Customers protected by Falcon Data Protection







Advanced data protection for the modern enterprise
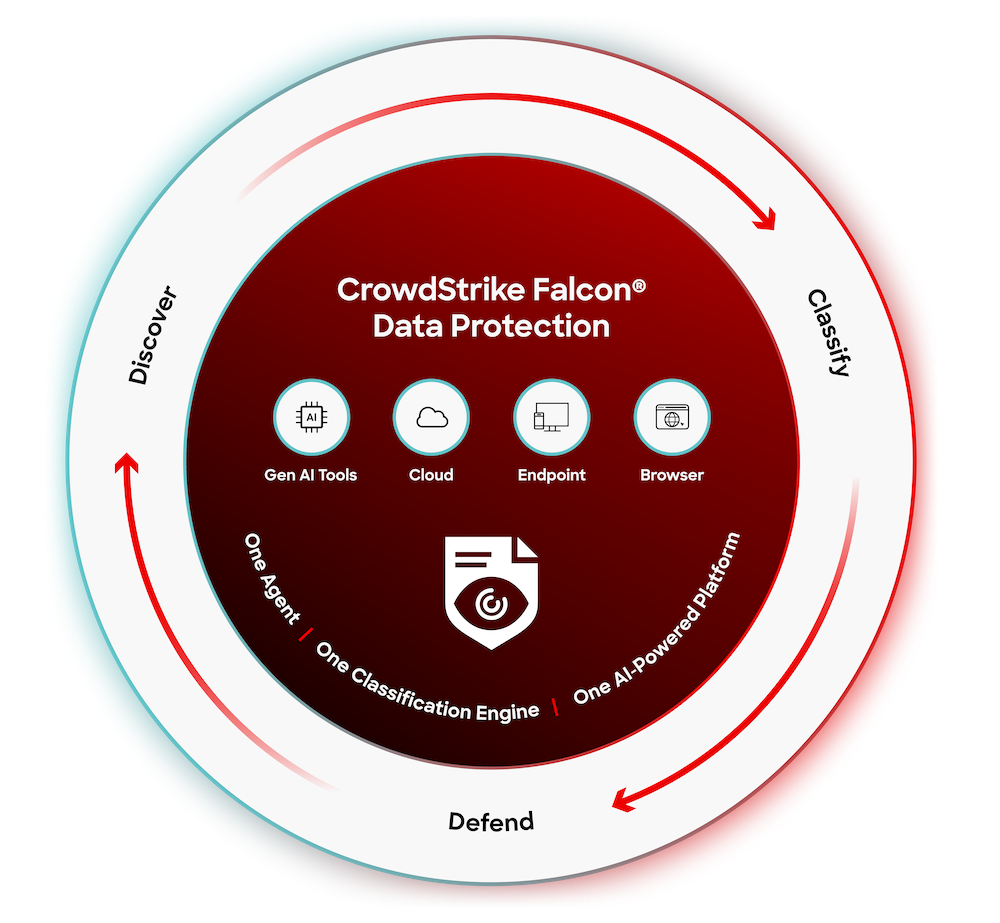
The industry’s only unified platform for data protection built on a unified agent and single console.
One agent. Instant visibility. Full control.
Deploy at scale with the Falcon platform’s unified agent and instantly gain visibility into sensitive data movement. Experience minimal configuration, no added infrastructure, and see known and unknown egress paths the moment protection is turned on.


Resting or moving, your data’s always a target
Continuously monitor sensitive data at rest and in motion across cloud infrastructure and endpoints. Detect unauthorized access and anomalies before data is exposed, and enforce security policies to stop adversaries and insiders before they succeed.
Where the insider sits, the threat begins
Prevent malicious insider attempts with encryption detection and security policy enforcement. Falcon Data Protection for Endpoint ensures seamless protection across Windows and macOS endpoints without complex configurations or added overhead.


Cloud runs at runtime. So should your protection.
Monitor data movement inside cloud infrastructure in real time. Falcon Data Protection for Cloud (beta) uses eBPF to monitor unauthorized data movement at runtime without added infrastructure and with minimal performance impact.
GenAI is the new insider threat vector
Prevent insiders from accidentally sharing sensitive data with GenAI tools. Falcon Data Protection for Endpoint tracks and blocks insider-driven data leaks to personal and corporate GenAI tools in real time, enforcing policies based on content type, source origin, and file type.

Customer Stories
See why organizations trust Falcon Data Protection.
What's New
1CrowdStrike 2025 Global Threat Report
2Benefits of Falcon Data Protection as realized by the CISO of a top-tier business school in the US