What is External Attack Surface Management (EASM)?
External Attack Surface Management (EASM) refers to the continuous discovery, monitoring, evaluation, prioritization, and remediation of attack vectors of an organization's external attack surface. An External Attack Surface, also known as Digital Attack Surface, is the sum of an organization’s internet-facing assets and the associated attack vectors which can be exploited during an attack.
Internet-facing assets include anything from domain names, SSL certificates and protocols to operating systems, servers, IOT devices and network services. These assets are scattered across on-premise, cloud environments and third-party vendors and represent the easiest way of accessing internal networks and sensitive data.
In the past decade organizations have accumulated an ever-growing list of public IP addresses to facilitate the communication between their internal network and the internet. Some of these IP addresses are officially registered but the majority of them are unregistered and ephemeral. Today, organizations’ external attack surfaces span beyond organizations’ known network ranges and often include assets managed by third party vendors.
What are the Main Challenges around External Attack Surface Mapping?
Both the shift to the cloud and IT democratization have created a new reality on the ground. Most organizations have major blind spots and limited visibility into their Shadow IT and asset exposure to the Internet. Trying to map the external attack surface with the visibility provided by traditional tools is almost impossible. Here is why:
Distributed IT Ecosystems
The days during which organizations had a well-defined network perimeter are long gone. Today, your assets are everywhere. In addition to your core network, you have regional offices, and subsidiaries, you work with third-party hosting providers, business partners all of which are connected to your network. As more and more assets are hosted beyond organizations’ firewalls, it has become increasingly difficult to efficiently manage and monitor them.
Siloed Teams
Multiple teams within the organizations are dealing with internet connected assets. IT managers, network engineers, DevOps and marketing are just a few. More often than not these teams are facing the dilemma of needing to quickly deliver results vs the need to comply with IT and security policies. Unofficial cloud instances, unproved websites and other assets will often be created without passing through official channels.
Your External Attack Surface is Constantly Changing
With 80%-95% of your IP addresses being ephemeral, keeping track of your internet-facing inventory using traditional methods is almost impossible. In addition, frequent changes in the external attack surface can also come from other directions. A small click on the wrong button can result in an unintentional risky exposure of an asset to the web.
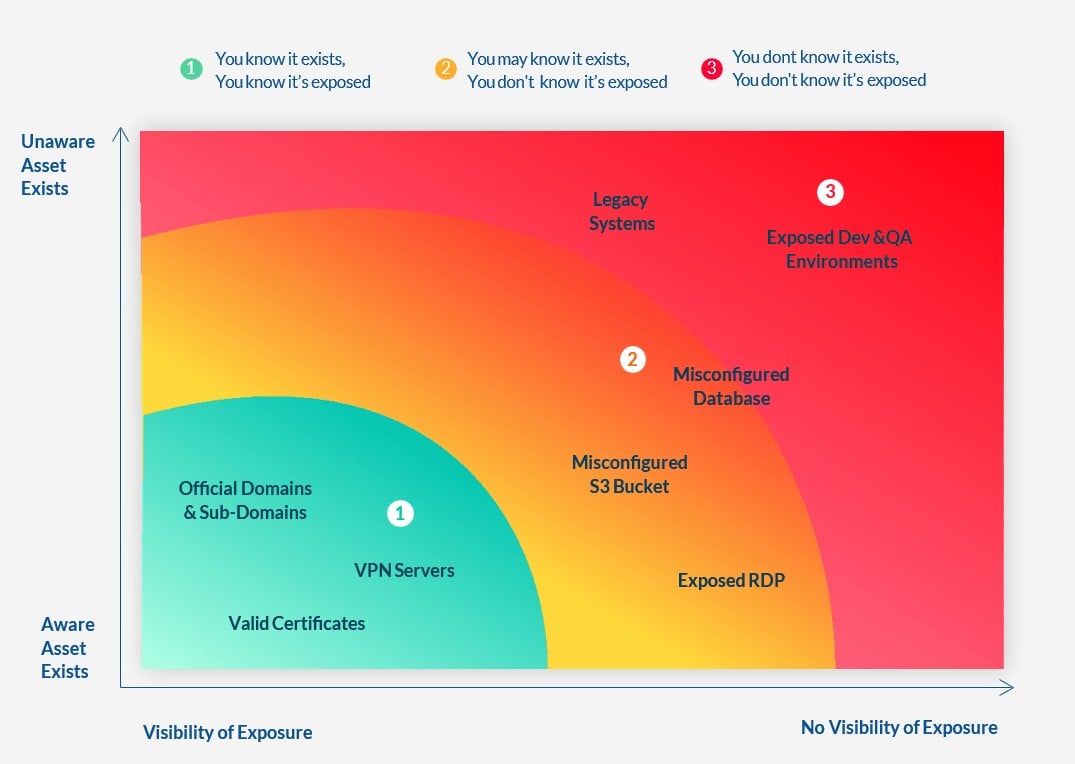
What Are The Risks Associated With Limited Attack Surface Visibility?
The latest data breach report by Verizon indicates that 70% of attacks are perpetrated by external threat actors. These attackers are clearly seeing and exploiting weak points in the network perimeter which companies leave unprotected. This is not surprising as Reposify’s data shows that on average organizations are unaware of 64% of their internet-connected assets.
In 2016 Gartner predicted that by 2020, 30% of successful attacks experienced by enterprises will be on their shadow IT resources. Our recent analysis indicates that around 38% of successful attacks in 2019 were results of shadow IT, misconfigurations and unknown exposures to the internet that could have been avoided if organizations had better visibility of their attack surface.
How Does An External Attack Surface Management Solution Help?
External Attack surface management is simply the only way to discover, manage and monitor your perimeter-less network at scale. With Shadow IT being so prevalent and human errors unavoidable, external attack surface management is taking a center stage with more and more companies establishing dedicated teams for attack surface management and reduction.
Identify Unknown Risks and Exposures in Real time
Automatically generate a complete asset inventory and discover assets of which you weren’t aware. Get notified of any new exposures, vulnerabilities & other security issues
Streamline Operations
Automatic risk prioritization and built in remediation advice will save precious time and help you focus on what matters most. The ability to easily share findings with internal teams as well as 3rd party vendors will increase operational efficiency and align teams.
Get More out of Your Existing Security Stack
How do you run a vulnerability scanner or pen testing on assets if you don’t know they exist? Getting an always up to date view of all your assets allows you to fully maximize the current tools you are using.
Optimize IT & Security Costs
Identify legacy systems, unused tools and servers to reduce inflated IT costs Save precious time and eliminate manual work.
Essential Components Of An External Attack Surface Management Solution
1. Autonomous Exposed Assets
Inventory Generation Automatic detection of all exposed assets, whether they are known or unknown, across all environments and the supply chain.
2. Business Context Insight
Ability to understand exactly to which business unit, subsidiary or 3rd party vendor each exposed asset belongs and how it is connected to the core network.
3. Automatic Asset Classification
Ability to instantly see all exposed assets by category, platform and service type .
4. Continuous External Surface Monitoring
Security insight generation and risks prioritization based on business context so you can focus on the most critical tasks at hand.







