CrowdStrike Services Helps Organizations Prioritize Patching Vulnerabilities with CrowdStrike Falcon Spotlight

When the CrowdStrike Services team conducts a proactive security engagement, such as a Cybersecurity Maturity Assessment or Tabletop Exercise, it often uses CrowdStrike Falcon® Spotlight to identify what vulnerabilities exist in the environment. Unfortunately, this can be a disheartening experience, as many organizations we see have millions, even tens of millions, of unpatched vulnerabilities. It’s typical to see at least a quarter of those listed with a CVSS rating of Critical.
It’s a grim testament to just how difficult it can be to run an effective vulnerability management program. The challenges that most customers face will probably sound familiar:
- The number of vulnerabilities far outnumber what the security or IT teams could ever hope to fix.
- Prioritizing only vulnerabilities rated Critical and High allows lower-rated vulnerabilities to linger and weaken your security posture.
- Asset criticality is often absent from prioritization efforts altogether.
- Patching systems can be mundane and seemingly unrewarding work for the seasoned IT/security professional.
This blog highlights the importance of effectively prioritizing vulnerabilities and shows how Falcon Spotlight can be used to do so effectively and with minimal effort.
The Basics of Vulnerability Management
There is no silver bullet for vulnerability management. Some of the security teams CrowdStrike Services works with have all of the building blocks in place but are not authorized to force system changes. Others recognize their knowledge gaps, but aren’t empowered to build a strong foundation by maturing their asset management practices.
Regardless of whether these kinds of obstacles exist, focusing on the fundamentals provides an important foundation. Automation and “single-pane-of-glass” tools are a key to success when the tasks are repeatable and the volume of work is large. As with many things in cybersecurity, these capabilities help decrease manual process fatigue and lead to increased efficiency of security programs. Vulnerability management is no exception — automation can help drive best practices in patch management across the board. Consistently applying updates for operating systems and key applications can dramatically reduce the total number of vulnerabilities, improve the organization’s security posture and make it easier to prioritize your remediation efforts.
For organizations that have mastered the basics, the next challenge is identifying and focusing on the issues that are most likely to cause problems or be exploited by an adversary. Of course, this is ever-changing.
This is an area where Falcon Spotlight can help. The CrowdStrike Services team, and many of CrowdStrike’s customers, use the Falcon Spotlight ExPRT.AI feature to focus their efforts. ExPRT.AI is an artificial intelligence model that offers a rating system utilizing telemetry and threat intelligence to provide a more accurate assessment of a vulnerability’s criticality, and it updates that assessment over time. For example, if threat intelligence shows that a vulnerability is being actively exploited, ExPRT.AI will adapt by increasing the criticality rating for that vulnerability. In addition to providing more accurate results, CrowdStrike Services has observed that ExPRT.AI generally produces a smaller combined number of vulnerabilities rated Critical and High — often less than 20% of the total according to the CVSS rating — thus reducing the amount of work required to make meaningful improvements to the organization’s overall security posture.
Watch this short video to see how Falcon Spotlight ExPRT.AI works.
How to Prioritize Assets
Filtering by CVSS or ExPRT.AI rating is only the first step in prioritizing vulnerability patching within Falcon Spotlight. The successful vulnerability management programs that CrowdStrike Services comes across also prioritize according to asset type, function and other criteria. The most successful programs are also aligned with the business’s goals and risk-prioritization. Because systems are not targeted equally — real-world threat actors and CrowdStrike red teams typically leverage only a few exploits against a small number of endpoints — this degree of prioritization allows security teams to markedly improve security by remediating a limited number of vulnerabilities for a limited number of assets. Improving the security of the assets most likely to be targeted can make a successful attack much more difficult.
Vulnerabilities on externally facing systems should always be a top priority, as these are easily accessible to any external attacker and therefore more likely to be targeted. Tier 0 resources such as domain controllers, AD certificate servers and SSO-related systems should also be considered high-priority assets. Though unlikely to be targeted from the outside since most are only accessible from an internal network, the security of these systems is critical to the security of the rest of the environment, and an adversary who gains access to the internal network will quickly seek them out. Unfortunately, it’s not uncommon for CrowdStrike Services to identify domain controllers on a customer’s network with vulnerabilities that are known to be actively exploited.
