How to Sniff Out (and Block) BloodHound Attacks

The growing adversary focus on “big game hunting” (BGH) in ransomware attacks — targeting organizations and data that offer a higher potential payout — has sparked a surge in the use of BloodHound, a popular internal Active Directory tool.
BloodHound expedites network reconnaissance, a critical step for moving laterally and gaining privileged access to key assets. In 2019, the CrowdStrike® Services team observed a dramatic increase in BloodHound use by threat actors — a change that was one of the key themes in the recent CrowdStrike Services Cyber Front Lines Report.
Why BloodHound?
![]()
In many ways, Microsoft’s Active Directory (AD) is the heart of a network in environments that use it — which is the majority. It handles identity, authentication, authorization and enumeration, as well as certificates and other security services. It’s designed to help find things, which generally enables and accelerates business operations. But the same characteristics that make it a cornerstone of business operations can make it the perfect guide for an attacker.
Since AD’s inception, smart attackers have leveraged it to map out a target network and find the primary point of leverage for gaining access to key resources — and modern tools like BloodHound have greatly simplified and automated this process. But smart companies can use these same techniques to find and remediate potentially vulnerable accounts and administrative practices before an attacker finds them, frustrating the quest for privileged access.
AD Analysis and BloodHound Basics
AD creates an intricate web of relationships among users, hosts, groups, organizational units, sites and a variety of other objects — and this web can serve as a map for a threat actor. If attackers want to determine which user account on which host will enable access to the data they are after, then BloodHound is an ideal tool for finding that information.
BloodHound is an open-source tool developed by penetration testers. Its purpose is to enable testers to quickly and easily gain a comprehensive and easy-to-use picture of an environment — the “lay of the land” for a given network — and in particular, to map out relationships that would facilitate obtaining privileged access to key resources.
BloodHound is designed to feed its data into the open-source Neo4j graphical database. This allows BloodHound to natively generate diagrams that display the relationships among assets and user accounts, including privilege levels. By selecting a specific network asset, the user can generate a map that shows paths for achieving privileged access to that host, as well as the accounts and machines from which that access could be gained.
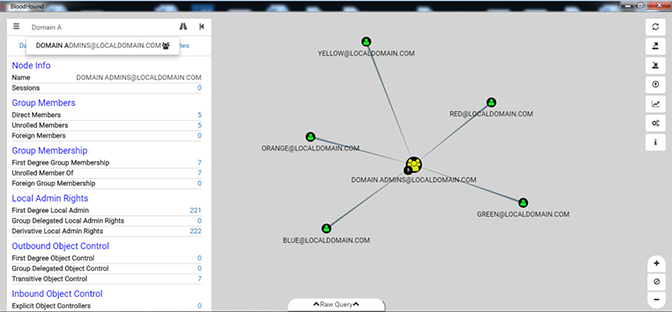
Example of a BloodHound map showing accounts, machines and privilege levels
What Can You Do?
To help thwart the use of BloodHound by threat actors attacking your network, CrowdStrike recommends the following practices:
- Leverage tools that will detect the use of BloodHound or another ingestor. For instance, the CrowdStrike Falcon® platform can detect and block the PowerShell version of the BloodHound ingestor if “Suspicious PowerShell Scripts and Commands” blocking is enabled in your prevention policy.
- Use BloodHound for your own purposes. Think about how you can use a tool such as BloodHound to enhance your network defense. BloodHound provides deep insight into how a network is organized and how permissions to access assets on that network are structured. This information can help you enhance your network defense strategy.
- Map out your network permissions. Harvest the insights from BloodHound, and then study those permissions the way an attacker might. This will allow you to find and eliminate the paths that an attacker might take to elevate their privileges and gain access to your key network and information assets.
- Change account permissions and privileged account management practices. This can help you make your network a much harder target for an attacker. In addition, this information can be used to discover security weaknesses, such as accounts that are vulnerable to attacks like Kerberoasting.
Download the complete report for more observations gained from the cyber front lines in 2019 and insights that matter for 2020: CrowdStrike Services Cyber Front Lines Report.
Additional Resources:
- Watch an on-demand webcast that takes a deep dive into the findings, key trends and themes from the report: CrowdStrike Cyber Front Lines Report CrowdCast.
- Read previous blogs on the key findings from the CrowdStrike Services Report: Part 1: Know Your Attackers and Part 2: Common Attacks and Effective Mitigation
- Learn more about the CrowdStrike Services team and how it can help your organization improve your cybersecurity readiness by visiting the webpage.
- Learn more about the powerful CrowdStrike Falcon® platform by visiting the webpage.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.

