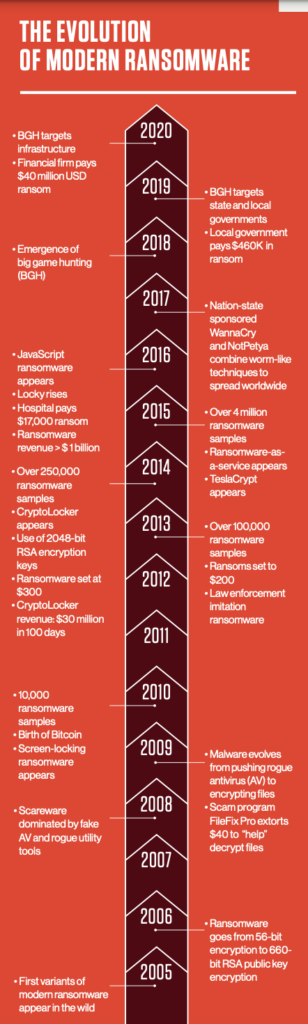
Following the evolution of ransomware, from a petty crime to a major economic windfall for global criminal enterprises, underscores why businesses should be deeply concerned about the threat. While its explosive growth over the past few years may make it seem otherwise, ransomware didn't come out of nowhere.
 An Old Scheme
An Old Scheme
Even though ransomware has been in the headlines consistently over the past five years or so, the idea of taking user files or computers hostage by encrypting files, hindering system access or other methods - and then demanding a ransom to return them - is quite old.
In the late 1980s, criminals were already holding encrypted files hostage in exchange for cash sent via the postal service. One of the first ransomware attacks ever documented was the AIDS trojan (PC Cyborg Virus) that was released via floppy disk in 1989. Victims needed to send $189 to a P.O. box in Panama to restore access to their systems, even though it was a simple virus that utilized symmetric cryptography.
Monetization
Despite its long history, ransomware attacks were still not that widespread well into the 2000s - probably due to difficulties with payment collection. However, the emergence of cryptocurrencies, such as Bitcoin in 2010, changed all that. By providing an easy and untraceable method for receiving payment from victims, virtual currencies created the opportunity for ransomware to become a lucrative business.
eCrime - a broad category of malicious activity that includes all types of cybercrime attacks, including malware, banking trojans, ransomware, mineware (cryptojacking) and crimeware - seized the monetization opportunity that Bitcoin created. This resulted in a substantial proliferation of ransomware beginning in 2012. However, this ransomware business model is still imperfect, because while Bitcoin payments are easy transactions for cyber criminals to use, they are not always so easy for their non-tech-savvy targets to navigate. To ensure payment, some criminals have gone so far as to open call centers to provide technical support and help victims sign up for Bitcoin - but this takes time and costs money
As it started to gain more mainstream appeal, ransomware developers recognized it as just the method of monetary extraction they'd been seeking. Bitcoin exchanges provided adversaries the means of receiving instant payments while maintaining anonymity, all transacted outside the strictures of traditional financial institutions.
CryptoLocker Appears
The table was set perfectly for the entrance of CryptoLocker in 2013. This revolutionary new breed of ransomware not only harnessed the power of Bitcoin transactions, but combined it with more advanced forms of encryption. It used 2048-bit RSA key pairs generated from a command-andcontrol server and delivered to the victim to encrypt their files, making sure victims had no way out unless they paid a tidy sum of about $300 for the key.
The Gameover Zeus banking Trojan became a delivery mechanism for CryptoLocker. The threat actors behind the botnet were among the first to truly realize the potential value of ransomware with strong encryption, to extend their profits beyond traditional Automated Clearing House (ACH) and wire fraud attacks that target the customers of financial institutions. CryptoLocker's backers had hit pay dirt, kicking off ransomware's criminal Gold Rush.
CryptoLocker Gameover Zeus was shut down in an operation spearheaded by the FBI and technical assistance from CrowdStrike researchers. Even though it was out of operation within seven months of starting, it served as proof to the entire cybercrime community of ransomware's tremendous business upside. This was the true inflection point for ransomware's hockey-stick growth.
Within a few months, security researchers were finding copious numbers of CryptoLocker clones in the wild and criminals from all over the world were scrambling to get a piece of the action. Since then, many organized crime gangs have shifted investments and resources from older core businesses, including fake AV, into ransomware operations. The criminal technologists have been working overtime to serve these potential customers by cranking up specialized operations to develop better ransomware code and exploit kit components, flooding Dark Web marketplaces with their wares.
The Advent of Big Game Hunting
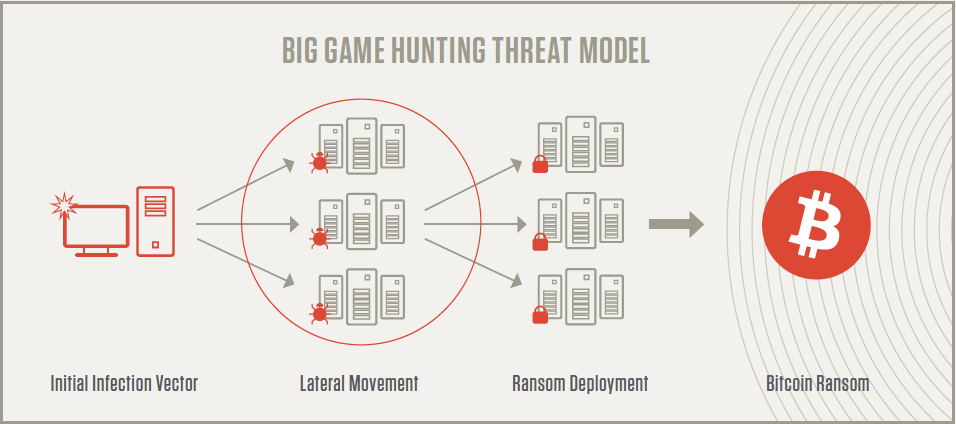
To optimize their efforts, ransomware operators decided to pivot from the "spray and pray" style of attacks that were dominating the ransomware space and focus on "big game hunting" (BGH). BGH combines ransomware with the tactics, techniques and procedures (TTPs) common in targeted attacks aimed at larger organizations.
