What is a phishing attack?
Phishing is a type of cyberattack where threat actors masquerade as legitimate companies or individuals to steal sensitive information such as usernames, passwords, credit card numbers, and other personal details. These attacks typically occur through deceptive emails, text messages, phone calls, and other forms of communication that appear to come from trusted sources.
The goal of phishing is to trick unsuspecting victims into taking a specific action, such as clicking on malicious links, downloading harmful files, or sharing private information like login credentials. The effectiveness of phishing attacks stems from their use of social engineering techniques that exploit human psychology. These attacks create a sense of urgency, fear, or curiosity, prompting victims to act quickly without verifying the authenticity of the request.
As technology evolves, so do phishing tactics, making these attacks increasingly sophisticated and difficult to detect. Despite growing awareness and improved security measures, phishing remains one of the most prevalent and damaging forms of cybercrime. It is vital to understand phishing and know how to spot these scams to safeguard corporate and personal data in today's digital age.
How does phishing work?
We've all encountered some of the classic phishing tactics: an urgent security alert from IT, a revised vacation policy from HR, or a request to share a document. These attacks come in many forms. Phishing remains a favored method among cybercriminals due to its low cost and high success rate in gaining access to personal data and a company's systems.
Phishing attacks use social engineering techniques — like canvassing your social media feeds — to gather personal details and craft convincing messages. Attackers often impersonate executives, senior managers, or trusted supply chain partners to deceive targeted recipients into taking action on fraudulent requests.
Phishing attacks are carefully crafted to mimic the tone and style of legitimate communications, making them difficult to distinguish from genuine messages. These messages focus on pressing matters like authorizing a wire transfer, processing an invoice payment, or providing confidential information. The sense of urgency created in these communications compels recipients to act quickly without verifying the authenticity of the request, playing directly into the hands of the attackers. This combination of social engineering and urgency makes phishing attacks highly effective and a persistent threat to individuals and organizations alike.
The evolution of phishing attacks
Phishing attacks have evolved significantly over the years, adapting to technological advancements and becoming more sophisticated. Here’s a breakdown of their evolution:
Early phishing scams (mid-1990s)
Phishing attacks initially targeted individuals via email. Attackers sent deceptive messages that appeared to be from legitimate sources like banks or online services. These scams relied on basic social engineering tactics to trick recipients into disclosing personal information.
Introduction of spear-phishing and whaling (mid-2000s)
Phishing techniques became more sophisticated with new techniques like spear-phishing and whaling. Spear-phishing targets specific individuals or organizations with personalized messages, and whaling targets high-profile executives. These attacks are highly tailored for their target victims to exploit trust and manipulate human behavior.
Expansion to multiple platforms (2010s)
As internet usage grew and online platforms diversified, phishing tactics expanded to include social media, messaging apps, and mobile devices. Attackers used multi-platform attacks to reach a wider audience and increase their success rates.
Integration of advanced techniques (present)
Today, phishing attacks leverage new innovations such as AI to improve their effectiveness. With AI, fraudsters can communicate more clearly, scale their attacks, and send messages in any language. Large language models (LLMs) make it easy for adversaries to remove poor grammar and other idiosyncrasies from phishing emails, making them sound more like a native speaker.

2023 Threat Hunting Report
In the 2023 Threat Hunting Report, CrowdStrike’s Counter Adversary Operations team exposes the latest adversary tradecraft and provides knowledge and insights to help stop breaches.
Download NowTypes of phishing attacks
Email phishing
Email phishing, where attackers use email as the primary method to send malicious links or attachments, remains one of the most common forms of phishing techniques. These emails often appear to come from legitimate sources, such as banks, social media platforms, or online services, and they typically include urgent requests or enticing offers to trick recipients into clicking on malicious links or downloading infected attachments. For example, an email might impersonate a well-known bank, asking the recipient to update their account information by clicking on a link that leads to a fake login page designed to steal their credentials.
Spear-phishing
Spear-phishing is a targeted form of phishing attack where specific individuals or organizations are singled out with personalized messages. Attackers gather information about their targets from various sources, such as social media profiles or company websites, to craft convincing messages. Spear-phishing often contains details tailored to the recipient's interests, job role, or relationships within the organization. For instance, an attacker might send an email to an employee pretending to be their manager, requesting sensitive financial information to complete a supposed urgent transaction.
Whaling
Whaling attacks target high-level executives, such as CEOs or CFOs, to gain access to substantial confidential data or financial assets. Attackers exploit the authority and trust associated with these positions to deceive recipients into complying with their requests. For example, an attacker might pose as the CEO and send an email to the CFO requesting an urgent wire transfer for a business acquisition, bypassing normal authorization processes and exploiting the CFO's desire to act quickly on the CEO's instructions.
