It is therefore more important than ever for the healthcare industry to harden its defenses to prevent access to critical systems.
COVID-19 — A Breeding Ground for Cybercrime
COVID-19 has contributed to an increasingly dynamic cyber threat landscape, as covered in a recent CrowdStrike Intelligence blog. A factor in this has been the rapid uptake of remote working. Shodan, known as the world's first search engine for internet-connected devices, has charted a spike in internet-exposed Remote Desktop Protocol (RDP) over the past month. The SANS Internet Storm Center has also reported a concurrent spike in RDP scanning, indicating that adversaries are alert to opportunities to exploit easy attack vectors. It is clear that many businesses, in their haste to resume operations, have increased their exposure to an equally significant business disruption in the form of ransomware.The destructive and disruptive capacity of adversaries targeting the industry is immense. OverWatch routinely sees adversaries employing tactics to expand their reach or maximize their impact within victim environments. This blog shares a firsthand account of the tactics, techniques and procedures (TTPs) currently seen in the wild targeting healthcare organizations. These insights are derived from OverWatch managed threat hunting operations empowered by the CrowdStrike Falcon® platform.
Emerging Themes Across Actors Targeting Healthcare
OverWatch has uncovered a number of attacks targeting the healthcare industry involving TTPs indicative of criminal activity. While OverWatch has seen adiverse range of suspected criminal adversaries targeting the healthcare industry, it has also observed two distinct trends that defenders should be alert to. The first is gaining initial access through brute forcing as well as the exploitation of internet-exposed services and public-facing applications to gain initial access — common techniques that continue to prove effective. The second trend is the effort that adversaries are putting into preparing their victims’ environment for maximum impact.
Healthcare Falling Victim to Preventable Access Techniques
OverWatch regularly sees the use of valid credentials as an initial access vector. Currently, the most frequently used collection method is password-spraying brute-force attacks against internet-facing services such as Server Message Block (SMB) and RDP. Compared to traditional brute-force attacks, password spraying can reduce the frequency of account lockouts and can therefore be more difficult to detect. It is common for this technique to successfully expose user credentials, including administrator accounts. Gaining access through unpatched public-facing servers has proven to be another popular method observed in recent intrusions targeting healthcare organizations. Adversaries are exploiting services with known vulnerabilities like IIS and SharePoint to access healthcare networks, demonstrating that tried-and-true methods remain effective in the wild today.In this period of heightened attention on the healthcare industry, it is crucial to maintain basic security hygiene. OverWatch encourages defenders to consider the following measures to harden their security tooling and maximize visibility across their networks:
- Fortify network access, particularly remote access. It is essential that network defenders enforce strong password policies and require two-factor authentication (2FA).
- Protect public-facing servers by ensuring that security patches are applied regularly. Logging and analyzing authentication to public servers would also be beneficial in helping identify unusual access attempts.
Case Study: OverWatch Thwarts “Rotten” Attack on Healthcare Industry
Exploitation of an IIS server was the initial vector in a healthcare intrusion that OverWatch threat hunters recently uncovered and thwarted. This particular intrusion exemplifies many of the pervasive threats facing the healthcare industry since the outbreak of COVID-19.
During routine continuous threat hunting across customer environments, OverWatch identified an active adversary presence. The adversary had launched their attack in the middle of the night (in the victim’s local time), expecting minimal security coverage. But those plans were derailed when OverWatch effectively identified the activity just one minute after the threat actor began interacting with the exploited server.
Hunting for abnormal PowerShell behavior can often pay dividends for threat hunters, and it proved pivotal in detecting this incident. Under the exploited IIS Worker Process (w3wp.exe), the adversary had executed a suspicious PowerShell command that created a .NET TCP object and used this to request data from a remote host. OverWatch has observed actors use this particular PowerShell technique to facilitate network communications to command-and-control (C2) servers. Subsequent analysis confirmed that in this instance, it was again the case.
