Multi and hybrid clouds add complexity and reduce visibility
Hybrid cloud providers combined with containerized and serverless architectures increase risk.
CrowdStrike Falcon® Cloud Security
See and secure everything across your clouds, your applications, and your data.
Outpacing Threats in the Cloud: Detection and Response Streamlined
Register nowCan you see and secure all your threats?
89%
Faster cloud detection and response1
6 to 1
Reduced six separate consoles to one unified console across cloud, endpoint, and identity1
$380k
Average savings per year2
Falcon Cloud Security is the industry’s only unified agent and agentless platform for complete code to cloud protection.
Cloud-native architecture. Best-in-class agent and agentless. Unified platform.
CrowdStrike Falcon® Cloud Security integrates every aspect of cloud security — CWP, CSPM, CIEM, CDR, and ASPM — into a unified console along with all other CrowdStrike modules, delivering deep visibility, detection and real-time response across the entire cloud-native stack.
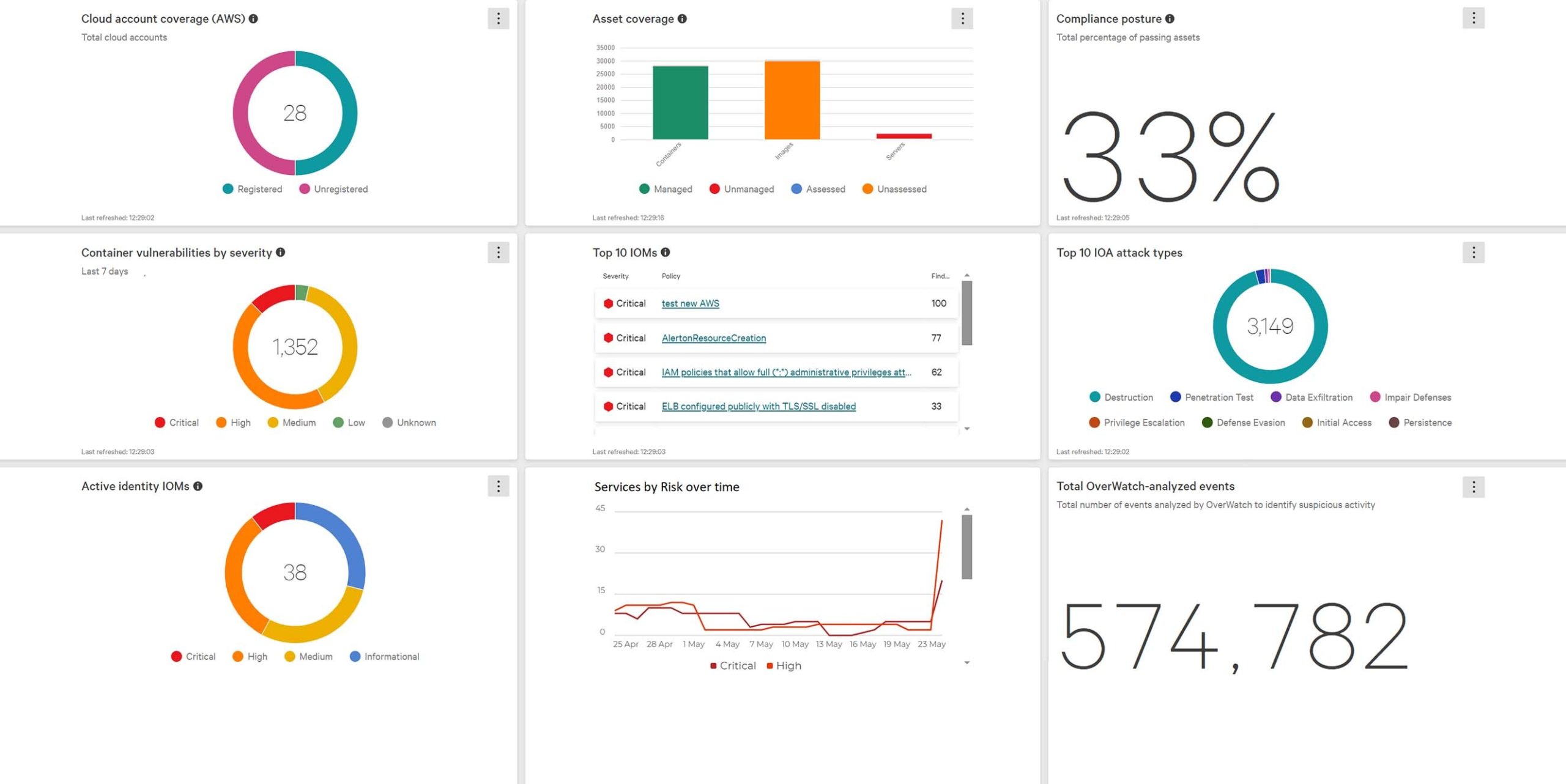
CrowdStrike offers visibility and business context into cloud applications by automatically mapping and identifying each microservice, database, API, and dependency. This enables customers to assess the business criticality of every attack surface, vulnerability, and threat.
