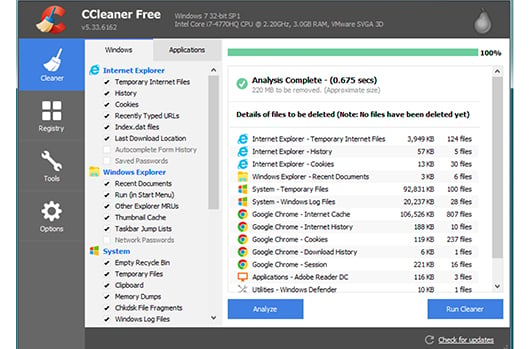
Protecting the Software Supply Chain: Deep Insights into the CCleaner Backdoor
The term “supply chain attacks” means different things to different people. To the general business community, it refers to attacks…
HIPAA PHI Getting Tougher to Safeguard but Compliance is Still Critical
The Health Insurance Portability and Accountability Act (HIPAA) has big consequences for organizations of all sizes. Companies and institutions that…
Why Cybersecurity Must Be a Board-Level Discussion
“What you don’t know will hurt you.” That’s the topic of a recent SC Magazine article by CrowdStrike CEO George…
Effective Cybersecurity Requires a “Hygiene-First” Approach
Although the frequency and damaging nature of breaches are realities today’s organizations must face, the announcement of what caused the…
The Right Endpoint Detection and Response (EDR) Can Mitigate Silent Failure
In a recent webcast, “The Maturing of Endpoint Detection and Response (EDR): Choosing the Right Solution,” Forrester Senior Analyst Chris…
Webcast Offers Critical Factors for Effective Endpoint Detection and Response (EDR)
In a recent webcast, “The Maturing of Endpoint Detection and Response (EDR): Choosing the Right Solution,” Forrester Senior Analyst Chris…
Address Zero-Day Threats Long Before an Attack Occurs
A recent interview with CrowdStrike VP of Product Marketing Dan Larson, for the CyberWire Daily Podcast, focuses on “zero-day” attacks…
New York State Cybersecurity Regulations for Financial Institutions are Tough, Critical, and Reach Beyond State Borders
Given today’s global cyber threatscape, the increased amount of targeted attacks against the financial sector — and New York City’s…
Decrypting NotPetya/Petya: Tools for Recovering Your MFT After an Attack
Making the world a better place has always been a core goal of CrowdStrike. In this blog post, we are…
CrowdStrike Falcon Endpoint Protection Receives Five Stars Across the Board in SC Magazine Evaluation
The CrowdStrike Falcon platform recently participated in a group evaluation by SC Magazine’s testing team, a U.S.-based team that includes…