CrowdStrike Counter Adversary Operations defined
Created in the summer of 2023, CrowdStrike Counter Adversary Operations (CAO) united two teams: the CrowdStrike Intelligence team and the CrowdStrike® Falcon OverWatch® threat hunting team. This first-of-its-kind team was formed with the goal to disrupt today’s adversaries and ultimately raise their cost of doing business.
CrowdStrike Counter Adversary Operations delivers four modules: Falcon Adversary OverWatch, CrowdStrike Falcon® Adversary Intelligence, CrowdStrike Falcon® Adversary Intelligence Premium, and CrowdStrike Falcon® Counter Adversary Operations Elite.
Why do security teams need threat intelligence and threat hunting? Why is traditional threat intelligence insufficient?
Today’s adversaries are increasingly fast and elusive, with rapidly changing motives and tactics. The combination of threat intelligence and threat hunting is essential to detect, disrupt, and stop adversaries.
Threat intelligence informs security teams with the latest adversarial insights so they can proactively adjust protections. Unfortunately, many security teams are overloaded with threat alerts and remain slow to translate threat intelligence to the right context for detection, investigation, and response. This unnecessary delay provides adversaries an opportunity to bypass detections and infiltrate the network.
Threat hunting fills this gap by proactively searching for cyber threats that are lurking undetected in a network. Cyber threat hunting demands robust telemetry to find malicious actors in your environment that have slipped past your initial security defenses. It only takes adversaries minutes to move laterally within a network(1), which is why threat hunting is an essential component of any defense strategy.
Many organizations do not have the resources or skills necessary to perform threat hunting, giving adversaries the chance to infiltrate, traverse laterally, and compromise confidential data without encountering any obstacles.
(1) CrowdStrike 2024 Global Threat Report; Fasted Recorded eCrime Breakout time 2 min and 7 seconds
What do teams need to fix these inefficiencies in threat intelligence and threat hunting?
To avoid these inefficiencies, security organizations need to have real-time intelligence on adversaries’ tools, techniques, and tradecraft and instantly apply that information to their environment and tools. A tight, continuous feedback loop of global adversary insights — refined with threat activity from local threat hunts — gives defenders visibility into adversarial activities related to their environment. These refined insights are more relevant and enable security teams to better detect, investigate, and disrupt threats before and during an attack.
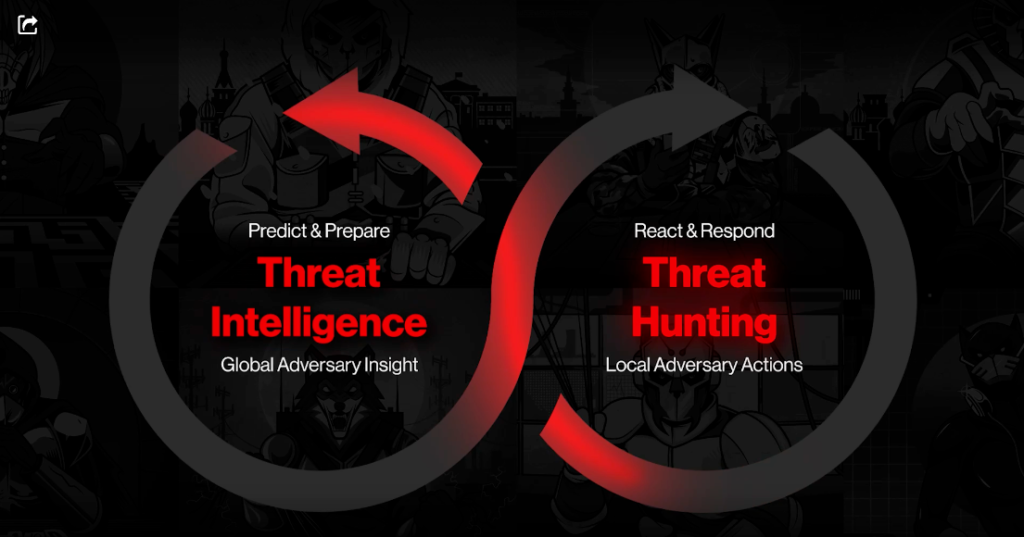
Benefits of unifying insights from threat intelligence and threat hunting
The combination of threat intelligence and threat hunting enables security teams to obtain full visibility into attack activity both inside and outside their network. This empowers them to expedite detections and deploy countermeasures more rapidly, ultimately improving their security posture.
Global threat insights — derived from real-world attacks — provide security teams an understanding of what may happen to them and help these teams predict adversary attacks. Insights derived from local threat hunts complement this global visibility with information about what is happening to them now.
This combination of global threat intelligence and insights from local threat hunting benefits multiple teams inside the security organization. Let’s take a look.
- In-depth technical details on the latest attacks provide security engineers the necessary context to deploy comprehensive detection and prevention policies.
- Insights into the latest discovered adversary behaviors gives threat hunters new leads on what to hunt for, resulting in faster and more effective hunts.
- Real-time threat context helps SOC analysts prioritize alerts and accelerate investigations, resulting in faster and more efficient risk mitigation.
- Providing attribution and detailed threat actor profiles enables responders to effectively eliminate malicious activities by helping them understand all pertinent behaviors and vulnerabilities being exploited.
- Security planners and decision-makers get trusted strategic insights into threats along with trends and industry-specific reports. This knowledge enables them to assess their risk posture and formulate security strategies, resulting in an enhanced return on investment.
Learn More
Adversaries are getting faster, so if you aren’t being proactive, you’re already too late. Watch how CrowdStrike Counter Adversary Operations unifies our industry-leading threat intelligence and hunting teams with integrated offerings to stop modern breaches and raise adversaries’ cost of doing business.
