What is PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) is a framework developed by the Payment Card Industry Security Standards Council (PCI SSC) to help secure and protect all payment card account data.
Launched on September 7, 2006, PCI DSS defines baseline technical, physical, and operational security controls necessary for protecting payment card account data.
The standards apply to any organization that stores, processes, or transmits cardholder data (CHD), including merchants, payment processors, issuers, acquirers, service providers or any other entity within the payment card ecosystem.
In addition to securing data itself, PCI DSS security requirements also apply to all system components included in or connected to the cardholder data environment (CDE). This includes people, processes, and technologies that store, process, or transmit cardholder data or sensitive authentication data.
What is payment card data?
PCI DSS defines two categories of payment account data:
- Cardholder data (CHD) that includes primary account number (PAN), cardholder name, expiration date, and service code; and
- Sensitive authentication data (SAD) that includes full track data (magnetic-stripe data or equivalent on a chip), card security code (CAV2/CVC2/CVV2/CID), and PINs/PIN blocks.
Is PCI compliance required by law?
No. PCI DSS is not reviewed or enforced by any government agency, nor is it enforced by the PCI SSC. Rather, compliance is determined by individual payment brands and acquirers based on the terms of the contract or agreement signed by the merchant or service provider with the card network.
However, while compliance with PCI DSS is not a legal matter, failure to comply with PCI DSS can result in significant fines as well as restrictions on use of payment platforms in the future.
Learn More
Learn how CrowdStrike can help you meet requirements from compliance and certification frameworks that are critical in ensuring the safe, smooth and compliant operation of your business.
The 12 PCI Compliance Requirements
PCI DSS defines 12 requirements designed to address six objectives:
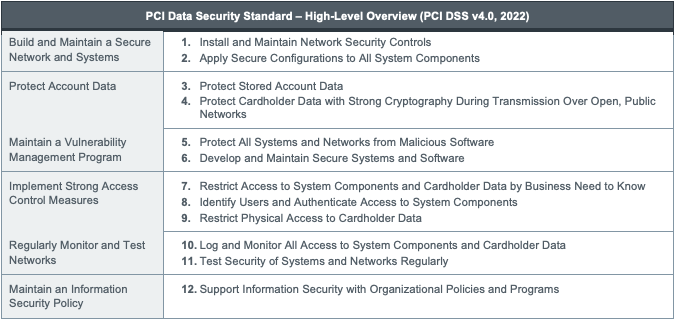 Source: PCI Security Standards Council
Source: PCI Security Standards CouncilRequirement 1: Install and maintain network security controls
Network security controls (NSCs) are policy enforcement points that control traffic between two or more subnets based on predetermined rules. Examples of network security controls include firewalls and VPNs. Specific requirements include making sure that all services, protocols, and ports that are allowed to ingress have been identified, approved, and properly defined.
Requirement 2: Apply secure configurations to all system components
Apply secure configurations to system components to reduce the ways an attacker may compromise the system. Because malicious actors often use default passwords that might be available to the public, it is essential to change them as soon as possible. Additionally, remove unnecessary software, functions, or accounts from the network and disable irrelevant services to significantly reduce attack surfaces.
Requirement 3: Protect stored account data
In the unwanted case of a breach into the network, there are a number of methods meant to protect critical account data from attackers intending to access it. Some of these methods include:
Requirement 4: Protect cardholder data with strong cryptography during transmission over open, public networks
To preserve the integrity and confidentiality of data, it is essential to use strong cryptography measures. For instance, personal area networks need encryption during transmissions where malicious actors can easily access the network, such as transmissions over public networks. These malicious actors tend to exploit network vulnerabilities to gain privileged access and escalate from there.
Requirement 5: Protect all systems and networks from malicious software
PCI DSS requires companies to deploy antivirus software from a reputable cybersecurity provider on all systems commonly affected by malicious software. This applies to all endpoints — even those that may not be used to process or store cardholder data, since malware attacks can originate and spread from any device.
Organizations must also ensure that the antivirus software is active, up-to-date, and fully operational by conducting regular scans.
Requirement 6: Develop and maintain secure systems and applications
This requirement is focused on defining and implementing the underlying policies and processes that enable the organization to quickly identify and assess the risk of security vulnerabilities within the data environment; it also dictates actions that must be taken to remediate such risks. A core component of this requirement is limiting potential vulnerabilities by deploying critical patches and updates to all systems, applications, and endpoints.