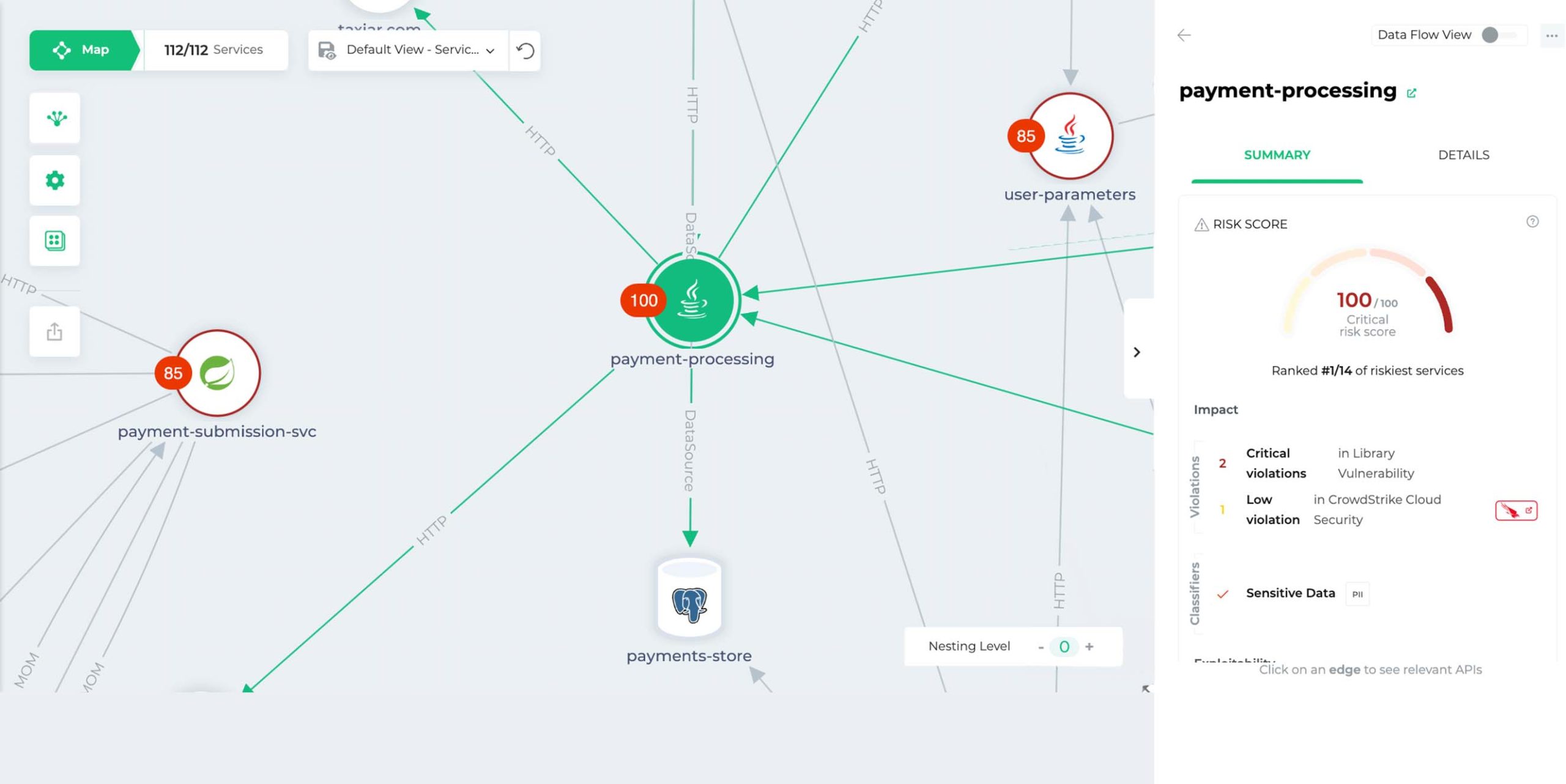
CrowdStrike enhances the analyst experience at every stage by leveraging AI and machine learning. Its risk scoring combines CVSS scores with critical business context, such as the location of sensitive data and active exploitation in the wild, enabling analysts to focus on the most important alerts.
