Should You Worry About Software Supply Chain Attacks?
While there is much discussion today about potential weaknesses in the hardware supply chain, given the recent attacks attributed to China, the software supply chain has already proven to be vulnerable with numerous attacks covered. Yet, even though these attacks seem to be making headlines more frequently, they are far from being a top concern of cybersecurity professionals. This disparity is one of the findings in a new report, “Seizing Control of Software Supply Chain Security,” based on a survey conducted by the independent firm Vanson Bourne and sponsored by CrowdStrike®. Among the findings is that while only 35 percent of respondents consider supply chain attacks an area of focus, 66 percent of organizations surveyed say they have come up against a supply chain attack.
What Is a Software Supply Chain Attack?
Software supply chain attacks occur when malicious code is injected straight at the source of a signed and trusted application. This application can then be distributed using the legitimate software update mechanism. The idea is to contaminate the trusted source and thereby gain access to a huge pool of trusting victims.
This scenario played out in May 2017, when the popular open-source video conversion tool Handbrake was compromised to include and distribute a remote access toolkit called Proton.
The same thing happened with NotPetya in June 2017. A ransomware payload was injected into a new version of a Ukrainian accounting software that was then distributed with the update.This happened again with the CCleaner attack of August 2017 when attackers found a way to insert malicious code into the CCleaner 5.33 update. That infected version was signed with a valid and authentic certificate and was available from the legitimate website of Avast, maker of CCleaner. Ultimately, more than two million users downloaded that update. Once installed, the malicious code in the update opened a backdoor and established communication with a command and control (C2) server.
Tracking The Attacks
Unfortunately, such attacks are not new and CrowdStrike has been tracking these kinds of activities for a long time. In 2014, for example, CrowdStrike Falcon® Intelligence™ had already observed such a technique. Back then, the nation-state actors ENERGETIC BEAR had managed to bundle their malware into the installers of software used by the organizations they were targeting. This tactic granted them remote access to sensitive systems that were part of critical energy infrastructure.
A number of nation-state adversaries have, in fact, demonstrated the capability and intention to conduct such supply chain attacks. To compound the risks, 90 percent of the survey respondents confirmed that they incurred a financial cost as a result of experiencing such an attack, which averaged $1.1 million. The accelerated trend of supply chain attacks, the fact that powerful attackers have the will and the means to conduct them, and the high cost of being a victim should be sufficient to make this type of attack a priority for cyber defenders.
What It Takes to Be Better Prepared
While there is no “silver bullet” defense, most organizations already have tools they can use to better prepare and protect themselves. Another part of the solution is process-driven and can be summarized by the adage “Trust but verify.” This can consist of establishing a process for testing new software and updates being deployed into an environment, or into gold images. This process used to be prevalent. New applications, software updates, and even content updates such as antivirus signature, used to be thoroughly tested before being deployed — if not to detect the presence of malware, then at least to uncover compatibility issues. Although verifications like these seem to be performed less and less, you should try to conduct the following checking procedures:
- Run the hash values of the software against threat intelligence and IOC feeds.
- Detonate the software in a sandbox for full analysis — the screenshot below shows an example of how Falcon Sandbox™ analysis would have identified the CCleaner update as being malicious.
- Run the update on some test systems first and observe the behavior, including the network connections it attempts to make. This is where a robust endpoint detection and response (EDR) solution such as CrowdStrike Falcon® Insight™ can provide the depth of visibility you need to understand what is going on, and to be alerted if malicious activities are detected.
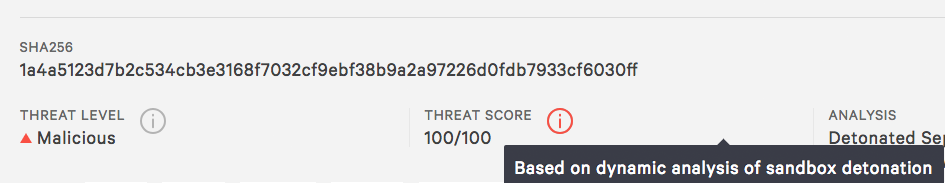
This example shows how Falcon Sandbox analysis would have identified the CCleaner update as being malicious. Analysis details, as well as IOCs and Yara rules, were also provided in the complete report, to enable immediate prevention.
Next, make sure your endpoint security product includes technologies that are able to prevent software supply chain attacks. This starts with an anti-malware solution that uses machine learning (ML) as opposed to signatures. ML is capable of identifying malware even if it’s unknown or digitally signed. The CrowdStrike Falcon® ML engine, for example, was able to detect and block NotPetya from the get-go. Unfortunately, 76 percent of the survey respondents indicated they are not currently using AI/ML to protect against software supply chain attacks. Of those, 28 percent are not even planning to use it, bypassing one of the most efficient ways to prevent these types of attacks.
