Automatically discover Azure workloads
Unlock detailed insights into your Azure environment to secure virtual machines, mitigate risks, and minimize your attack surface.
CrowdStrike Falcon® Cloud Security
Focus on your business. We’ll handle the security.
The security, visibility, and control you demand — without the complexity.
Get unparalleled insights into your Azure virtual machines, identify unprotected resources, and reduce your attack surface by automatically discovering virtual machine deployments — no agent required.
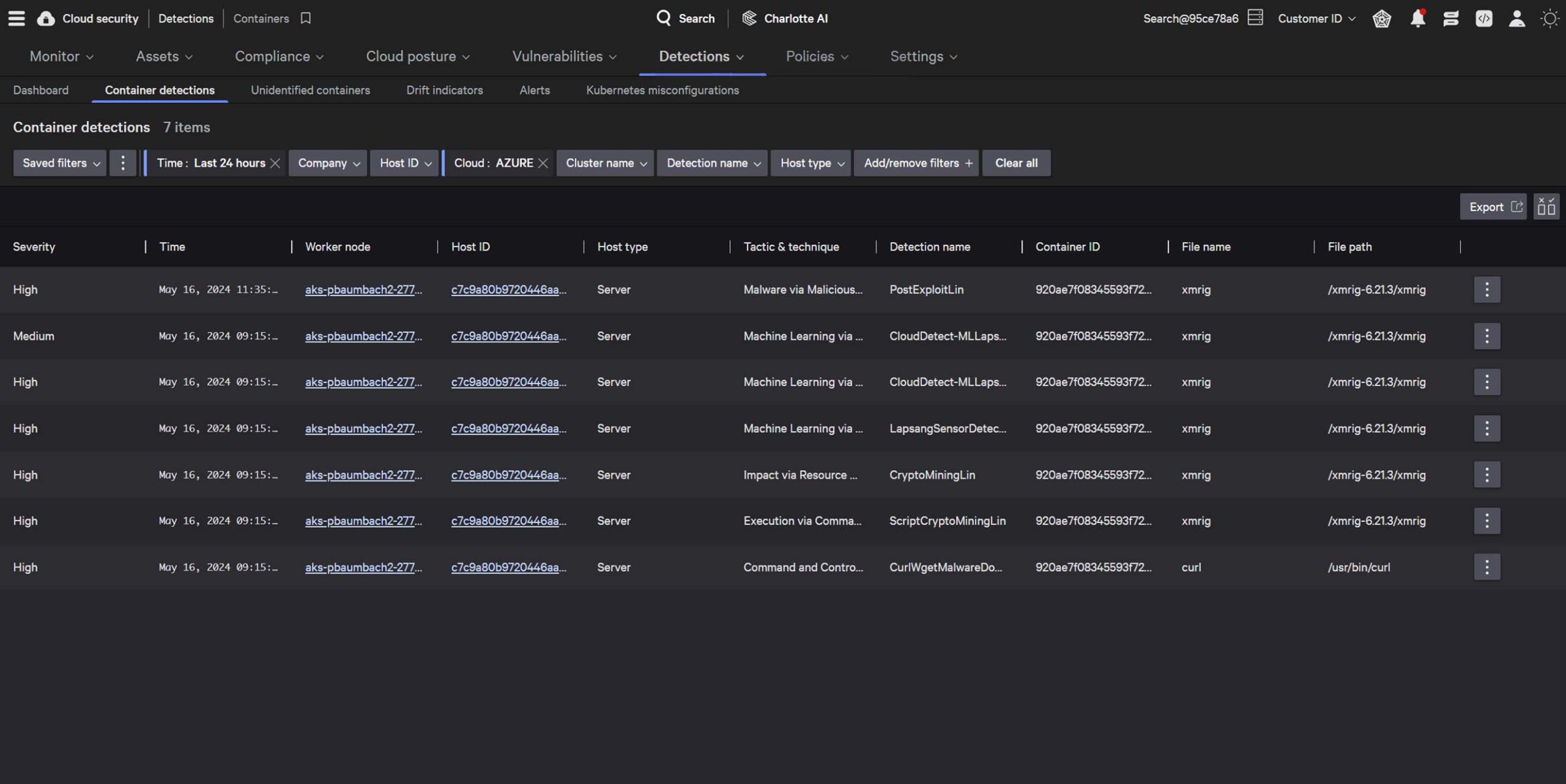
Access exhaustive metadata and continuous monitoring for visibility into all Azure workload activities, including those within containers, enabling proactive threat hunting and investigation across environments.


Secure your Azure containers and hosts with a single agent. Our platform offers runtime protection and granular visibility into container activities, supporting a variety of technologies and deployments.
CrowdStrike Falcon® for Azure combines cutting-edge technology to protect workloads at their most vulnerable, integrating custom IOAs and threat intelligence for dynamic threat prevention and detailed attack context.

Built for the cloud, the CrowdStrike Falcon® platform enhances Azure security with minimal operational impact, powerful API integrations, and flexible subscription models, facilitating efficient security and agile business operations.


Discover how CrowdStrike’s advanced protection can secure your cloud environment. No strings, no hassle.
Start interactive demo