Generally, seeing a lone PowerShell command would be a weak indicator of attack. But OverWatch threat hunting views all activity in the context of time-sensitive surrounding events. Indeed, starting within a minute of this initial indicator, OverWatch noted that Falcon endpoint telemetry recorded a wide range of discovery commands being executed on the same server. In combination, this burst of activity exposed the hands-on operator’s presence. Over a seven-minute period, the adversary performed the following reconnaissance:net1 time /domnet1 group "domain computers" /domnltest.exe /domain_trustssysteminfonet1 group "domain admins" /domnet.exe group "" /dom
Twelve minutes after initially landing on the server, the adversary wrote a binary named 1582790468.382706.exe (SHA256 df4d70d0bc19f0e26ff85145d4e9b55666ac746b7bc5006bb11085a2929e710a) to the temp directory and executed it. This turned out to be a variant of the Rotten Potato privilege escalation tool. After failing to execute properly, the actor ran the following commands to troubleshoot:whoami"C:\windows\temp\1582790468.382706.exe" --help"C:\windows\temp\1582790468.382706.exe" -z -l 1111 -encodedCommand
By this point, OverWatch threat hunting notifications and insights had enabled the victim healthcare organization to rapidly respond. Responders were able to network contain the machine before the adversary could achieve any further actions on the target server or break out from the beachhead."C:\WINDOWS\system32\whoami.exe"
Adversary Preparations for Maximum Impact
Once they achieve initial access, adversaries are often employing measures to prepare their victims’ environment for ransomware deployment to achieve disruption. As evidenced by the intrusion case study above, adversaries use various techniques to establish persistence, escalate privileges, and perform host and network discovery. Adversary activities that OverWatch has observed being used successfully against the healthcare industry in the first quarter of 2020 include many common yet perpetually effective techniques. For example:
- Using
“living-off-the-land” (LOTL) capabilities like PowerShell and BITSAdmin to evade detection while retrieving malicious-purpose tools from external resources. - Using credential harvesting tools to extend the potential reach of the attack. Commonly seen tools in recent credential-harvesting attempts against healthcare organizations include PowerKatz, LaZagne, and the classic Mimikatz, as well as the Csvde command-line tool to export Active Directory data.
- Employing defense-evasion techniques like indicator removal from target hosts — for example, through clearing logs with the native Microsoft wevtutil tool.
- Establishing persistence by deploying web shells and PowerShell reverse shells.
- Escalating privileges using tools like Rotten Potato.
- Making efforts to identify security software possibly running on target hosts.
Tying It All Together
All techniques that OverWatch has observed in targeted eCrime intrusions against the healthcare sector since the beginning of January 2020 are noted in the following MITRE ATT&CK® chart. While OverWatch assesses that there are various distinct adversaries responsible for the attacks against the healthcare sector, their post-exploitation activity has recently coalesced around these behaviors.Threat hunters and security analysts protecting networks associated with healthcare providers should prioritize detection and response capabilities against these techniques currently being seen in the wild.
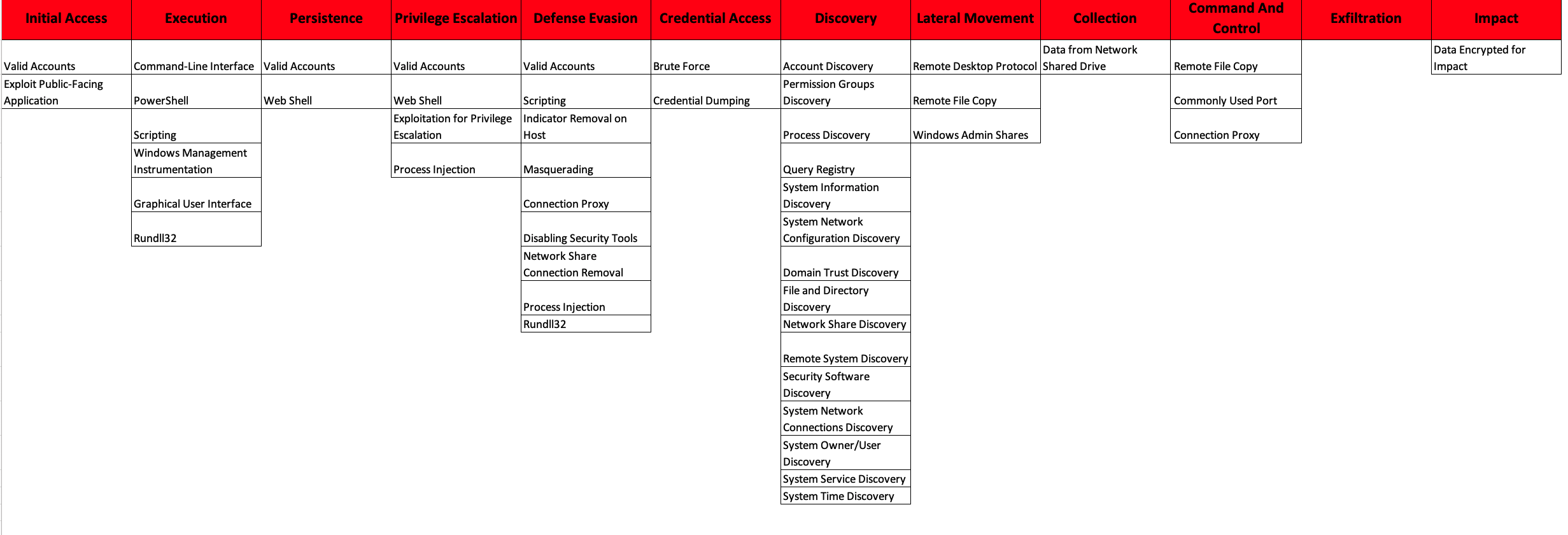 This MITRE ATT&CK chart reveals a lot about the nefarious motivations of the adversaries that OverWatch is encountering targeting the healthcare industry. (Click on chart to enlarge it.)