Smishing and vishing
SMS phishing (smishing) and voice phishing (vishing) are phishing attacks conducted via SMS messages and voice calls, respectively. Smishing involves sending text messages that appear to be from legitimate sources, often containing links to malicious websites or instructions to call a fraudulent phone number. Vishing uses phone calls to deceive victims into revealing sensitive information like passwords or credit card numbers. For instance, a vishing attack might involve a scammer posing as a bank representative and calling a victim to request verification of their account details over the phone.
Social media phishing
Social media phishing attacks target users on social networking platforms by sending direct messages or posts containing malicious links. Attackers may create fake profiles or hack into legitimate accounts to spread phishing links or messages that appear to come from friends or trusted contacts. These messages often lead to malware-infected websites or fake login pages designed to steal users' credentials.
Application phishing
Application phishing, also known as in-app phishing, targets users through legitimate applications. Attackers create fake login screens or malicious pop-up messages within legitimate applications to trick users into entering their login credentials or personal information. This form of phishing exploits users' trust in the application and can lead to unauthorized access to their accounts or devices.
Learn More
Read this post to learn about the difference between a phishing attack and spoofing attack to stay informed on different ways adversaries can get to you.
How to recognize phishing attacks
Common characteristics
Phishing emails have several common characteristics that can help you identify them.
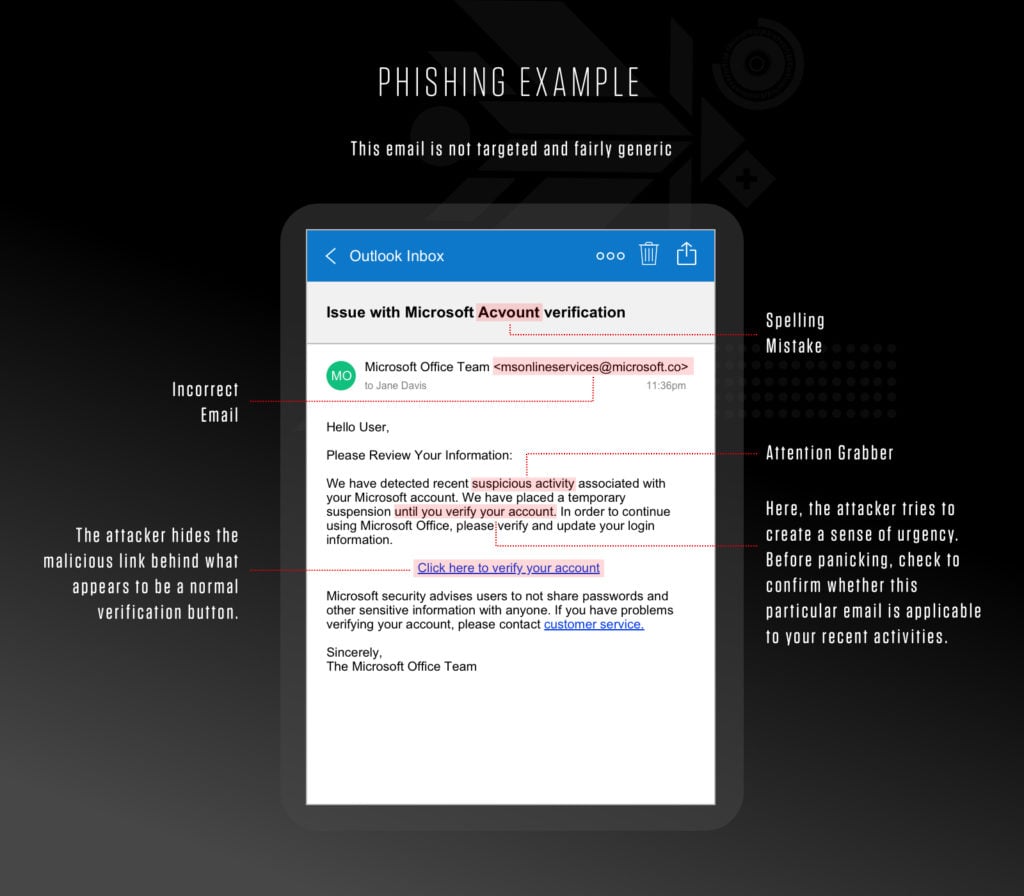
Typical signs include:
- Urgent language that creates a sense of immediate action required
- Spelling and grammatical errors, which are often indicative of a hastily composed message
- Generic greetings like "Dear User" instead of personalized salutations
- Threats of consequences if action is not taken immediately
- Requests for personal information, such as usernames, passwords, or credit card numbers
- Suspicious links that do not match the legitimate website address or use URL shorteners
- Unexpected attachments, especially executable files (i.e., .exe files) or .zip files
- Messages that appear to come from a legitimate organization but have a slightly altered domain name (e.g., amaz0n.com instead of amazon.com)
- Lack of contact information or a way to reach the sender outside of email
- Too-good-to-be-true offers or prizes that require personal information to claim
Analyzing URLs and domain names
Analyzing URLs and domain names is crucial for spotting phishing attempts. Here are some key practices you should use:
- Scrutinize the web address: Look for subtle misspellings or variations in domain names that may resemble legitimate sites. For example, a phishing attempt might use a domain like “www.amaz0n.com,” replacing the letter "o" with a zero
- Check for HTTPS: Ensure the site is secure by checking for "https://" in the URL. Legitimate websites use HTTPS to encrypt data sent between the website and the user.
