What is Email Spoofing?
Email spoofing is a type of cyberattack that targets businesses by using emails with forged sender addresses. Because the recipient trusts the alleged sender, they are more likely to open the email and interact with its contents, such as a malicious link or attachment.
Reasons for email spoofing
Phishing
Most email spoofing attempts lead to phishing attacks. A phishing email can appear to be from your bank, employer or boss, or use techniques to coerce information out of you by pretending, for example, to be a government agency.
The hacker could steal existing account credentials, deploy ransomware, or acquire enough information to open a new fraudulent account.
Expert Tip
Email Spoofing vs Phishing
A spoofed email is a gateway to a phishing attack. A phishing email can only be classified as a spoofing email if it includes a forged sender’s address.
Masking Identity
A spoofed email is anonymous. Hackers sometimes use spoofed emails to mask their identity and pre-establish trust with the user by appearing to be from a reputable organization or person.
Avoid Spam Filters
Hackers use spoofed emails as a means to get around email spam filtering. When an email is spoofed, it is unlikely to be caught in spam filters, and may often look like an email you get everyday.
Identity Theft
When the spoofed email appears to be trustworthy, many unsuspecting users send personal information and credentials to hackers. For example, hackers may ask for healthcare information or identity verification.
How does email spoofing work?
Email spoofing does not hack a sender’s account. It only makes an email appear as if it is coming from the sender. The difference is that, if a sender’s account were actually hacked, the spoofer could gain access to the person’s contacts or use the account to spam people, thereby causing a drop in email reputation. Email reputation is a measure that impacts deliverability.
Email spoofing attacks are conducted by using a Simple Mail Transfer Protocol or SMTP server and an email platform, such as Outlook, Gmail, etc. The scammer changes fields within the message header, such as the FROM, REPLY-TO, and RETURN-PATH fields.
This is possible because of the way email has evolved. Message headers, which include the TO, FROM, and BCC fields, are separated from the body of the message. Because security was not built in when SMTP was created, SMTP has no way to authenticate addresses.
Real world email spoofing example
One example of an email spoofing campaign used to leverage a second-stage wire fraud attack was common enough to become the subject of an IRS bulletin. In this attack, spoofed emails that appeared to come from executives in targeted organizations were sent to employees in HR or payroll. The fraudulent emails urgently requested a list of all employees and their W-2 forms. So far, this was a standard email spoofing scam. But there was a twist—the phishing scam was followed up by another asking the employee to make a wire transfer. This stage of the attack was a business email compromise, or BEC attack. This two-stage scam is still observed in frequent use today.
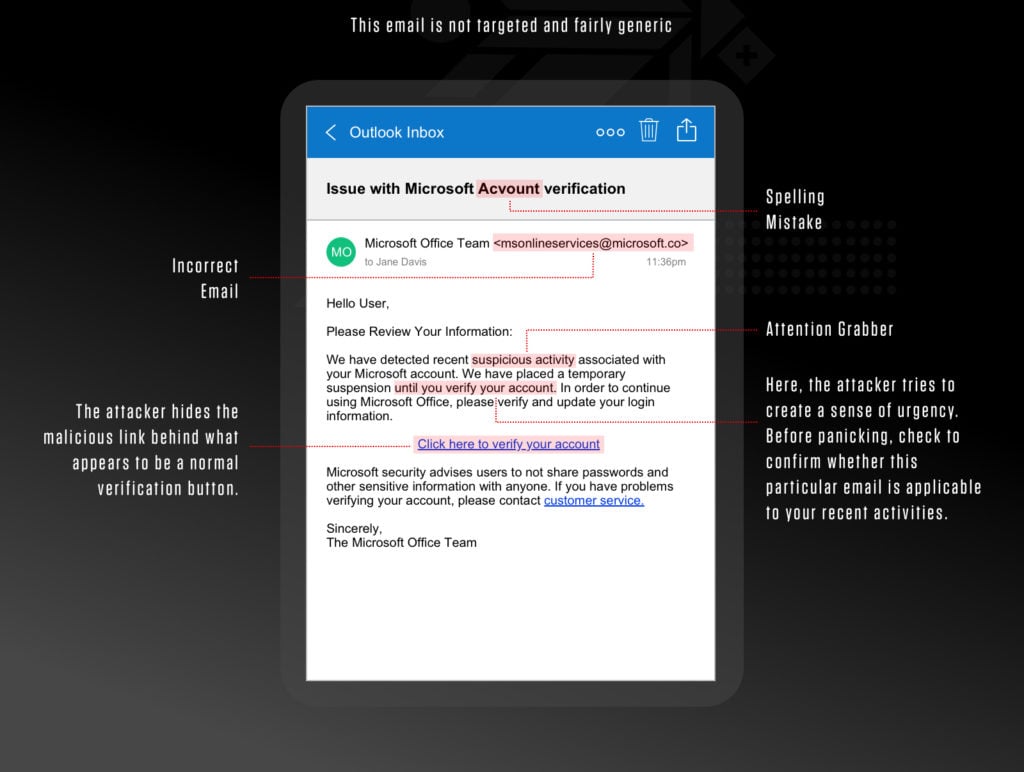
How to identify a spoofed email
- The displayed sender name does not match the email address
- The information in the email signature, such as the telephone number, doesn’t align with what is known about the sender (i.e., the sender is located in California but the phone number in the sig file has a Massachusetts area code)
- Check the email header for the RECEIVED line. It should match the email address that is displayed in the email
- Check the email header for RECEIVED-SPF. It should say Pass. If it says Fail or Softfail, the email may have been spoofed
- If the organization is using DKIM and DMARC, the AUTHENTICATION-RESULTS will show whether the email passed the requirements of those protocols.
How to protect yourself from email spoofing
Use email security protocols
Email security protocols use domain authentication to reduce threats and spam. The email security protocols in use today are Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC).
SPF detects forged sender addresses during the delivery phase, but it can only detect them in the envelope of the email, which is used when an email is bounced. However, when used in conjunction with DMARC authentication, SPF can detect a forged “visible sender,” which is a technique that is commonly used in phishing and spam.
Encrypt emails
DKIM uses public and private keys to prove that a sender is who they say they are. Each message that goes out through SMTP needs a pair of keys that match a public DNS record, which is verified by the receiving mail server.
Deploy an email security gateway
Email security gateways, or Secure Email Gateways, are a collection of technologies that work on a network level to block emails that do not meet security policy requirements. An email security gateway scans all incoming and outbound email and may also include capabilities like malware blocking, spam filtering, content filtering, and email archiving. Because these protective actions occur at the network level, users are not impacted at all.
Use an antimalware solution
Antimalware may detect and block spoofed emails before they reach their targets’ inboxes. It’s important to keep antimalware software up to date because attackers are alert to newly-identified vulnerabilities and act quickly to exploit them.







