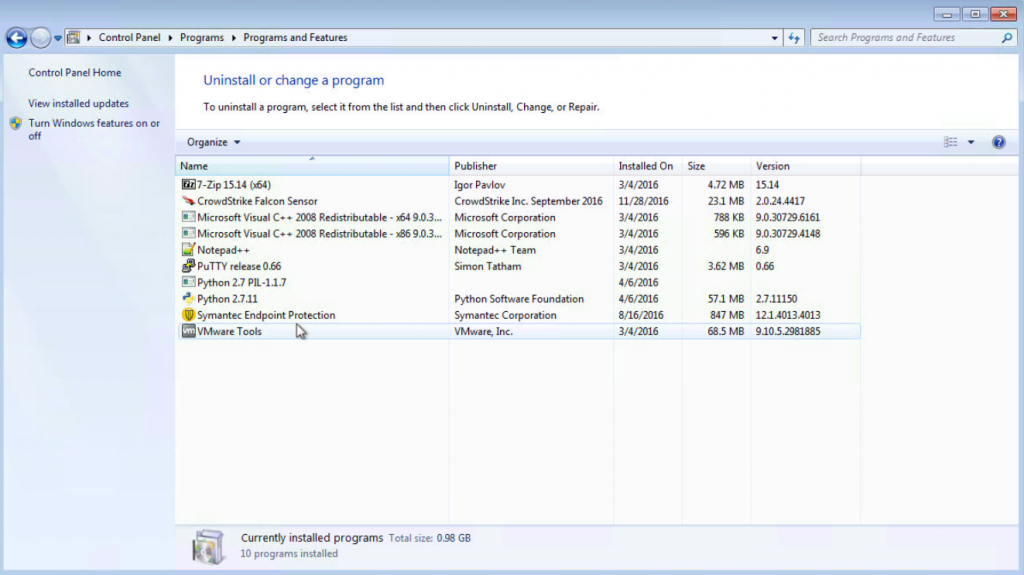
Removing traditional antivirus
Select the previous AV vendor and then select the “uninstall” option that appears above the list of installed programs. Different vendors may have additional steps or multiple applications that will need to be removed.
Note: In the case of McAfee, uninstall the McAfee Agent last, removing all the other installed programs first. This order seems to be the most effective in our experience (Some vendors may require a reboot).
After a reboot, if necessary, verify that the uninstall was successful in the Action Center. Open the Action Center and navigate to the Control Panel -> System and Security -> Action Center.
Under “Virus Protection” and “Spyware and Unwanted Software protection” CrowdStrike should be the only listed vendor.
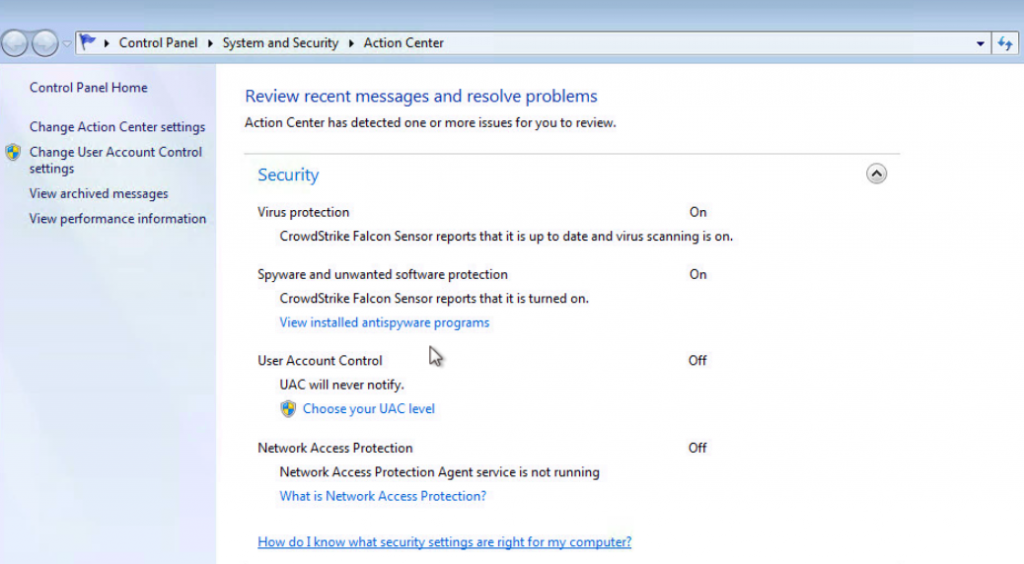
Actions Center with CrowdStrike as Security Vendor
Next change the policy in Falcon from a detection policy to prevention and detection. Doing this should be done after testing on a subset of systems in your organization to ensure the desired levels of information are received in the Falcon console.
