Organizations See Dramatic Reductions in Alert Fatigue With CrowdScore
Organizations face enormous challenges in prioritizing, understanding and responding quickly to a deluge of alerts triggered by a wide range of modern threats. CrowdStrike’s new CrowdScoreTM capability is proving to be a true force multiplier, giving overworked security teams a crucial speed boost in this must-win race against the adversary.
In recent blogs, we showed how “noise” is a key problem facing security teams, resulting in massive alert fatigue and missed attacks. CrowdScore introduces sophisticated techniques that effectively measure and prioritize incidents, solving these key problems, while also helping security executives get a clear picture of the attacks targeting their organizations in real time.
CrowdScore and the new Incident Workbench are now available to all users of Falcon InsightTM. These groundbreaking new features have been deployed with select customers and we are excited to share some of the fantastic results these early adopters are seeing in the real world, beginning with how CrowdScore helps to solve the problem of alert fatigue.
Intelligently Prioritized Incidents Eliminate Alert Fatigue
Organizations of all types struggle with alert fatigue, where the stream of potential threats can bury the signal in noise. All too often, important alerts are missed and valuable human resources are squandered as security teams attempt to piece together a cohesive picture from piles of individual alerts.
CrowdScore uses sophisticated, cloud-based analytics to combine seemingly disparate security alerts and indicators into incidents. By focusing on the full incident rather than individual alerts, organizations can see a massive reduction in the number of items that require an analyst’s attention.
In addition, with the full context derived from CrowdStrike Threat Graph®, CrowdScore’s smart prioritization engine streamlines the triage process by presenting analysts with the most critical threats first.
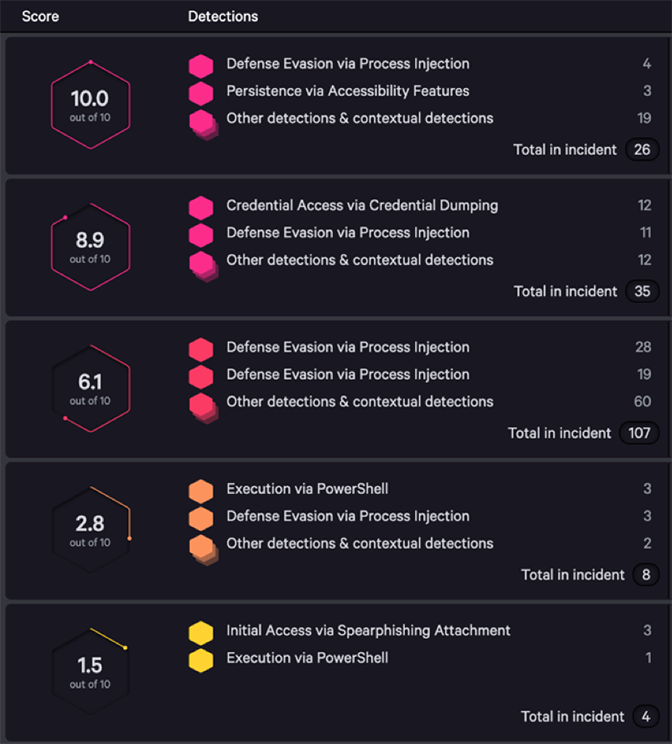
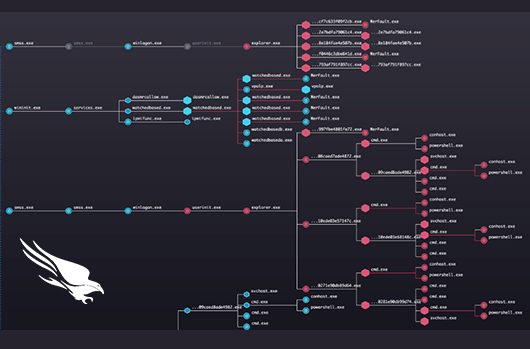
Figure 1: Shifting from alerts to intelligently-prioritized incidents
One way to measure productivity gains and the corresponding reduction in alert fatigue is to examine the amount of queued work that a security team needs to deal with in a given day. Customers shifting from alert-focused to incident-focused triage and investigations can realize enormous gains in productivity, by working at a higher level of abstraction. Consider the average heavy user of the Falcon platform: those who see 100 or more security alerts per day. Looking at the early adopters of CrowdScore and the new incident-based workflow, the average organization in this category saw a 98% reduction in the size of their work queue, comparing alert counts to incident counts.