This MITRE ATT&CK chart reveals a lot about the nefarious motivations of the adversaries that OverWatch is encountering targeting the healthcare industry. (Click on chart to enlarge it.)Security Recommendations
As the healthcare industry remains on high alert, its network defenders should ensure that all of their workloads are covered by proper endpoint security and that they have an active monitoring and detection program enabled by continuous proactive threat hunting.
Ransomware Attacks
Adversaries do not appear to be prioritizing stealthy footholds with the intention of exfiltrating sensitive patient records or proprietary data over a long period of time. Rather, the focus often is rapid operations to gain access, escalate privileges and inflict damage (potentially in the form of ransomware).
Recommendations
- Turn it on and push it out! Fully leverage the protection you have. Fortunately for the presumptive victims in the cases outlined above, the Falcon OverWatch threat hunting team and CrowdStrike Falcon® platform preventions provided the essential early warning and protections to quickly identify the adversaries, limit any potential damage and prevent a catastrophic shutdown of the network.
- Watch for suspicious behaviors in order to strengthen detection and prevention over the long haul. The specific ransomware you encounter changes every day; the underlying behaviors do not. Modern endpoint detection and response (EDR) solutions allow you to monitor processes to detect suspicious actions, such as unusual discovery commands executed under server parent processes. File monitoring is also helpful in detecting changes to files in server directories where adversaries may attempt to install web shells.
Credential Theft
As stated above, OverWatch is regularly seeing the use of valid credentials as the initial access vector.Recommendations
- Protect identities. As a baseline, 2FA should be established for all users because today’s attackers have proven to be adept at accessing and using valid credentials, quickly leading to deeper compromise. Properly deployed, 2FA makes it much more difficult for adversaries to leverage privileged access to achieve their objectives.
- Ensure robust privilege access management. It’s important to note that 2FA is not a panacea, and implementing it does not immediately solve the problem of protecting identities. In addition to 2FA, a robust privilege access management process will limit the damage adversaries can do if they get in, and reduce the likelihood of lateral movement.
Social Engineering Schemes
Due to the widespread use of COVID-19-themed phishing lures and scams and an increasing number of remote workers, employees in all industries should remain vigilant and take advantage of the resources available to enhance their security postures in the context of this new threat landscape.Recommendation
- Enlist your users in the fight. While technology is clearly critical in the fight to detect and stop intrusions, the end user remains a critical link in the chain to stop breaches. User awareness programs should be initiated to combat the continued threat of phishing and related social engineering techniques.
Rapid Incident Response Is Key
The activities described in this blog reinforce the importance of a defensive cybersecurity posture. OverWatch has repeatedly seen how a properly configured CrowdStrike Falcon® platform can block adversaries attempting to perform targeted ransomware intrusions. Further, when coupled with human-driven continuous threat hunting, intrusions leveraging LOTL techniques can be identified and derailed long before adversaries can establish a foothold in the environment.Recommendations
- Accept the 1-10-60 challenge. Combating sophisticated adversaries requires a mature process that can prevent, detect and respond to threats with speed and agility. CrowdStrike urges organizations to pursue the “1-10-60 rule” in order to effectively combat sophisticated cyberthreats:
- Detect intrusions in under one minute.
- Investigate and understand threats in under 10 minutes.
- Contain and eliminate the adversary from the environment in under 60 minutes.
Organizations that meet this 1-10-60 benchmark are much more likely to eradicate the adversary before the attack spreads from its initial entry point, minimizing impact and further escalation. Meeting this challenge requires investment in deep visibility, as well as automated analysis and remediation tools across the enterprise, reducing friction and enabling responders to understand threats and take fast, decisive action.
- Look for partners to help fill the talent gap. Operating at 1-10-60 velocity takes more than technology. Defending against sophisticated threats ultimately requires mature processes and effective, dedicated security professionals. Not every organization is equipped to engage in this sort of battle 24/7. Successful enterprises often look outward for help, partnering with best-in-class external solution providers to help fill critical talent gaps in a cost-effective manner.
Additional Resources
- Read a blog on COVID-19 cybersecurity from CrowdStrike CEO George Kurtz.
- Learn more about the cybersecurity challenges during COVID-19 and recommendations for securing your remote workforce in blogs by CrowdStrike CTO Mike Sentonas and Chief Product and Engineering Officer Amol Kulkarni.
- Access resources to help you ensure the security of your organization and remote workers by visiting the CrowdStrike COVID-19 resource hub.
- Watch an on-demand webcast featuring CrowdStrike Intelligence and endpoint security experts: “Cybersecurity in the Time of COVID-19.”
- Download the CrowdStrike 2020 Global Threat Report.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)









































