Taking Security to the Next Level: CrowdStrike Now Analyzes over 100 Billion Events Per Day

From the very beginning, CrowdStrike® set out on its mission to stop breaches by harnessing the power of the cloud. The cloud has transformed the IT landscape, allowing customers to deploy new services faster, without expensive infrastructure and the maintenance headaches that come along with it. In the case of the CrowdStrike Falcon® platform, it has an additional critical benefit: crowdsourced threat telemetry.
By coming together in the cloud, our customers participate in the world’s largest telemetry pool focused on stopping threats. Together they contribute to, and reap the benefits of, a massive set of metadata from a diverse global population.
CrowdStrike recently reached a significant milestone in our breach-stopping journey: Our customer base is contributing more than 100 billion events per day into the CrowdStrike Threat Graph™. This massive amount of data is continuously collected and correlated in our purpose-built, cloud-native graph database to deliver protection against new and emerging threats in real time across all CrowdStrike customers. As the volume of events that are aggregated and analyzed increases, our customers continue to stay a step ahead of today’s stealthiest and most sophisticated adversaries.
One hundred billion is a huge number, equivalent to the global daily volume of Facebook’s WhatsApp and Messenger combined. CrowdStrike is rightfully proud of this accomplishment because it speaks to the dedication and expertise of our engineering team, and the incredibly resilient, efficient and scalable platform they have created. However, we are even prouder of the fact that this achievement, which is made possible by our visionary cloud architecture, is the result of a global effort that benefits all CrowdStrike customers equally — from the largest enterprise to the smallest organization.
The Importance of Massive Data Sets
The ability to crowdsource a huge range of threat telemetry and determine the context of each threat — the “how, why and when” — is essential to effective detection, prevention and remediation. The ability to house and harness a data set of this magnitude emphasizes the essential role of the cloud for delivering the next generation of endpoint security. While other vendors have struggled with cloud adoption, CrowdStrike’s cloud-native architecture was built from the ground-up to be able to handle this extraordinary number of events per day — and more. While we pause a moment to reflect on our exponential growth, our systems are smoothly advancing on a trajectory that will take us eventually to a trillion events per day and beyond. As the data set grows, it also learns. Our advances in artificial intelligence and machine learning depend on the ability to leverage massive data sets — the bigger the better. This is key for ensuring the strongest possible zero-day protection against today’s threats — and tomorrow’s.
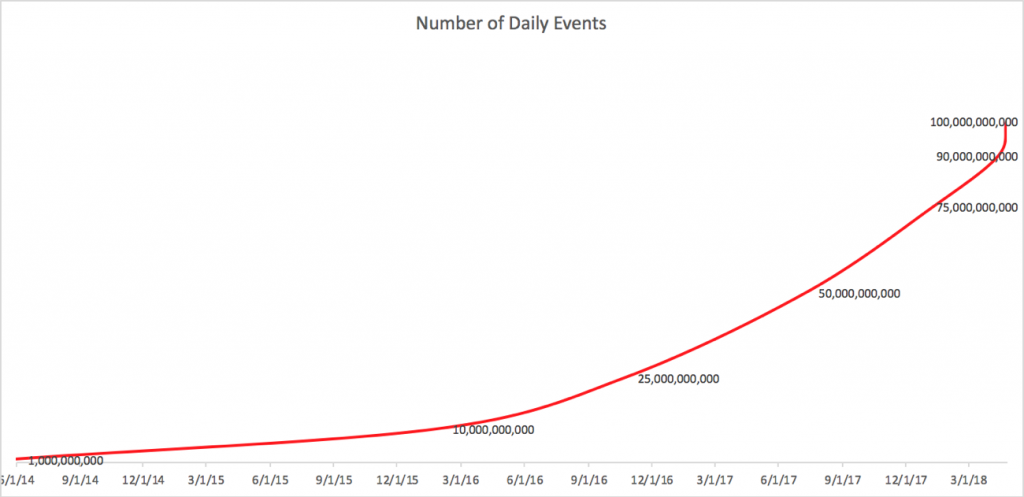
The chart below shows the steep trajectory of the increasing amount of data per day contributed by CrowdStrike customers since 2014. When I joined CrowdStrike in 2014, the platform was processing a few billion events a day. Since then, the platform has continued to scale, seamlessly powered by the forward-looking architecture that has stood the test of time. Any massive cloud platform runs into production issues. At CrowdStrike, we are also proud of the way we respond to production issues — always conducting blameless post-mortems and staying laser-focused on fixing root causes. This results in a robust, scalable platform and allows the team to continue thinking about scaling to the next 10x.
Making Data Actionable
Of course collecting and collating data is only the first step toward creating actionable insights and stopping threats in their tracks. Here are a few other numbers that tell the full story of how CrowdStrike makes this data actionable:
- Data is collected and indexed: 100 billion events per day are gathered from 176 countries across all deployed sensors.
- Data is enriched: Threat intelligence covering more than 100 known adversaries and thousands of associated indicators of compromise — also, “known bad” domains and IPs are added.
- Data is analyzed: Data is immediately available for multi-sourced automated analysis where we are able to make more than 2.3 million decisions each second around behaviors that are good, bad or somewhere in between. CrowdStrike employs expert managed hunting teams add human intelligence to complement the automated analysis.
- Data is made actionable: New classes of attacks seen at any of our customers are converted to indicators-of-attack (IOAs)-based prevention, validated, and all CrowdStrike sensors are immediately updated to protect against these new threats.
Being able to transform this data into actionable information that allows CrowdStrike customers to take effective and immediate measures that can thwart a cyberattack to stop a breach is what drives the value and rapid adoption of the CrowdStrike Falcon® endpoint protection platform.
Cloud enables Crowd
While many pundits talk about the power of the cloud to enable transformation, at CrowdStrike it remains a simple technology that enables a much stronger force multiplier: the power of the crowd. Today we celebrate a major milestone in proven scalability. CrowdStrike’s ability to process, correlate and analyze hundreds of billions of events daily, as well as investigate petabytes of historical data, reflects capabilities that are orders of magnitude beyond what existing analysis platforms offer. Still, we recognize that this number isn’t what drives successful outcomes for our customers. The metric that really matters is the one we set out to affect on Day One: the uncountable thousands of breaches that customers have prevented through the enormous strength of community.
Learn more about the CrowdStrike Falcon® Platform
Learn how CrowdStrike Threat Graph analyzes and correlates data