- Avoid shortened URLs: Avoid clicking on shortened URLs (e.g., bit.ly, t.co) that may redirect you to malicious websites. Always try to visit the full URL to verify its authenticity.
Verification techniques
Verifying the authenticity of messages and senders is essential to avoid falling victim to phishing attempts. Here are some effective methods you should use:
Contact organizations directly: Always use official contact information obtained independently to verify the legitimacy of requests. For example, if you receive an email requesting sensitive information, such as a password reset or financial details, contact the organization directly using contact information from a trusted source like their official website.
Verify requests for personal information: Be cautious of any email, phone call, or message that requests personal information. Legitimate organizations typically do not ask for sensitive information via email or phone without prior arrangement.
- Scrutinize sender information: Carefully check the sender's email address and name. Phishing emails often use spoofed email addresses or names that resemble legitimate entities but have slight variations.
Learn More
Read this 101 to see more examples of phishing emails and become more proficient at spotting a phishing email.
How to prevent a phishing attack
To protect yourself and your organization from phishing attacks, you must take proactive measures and stay vigilant. Here are some best practices that will help keep you safe:
Train your employees: Educate your employees to recognize and promptly respond to phishing attempts. Encourage them to report suspicious emails to your corporate security team.
Use an endpoint protection solution: Anti-malware tools scan devices to prevent, detect, and remove malware that enters the system through phishing attacks.
Use an email security solution: Email security solutions use predefined blocklists created by expert security researchers to automatically block malspam delivery or move malspam emails to a junk folder.
Use an up-to-date browser and software: Regardless of system or browser, make sure to always use the latest version. New and innovative attacks are launched all the time, so constantly patching and updating the organization’s solutions will provide stronger defenses against malspam threats.
Never reply to spam: Responding to phishing emails lets cybercriminals know that your address is active. They will then put your address at the top of their priority lists and continue to retarget it.
Use multi-factor authentication (MFA): MFA adds an extra layer of security by requiring a second form of verification, such as a code sent to a mobile device, to access sensitive accounts.
Don’t open suspicious emails: If you believe you have a phishing email in your inbox, do not open it, and report it through the proper channels. Employees can report suspicious emails to their organizations’ IT departments, and they can also be good internet citizens by forwarding the emails to the U.S. government’s Cybersecurity and Infrastructure Security Agency (CISA) at phishing-report@us-cert.gov.
Check for domain abuse: Criminals often abuse existing brand and domain names (e.g., amaz0n.com). Security teams need to check on a continuous basis for potential abuse of their domain names as well as the domain names of some of their key business partners. If a malicious domain has been spotted, please send a takedown request to the domain service provider.
Learn More
As cybercrime of all kinds, and phishing, in particular, reaches new heights in 2023, it’s important for every person in your organization to be able to identify a phishing attack and play an active role in keeping the business and your customers safe.
What to do if you fall victim to phishing
Immediate actions
If you fall victim to a phishing attack, it's crucial to act quickly to mitigate the damage. Here are the steps you should take:
1. Change your passwords
Immediately change the passwords for all affected accounts, especially those that may have been compromised. Use strong, unique passwords and consider using a password manager to keep track of them.
2. Notify banks and relevant authorities
Contact your bank and other financial institutions to inform them of the potential breach. They can monitor your accounts for suspicious activity and help protect your funds.
3. Check your accounts
Review all your accounts for unauthorized transactions or changes. Report any suspicious activity to the respective institutions right away.
4. Enable two-factor authentication (2FA)
Add an extra layer of security to your accounts by enabling 2FA, which requires a second form of verification to access your accounts.
5. Track potential data or personally identifiable information (PII) leakage
If accounts have been compromised, use a digital risk protection solution to search the dark web, criminal forums, or underground communities for leaked credentials or private data. Access brokers monetize stolen credentials and sell them via specialized underground channels.