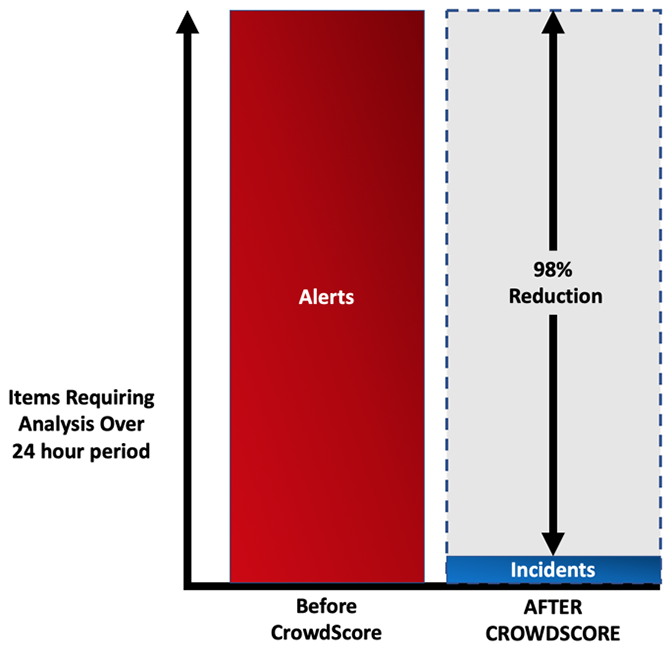
Figure 2: Representative Reduction in Security Analyst Work by Moving to Incident-driven Workflow
The benefits associated with relieving the pressure on overtaxed security teams are clear, but it doesn’t stop there.
Prioritization and Context Speed Investigations
Speed to investigate is another key metric for security organizations. According to CrowdStrike’s 2019 Global Security Attitude Survey, the average organization takes 162 hours — nearly seven full days – to detect, triage, investigate and contain a threat. When modern attacks pivot from initial entry to lateral movement in minutes, this is clearly too long.
Decreasing the time required to investigate and respond to attacks is critical in order for organizations to stay ahead of adversaries. CrowdScore helps organizations accomplish this goal with the new Incident Workbench.
