Reconnaissance Detection (Blue Team)
As we move through this Red Team vs. Blue Team series, our intent is to provide insight into both sides…
Open Source Active Reconnaissance (Red Team)
With the current threat landscape and likelihood of targeted attacks, organizations are dealing with myriad attempts to breach their network…
Moving beyond Indicators of Compromise (IOCs)
For the last few years, the security industry has become very enamored with Indicators of Compromise (IOCs) as a way to…
Using OS X FSEvents to Discover Deleted Malicious Artifacts
File System Events (FSEvents) in OS X 10.7+ introduced the capability to monitor changes to a directory. FSevents are logged…
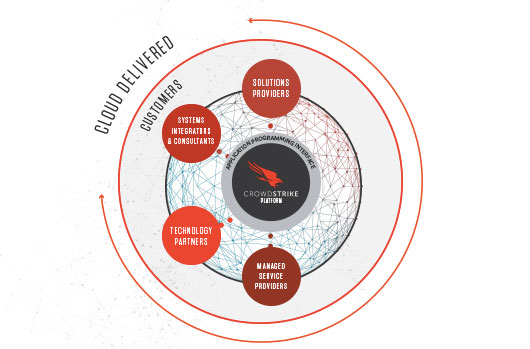
The Security Partner Ecosystem in a Cloudy World
I get excited when I see any technology that is built on a core platform that enables customers and partners…
Are You More Interested in Stopping a Breach or Stopping Malware?
This is a question I ask a lot of organizations that I speak with. While the obvious answer should be…
Can’t Protect Your Data from Ransomware? Think Again.
Read Video Transcript All too often, I hear from executives of large and small organizations that aside from targeted attacks,…
CrowdStrike Winter Release: What the !@#$ is next-generation?
I’d love to tell you about all the cool stuff in our Falcon platform winter release. It represents a huge…
Investigating PowerShell: Command and Script Logging
PowerShell is becoming ubiquitous in the Microsoft ecosystem, and, while it simplifies administration, it opens up a nearly unprecedented suite…
CrowdStrike’s 2015 Global Threat Report: Intelligence for the Business
Over the past several years an increasing number of organizations have turned to threat intelligence to counter the aggressions of…