6. Disconnect from the internet
If you believe malware has been installed on your device, disconnect it from the internet to prevent further unauthorized access or data transmission.
Reporting phishing attacks
Reporting phishing attacks to the appropriate authorities is essential for combating these cyber threats. Here’s how to do it:
1. Report the attack to the Federal Trade Commission (FTC)
Visit the FTC’s website to file a report. Providing detailed information helps the FTC track and combat phishing scams.
2. Notify internet service providers (ISPs)
Inform your ISP about the phishing attack. They can take steps to block the malicious emails and investigate the source.
3. Report the attack to an anti-phishing organization
Use platforms like the Anti-Phishing Working Group (APWG) to report phishing attempts. They collect data and work to reduce the prevalence of phishing attacks.
4. Inform your organization
If the phishing attack occurred at work, notify your IT department or security team immediately. They can take measures to secure the network and prevent further incidents.
Recovery and damage control
After taking immediate actions and reporting the attack, focus on recovery and limiting any potential damage:
1. Contact credit reporting agencies
Notify major credit reporting agencies like Equifax, Experian, and TransUnion about the phishing incident. They can place fraud alerts on your credit file to prevent identity theft.
2. Monitor for identity theft
Regularly check your credit reports and bank statements for signs of identity theft. Consider enrolling in an identity theft protection service for ongoing monitoring.
3. Secure your devices
Run a full security scan on all affected devices using reputable antivirus and anti-malware software. Remove any detected threats to ensure your devices are secure.
4. Educate yourself
Learn more about phishing techniques and how to protect yourself from future attacks. Staying informed can help you recognize and avoid potential threats.
By taking these steps, you can mitigate the impact of a phishing attack and better protect yourself and your organization from future incidents.
Learn More
Read this blog to learn how you can stop phishing attack with Falcon Next Gen SIEM and SOAR.
Future trends in phishing
The role of AI in phishing and anti-phishing efforts
AI is playing a significant role in both enhancing phishing attacks and bolstering defenses against them. On the attacker’s side, AI is used to craft more convincing phishing emails by analyzing and mimicking the language patterns of native speakers. AI can eliminate grammar and spelling errors as well as other telltale signs that typically make it easy to spot phishing attempts. As a result, bad actors are able to create phishing messages that are more difficult to identify at a glance. Additionally, AI algorithms can personalize attacks by analyzing social media profiles and other online data to create highly targeted and convincing phishing messages.
On the defensive side, cybersecurity professionals are leveraging AI to combat phishing. AI-powered anti-phishing tools can analyze vast amounts of data in real time to identify and block phishing attempts. These tools use machine learning algorithms to identify patterns and anomalies that indicate phishing, providing faster and more accurate detection than traditional methods. AI is also used in training programs to simulate phishing attacks, helping employees learn to recognize and respond to phishing threats more effectively.
Emerging threats and innovations in phishing tactics
As technology evolves, so do phishing tactics. One of the most concerning emerging trends is the use of deepfake technology. Deepfakes use AI to create highly realistic fake audio and video content. Cybercriminals can use deepfakes to impersonate executives, colleagues, or other trusted individuals, adding a new layer of deception to phishing attacks. For example, an attacker could create a deepfake video of a CEO instructing an employee to transfer funds to a fraudulent account, making the request seem authentic.
The integration of AI and deepfake technology into phishing tactics represents a significant challenge. As these technologies continue to develop, it will be crucial for organizations to stay ahead by implementing advanced security measures and continuously educating their employees about these evolving threats.
Stay vigilant
As phishing tactics continue to evolve, staying informed and proactive is crucial. Adopting robust security measures is essential in protecting yourself and your organization from these increasingly sophisticated attacks. And one of the most effective defenses against phishing lies in ongoing education and awareness.
Encourage a culture of vigilance where everyone is empowered to recognize, report, and avoid falling victim to phishing attempts. By staying informed about the latest threats and best practices, we can collectively combat phishing and create a safer digital environment for all.
Protecting from phishing attacks with CrowdStrike
Protecting from a phishing attack starts with following the prevention tips listed above. Nevertheless, organizations find a lot of value in having a tool or service that aids protection.
Don’t wait until you are phished to find the right solution for your business. With CrowdStrike Falcon® Complete managed detection and response (MDR), you can stop breaches on endpoints, workloads, and identities with expert management, threat hunting, monitoring and remediation.

Harnessing Email Data to Stop Phishing Attacks with Falcon Next-Gen SIEM
Read this post to learn how CrowdStrike Falcon® Next-Gen SIEM helps security teams detect and stop phishing threats.
Read Now