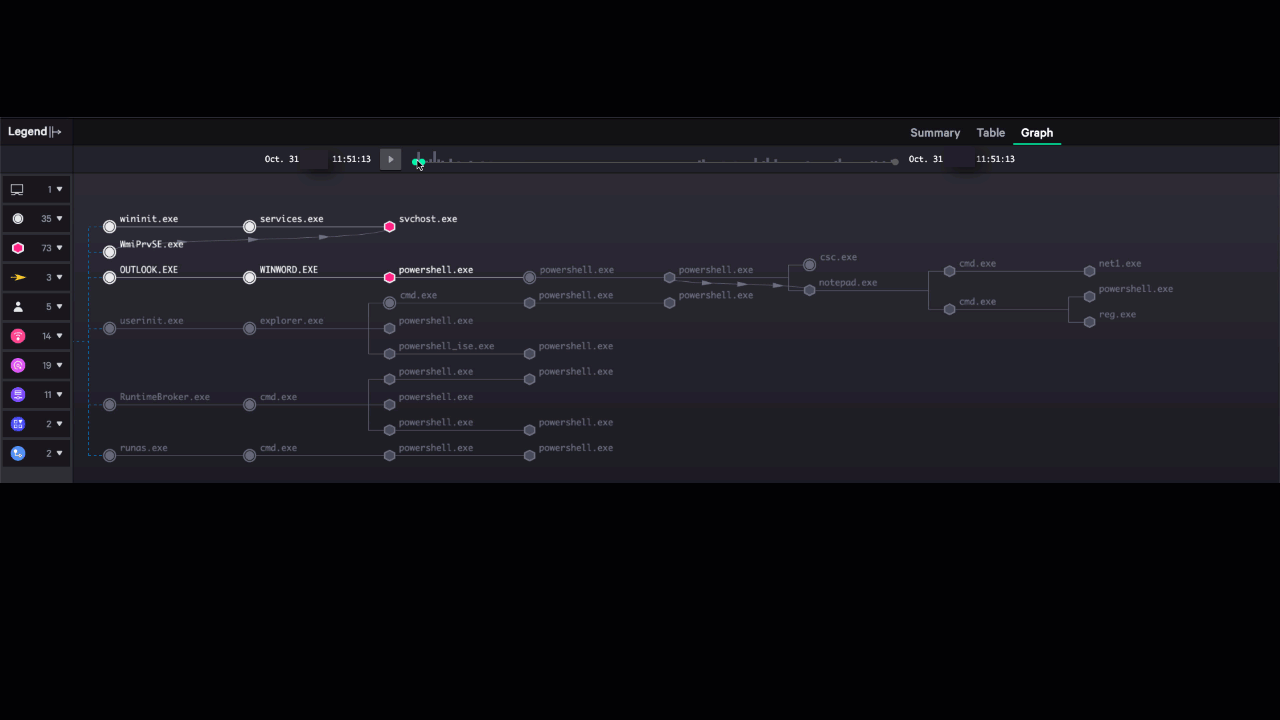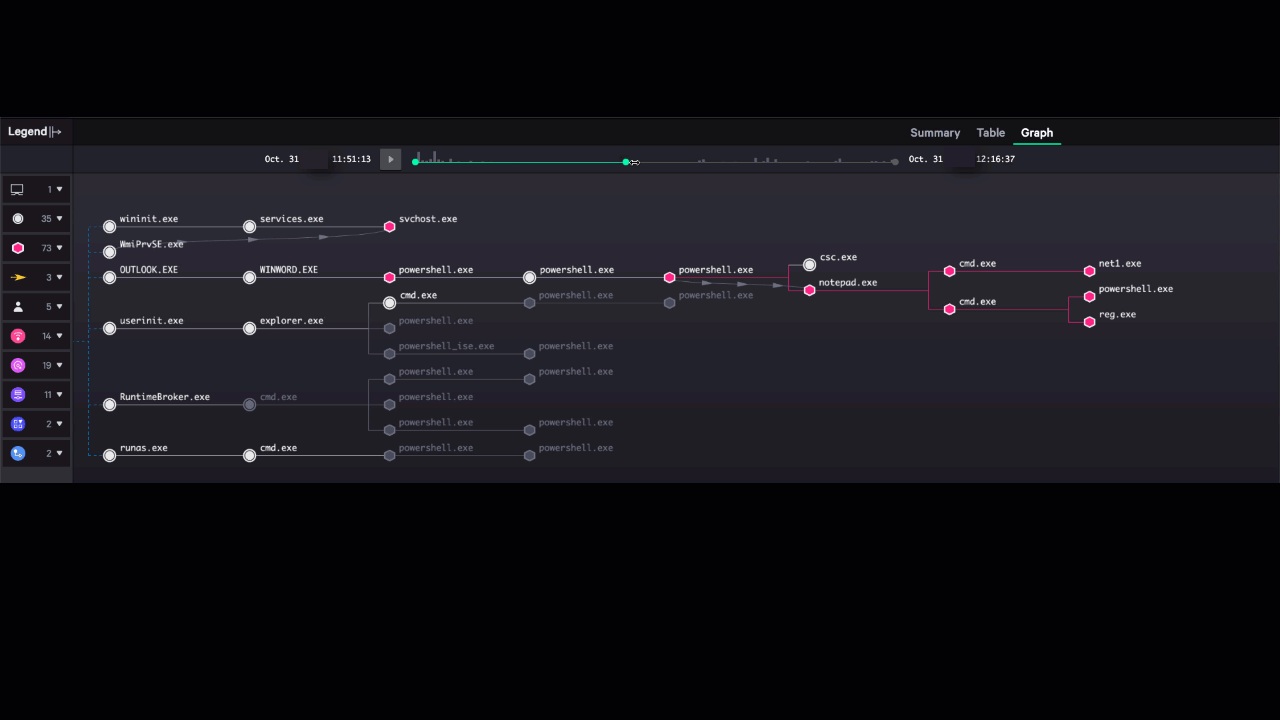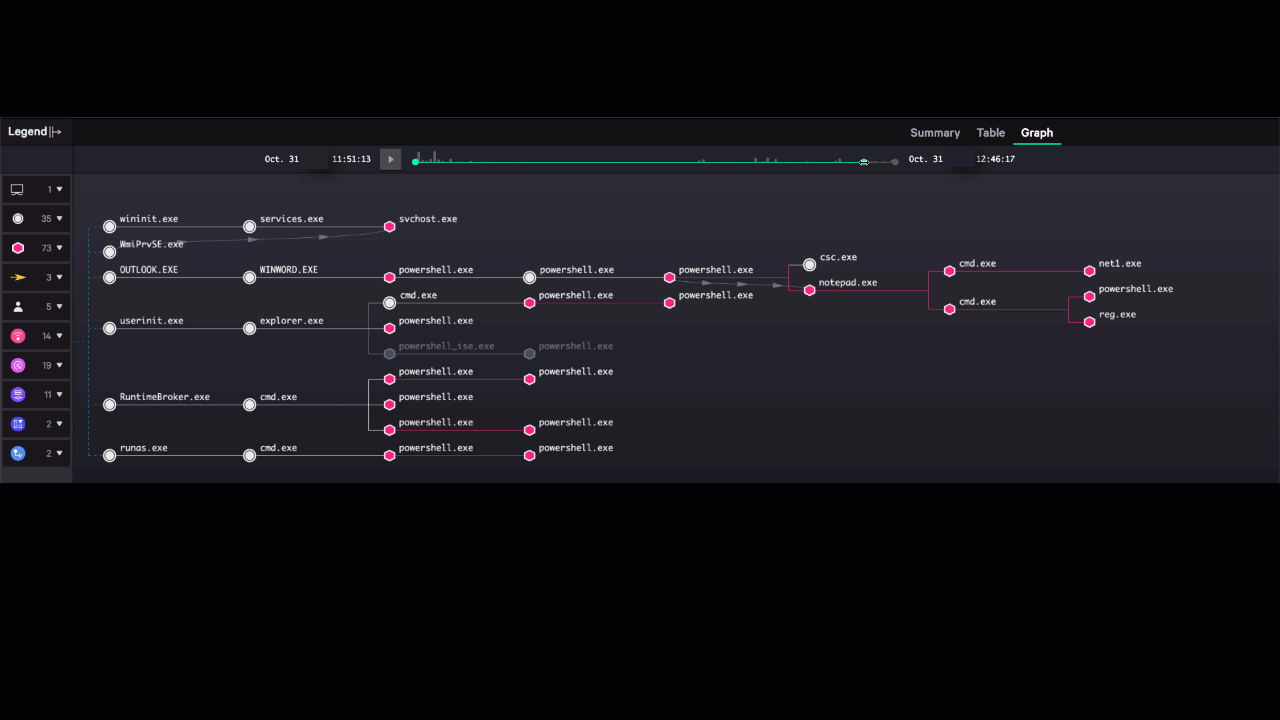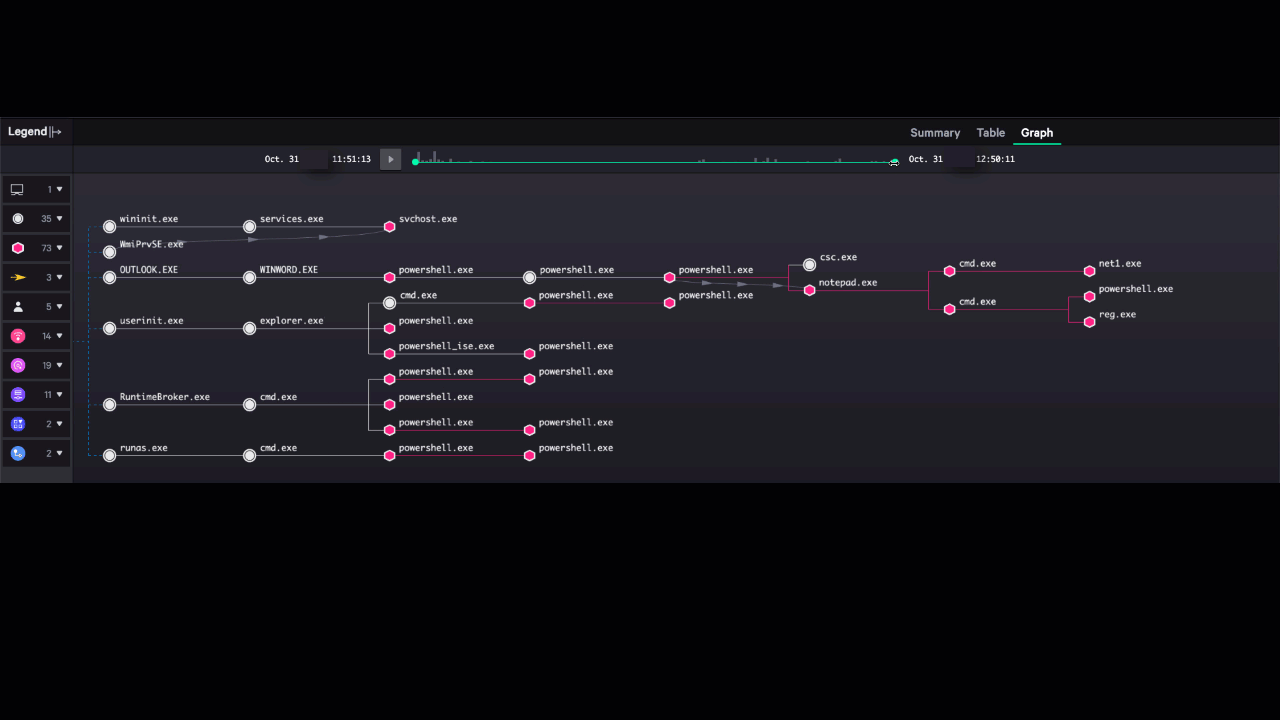
Figure 3: Reducing time-to-investigate through the Incident Workbench
The Incident Workbench pulls together a wide range of information that analysts need in order to orient themselves and act on a threat. It displays not only the alerts related to an incident, but also enriches the alert with deep context extracted from Threat Graph that builds out a much more complete picture of the threat. It displays relationships between elements of the attack, including a dynamic timeline showing how the attack evolved over time.
Incident Workbench automates data collection that would take hours or longer in most organizations, helping organizations make measurable progress toward meeting the 1-10-60 Challenge.
See the Big Picture