Other systems that often belong high on the priority list include Exchange servers, database servers and systems used for IT management functions such as software deployment, as these systems may contain sensitive information and are often associated with privileged accounts. It’s fairly common, for example, to see a SQL service account running as a domain administrator (an example of excessive privileges that should be fixed), and the CrowdStrike Services team has seen ransomware groups use an organization’s own software deployment tools against them.
Notably, a security or IT team can address all of the above priorities without seeking input from the rest of the business, because they are high-value targets from an attacker’s perspective. But the most successful vulnerability management programs also prioritize high-value assets from a business perspective. It starts with identifying critical business assets, such as systems that must remain up for the business to function or that host mission-critical data. If the organization has performed a “crown jewels” assessment, its results should be used to prioritize systems that hold important confidential data or play a pivotal role in the organization’s business processes.
Unfortunately, many organizations have not identified their most critical assets from the business perspective. These organizations may have a security team that is siloed or does not collaborate with the rest of the organization, or from one side or both there’s a lack of communication and engagement. The security team ends up making a best effort to “go do security” without an accurate idea of what matters most to the business. For these organizations, it’s worth noting that even without undergoing a formal analysis, informal attempts to identify business-critical systems or systems containing PII, PHI, etc., can still provide a helpful guide to determining which vulnerabilities to prioritize. (Note that such analysis yields benefits beyond vulnerability management in that it can add value to shaping disaster recovery plans, scoping the severity of incidents and informing broader risk management efforts.)
Divide and Conquer Through Focused Prioritization
CrowdStrike Services recommends that customers use Falcon Spotlight to help with prioritization by filtering vulnerability results on such criteria as hostname, system type (workstation, server or domain controller), IP range, vendor, product name and/or by the group tag applied to the asset. Tags can be applied to systems either at installation, via a command-line option or through Host Management in the Falcon console.
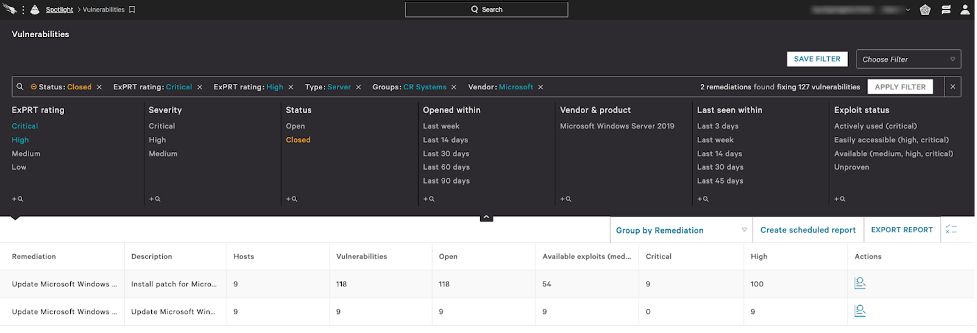
Figure 1. Filtering for Critical and High vulnerabilities on a specific group of servers (click to enlarge)
As a complement to filtering by asset, customers can also filter for vulnerabilities that are known to be exploited. Spotlight can filter on Exploit Status, which can be “Actively Used,” “Easily Accessible,” “Available” or “Unproven.” Because threat actors often rely on a small number of exploits to gain initial access, escalate privileges or move laterally, filtering in this manner helps create a manageable list of vulnerabilities, allowing organizations to significantly improve their security posture with a relatively small amount of effort.
During customer engagements, CrowdStrike Services gets even more focused, searching for specific vulnerabilities the team knows to be actively targeted by various threat actors. Some of our more mature customers take a similar approach and prioritize vulnerabilities that have been mentioned in their threat intelligence feeds, ISAC reports and other sources. This type of targeted remediation can be carried out by any organization. CISA maintains a public catalog of vulnerabilities known to be exploited and periodically publishes a list of the most exploited vulnerabilities. With Falcon Spotlight, customers can create a search for these high-profile vulnerabilities based on their CVE IDs and bookmark the search so they can revisit the results later for an updated look at their environment.