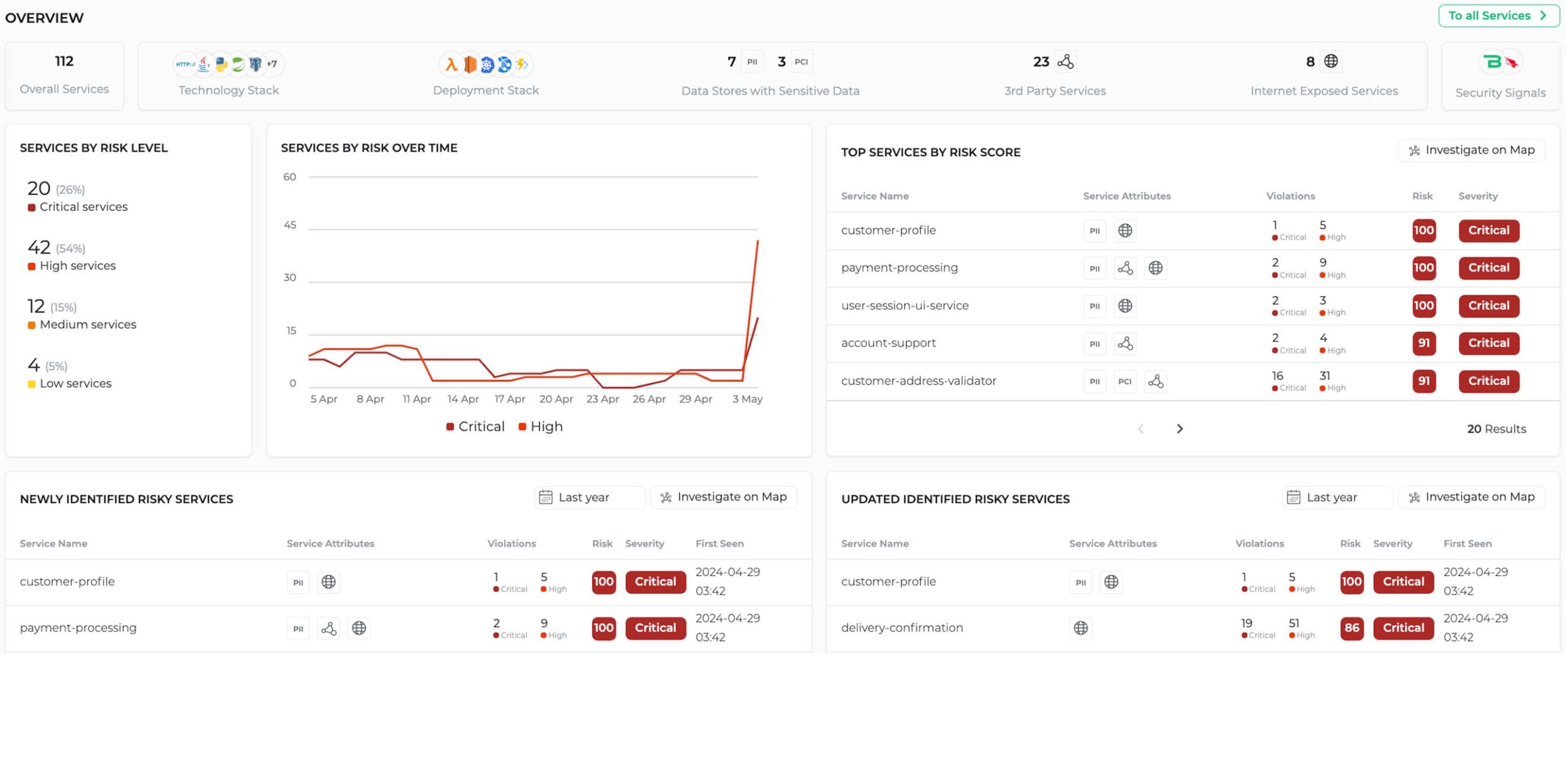
Stop cloud threats in real-time with advanced runtime protection built on the same revolutionary unified agent as our leading EDR and Identity Protection. This unified Falcon agent provides deep visibility, detection, and response across the entire cloud-native stack, covering all workloads, containers, and Kubernetes environments.
