Complete Guide to Next-Gen SIEM
Complete Guide to Next-Gen SIEM
Building a first-class security operations center is no simple feat – maintaining it is even harder. Below, we discuss four security operations center best practices that every organization should strive for.
1. Start with strategy
The first step in establishing an organization’s SOC is to define a clear strategy that aligns with the organization’s business goals. This process should include an enterprise-wide assessment, during which the team can take inventory of existing assets and resources, and also identify gaps or potential vulnerabilities within the business that could be exploited by adversaries.
Another key aspect of strategic planning is developing a clear, comprehensive set of processes that will guide the SOC team in all manners of operation, including monitoring, detection, response and reporting.
Given the increasing complexity of the threat landscape, organizations will likely need to constantly review and update their strategy and processes to reflect new and emerging risks. Likewise, the organization at large must be made aware of basic security operations and best practices to help preserve the business’s overall health and performance.
2. Enable organization-wide visibility
The SOC can only protect known assets. At the same time, any device can compromise network security. It is crucial, therefore, that the SOC identifies all digital assets — including networks, databases, devices/endpoints, websites and information stores — and incorporates their individual data logs into a single monitoring and analysis function. It is also important to map the use of third-party services and traffic flowing between the assets, as threats may derive from this activity.
Creating this end-to-end visibility will not only help protect each asset individually, but also create a complete view of typical behavior and activity for the organization. This makes it easier for security technologies and tools to identify and prioritize risks and recommend actions for remediation in the future.
Expert Tip
Many security operations centers face challenges around volume, complexity, skills, and cost.
3. Establish the technology stack
The SOC is not a single asset — it is a combination of people, processes and technologies that work together to protect and defend the organization. On the technology side, there are many critical components that make up the digital backbone of the security center. These include the following:
- A security information and event management (SIEM) system, which aggregates and correlates data from network and device security feeds
- Digital assessment and monitoring systems, which detect anomalous behaviors or activity
- Prevention tools, such as firewalls or antivirus software
- Threat detection tools that use artificial intelligence (AI) and machine learning (ML) to recognize suspicious activity and escalate it within the SOC
- Threat response capabilities that use intelligent automation to automatically respond to low-level security threats and routine incidents
Due to the advanced nature of the threat landscape, as well as the complexity of the global business operations, organizations must leverage the latest digital technologies to stay a step ahead of cyber adversaries. Next-gen cloud-based security solutions play an important role, as they allow the organization to deploy tools quickly and support the ability to update or adapt to new threats. The CrowdStrike Falcon®® platform is a cloud-native security solution that provides real-time, continuous visibility and security across the organization’s assets. This solution combines many of the key aspects of a SOC, as well as a dedicated team to respond and manage the most sophisticated threats.
4. Combine intelligent automation and human resources to respond to threats
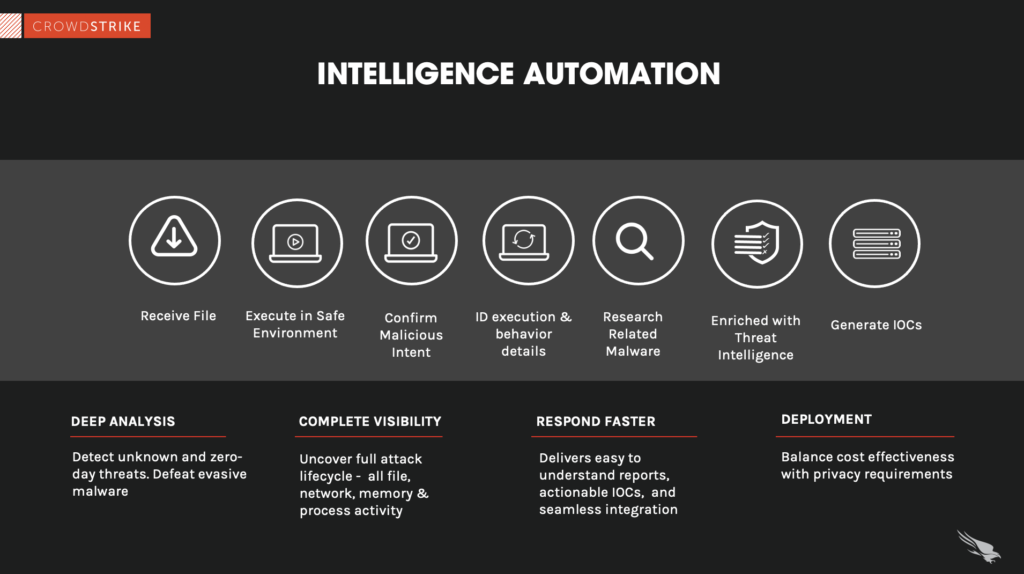
The most mature SOCs use a combination of threat intelligence automation and human oversight to manage security. Typically, the threat monitoring and detection tools provide the first line of defense, identifying risks and prioritizing them. Relatively low-level threats can be addressed through automation, while more advanced risks require human intervention. By combining highly skilled security professionals with AI-enabled solutions, organizations can not only ensure the safety of their network and assets but also do so with the least amount of time, cost and effort.
Advances in technology continue to increase the accuracy of detection tools and their ability to assess each risk. In addition, like any AI and ML tools, those used in cybersecurity improve over time, leveraging increasing amounts of data to better understand baseline activity and detect anomalies. The most advanced automation systems use behavioral analysis to “teach” these tools the difference between regular day-to-day operations and real threats, freeing humans to focus on higher-priority work.
Security Operations Center Assessments
When you become embedded in a daily routine of alert fatigue, it’s difficult to realize the gaps that may exist. In addition, simply keeping up with the latest trends, technologies, processes and threat intelligence becomes a luxury that few have the time for.
The CrowdStrike Security Operations Center (SOC) Assessment helps organizations quickly understand how to mature their security monitoring and incident response capabilities and takes them to the next level.
The SOC Assessment involves:
- Engaging workshops: In interactive workshops, CrowdStrike experts gather information on your existing SOC operations and share best practices.
- In-depth reporting: You receive a detailed, tailored report based on the workshops, documentation analysis and follow-up discussions.
- Prioritized areas for improvement: The assessment includes a roadmap of prioritized recommendations that will strengthen and improve your SOC’s ability to effectively detect and respond to cybersecurity incidents.
Discover the world’s leading AI-native platform for next-gen SIEM and log management
Elevate your cybersecurity with the CrowdStrike Falcon® platform, the premier AI-native platform for SIEM and log management. Experience security logging at a petabyte scale, choosing between cloud-native or self-hosted deployment options. Log your data with a powerful, index-free architecture, without bottlenecks, allowing threat hunting with over 1 PB of data ingestion per day. Ensure real-time search capabilities to outpace adversaries, achieving sub-second latency for complex queries. Benefit from 360-degree visibility, consolidating data to break down silos and enabling security, IT, and DevOps teams to hunt threats, monitor performance, and ensure compliance seamlessly across 3 billion events in less than 1 second.