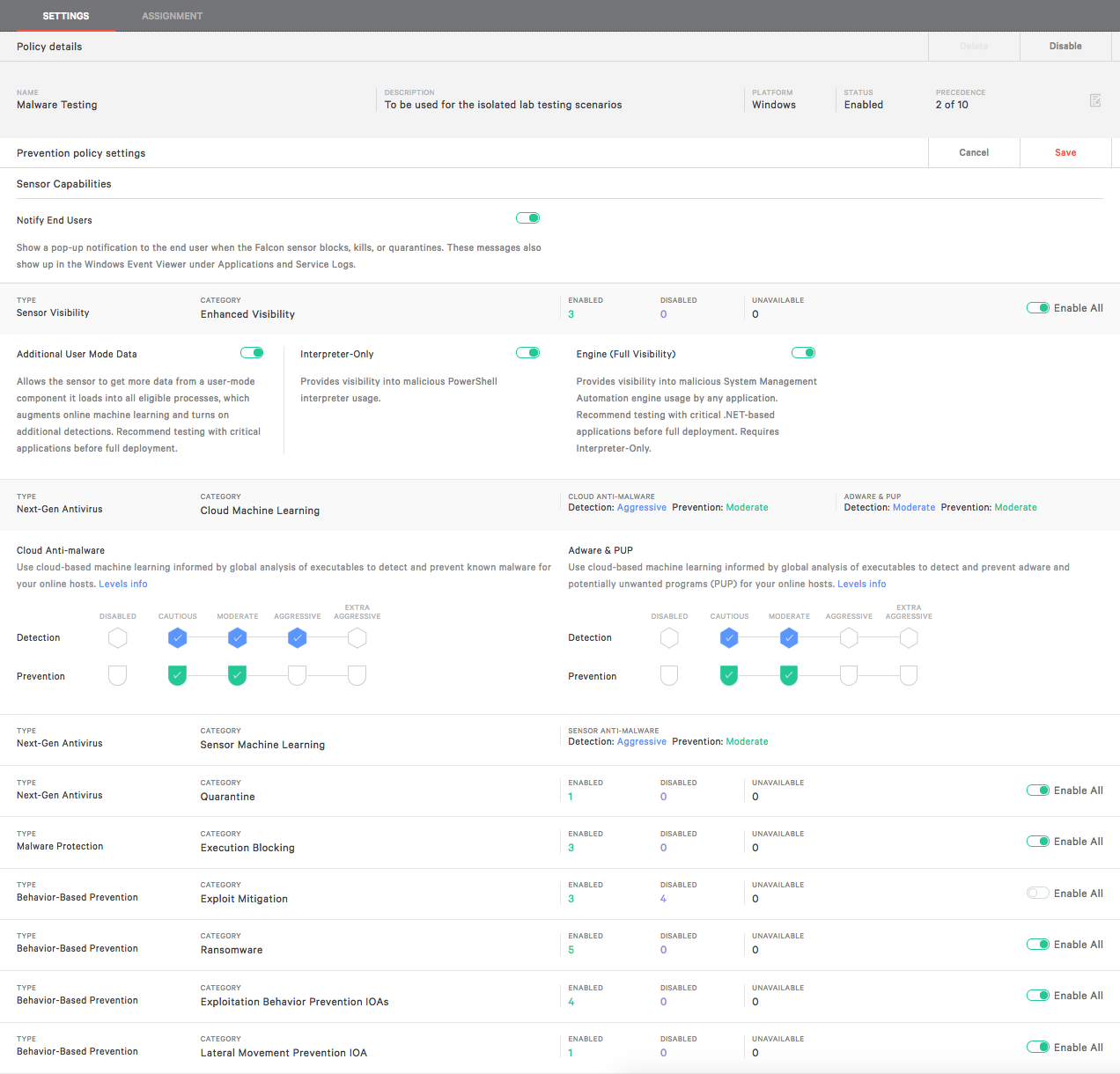
Verify that the policy changes apply to the group of systems intended by clicking on the “current members” tab at the top of the policy configuration page.
Before leaving any page, make sure the changes are saved and that the policy has been enabled. While policy changes are in effect relatively quickly, moving machines from one policy to a new or different policy may take more time.
Conclusion
You should now have a good idea of how to run in parallel or replace your existing endpoint security product with CrowdStrike’s Falcon Prevent and Falcon Insight.
More resources