Four Steps to Choosing the Right Antivirus Replacement
Few security experts would dispute the fact that legacy antivirus (AV) solutions are no match for today’s most stealthy and…
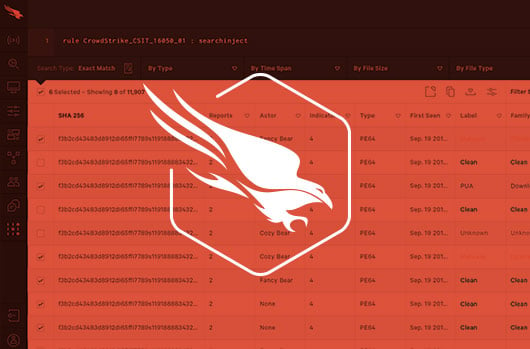
CrowdStrike Summer Release 2017: Falcon Search Engine Brings Speed and Agility to Cybersecurity
Today we are proud to announce the CrowdStrike Falcon® Search Engine, the largest and fastest search engine exclusively for cybersecurity…
Webcast Unpacks Fileless Attacks and Explains What it Takes to Fight Them
A new webcast, “Understanding Fileless Attacks and How to Stop Them,” explains the rise in fileless attacks and why this…
Visit CrowdStrike at Black Hat 2017
This year marks a 20-year milestone for Black Hat, one of the cybersecurity industry’s signature events. Originally an offshoot of…
Achieving Cybersecurity Effectiveness in a World of Advanced Threats
CrowdStrike CEO and co-founder George Kurtz was featured In a recent Forbes article, Security Advice from the CEO of the…
When Worlds Collide: The Impact of Cyber Threats Crossing Over to the Physical World
A recent article in Information Age, titled “As the digital and physical worlds collide it’s time for a security refresh,”…
NotPetya Technical Analysis Part II: Further Findings and Potential for MBR Recovery
Update: Due to naming convention consistency in the industry, CrowdStrike is now calling this variant of Petya - NotPetya. Executive…
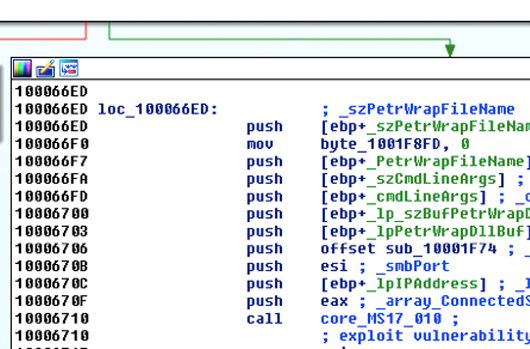
NotPetya Technical Analysis – A Triple Threat: File Encryption, MFT Encryption, Credential Theft
Update: Due to naming convention consistency in the industry, CrowdStrike is now calling this variant of Petya - NotPetya. Executive…
CrowdStrike CEO and Co-founder George Kurtz Wins Ernst & Young Entrepreneur of the Year for Security
CrowdStrike® added a prestigious award to its many achievements when CEO and co-founder, George Kurtz, was named Ernst & Young…
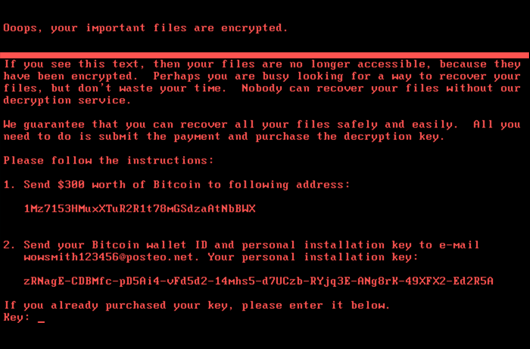
CrowdStrike Protects Against NotPetya Attack
Update: Due to naming convention consistency in the industry, CrowdStrike is now calling this variant of Petya - NotPetya. On…