Finally, CrowdScore is helping security teams cut through the noise to truly understand their organizations’ threat level on a continuous basis. This organizational “DEFCON” score updates in real time, and makes it easy for security leaders to quickly understand if they are under attack and the severity of the threat, so they can immediately mobilize the appropriate response.
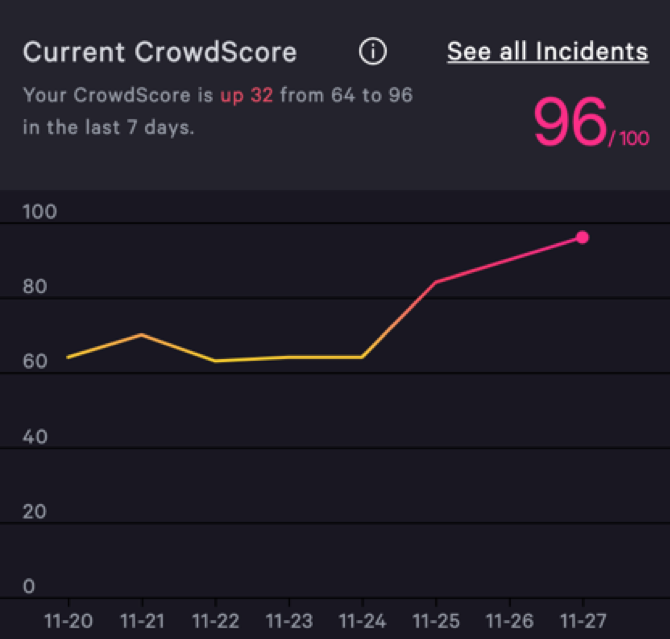
Figure 4: CrowdScore shows the real-time current threat level
CrowdStrike customers are already seeing the benefits of this executive-level visibility and integrating the CrowdScore metric into their day-to-day reporting and workstream. According to one director of security operations for a major apparel retailer, “CrowdScore gives us a single, easy-to-understand metric that we can use to clearly communicate the severity of today’s threats to our senior leaders. Our CIRC (cyber incident response center) manager uses it to report the daily threat level, which helps everyone in our organization understand when we need all hands on deck. CrowdScore puts threats in context for us, so our leaders can immediately see the big picture.”
We’re Just Getting Started
The early results for CrowdScore and the Incident Workbench are very promising, and this is just the tip of the iceberg. If you’d like to learn more, I hope you’ll join us for our upcoming webinar on Dec. 10, where we’ll explore these new features in more detail and show you how they are helping to transform security organizations.
Additional Resources:
- Attend our webinar to learn more about CrowdScore.
- Read more about CrowdScore in the following blogs:
- Learn more about the CrowdStrike Falcon® Platform by visiting the webpage.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and learn how true next-gen AV performs against today’s most sophisticated threats.


