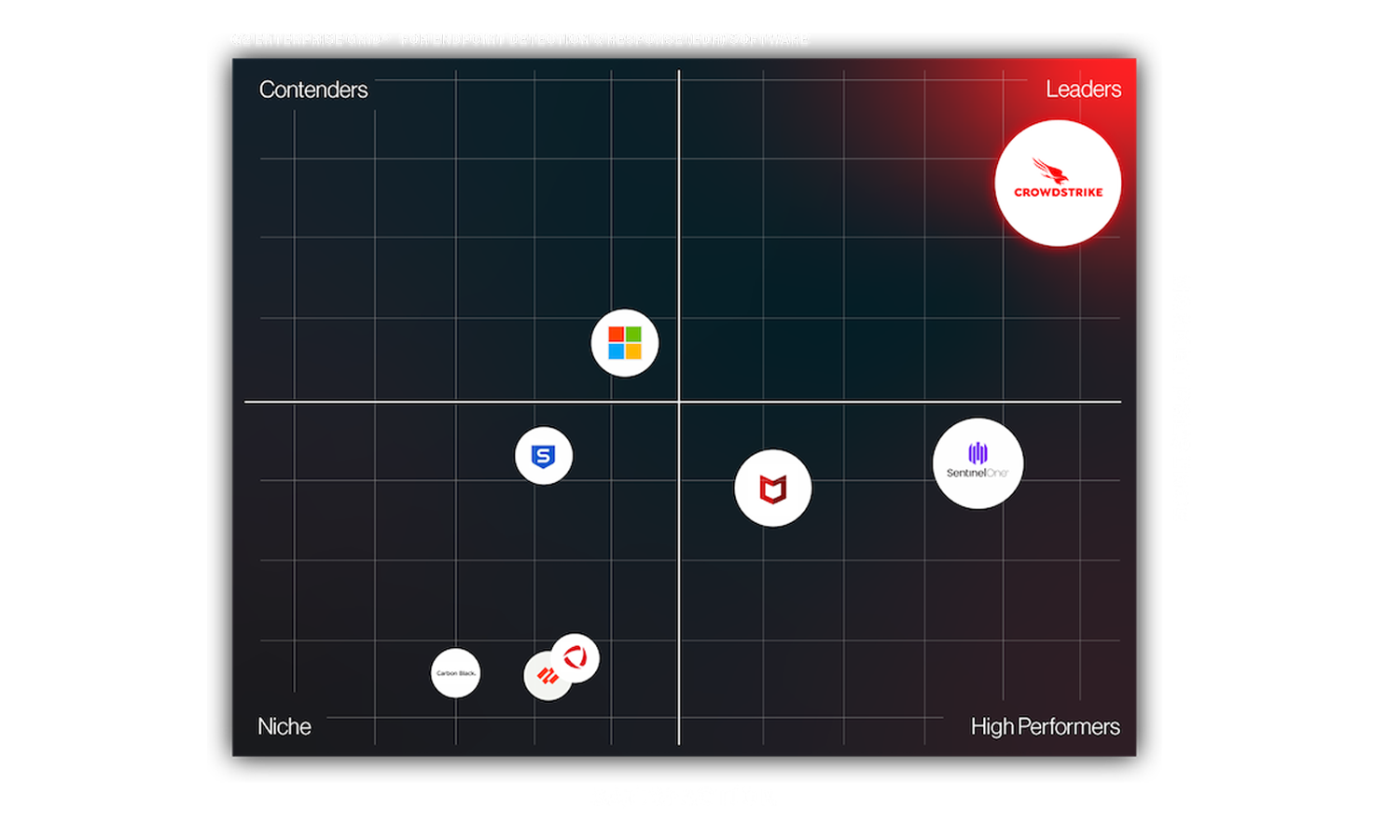
CrowdStrike vs the competition
Compare security solutions
Evaluating cybersecurity vendors? Check out our side-by-side comparisons by clicking on each of them below.
Ready to try CrowdStrike for yourself?
Get access to the CrowdStrike Falcon® platform powered by the CrowdStrike Security Cloud and see for yourself why organizations choose CrowdStrike over the competition.