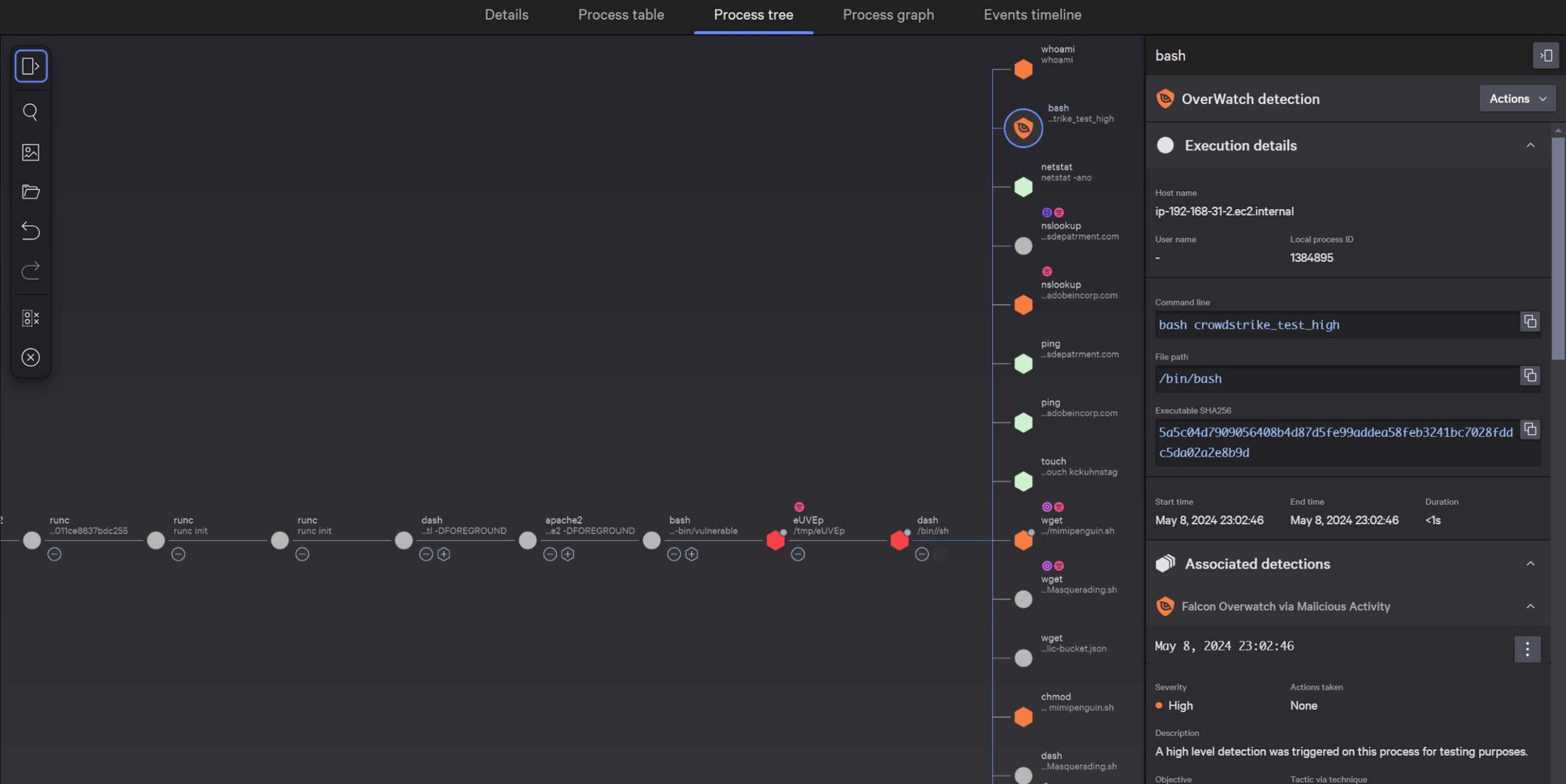
CrowdStrike Falcon® Adversary OverWatch is the only 24/7 cloud threat hunting service that proactively disrupts adversaries in real-time. Powered by leading threat intelligence and advanced AI, our global experts work tirelessly to prevent breaches. CrowdStrike tracks over 230 adversaries, processes 200K new IOCs daily, and manages over 300 million total IOCs, giving defenders a significant advantage.
Accelerate mean time to respond by 89% with leading cloud detection and response (CDR) that unifies elite 24/7 managed services and world-class threat intelligence with the industry’s most complete cloud security platform to stop breaches. CrowdStrike’s integrated threat intelligence tracks 230+ adversaries, providing a comprehensive understanding of a wide array of potential threats, enabling organizations to anticipate and respond to attacks more effectively.