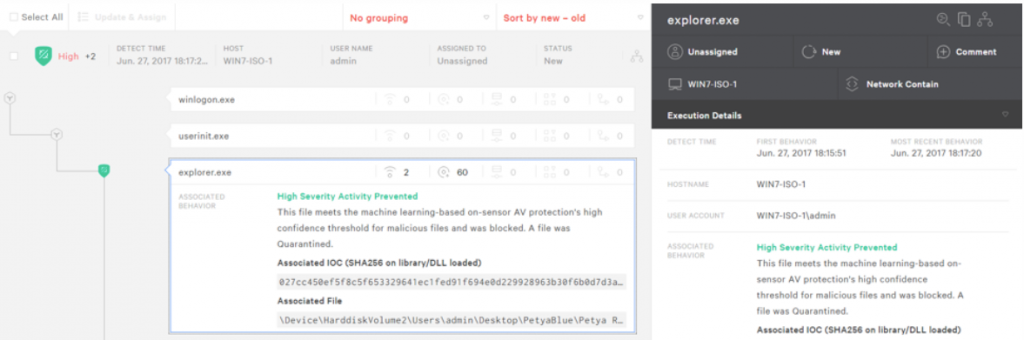
This example shows how the CrowdStrike Falcon® endpoint protection machine learning engine blocked NotPetya
Behavioral blocking can be another efficient method to prevent the execution of malware originating from the software supply chain. Falcon endpoint protection was also capable of preventing NotPetya with CrowdStrike behavioral IOAs (indicators of attack). One of the behaviors that Falcon could observe during a NotPetya infection was RUNDLL32.EXE behaving maliciously. Falcon was able to see and stop the following activities, as shown in the illustration below:
- RUNDLL32.EXE attempting to execute a malicious DLL
- RUNDLL32.EXE simultaneously trying to steal credentials
- RUNDLL32.EXE writing them to a temp file
- RUNDLL32.EXE invoking a command to set the task scheduler to reboot the system in the near future
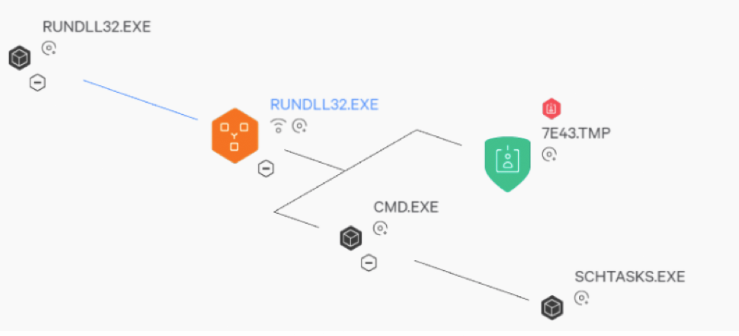
This example shows the Falcon UI process tree with a history of RUNDLL32.EXE malicious behavior
Detecting the malicious activities that follow a successful software supply chain attack is also a critical part of protecting against them. You need to be able to find out as early as possible if you have been compromised, so you can respond quickly and mitigate potential damage. It’s sometimes easy to tell if you’ve been hit — as with the NotPetya ransomware — but the CCleaner and Handbreak attacks were stealthier. A threat intelligence subscription will help you monitor and keep abreast of known malicious domains and IPs, notifying you if the malware installs successfully and tries to communicate with its C2. That will also give you the ability to proactively block those domains and IPs.
In terms of responding to a potential breach, a software inventory solutions such as Falcon Discover™ will immediately find the systems where the compromised software has been installed, or validate that your environment is safe. Finally, incident response (IR) services or a full endpoint management solution like Falcon Complete™ can do the cleanup on your behalf, often getting you back to business in record time.
Software supply chain attacks are insidious because they abuse the trust between a vendor and its customers, causing damage to both parties. Eighty percent of the 1,300 respondents in the Vanson Bourne survey believe that software supply chain attacks have the potential to become one of the biggest cyber threats over the next three years. This trend has also been reported by CrowdStrike Falcon® Intelligence, which has observed an increase of those types of attacks in frequency and sophistication. If these forecasts are correct, organizations should start preparing themselves now to mitigate the risks to come.
Learn more:
Read the survey report: “Seizing Control of Software Supply Chain Security.”
Get an in-depth understanding of true “next-gen” endpoint detection and response (EDR) capabilities in this white paper: “EDR — Automatic Protection Against Advanced Threats.”
Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.


