Accelerate Partner ProgramStrategic technology partners
Innovate with CrowdStrike to deliver best-in-class solutions to solve real-world challenges
The future of cybersecurity - delivered today
The power of one platform delivering the future of cybersecurity
250 million
API requests per day
400+
integrations
2 trillion
events/day
Technology ecosystem partners
Provide robust protection with custom-built applications on a leading cybersecurity marketplace:
- Enable customers to discover, try, buy and deploy your apps
- Solve use cases, leverage industry leading AI, and maximize the joint business and technical value for customers
- Offer differentiated solutions with accelerated time to market

Cloud service providers
Simplify and secure the journey to the cloud with enhanced protection across cloud environments:
- Get comprehensive cloud security offerings from a cloud-native platform
- Access robust service integrations with strategic cloud provider partners including AWS, Google Cloud, and Red Hat
- Secure all critical areas of enterprise risk, including endpoints, workloads, identities and data

Embedded OEM partners
Harness the power of CrowdStrike technology in your products to build innovative solutions that meet your customers’ needs:
- Deploy industry-leading security capabilities, advanced analytics and AI, and threat intelligence in your products
- Accelerate time-to-market with tried-and-tested CrowdStrike technology
- Free up development resources and gain support expertise to streamline product delivery
Visit the
CrowdStrike Marketplace
CrowdStrike Marketplace
Visit the
CrowdStrike Marketplace
CrowdStrike Marketplace
An open ecosystem
to meet your business needs
to meet your business needs
Innovate at cloud scale
Meet your business needs with differentiated and interoperable security applications built on the cloud-scale Falcon platform, without complexity or cost overhead.
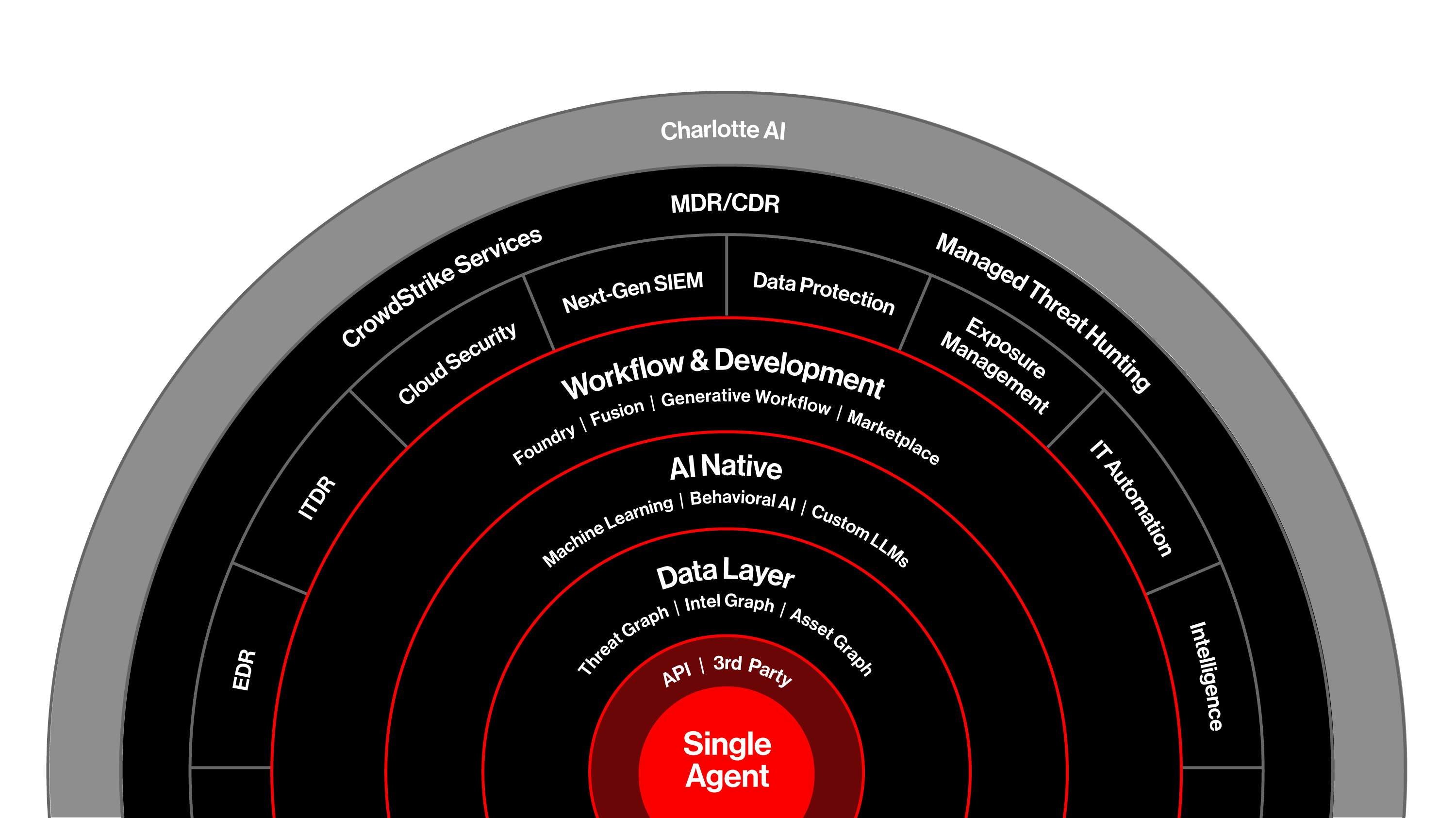
Benefit from data-driven insights
Harnesses the power of big data and artificial intelligence to deliver comprehensive visibility and rich data analytics to arm your team with contextual insights.

Minimize risk with a cyber leader
Get protection across the entire threat lifecycle with the world's most advanced cloud-native platform that secures the critical areas of enterprise risk.

Maximize your investments
Extend your investments in the Falcon platform with unified industry-leading capabilities and consolidated cybersecurity products, built to stop breaches.

Customer case studies


