Stopping Ransomware Threats With The CrowdStrike Zero Trust Solution
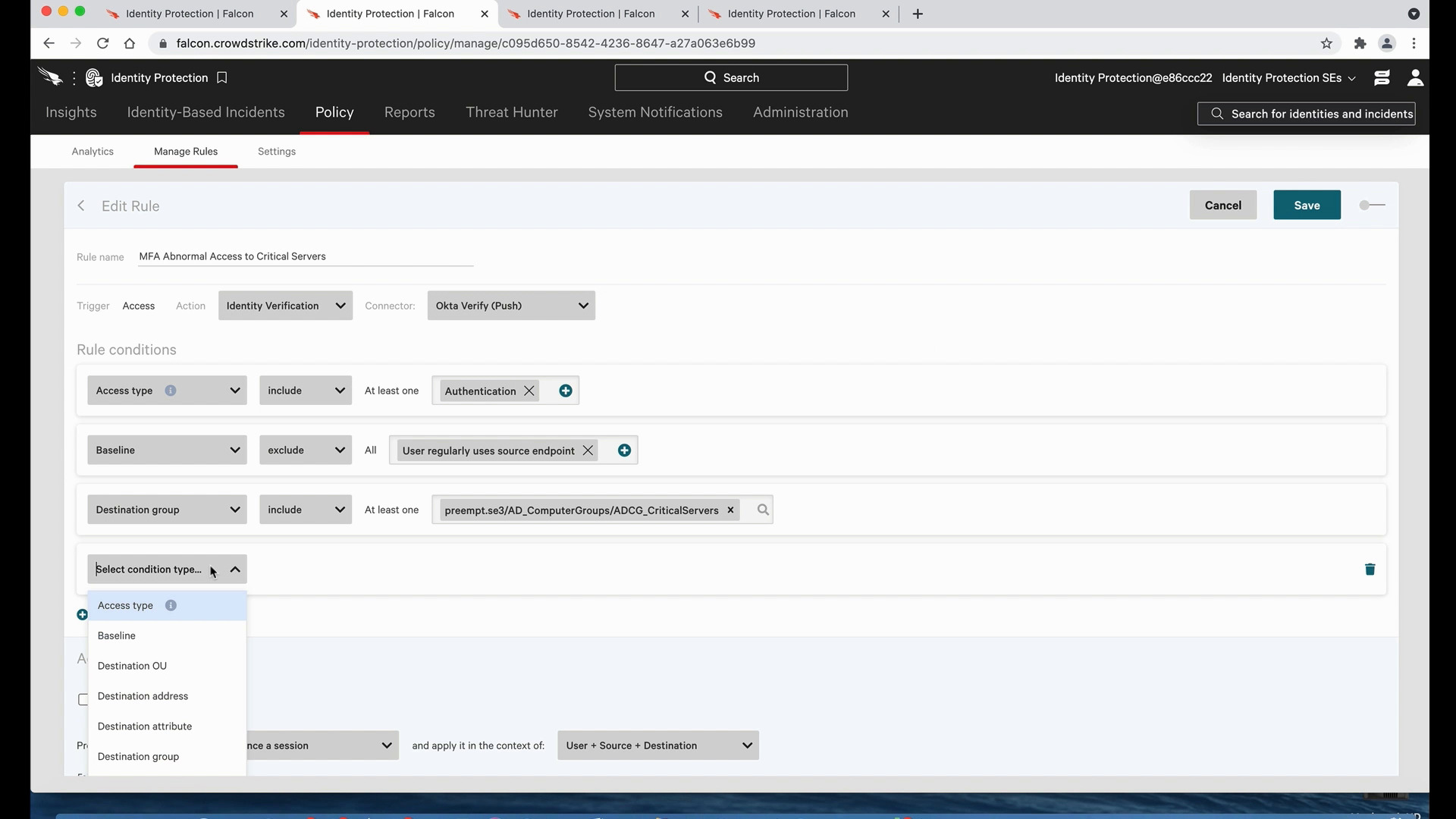
Modern attacks such as ransomware don’t typically linearly follow the kill chain. The attacks need not enter the organization through phishing attempts and then run the exploit on the endpoints. The ransomware attack can enter via compromised credentials, weak Active Directory security, or through vulnerable workloads, containers, or SaaS applications.
Watch this demo to see how the CrowdStrike Zero Trust solution can detect and stop ransomware threats in your organization.
Discover More at our
Resource Center
TECHNICAL CENTER
For technical information on installation, policy configuration and more, please visit the CrowdStrike Tech Center.
Visit the Tech Center