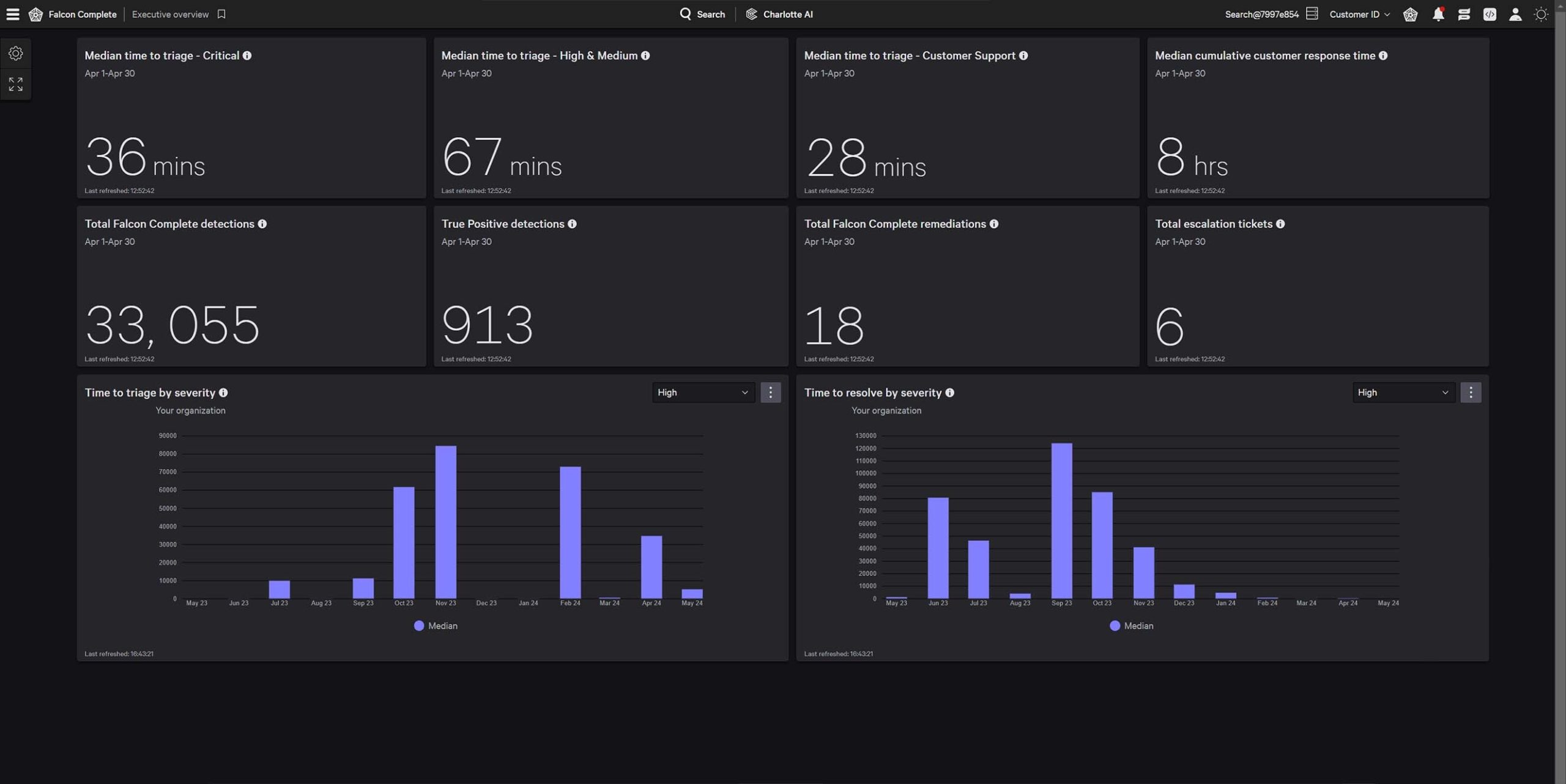
Recognized for our advanced, strategic approach to cloud security with the highest score of all vendors in Strategy.
Discover why customers choose CrowdStrike over competitors to stop breaches.
See the difference
Explore our cloud security products, services, and providers.
Discover how CrowdStrike’s advanced protection can secure your cloud environment. No strings, no hassle.
Start interactive demo1 Results are from Mercury Financial. Individual results may vary by customer.
2 These numbers are projected estimates of average benefit based on recorded metrics provided by customers during pre-sale motions that compare the value of CrowdStrike with the customer’s incumbent solution. Actual realized value will depend on individual customer’s module deployment and environment.