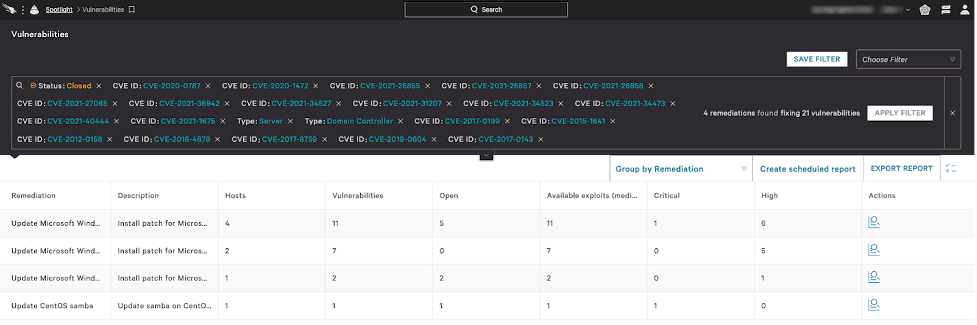
Figure 2. Filtering for specific vulnerabilities known to be actively leveraged by threat actors (click to enlarge)
During a Technical Risk Assessment with Falcon Spotlight in a large customer environment, CrowdStrike Services observed millions of critical vulnerabilities across tens of thousands of endpoints. By limiting the results to servers and domain controllers that contained any of approximately 20 widely exploited vulnerabilities, the CrowdStrike Services team was able to produce a much more manageable list of approximately 2,000 vulnerabilities across 700 hosts. Additionally, Falcon Spotlight was able to produce a list of the 44 unique remediations needed to fix these vulnerabilities. The prospect of trying to fix millions of vulnerabilities may seem overwhelming, even for the largest organizations, but 44 remediations is actionable for an organization of any size. Additionally, because these were vulnerabilities that various threat actors were known to leverage in their attacks, fixing them would meaningfully improve the client’s security posture.
Larger organizations may have IT teams assigned to different locations, system types or business applications. By using Falcon Spotlight to filter on hostname, host type, IP range, group tag and/or product name, these customers can produce and export a list of vulnerabilities, hosts and remediations tailored to each team or group in the organization. This will make their results more actionable and can enable them to move remediation efforts forward in multiple areas independently. This is also useful if the security team is lacking in organizational buy-in and wants to work with one team as a test case before pushing forward with their vulnerability management program enterprise-wide.
Falcon Spotlight also provides useful insight into the state of patch management in an organization’s IT environment. Falcon Spotlight’s Installed Patches page shows when systems were last patched, whether they need to be rebooted and how many patches are pending. Searching for systems that haven’t been patched in more than 30 or 60 days can identify gaps in the organization’s IT processes, while searching for systems that have been patched in the last week can identify whether work has been done toward outstanding remediations. This facilitates better communication between IT and security teams, makes it easier to determine whether remediation work has been started and helps identify when remediation is not complete. A reboot could prevent an incident response engagement.
Tailor Prioritization for Your Organization
There are many ways to prioritize vulnerability assessment and remediation efforts, and one organization’s approach doesn’t have to match another’s. Most organizations that CrowdStrike Services has seen succeed started by working with their data and experimenting with different filtering criteria to develop an understanding of what is in their environment. The suggestions in this blog are techniques we have seen organizations use successfully, but they are merely a starting point. Organizations should use other criteria, or split up or combine results in ways that make sense for them. It’s often best to start small and grow as the organization and its IT teams get comfortable with the process. Once the organization has a set of results that they think are actionable and important, they should start working on remediation. Most organizations will change their approach over time so they shouldn’t let analysis paralysis keep them from moving forward.
See for yourself how the industry-leading CrowdStrike Falcon platform protects against modern threats. Start your 15-day free trial today.
Additional Resources
- Find out more about CrowdStrike Services incident response, technical assessments, training, and advisory services.
- Learn more about how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself with a free trial of Falcon Prevent™.