According to this requirement, organizations should also incorporate security requirements in all phases of the development process.
Requirement 7: Restrict access to system components and cardholder data by business “need-to-know”
Access management is one of the most critical components in ensuring your network is protected from unauthorized access that can have detrimental effects on your company and data integrity. The core of access management involves the creation of rules that provide specific users with access to specific applications or data and for specific purposes only. For this, ensure all users have the right amount of privileged access to data and applications. Adopt the principle of least privilege (POLP), which states you should only provide a user with the minimum level of privileged access needed to perform their job duties.
Requirement 8: Identify users and authenticate access to system components
The two fundamental principles of this requirement include establishing the identity of a user of a process on a computer system and verifying the user is indeed associated with the identity they are claiming.
Using unique IDs (or preventing account sharing between several users) not only limits exposure but helps the organization trace the chain of events when a breach occurs. This makes it easier to respond and contain a data breach and determine its origin and progression.
This requirement also states that multi-factor authentication (MFA) is required for any user to access cardholder data environments.
Requirement 9: Restrict physical access to cardholder data
This requirement focuses on the physical security of cardholder data. According to this standard, all hard copies of CHD (such as paper files or hard drives) must be retained in a secure physical location. Access should be granted only to those with the necessary privileges; an access log should be maintained.
Additional security measures related to this requirement include:
- Installation of video cameras and/or electronic access controls at the physical location
- Retention of access logs and recordings for at least 90 days
- Development of access protocols that allow the organization to authenticate authorized users
- Application of additional security measures to all portable assets that contain CHD
Requirement 10: Log and monitor all access to system components and CHD
One of the most common examples of noncompliance with PCI DSS relates to failing to keep proper records and supporting documentation of when sensitive data was accessed and who did so.
According to this requirement, any action pertaining to CHD or PANs should be logged using a time-stamped tracking tool from a reputable software provider. These logs should then be sent to a centralized server where they are reviewed daily for anomalous behavior or suspicious activity.
Implementation of security information and event management (SIEM) — a set of tools and services that help organizations manage data logs and analyze this data to recognize potential security threats and vulnerabilities before a breach occurs — can help organizations manage this particular PCI DSS requirement.
Requirement 11: Test security systems and networks regularly
This requirement focuses on testing the software applications, security measures, or other tools outlined in the previous 10 requirements to ensure overall compliance.
Specific requirements include but are not limited to:
- Conducting quarterly scans of all wireless access points
- Conducting quarterly vulnerability scans
- Conducting annual application and network penetration testing on all external IPs and domains
- Conducting regular web traffic and file monitoring
Requirement 12: Support information security with organizational policies and programs
The final PCI DSS requirement focuses on creating an overarching information security policy for employees or other stakeholders. This standard explicitly documents all security-related rules, including those related to technology use, data flows, data storage, data use, personal responsibility, and more.
This policy must be reviewed annually; it must also be distributed to all relevant parties, who must then review and acknowledge receipt of the policy.
Other measures included in requirement 12 relate to risk assessments, user awareness training, and incident response plans.
Learn More
Read this post to learn about additional data compliance and standards that will help your organization keep sensitive data safe from adversaries.
CrowdStrike and PCI compliance
PCI compliance can be a complex and potentially time-consuming task for companies that lack expertise in data security. For this reason, it is often helpful for organizations to engage a reputable cybersecurity partner to help them take steps to comply with these requirements and automate much of the related activity.
Another benefit of partnering with a cybersecurity solution provider to address core PCI requirements is that they can help clients maximize any security investments so that the company not only addresses compliance with PCI DSS but leverages acquired tools, technologies, and services to protect the organization more broadly.
Since 2016, the CrowdStrike Falcon® platform has been independently validated to assist organizations and businesses with compliance with PCI DSS requirements. This validation was provided in a report by Coalfire, a leading assessor for global PCI and other compliance standards across the financial, government, industry, and healthcare industries.
Coalfire determined that the Falcon platform is effective and provides substantial support for PCI DSS requirements. The platform’s capabilities in threat detection and response — as well as those associated with activity logging — make it a solid option to address system protection and monitoring requirements for PCI DSS.

CrowdStrike Falcon Applicability for PCI DSS V4.0
For more information about how CrowdStrike can help your organization address critical PCI DSS requirements, please download our whitepaper: CrowdStrike Falcon Applicability for PCI DSS V4.0
Download Now