What security problems does Counter Adversary Operations address?
Adversaries are faster and more sophisticated than ever before, and defenders can’t keep up, leaving them vulnerable to breaches. Without the right protections in place, defenders risk damage to their brand, reputation, and financial standing. There are several reasons behind these threat risks:
- Security tools are not infallible: Actors like to hide in the gaps between different tools. Security teams are looking to reinforce security solutions with threat hunting across endpoint, identity, cloud, and the criminal underground to keep pace with sophisticated threats.
- Security teams are wasting resources: Despite major investments in legacy tools — like legacy security information and event management (SIEM) solutions — security teams struggle to realize the value they are hoping for. Poor detection guidance and high false positives lead to lost analyst and security engineering time.
- Skilled security teams are expensive: Advanced cyber teams are expensive, and few organizations can staff a dedicated threat intelligence or threat hunting team. And many organizations that can afford advanced cyber teams are unable to adapt to evolving threats and remain stuck with irrelevant or out-of-date intelligence.
What do organizations need to solve these problems?
To better detect and understand existing security events, security teams need reliable and comprehensive threat intelligence providing real-time context to reduce the attack surface, improve defenses, guide threat hunters and detection engineers, and update leadership.
This context must be seamlessly available in the analysts’ daily workflows to accelerate understanding and decision-making. Automation becomes critical to shorten the time between detecting, investigating, and responding to incidents and instantly deploying countermeasures.
Smaller organizations that lack resources need a cost-effective solution. They must acquire the skills and visibility required to protect against modern attacks, as relying solely on individual security controls leaves them vulnerable.
CrowdStrike CAO offerings
CrowdStrike Counter Adversary Operations empowers security teams to defend against adversaries by providing a mix of AI and human expertise, automation, and world-class threat insights.
- CrowdStrike Counter Adversary Operations threat experts hunt adversaries for you with AI and cutting-edge intelligence to track every attacker’s move in real time across customer endpoints, cloud, and identity data. CrowdStrike CAO applies these findings to your environment, and real-time alerts ensure you stay informed about any threat.
- CrowdStrike CAO helps security teams accelerate investigation and response time so they can focus their attention on stopping threats before the breach.
- CrowdStrike Counter Adversary Operations provides trusted, industry-leading insights to fortify defenses, disrupt attacks, and raise costs for the adversary.
How are these capabilities offered?
CrowdStrike offers four modules that bring together elite CrowdStrike threat hunters and industry-leading threat intelligence — an industry-first combination with unmatched power to pursue and stop adversaries. These offerings are built to hunt down threat actors, accelerate investigation and response time, and fortify defenses:
- CrowdStrike Falcon Adversary OverWatch: Around-the-clock protection across endpoint, identity, and cloud workloads is delivered by AI-powered threat hunting experts, and built-in threat intelligence exposes adversary tactics, vulnerabilities, and stolen credentials.
- CrowdStrike Falcon Adversary Intelligence: End-to-end intelligence automation cuts response time across the security stack and empowers security teams to instantly submit potential threats to an AI-powered sandbox, extract indicators of compromise, and deploy countermeasures — all while continuously monitoring for fraud and protecting your brand, employees, and sensitive data.
- CrowdStrike Falcon Adversary Intelligence Premium: World-class intelligence reporting, technical analysis, and threat hunting and detection libraries enable organizations to lower the time and cost required to understand and defend against sophisticated nation-state, eCrime, and hacktivist adversaries.
- CrowdStrike Falcon Counter Adversary Operations Elite: The industry’s first and only white-glove service created to rapidly disrupt sophisticated adversaries with the fusion of industry-leading intelligence and threat hunting. CrowdStrike’s Counter Adversary Operations assigned analysts will use advanced investigative and threat hunting tools to identify and disrupt adversaries across the customer IT environment and beyond.
Business and security outcomes with CrowdStrike Counter Adversary Operations offer
CrowdStrike Counter Adversary Operations provides multiple business and security outcomes, such as reduction in research time, workload, and staffing costs as well as improved security posture.
Listed below are the distinct business value metrics derived from customer interviews after implementing one of the CrowdStrike Counter Adversary Operations modules:
- 95% avoidance in threat hunting staffing costs(1)
- 97% reduction in time researching adversaries and emerging threats(1)
- 85% reduction in researching new alerts(1)
- 80% increase in security posture(1)
(1)CrowdStrike Business Value Assessments (BVAs). CrowdStrike BVA numbers are projected estimates of average benefits based on recorded metrics provided by customers during pre-sale motions that compare the value of CrowdStrike with the customer's incumbent solution. Actual realized value will depend on individual customer's module deployment and environment.
Who can benefit from Counter Adversary Operations?
The CrowdStrike Counter Adversary Operations portfolio is designed for organizations of all sizes, verticals, and regions, providing easy-to-consume modules that combine intelligence and threat hunting expertise to pursue adversaries and stop breaches.
For small and medium-sized businesses (SMBs), Falcon Adversary OverWatch helps organizations achieve 24/7 protection across endpoint, identity, and cloud workloads that would otherwise be too expensive.
CrowdStrike Falcon Adversary OverWatch
Enterprises with a SOC can optimize the effectiveness of their entire enterprise security stack through automated intelligence orchestration, context enrichment, and AI-powered investigative tools with Falcon Adversary Intelligence.
CrowdStrike Falcon Adversary Intelligence
For the most mature organizations with dedicated threat hunting and detection teams, Falcon Adversary Intelligence Premium enables security teams to enhance cybersecurity controls and shape their security strategy to stop breaches more effectively.