Rather than launching large numbers of ransomware attacks against small targets, the goal of BGH is to focus efforts on fewer victims that can yield a greater financial payoff - one that is worth the criminals' time and effort. This transition has been so pronounced that BGH was recognized as one of the most prominent trends affecting the eCrime ecosystem in the CrowdStrike® 2020 Global Threat Report.
In 2020, CrowdStrike Services observed the continued evolution and proliferation of eCrime adversaries engaging in big game hunting (BGH) ransomware techniques. This trend is continuing into 2021 - a recent high-profile example is the CARBON SPIDER/DarkSide attack on a U.S. fuel pipeline.
Ransomware Actors Increase Pressure
CrowdStrike Services has observed eCrime adversaries utilizing various techniques to increase pressure on victim organizations to pay their extortion. While in previous years ransomware eCrime adversaries were rarely observed exfiltrating data, 2020 witnessed a widespread adoption of ransomware with data-leak extortion tactics among multiple eCrime groups. This method involves both encrypting a victim organization’s environment and also exfiltrating data with the threat to leak it if the extortion demand is not paid.
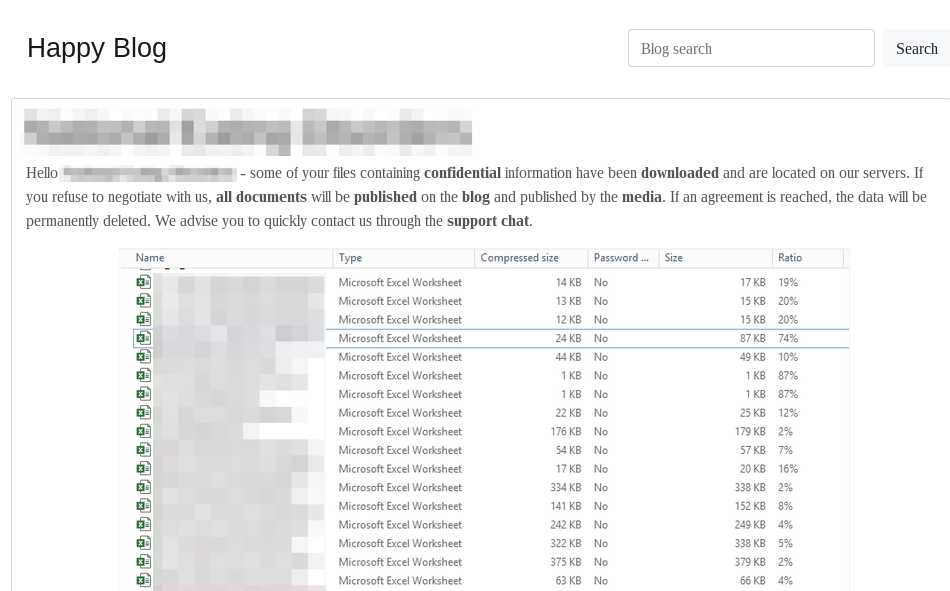
Not only has the number of eCrime dedicated leak sites grown, threat actors have also become more sophisticated in their methods of leaking the data. In general, eCrime adversaries will leak exfiltrated data slowly, saving what they perceive to be the most sensitive data for last in an effort to increase pressure on the victim organization to pay the extortion, rather than posting all of the exfiltrated data at once.
During several recent ransomware incidents, the eCrime adversaries, after deploying ransomware to the victim organization’s environment, have utilized stolen credentials to gain access to the victim organization’s email instance to send extortion-related emails to users demanding payment to prevent exfiltrated data from being leaked. In other instances, the eCrime adversaries have called and harassed employees of a victim organization following ransomware infection. Finally, CrowdStrike also observed threat actors increase pressure for payment with credible threats of distributed denial-of-service (DDoS) attacks if ransom payment is not received.
Ecrime Adversaries Collaborate
CrowdStrike has also observed formal collaboration among eCrime adversaries as well as shared tactics. In June 2020, the self-named “Maze Cartel” was created when TWISTED SPIDER, VIKING SPIDER and the operators of LockBit ransomware entered into an apparent collaborative business arrangement. After this occurred, leaks associated with VIKING SPIDER’s Ragnar Locker began appearing on TWISTED SPIDER’s dedicated leak site and Maze ransomware began deploying ransomware using common virtualization software, a tactic originally pioneered by VIKING SPIDER.
The Future of Ransomware
Over the last several years, eCrime adversaries that engage in BGH ransomware have advanced rapidly in terms of their capabilities and sophistication. It is reasonable to expect that this trend will continue at an accelerated rate with the same goal in mind – to apply as much pressure as possible to organizations to pay ever-larger extortion demands.
CrowdStrike expects that eCrime adversaries will continue to refine their data-leak extortion ransomware tactics, develop increasingly sophisticated exfiltration tooling that can be deployed widely, and automate data exfiltration by searching for, identifying and exfiltrating sensitive data by keyword.

CrowdStrike State of Ransomware Survey
CrowdStrike surveyed 1,100 global security leaders about ransomware. Discover what they had to say.
Download Now






